Chinese-linked APT UAT-8837 targets North American critical infrastructure since 2022, using advanced tactics.
Published on: 2026-01-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-linked APT UAT-8837 targets North American critical infrastructure
1. BLUF (Bottom Line Up Front)
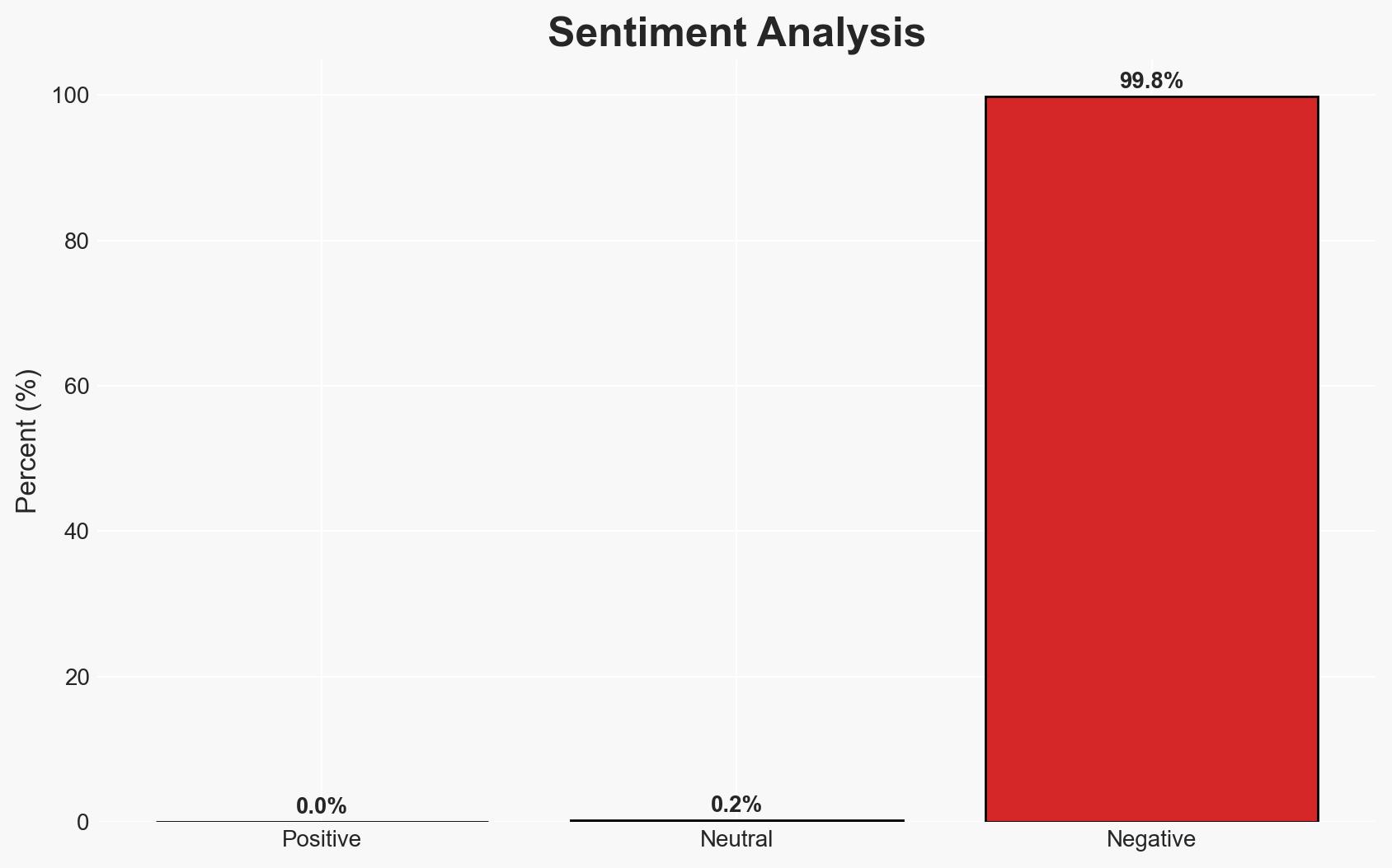
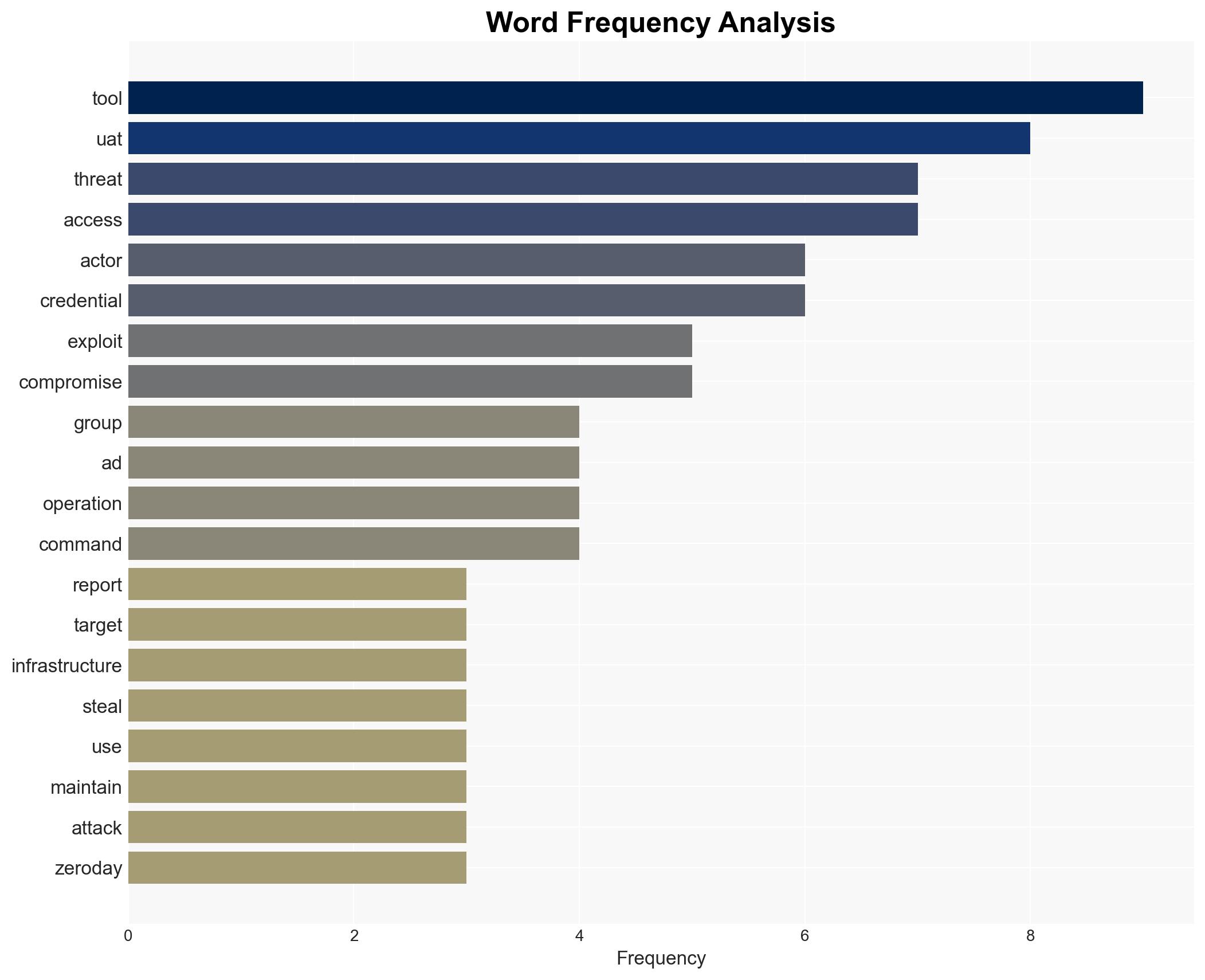
The threat group UAT-8837, likely linked to China, is targeting North American critical infrastructure using advanced cyber techniques. The group’s operations suggest a strategic focus on disrupting or gaining intelligence on critical sectors. This assessment is made with moderate confidence due to the overlap in tactics, techniques, and procedures (TTPs) with other known China-linked threat actors.
2. Competing Hypotheses
- Hypothesis A: UAT-8837 is a China-nexus APT group specifically targeting North American critical infrastructure to gather intelligence or disrupt operations. This is supported by TTP overlaps with known China-linked actors and the use of sophisticated tools and zero-day exploits. However, the sporadic nature of targeting introduces uncertainty.
- Hypothesis B: UAT-8837 is an independent cybercriminal group using similar TTPs to China-linked actors to mask its true origins and intentions. This is less supported due to the strategic nature of the targets and the complexity of the operations, which are more indicative of state-sponsored activity.
- Assessment: Hypothesis A is currently better supported due to the alignment of TTPs with known China-linked APTs and the strategic targeting of critical infrastructure. Indicators such as further attribution evidence or shifts in targeting patterns could alter this judgment.
3. Key Assumptions and Red Flags
- Assumptions: UAT-8837 is state-sponsored; the group’s primary objective is intelligence collection or disruption; the tools and exploits used are indicative of advanced capabilities.
