China-Linked APT Targets U.S. Critical Infrastructure via Sitecore Zero-Day Exploit
Published on: 2026-01-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-Linked APT Exploits Sitecore Zero-Day in Attacks on American Critical Infrastructure
1. BLUF (Bottom Line Up Front)
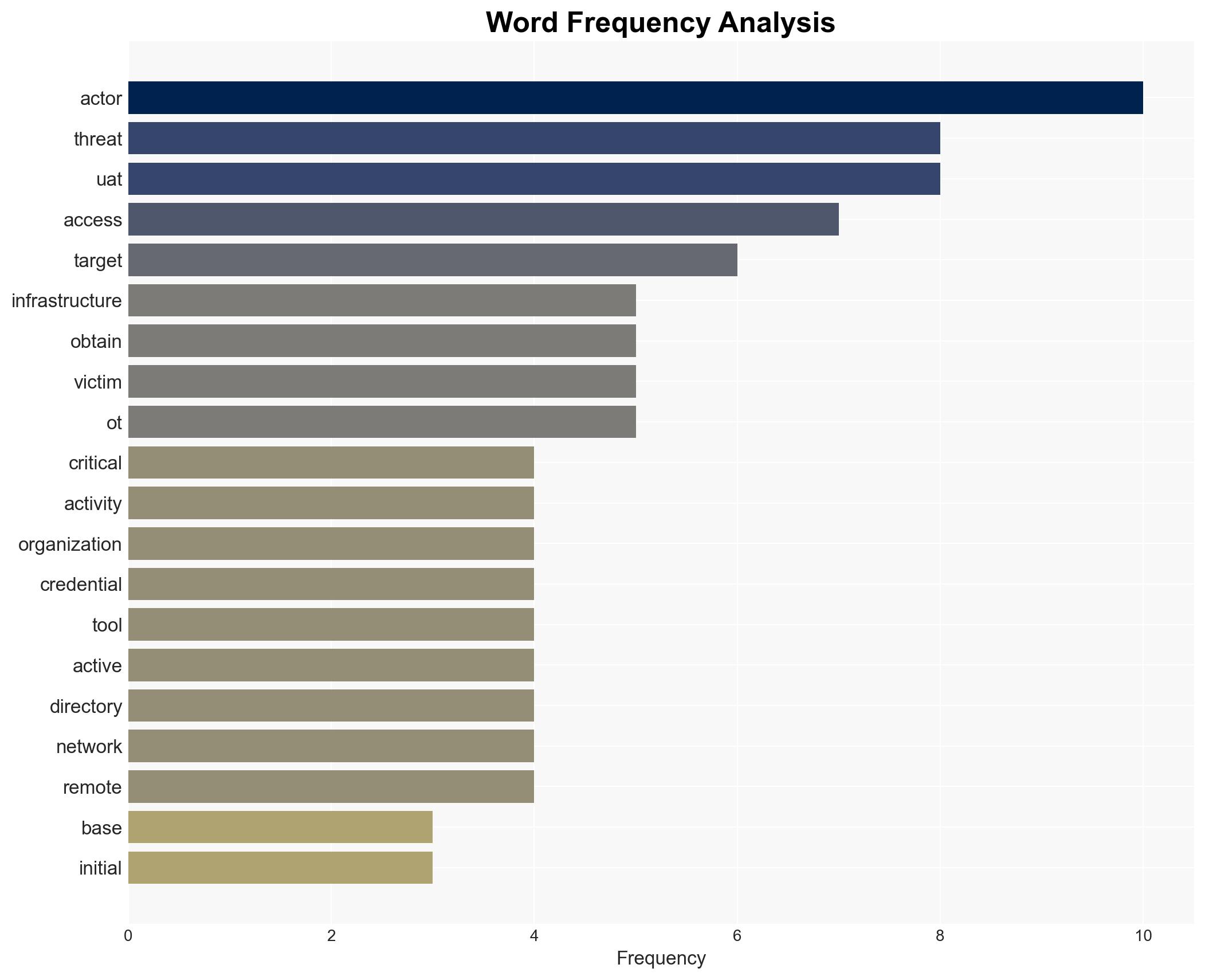
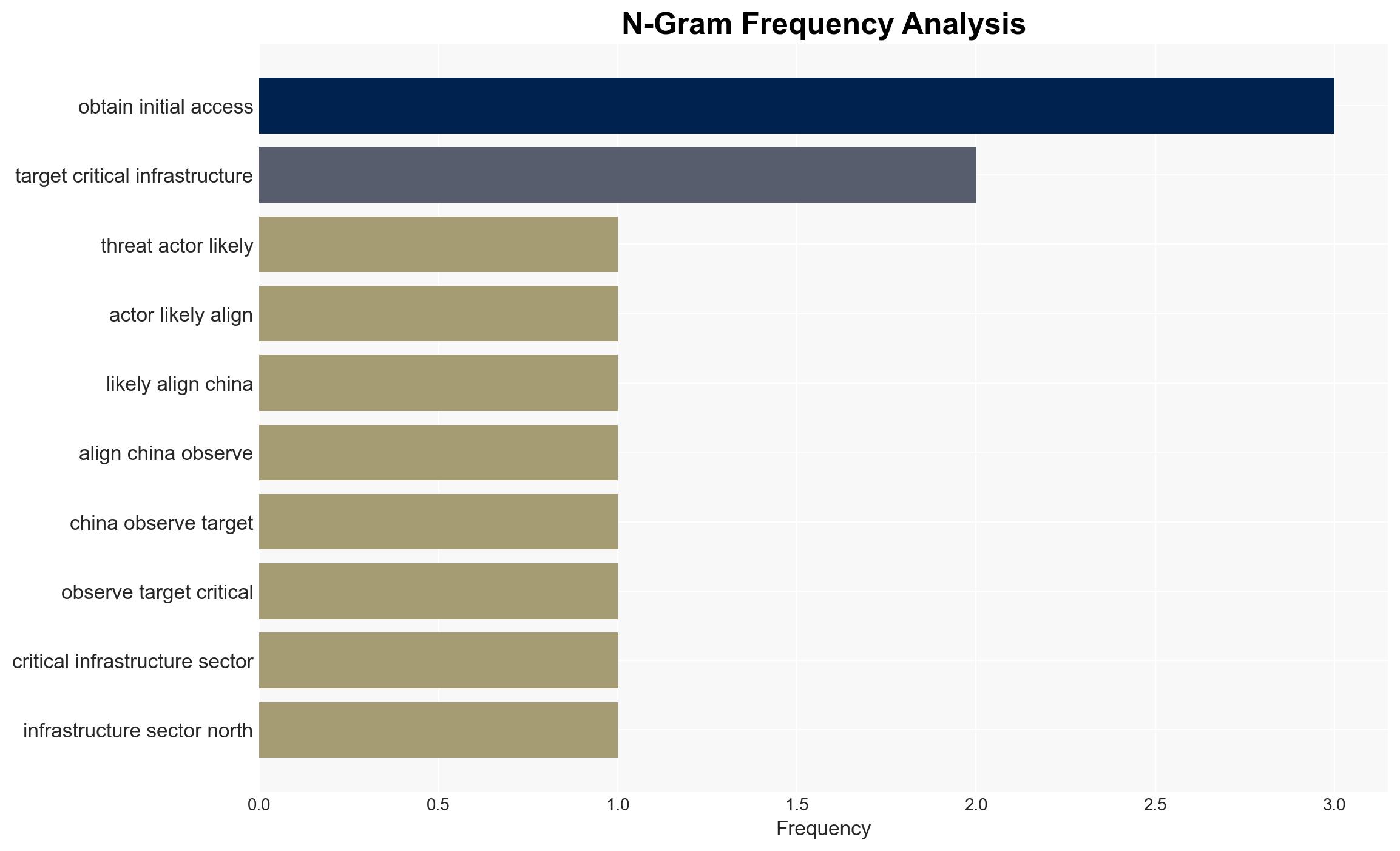
A China-linked advanced persistent threat (APT), identified as UAT-8837, is exploiting a Sitecore zero-day vulnerability to target critical infrastructure in North America. The group’s activities suggest a focus on obtaining initial access and exfiltrating sensitive information. This assessment is made with moderate confidence due to observed tactical overlaps with other known Chinese APT campaigns and the use of sophisticated tools. The affected sectors include high-value organizations within critical infrastructure domains.
