Kyowon Group Reports Data Breach Following Ransomware Attack Affecting Millions of Accounts
Published on: 2026-01-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: South Korean giant Kyowon confirms data theft in ransomware attack
1. BLUF (Bottom Line Up Front)
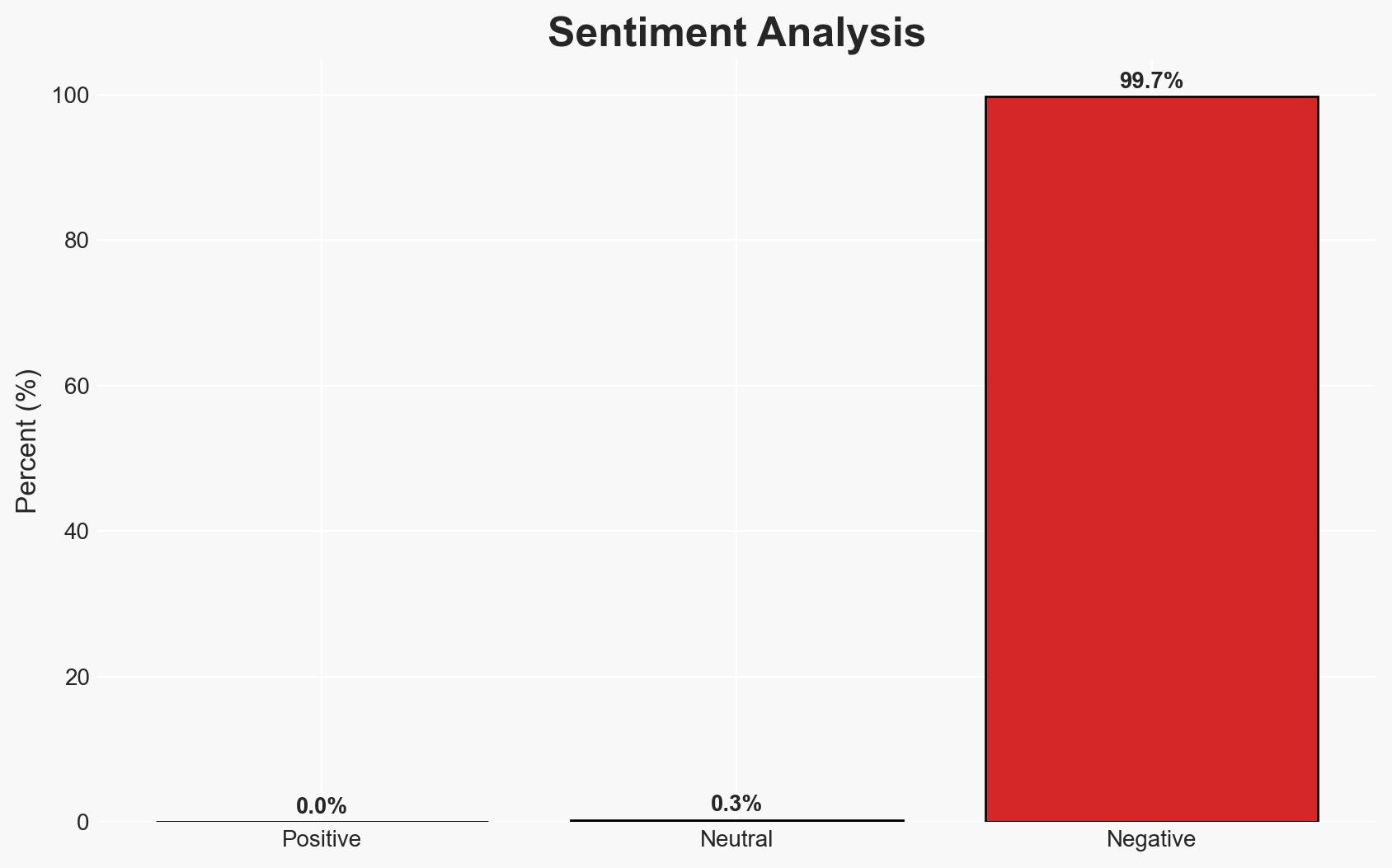
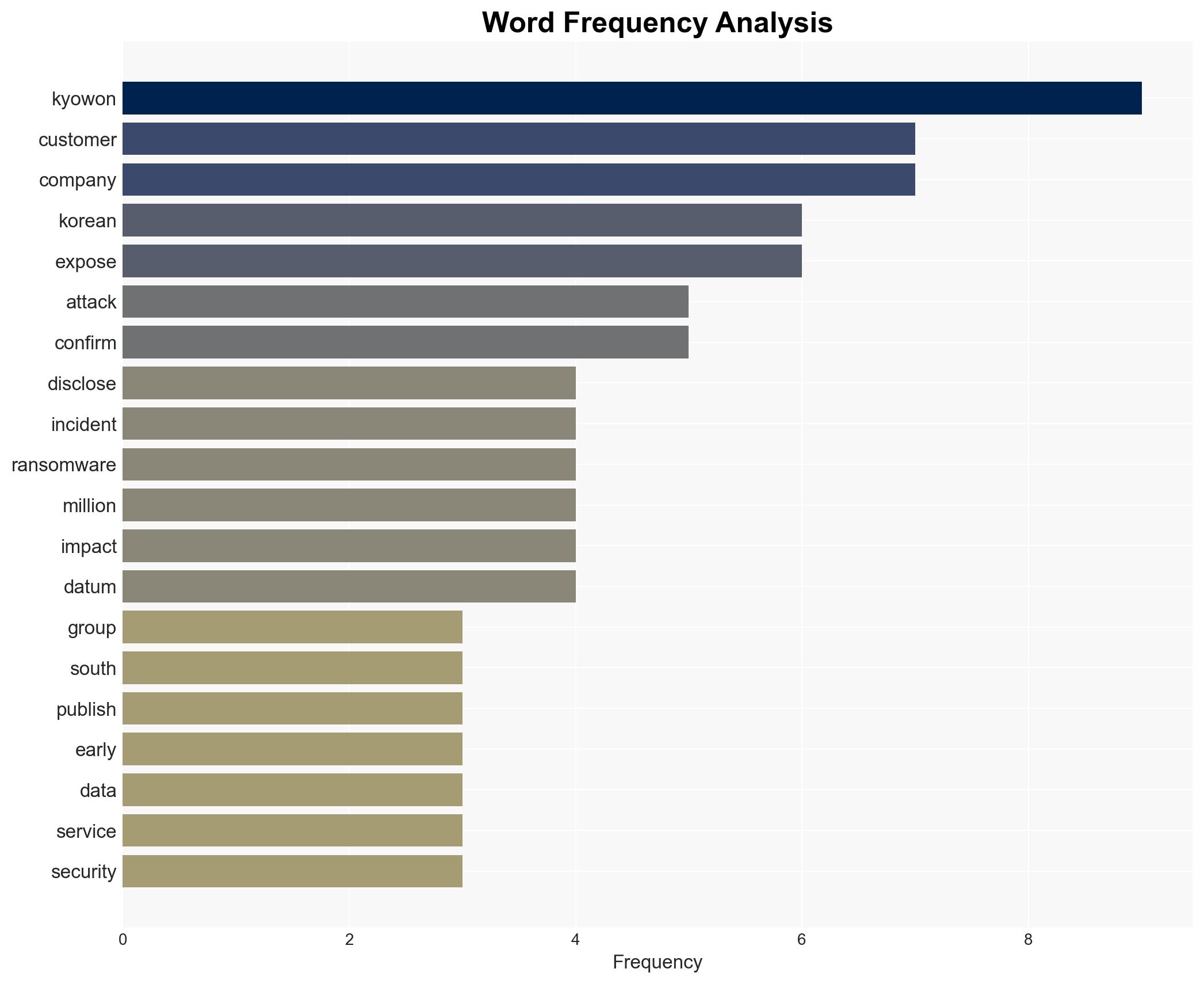
The Kyowon Group, a major South Korean conglomerate, has confirmed a ransomware attack that resulted in the theft of data, potentially impacting millions of customer accounts. The attack disrupted operations and affected a significant portion of the company’s servers. The most likely hypothesis is that this attack is part of a broader trend of cyberattacks targeting South Korean companies. Overall confidence in this assessment is moderate due to limited information on the attackers and their motives.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack on Kyowon is part of a coordinated campaign targeting South Korean companies, possibly by a state-sponsored group. This is supported by the recent pattern of similar attacks on major South Korean firms. However, the lack of claims by known ransomware groups introduces uncertainty.
- Hypothesis B: The attack is an isolated criminal act by financially motivated cybercriminals seeking ransom payments. The absence of a claim by major ransomware groups and the focus on data exfiltration could support this hypothesis, though it does not explain the broader pattern of attacks in the region.
- Assessment: Hypothesis A is currently better supported due to the pattern of recent cyberattacks on South Korean companies, suggesting a potential strategic targeting. Key indicators that could shift this judgment include attribution of the attack to a known group or evidence of ransom demands.
3. Key Assumptions and Red Flags
- Assumptions: The attack is assumed to be part of a larger trend; customer data exposure is assumed significant; Kyowon’s response will be transparent and timely.
