Preventative Measures to Mitigate Risks of the ManageMyHealth Cyber Attack
Published on: 2026-01-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Five ways the ManageMyHealth cyber attack could have been avoided
1. BLUF (Bottom Line Up Front)
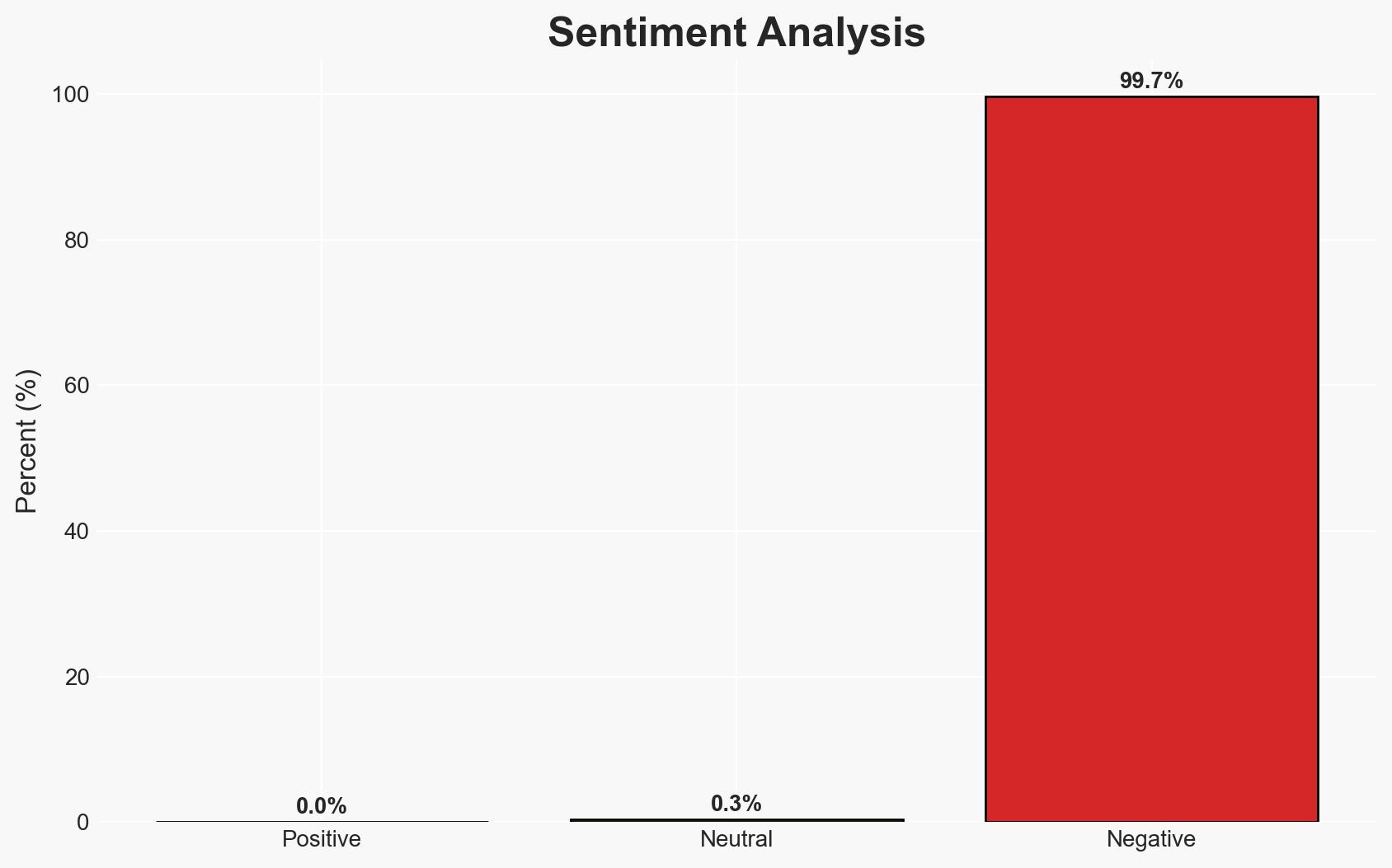
The ManageMyHealth cyber attack exposed significant vulnerabilities in handling sensitive medical data, affecting approximately 127,000 individuals. The most likely hypothesis is that inadequate security measures, such as the lack of mandatory two-factor authentication, facilitated the breach. This incident highlights the need for improved cybersecurity protocols and regulatory frameworks. Overall confidence in this assessment is moderate due to limited information on the breach’s technical specifics.
2. Competing Hypotheses
- Hypothesis A: The breach occurred due to inadequate cybersecurity measures, particularly the absence of mandatory two-factor authentication. Supporting evidence includes expert criticism of ManageMyHealth’s security practices. However, the specific technical vulnerabilities exploited remain unclear.
- Hypothesis B: The breach was primarily due to sophisticated cybercriminal tactics, independent of ManageMyHealth’s security posture. While the hacker’s actions, such as resetting ransom deadlines, suggest advanced tactics, there is insufficient evidence to prioritize this over security lapses.
- Assessment: Hypothesis A is currently better supported due to expert consensus on the need for stronger security measures. Key indicators that could shift this judgment include detailed forensic analysis revealing advanced attack methods.
3. Key Assumptions and Red Flags
- Assumptions: The breach was facilitated by inadequate security measures; the hacker’s claims about the number of files are accurate; current penalties are insufficient deterrents.