2. Competing Hypotheses
- Hypothesis A: UAT-8837 is a China-nexus APT group exploiting the Sitecore zero-day vulnerability to target North American critical infrastructure. This hypothesis is supported by tactical overlaps with known Chinese APT campaigns and the use of advanced tools. However, uncertainty remains regarding the full extent of their capabilities and objectives.
- Hypothesis B: UAT-8837 may be an independent cybercriminal group using Chinese APT tactics to obfuscate their true origin. This hypothesis is less supported due to the lack of evidence indicating financial motivations typical of cybercriminals and the high level of sophistication in their operations.
- Assessment: Hypothesis A is currently better supported due to the alignment of TTPs with known Chinese APT patterns and the strategic targeting of critical infrastructure. Indicators that could shift this judgment include evidence of financial transactions or communications linking UAT-8837 to non-state actors.
3. Key Assumptions and Red Flags
- Assumptions: UAT-8837 is state-sponsored; the Sitecore zero-day was unknown to defenders prior to exploitation; the primary objective is espionage rather than disruption.
- Information Gaps: Detailed attribution of UAT-8837 to specific Chinese entities; comprehensive impact assessment on affected organizations; full scope of compromised data.
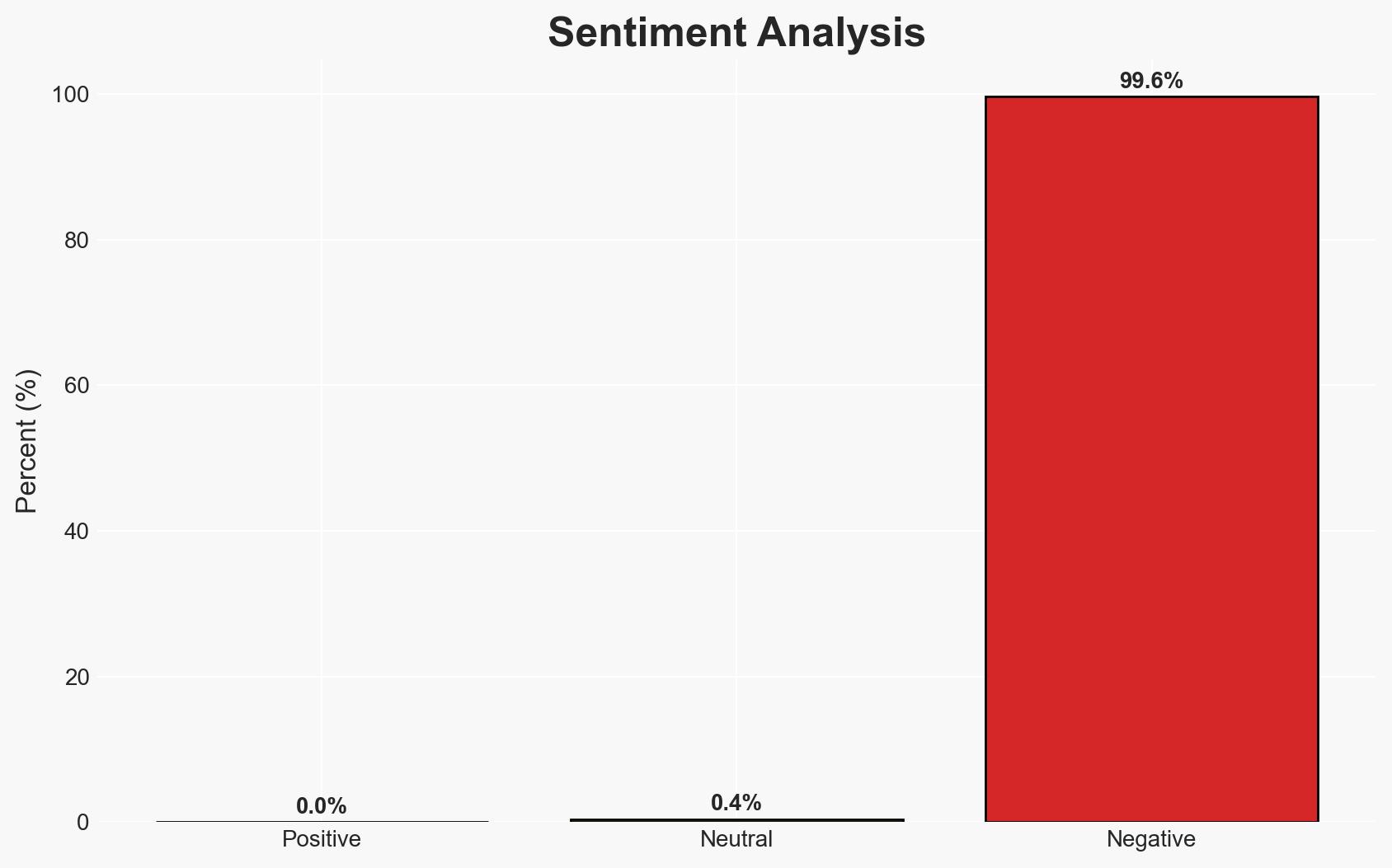
- Bias & Deception Risks: Potential confirmation bias in attributing activities to China; reliance on cybersecurity firms’ analysis which may have inherent biases; possible use of false flags by UAT-8837 to mislead attribution.
4. Implications and Strategic Risks
The exploitation of a zero-day vulnerability by a China-linked APT targeting critical infrastructure could escalate geopolitical tensions and lead to increased cyber defense measures. The ongoing threat may prompt policy changes and impact international relations.
