Tauranga Pensioner Concerned Over Identity Theft Following ManageMyHealth Cyber Breach Affecting 127,000 Users
Published on: 2026-01-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
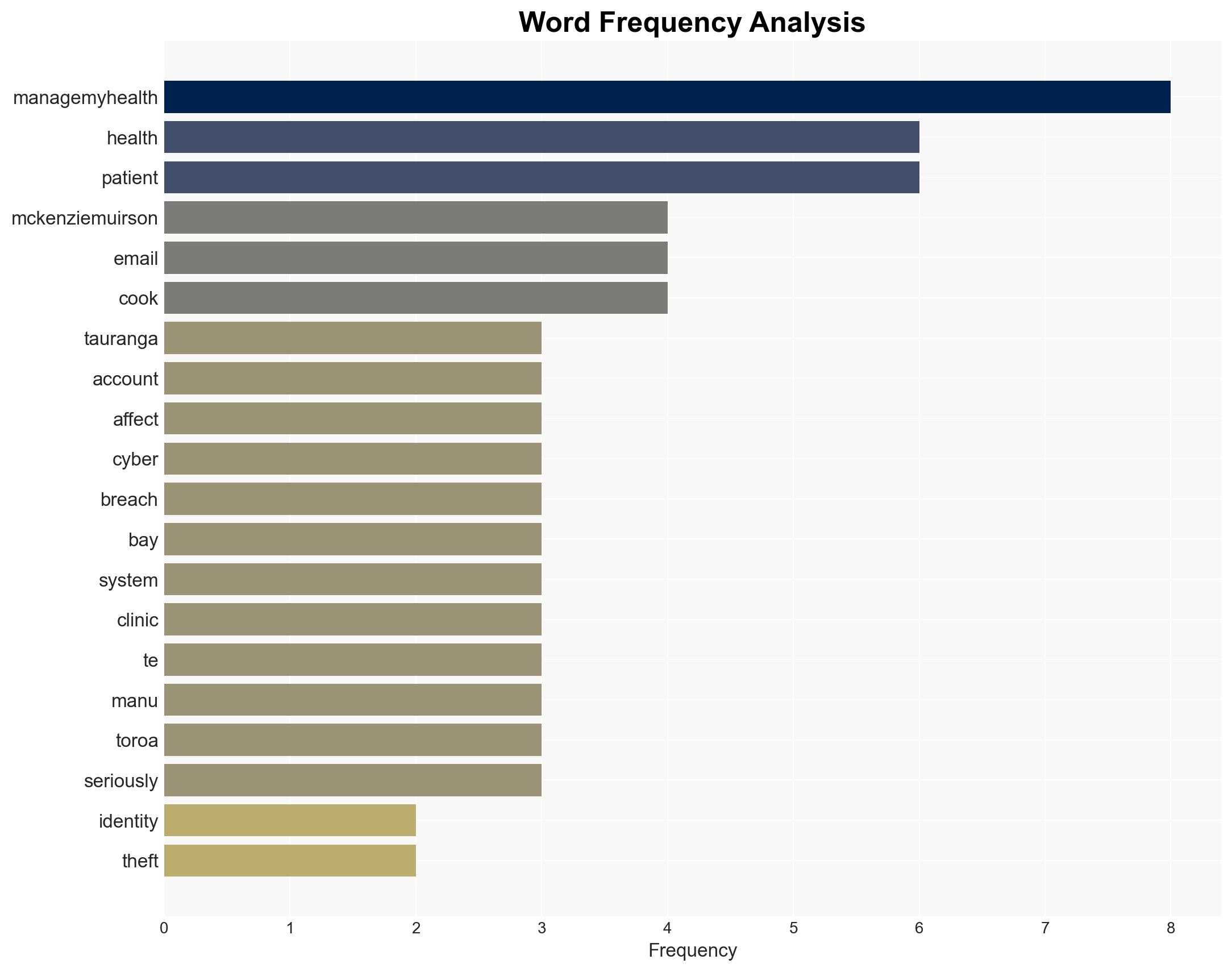
Intelligence Report: ManageMyHealth cyber attack Tauranga patient fears identity theft
1. BLUF (Bottom Line Up Front)
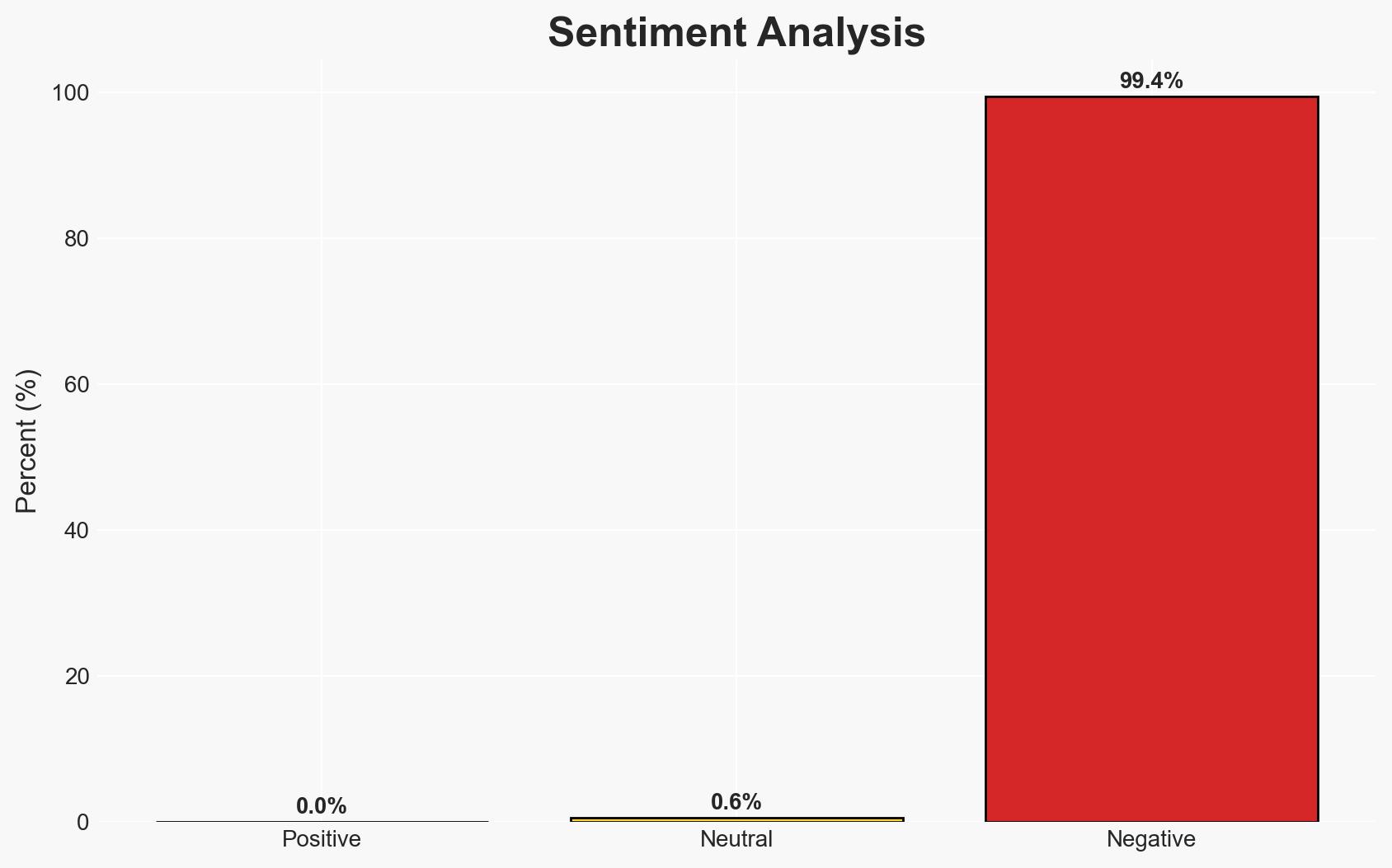
The ManageMyHealth cyber breach has compromised sensitive health records of over 127,000 users, raising significant concerns about identity theft and data security, particularly in Northland, New Zealand. The breach highlights vulnerabilities in health information systems and the potential for broader impacts on patient trust and data protection practices. Current analysis supports the hypothesis that the breach resulted from inadequate cybersecurity measures. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The breach was due to inadequate cybersecurity measures by ManageMyHealth. This is supported by the lack of specific details on how the breach occurred and the broad impact on users. However, the exact method of breach remains unclear, creating uncertainty.
- Hypothesis B: The breach was a targeted cyber-attack by an external actor aiming to exploit health data for financial gain. While plausible, there is no direct evidence or claims of responsibility to support this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the absence of evidence indicating a targeted attack and the general nature of the breach. Indicators such as further technical details or claims of responsibility could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The breach was not state-sponsored; ManageMyHealth’s cybersecurity protocols were insufficient; affected users are at risk of identity theft; data retention policies contributed to the breach’s impact.
- Information Gaps: Specific technical details of the breach method; identity of potential perpetrators; extent of data misuse post-breach.
- Bias & Deception Risks: Potential bias in self-reported security measures by ManageMyHealth; lack of independent verification of breach details; possible underreporting of affected regions.
4. Implications and Strategic Risks
The ManageMyHealth breach could lead to increased scrutiny of healthcare data security practices and regulatory responses. The incident may also erode public trust in digital health platforms, affecting user engagement and compliance.
- Political / Geopolitical: Potential for legislative action to enhance data protection laws and oversight in New Zealand.
- Security / Counter-Terrorism: Increased risk of exploitation of compromised data by criminal networks.
