Poland Accuses Russia of Orchestrating Cyberattacks on Energy Infrastructure
Published on: 2026-01-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Polish Premier Blames Russia for Cyberattack on Energy Facilities
1. BLUF (Bottom Line Up Front)
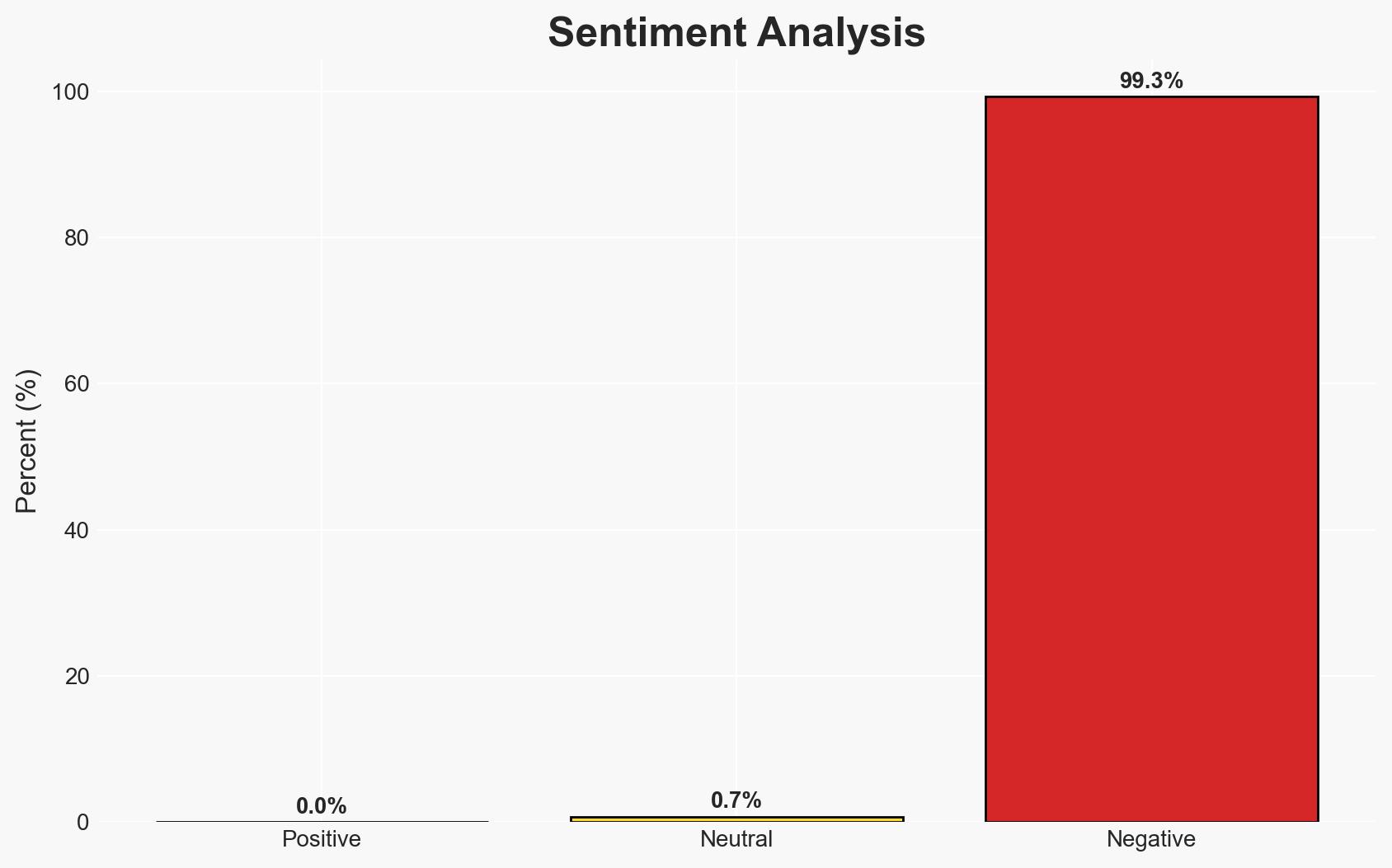
Poland’s Prime Minister has attributed recent cyberattacks on the country’s energy infrastructure to Russian-linked groups, highlighting ongoing hybrid threats from Moscow. The attacks, although not crippling, underscore Poland’s vulnerability as a frontline NATO state. The overall confidence level in this assessment is moderate due to the lack of direct attribution evidence and the complex nature of cyber attribution.
2. Competing Hypotheses
- Hypothesis A: The cyberattacks on Polish energy facilities were orchestrated by Russian state-affiliated groups. This is supported by Poland’s history of being targeted by Kremlin-linked hackers and the geopolitical context of Russia’s aggression in the region. However, direct attribution remains challenging, and the evidence is largely circumstantial.
- Hypothesis B: The attacks were conducted by independent hacker groups or other state actors seeking to exploit tensions between Poland and Russia. This hypothesis considers the possibility of false flag operations or opportunistic attacks by non-Russian entities. The lack of concrete evidence linking the attacks directly to Russian state actors supports this alternative explanation.
