Analyzing Cryptojacking Threats: Insights from Real-World Botnet Attacks and Initial Access Brokers
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Battling Cryptojacking Botnets and IABs Guest Diary Thu Jan 15th
1. BLUF (Bottom Line Up Front)
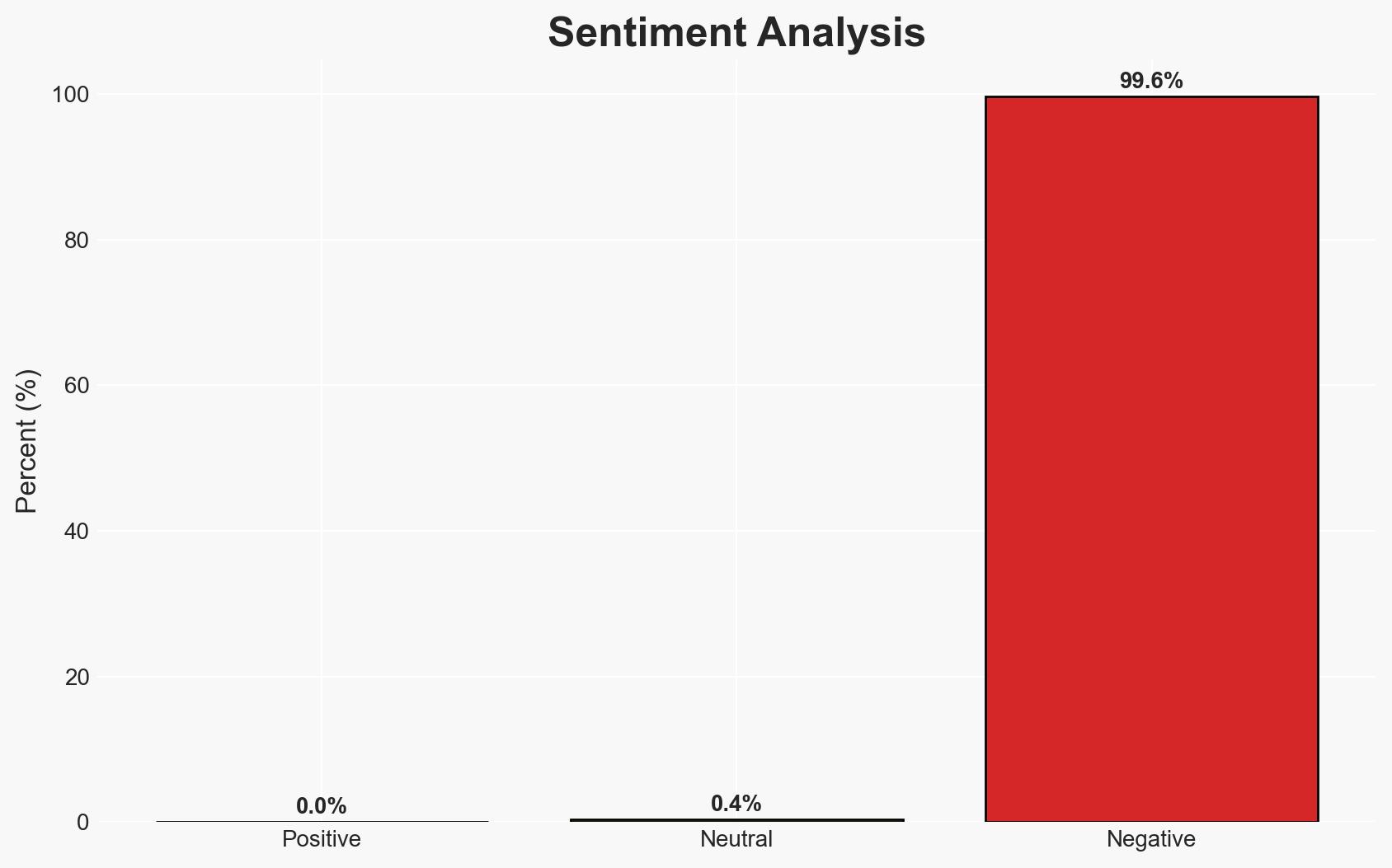
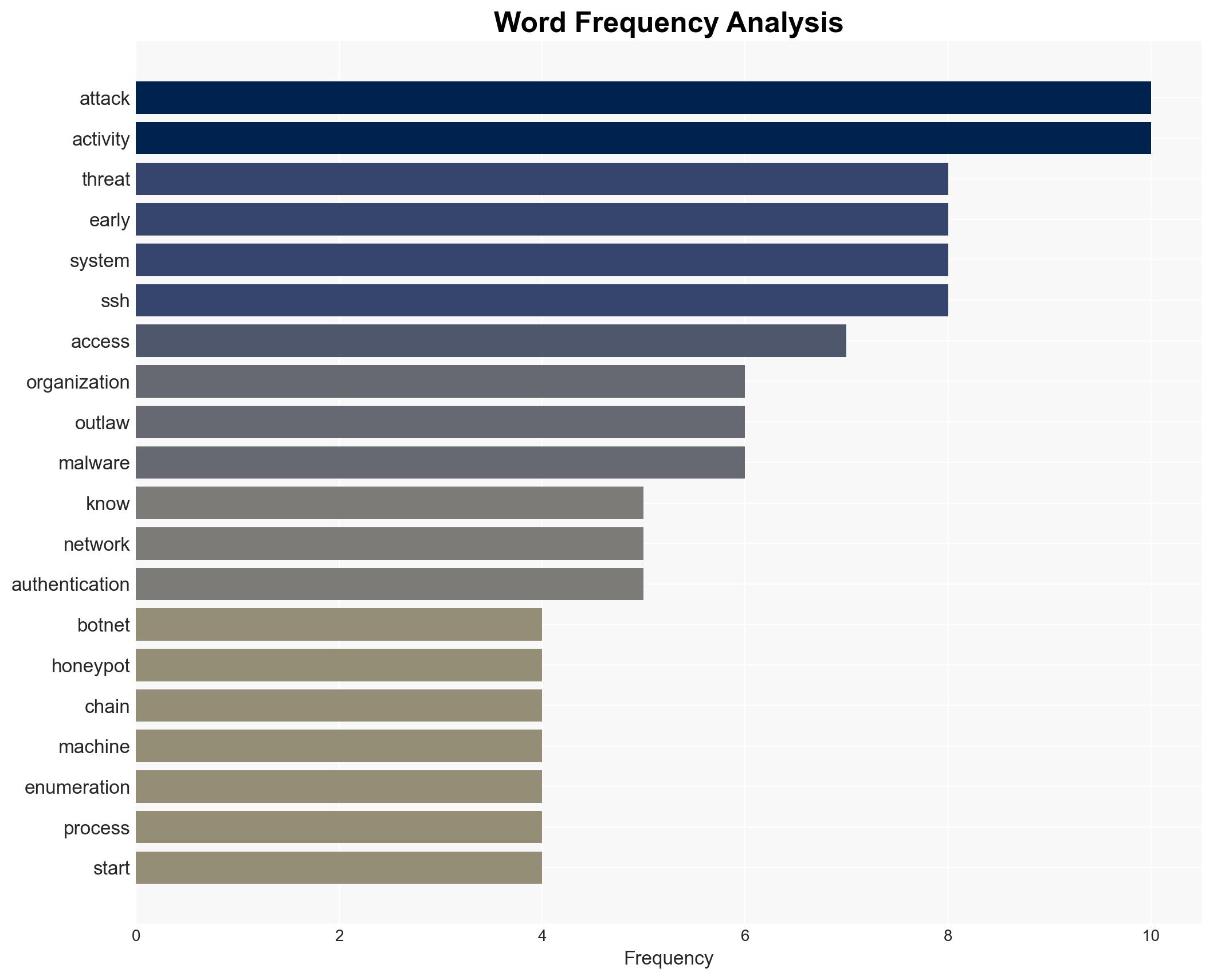
The observed cryptojacking and botnet activities, potentially linked to the organization “Outlaw,” represent a significant cyber threat with implications for network security and operational integrity. The most likely hypothesis is that these activities are part of a broader strategy to exploit compromised systems for financial gain and further cyber operations. This assessment is made with moderate confidence due to the observed patterns and known tactics of similar groups.
2. Competing Hypotheses
- Hypothesis A: The cryptojacking and botnet activities are primarily aimed at resource exploitation for financial gain. This is supported by the enumeration and system information gathering observed, which are typical of cryptojacking operations. However, the full extent of the network’s intentions remains uncertain.
- Hypothesis B: The activities are a precursor to more sophisticated cyber operations, such as DDoS attacks or selling access to other threat actors. This is supported by the involvement of Initial Access Brokers (IABs) and the potential for these footholds to be monetized in various ways.
- Assessment: Hypothesis A is currently better supported due to the direct evidence of cryptojacking-related activities. Key indicators that could shift this judgment include evidence of coordination with other threat actors or the discovery of infrastructure supporting broader cyber operations.
3. Key Assumptions and Red Flags
- Assumptions: The activities are linked to the “Outlaw” group; the primary motivation is financial gain; the observed IPs are accurately attributed to the threat actors; the enumeration scripts are indicative of initial access operations.
- Information Gaps: Lack of comprehensive attribution to specific actors; insufficient data on the full scope of the network’s operations; unknowns about potential collaboration with other cybercriminal entities.
