Lumen’s Black Lotus Labs Neutralizes Over 550 C2 Servers Linked to AISURU and Kimwolf Botnets
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Lumen disrupts AISURU and Kimwolf botnet by blocking over 550 C2 servers
1. BLUF (Bottom Line Up Front)
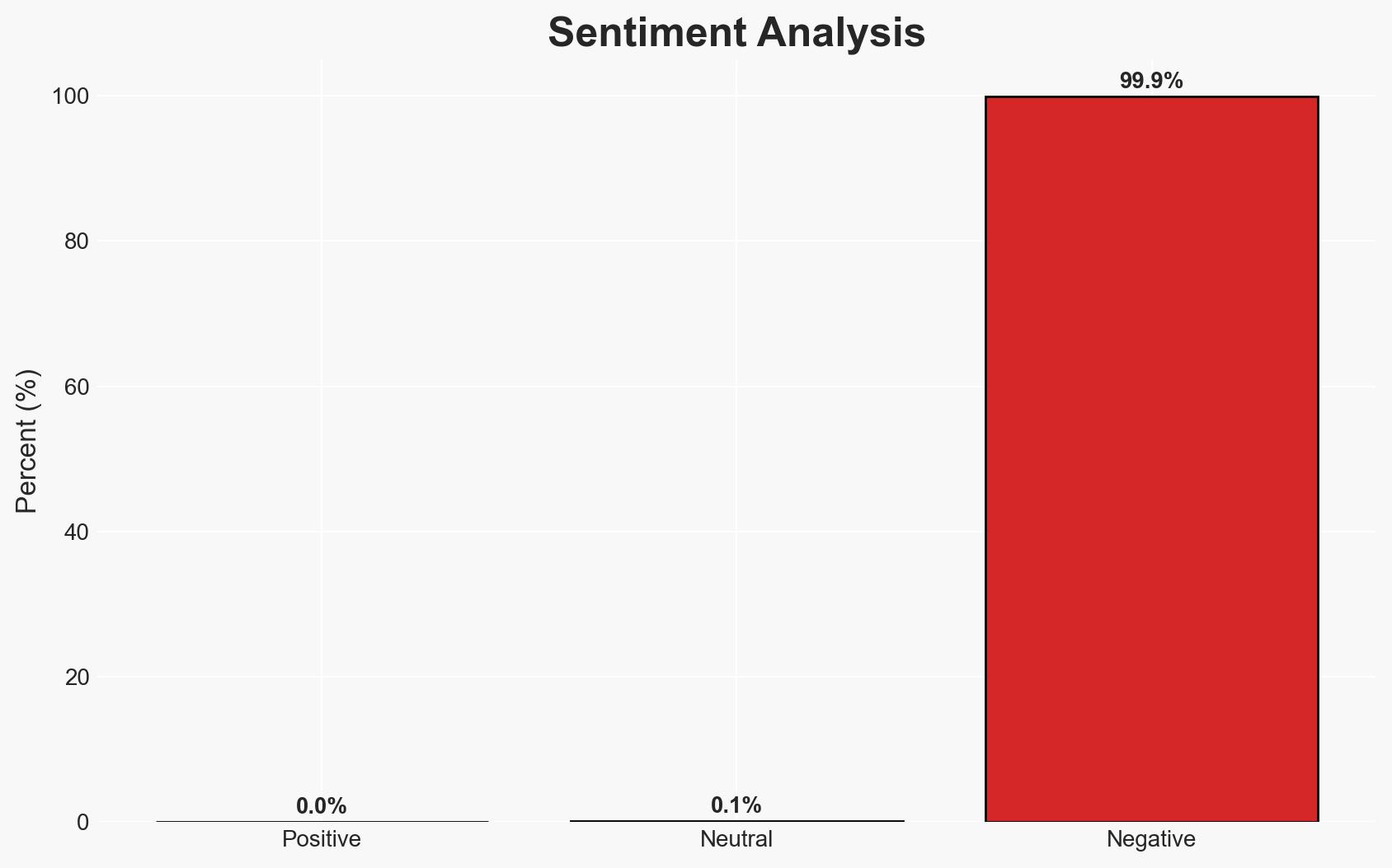
Lumen’s disruption of over 550 command-and-control (C2) servers linked to the AISURU and Kimwolf botnets significantly impacts the operational capabilities of these networks, which are used for DDoS attacks and proxy abuse. The action primarily affects broadband providers and could reduce the frequency and intensity of such attacks in the short term. Overall, there is moderate confidence that this disruption will temporarily hinder the botnets’ operations but may not eliminate the threat entirely.
2. Competing Hypotheses
- Hypothesis A: The disruption of C2 servers will lead to a significant and sustained reduction in the operational capabilities of the AISURU and Kimwolf botnets. Supporting evidence includes the immediate impact on over 550 C2 nodes and the reduction in botnet traffic. However, the adaptability of botnet operators and potential for rapid reconstitution are key uncertainties.
- Hypothesis B: The disruption will only temporarily affect the botnets, which will quickly adapt and restore their capabilities. This is supported by the botnets’ use of advanced techniques such as EtherHiding and the global distribution of their infrastructure. The lack of comprehensive data on the full extent of the botnet’s infrastructure is a contradicting factor.
- Assessment: Hypothesis B is currently better supported due to the sophisticated nature of the botnets and their ability to evade detection and takedown efforts. Indicators that could shift this judgment include sustained reductions in attack volumes and further successful disruptions of botnet infrastructure.
3. Key Assumptions and Red Flags
- Assumptions: The botnets rely heavily on the disrupted C2 infrastructure; operators will face challenges in quickly re-establishing full operational capacity; law enforcement collaboration will continue to be effective.
- Information Gaps: The full extent of the botnets’ infrastructure and the identity of key operators remain unclear. Detailed intelligence on the botnets’ reconstitution strategies is lacking.
- Bias & Deception Risks: There is a risk of overestimating the impact of the disruption due to reliance on data from a single source (Lumen). The potential for botnet operators to use misinformation to conceal their activities should be considered.
4. Implications and Strategic Risks
The disruption of the AISURU and Kimwolf botnets could lead to temporary reductions in DDoS attack volumes, but the long-term impact is uncertain. The situation could evolve with botnet operators adapting their strategies.
- Political / Geopolitical: Increased international cooperation in cyber defense could be prompted, but there is a risk of retaliatory cyber actions by affected parties.
- Security / Counter-Terrorism: A temporary reduction in DDoS attacks may improve network stability for critical infrastructure, but the threat remains if botnets reconstitute.
- Cyber / Information Space: The disruption highlights the need for ongoing vigilance and adaptive cybersecurity measures to counter evolving threats.
- Economic / Social: Reduced DDoS activity could lead to improved service reliability for broadband providers, but economic impacts are likely minimal unless disruptions persist.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of botnet activity, particularly for signs of reconstitution; increase collaboration with international cyber defense entities.
- Medium-Term Posture (1–12 months): Develop resilience measures for critical infrastructure; invest in advanced threat detection and response capabilities.
- Scenario Outlook: Best case: Botnets remain disrupted, leading to sustained reductions in DDoS attacks. Worst case: Botnets quickly adapt and resume operations at previous levels. Most likely: Botnets partially reconstitute, leading to intermittent disruptions.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, DDoS attacks, botnets, cyber defense, network stability, international cooperation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us