- Information Gaps: Detailed attribution evidence linking UAT-8837 directly to Chinese state entities; comprehensive understanding of the group’s long-term objectives and targets.
- Bias & Deception Risks: Potential confirmation bias in linking TTPs to China; risk of deception by the threat actor to misattribute activities.
4. Implications and Strategic Risks
The activities of UAT-8837 could lead to increased geopolitical tensions and necessitate enhanced cybersecurity measures across critical infrastructure sectors. The group’s operations may evolve, potentially expanding to other regions or sectors.
- Political / Geopolitical: Potential for diplomatic friction between China and North American countries, especially if attribution is confirmed.
- Security / Counter-Terrorism: Increased threat to critical infrastructure, necessitating heightened security postures and inter-agency cooperation.
- Cyber / Information Space: Escalation in cyber defense measures and potential retaliatory cyber operations; increased focus on securing zero-day vulnerabilities.
- Economic / Social: Potential economic impacts from disrupted infrastructure services; public concern over cybersecurity vulnerabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; share threat intelligence with relevant sectors; patch known vulnerabilities, especially zero-day exploits.
- Medium-Term Posture (1–12 months): Develop resilience measures and incident response plans; strengthen international cybersecurity partnerships; invest in advanced threat detection capabilities.
- Scenario Outlook:
- Best: Successful attribution and diplomatic resolution reduce threat activity.
- Worst: Escalation of cyber operations leads to significant infrastructure disruptions.
- Most-Likely: Continued sporadic attacks with gradual improvements in defensive measures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, critical infrastructure, China, advanced persistent threat, zero-day exploits, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us