- Assessment: Hypothesis A is currently better supported due to the pattern of previous attacks linked to Russian interests and the strategic context of Poland’s support for Ukraine. Indicators such as increased cyber activity from known Russian-linked groups could further substantiate this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: The attribution to Russian-linked groups is based on historical patterns; Poland’s strategic importance makes it a likely target; cyber attribution remains inherently difficult.
- Information Gaps: Lack of technical forensic evidence directly linking the attacks to Russian state actors; limited visibility into the operational capabilities of the attackers.
- Bias & Deception Risks: Confirmation bias due to Poland’s geopolitical stance; potential for misinformation or disinformation campaigns by involved parties.
4. Implications and Strategic Risks
This development could escalate tensions between NATO and Russia, potentially leading to increased cyber and hybrid warfare activities. Poland’s role as a conduit for military aid to Ukraine makes it a strategic target.
- Political / Geopolitical: Increased diplomatic strain between Poland and Russia; potential for NATO to reassess its defensive posture in Eastern Europe.
- Security / Counter-Terrorism: Heightened alert for further cyber and hybrid threats; potential for retaliatory actions by Poland or its allies.
- Cyber / Information Space: Escalation in cyber operations targeting critical infrastructure; potential for information warfare to influence public perception.
- Economic / Social: Potential disruptions to energy supply could impact economic stability; public concern over national security may rise.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure; engage in diplomatic channels to address cyber threats; increase public awareness of cyber risks.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity partnerships within NATO; invest in resilience measures for critical infrastructure; develop rapid response capabilities.
- Scenario Outlook:
- Best: Diplomatic resolutions reduce cyber threat levels; enhanced defenses deter future attacks.
- Worst: Escalation of cyberattacks leads to significant infrastructure damage and geopolitical conflict.
- Most-Likely: Continued low-level cyber skirmishes with occasional spikes in activity; ongoing geopolitical tension.
6. Key Individuals and Entities
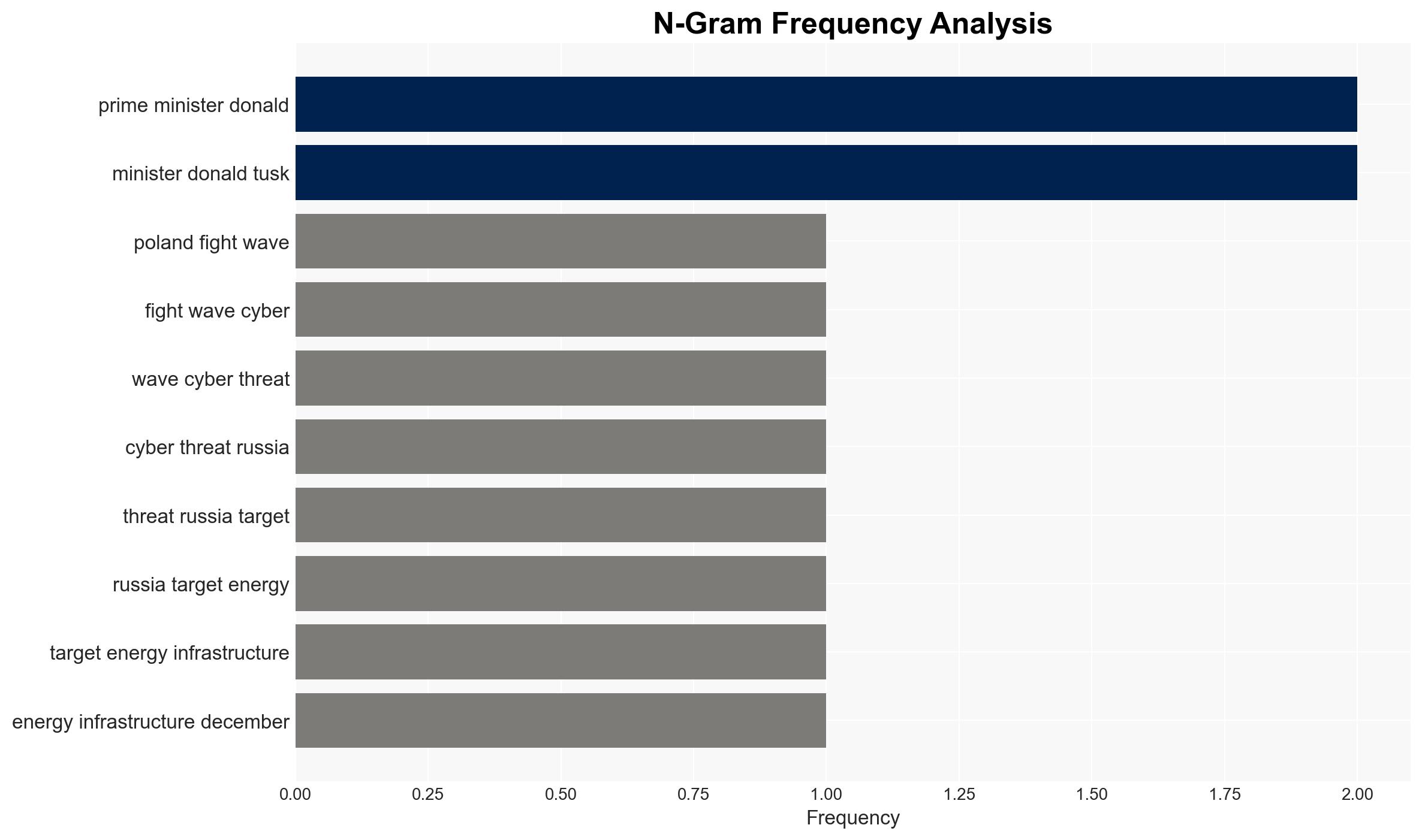
- Donald Tusk – Polish Prime Minister
- Not clearly identifiable from open sources in this snippet – Russian-linked hacker groups
- Not clearly identifiable from open sources in this snippet – Polish grid operator PSE
7. Thematic Tags
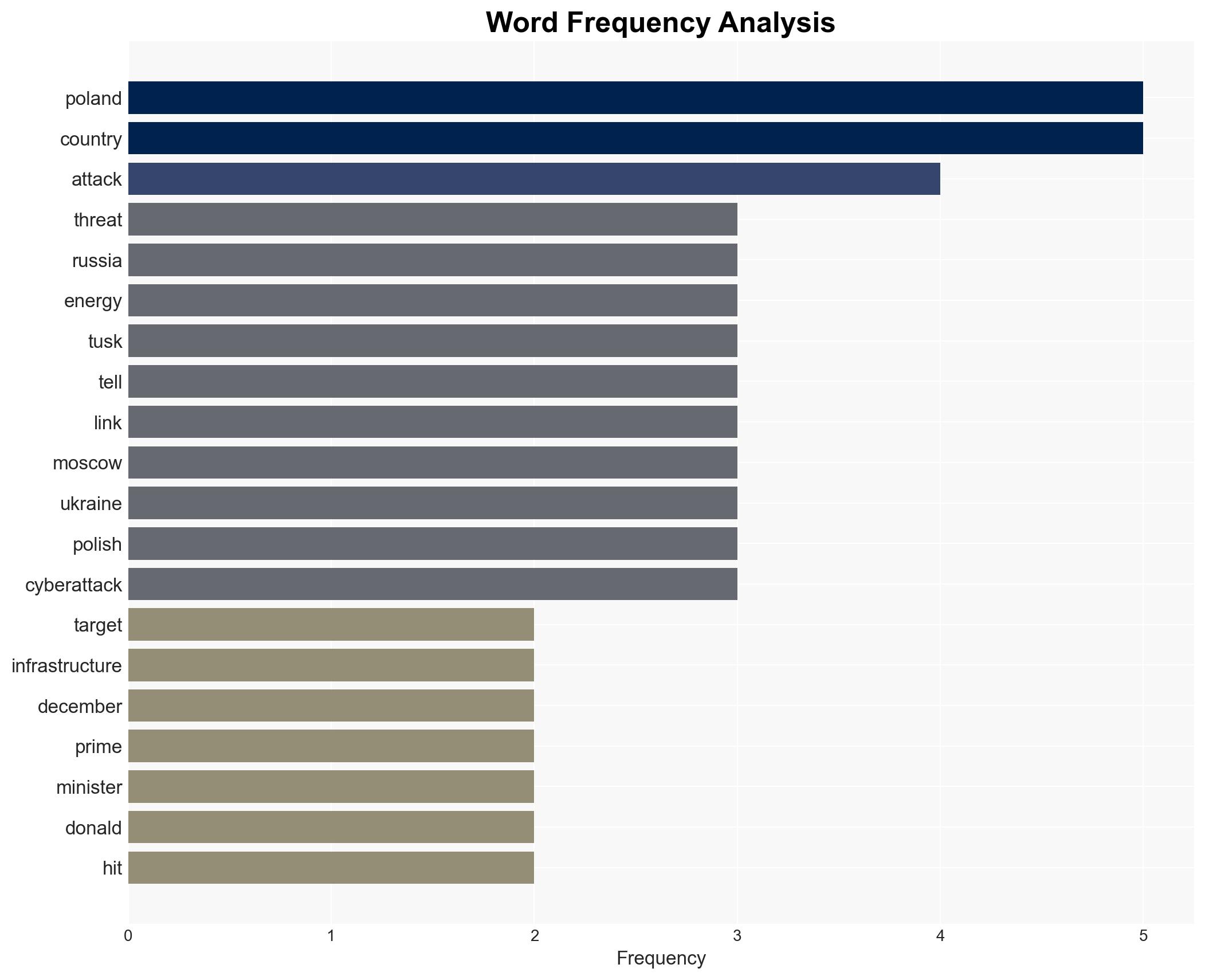
cybersecurity, hybrid warfare, NATO, Russia-Poland relations, energy infrastructure, geopolitical tension, cyber attribution
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us