- Information Gaps: Specific details on the attackers, their motives, and the full extent of data compromised are missing.
- Bias & Deception Risks: Potential bias in media reporting and company statements; risk of deception by attackers in not claiming responsibility.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of South Korean cybersecurity practices and potential regulatory changes. The broader trend of attacks may escalate tensions in the region if state-sponsored involvement is confirmed.
- Political / Geopolitical: Potential for increased geopolitical tensions if state-sponsored involvement is confirmed.
- Security / Counter-Terrorism: Heightened alert for further cyberattacks on critical infrastructure.
- Cyber / Information Space: Increased focus on cybersecurity measures and potential for retaliatory cyber operations.
- Economic / Social: Potential loss of consumer trust and financial impact on Kyowon; broader economic implications if similar attacks continue.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of South Korean cyber activity; support Kyowon in forensic investigation; engage with international partners for intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures for critical sectors; strengthen public-private partnerships in cybersecurity; invest in capability development for rapid response.
- Scenario Outlook:
- Best: Attack is isolated, and Kyowon recovers with minimal data loss.
- Worst: State-sponsored campaign confirmed, leading to regional tensions.
- Most-Likely: Continued pattern of cyberattacks with gradual improvements in defensive measures.
6. Key Individuals and Entities
- Kyowon Group
- Korea’s Internet & Security Agency (KISA)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, South Korea, data breach, cybercrime, information security, corporate risk
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us