- Political / Geopolitical: Potential diplomatic strains between China and North America; increased calls for international cyber norms and agreements.
- Security / Counter-Terrorism: Heightened alert levels in critical infrastructure sectors; potential for retaliatory cyber operations.
- Cyber / Information Space: Increased focus on zero-day vulnerability management; potential for widespread adoption of enhanced cybersecurity protocols.
- Economic / Social: Potential economic impact from disrupted services; increased public concern over cybersecurity threats.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Patch vulnerable systems; enhance monitoring of critical infrastructure networks; share threat intelligence with relevant stakeholders.
- Medium-Term Posture (1–12 months): Develop resilience measures against zero-day exploits; strengthen international partnerships for cyber defense; invest in cybersecurity training and awareness programs.
- Scenario Outlook:
- Best: Successful mitigation of vulnerabilities and improved international cyber cooperation.
- Worst: Escalation of cyber conflicts leading to significant disruptions in critical infrastructure.
- Most-Likely: Continued low-level cyber espionage activities with periodic disruptions.
6. Key Individuals and Entities
- UAT-8837 (China-linked APT group)
- Cisco Talos (Cybersecurity firm)
- Sitecore (Software company)
- Mandiant (Cybersecurity firm)
- Asheer Malhotra, Vitor Ventura, Brandon White (Researchers)
7. Thematic Tags
cybersecurity, cyber-espionage, critical infrastructure, zero-day vulnerability, China-linked APT, information security, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us