Hacker Breaches Therapy Database, Exposes Personal Data of 33,000 Patients for Ransom
Published on: 2026-01-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: A faceless hacker stole my therapy notes now my deepest secrets are online forever
1. BLUF (Bottom Line Up Front)
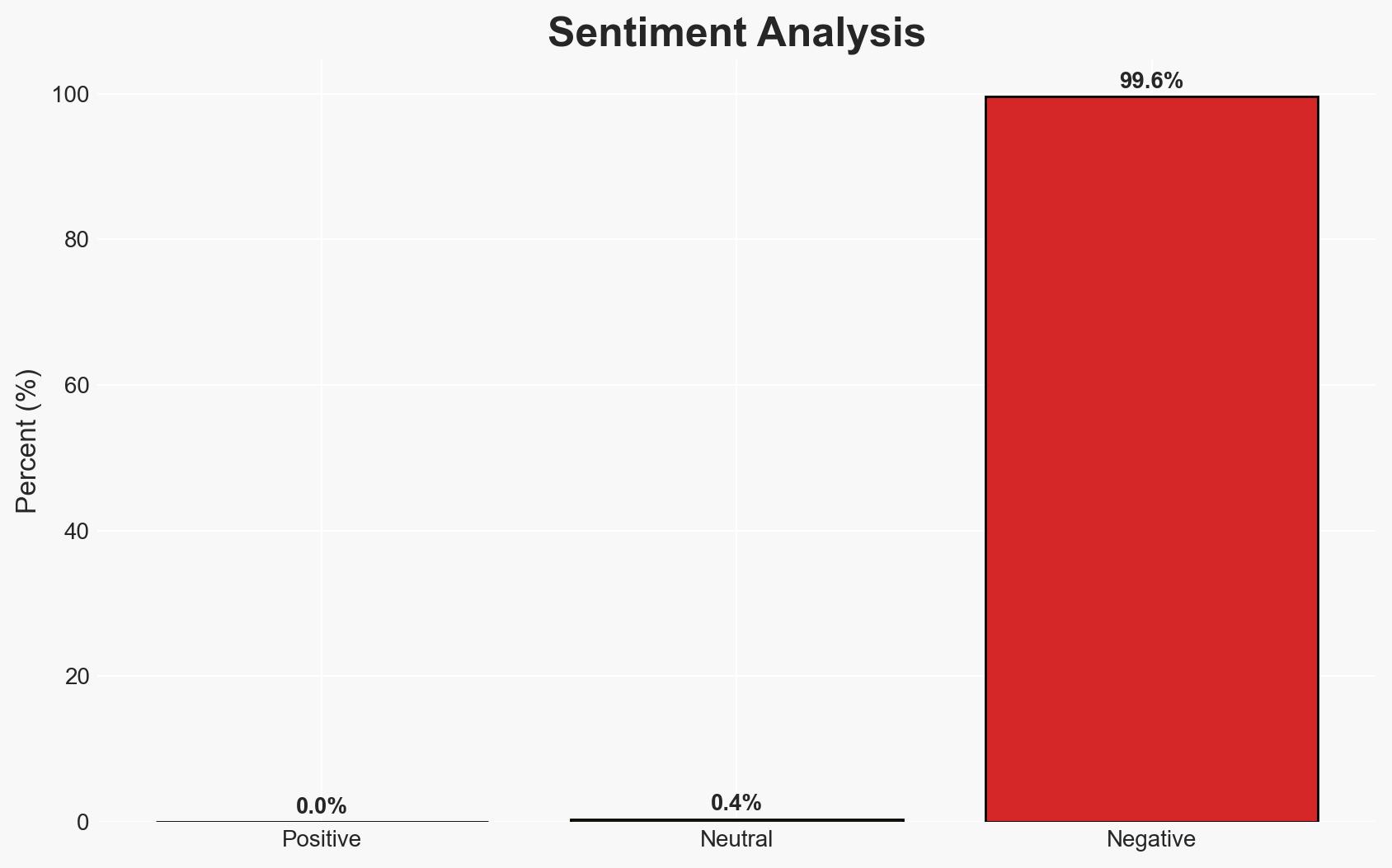
The breach of Vastaamo’s patient database, affecting 33,000 individuals, represents a significant cyber incident with implications for personal privacy and national security in Finland. The most likely hypothesis is that the attack was financially motivated, targeting sensitive personal data for extortion. This incident highlights vulnerabilities in data protection and has led to widespread public distress. Overall confidence in this assessment is moderate due to limited information on the perpetrator’s identity and motives.
2. Competing Hypotheses
- Hypothesis A: The hacker’s primary motivation was financial gain through extortion. Supporting evidence includes the demand for bitcoin payments and the threat to publish sensitive data. Contradicting evidence is the early release of data on the dark web, which reduces potential financial returns. Key uncertainties include the hacker’s identity and whether financial gain was the sole motive.
- Hypothesis B: The attack was intended to cause social disruption or damage Vastaamo’s reputation. This is supported by the public release of data, which maximizes social impact. However, the extortion demands suggest financial motives were also significant.
- Assessment: Hypothesis A is currently better supported due to the explicit financial demands. Key indicators that could shift this judgment include evidence of state sponsorship or ideological motives.
3. Key Assumptions and Red Flags
- Assumptions: The hacker acted independently without state sponsorship; Vastaamo’s data security measures were inadequate; the hacker’s primary goal was financial extortion.
- Information Gaps: The identity and location of the hacker; the full extent of data distribution; potential state or non-state actor involvement.
- Bias & Deception Risks: Confirmation bias towards financial motives; potential deception by the hacker regarding their true intentions.
4. Implications and Strategic Risks
This breach could lead to increased scrutiny of data protection laws and practices in Finland and beyond. It may also inspire similar attacks on other sensitive data repositories.
- Political / Geopolitical: Potential for legislative changes and international cooperation on cybercrime prevention.
- Security / Counter-Terrorism: Increased awareness and preparedness for data-related extortion threats.
- Cyber / Information Space: Highlighted vulnerabilities in healthcare data protection; potential for copycat attacks.
- Economic / Social: Public distrust in digital services; psychological impact on affected individuals.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web for data circulation; support affected individuals with psychological and legal assistance.
- Medium-Term Posture (1–12 months): Strengthen data protection regulations; foster public-private partnerships for cybersecurity resilience.
- Scenario Outlook:
- Best: Rapid identification and prosecution of the hacker, leading to improved data security practices.
- Worst: Continued data circulation causing long-term harm to individuals and institutions.
- Most-Likely: Incremental improvements in data security with ongoing challenges in mitigating data breach impacts.
6. Key Individuals and Entities
- Vastaamo (Finnish psychotherapy service provider)
- Meri-Tuuli Auer (affected individual)
- Not clearly identifiable from open sources in this snippet (hacker)
7. Thematic Tags
cybersecurity, data breach, extortion, privacy, Finland, healthcare data, national security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us