- Cyber / Information Space: Heightened awareness and potential for similar attacks on other health information systems.
- Economic / Social: Possible financial losses for affected individuals and reputational damage to ManageMyHealth.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive forensic investigation; enhance user communication on protective measures; initiate a review of cybersecurity protocols.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; implement advanced threat detection and response systems; engage in public awareness campaigns on data protection.
- Scenario Outlook:
- Best: Breach contained with minimal data misuse, leading to improved security measures.
- Worst: Data widely exploited, resulting in significant identity theft and financial losses.
- Most-Likely: Moderate exploitation of data, prompting regulatory and security enhancements.
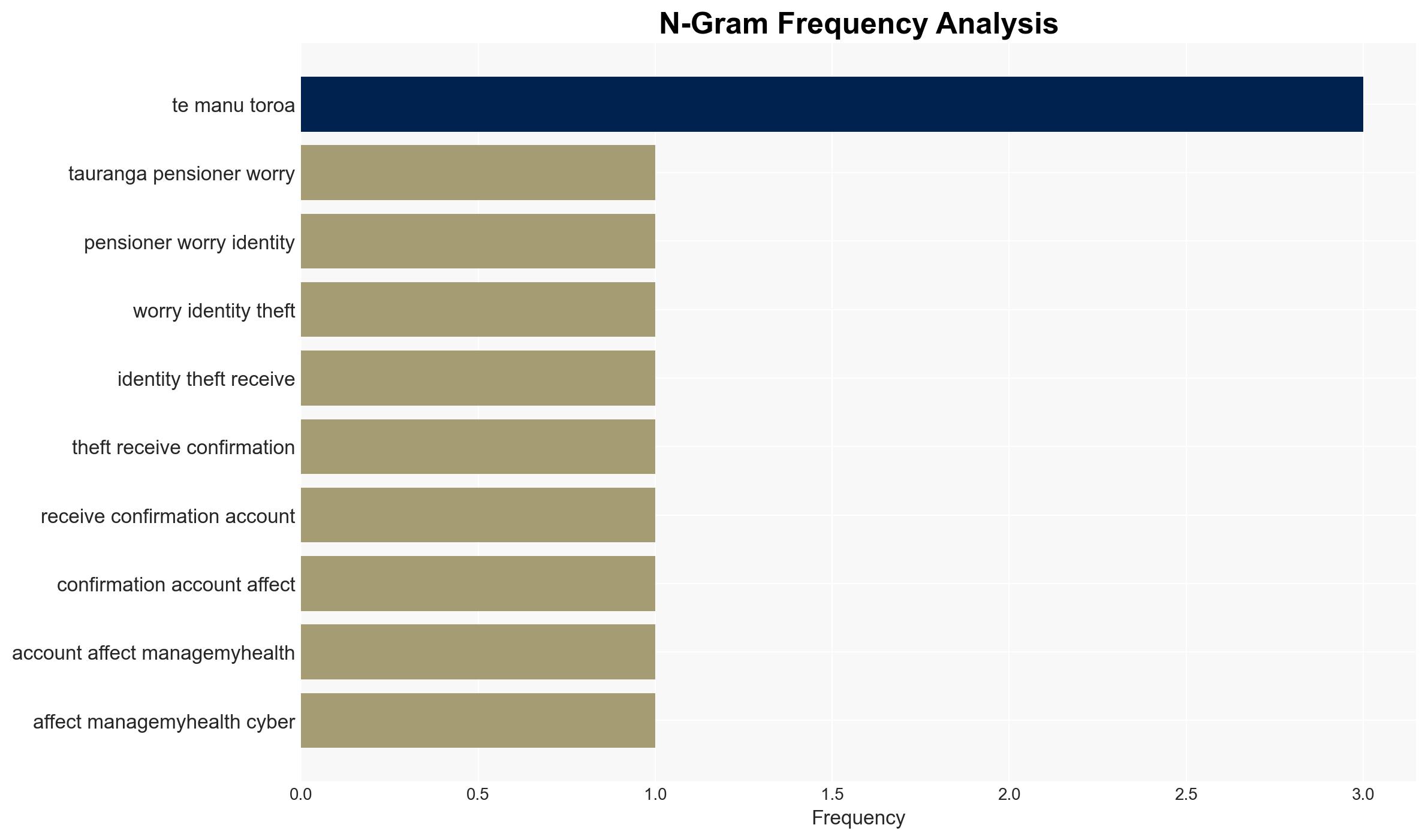
6. Key Individuals and Entities
- Kaye McKenzie-Muirson, affected user
- ManageMyHealth, health information platform
- Health NZ, national health authority
- Te Manu Toroa, healthcare provider
- Pat Cook, Te Manu Toroa chief executive
7. Thematic Tags
cybersecurity, data breach, identity theft, healthcare, New Zealand, data protection, public trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us