- Bias & Deception Risks: Potential bias in attributing activities to known groups based on limited evidence; risk of misinterpretation of the threat actors’ ultimate objectives; possibility of deceptive tactics to mislead attribution efforts.
4. Implications and Strategic Risks
The development of cryptojacking and botnet activities could lead to increased cyber threats and operational disruptions, affecting both public and private sector entities. The evolution of these threats could have wide-ranging impacts across various domains.
- Political / Geopolitical: Potential for increased tensions if state actors are involved or if attacks target critical infrastructure.
- Security / Counter-Terrorism: Heightened threat environment requiring enhanced cyber defenses and incident response capabilities.
- Cyber / Information Space: Increased need for monitoring and threat intelligence to detect and mitigate similar attacks.
- Economic / Social: Potential economic impact due to resource drain and operational disruptions, affecting business continuity and public trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance network monitoring and threat detection capabilities; isolate compromised systems; update incident response plans to address cryptojacking and botnet threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms and law enforcement; invest in cybersecurity training and awareness programs; strengthen international cooperation on cybercrime.
- Scenario Outlook:
- Best Case: Effective mitigation and international collaboration reduce the threat, leading to arrests and dismantling of the network.
- Worst Case: Escalation of attacks targeting critical infrastructure, causing significant economic and operational damage.
- Most-Likely: Continued low-level attacks with periodic spikes in activity, requiring ongoing vigilance and adaptation of defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cryptojacking, botnets, initial access brokers, cybercrime, threat intelligence, network security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us