- Information Gaps: Specific technical details of the breach; the full extent of data compromised; the hacker’s identity and capabilities.
- Bias & Deception Risks: Potential bias from cybersecurity experts advocating for stronger measures; possible deception by the hacker regarding data volume and ransom demands.
4. Implications and Strategic Risks
This development underscores vulnerabilities in healthcare cybersecurity, potentially leading to increased regulatory scrutiny and demands for enhanced security protocols.
- Political / Geopolitical: Potential for increased government intervention and regulatory changes in healthcare data protection.
- Security / Counter-Terrorism: Heightened awareness of cyber threats to critical infrastructure, possibly leading to increased security measures.
- Cyber / Information Space: Likely escalation in cyber defense initiatives and public awareness campaigns on data protection.
- Economic / Social: Potential loss of public trust in digital health services, impacting user engagement and healthcare delivery.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement mandatory two-factor authentication; conduct a comprehensive security audit; enhance incident response protocols.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in staff training and awareness; advocate for stronger regulatory frameworks.
- Scenario Outlook:
- Best: Rapid implementation of security measures restores public trust.
- Worst: Further breaches occur, leading to significant regulatory penalties and loss of user base.
- Most-Likely: Gradual improvements in security and regulatory compliance, with periodic challenges.
6. Key Individuals and Entities
- ManageMyHealth
- Canopy Healthcare
- Health Minister Simeon Brown
- National Cyber Security Centre
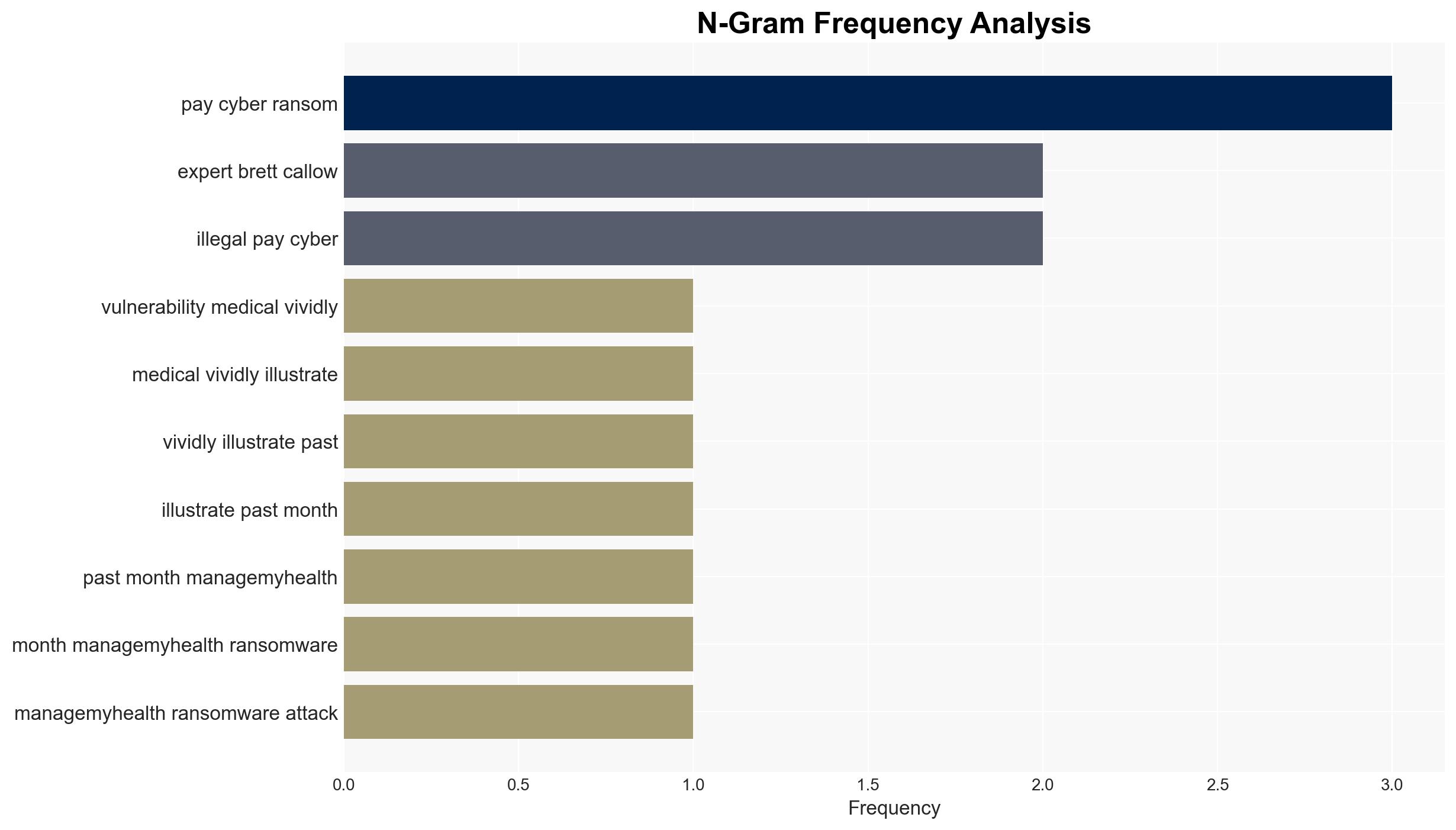
- Security expert Brett Callow
- Democracy Project director Dr Bryce Edwards
- Simply Privacy principal Frith Tweedie
7. Thematic Tags
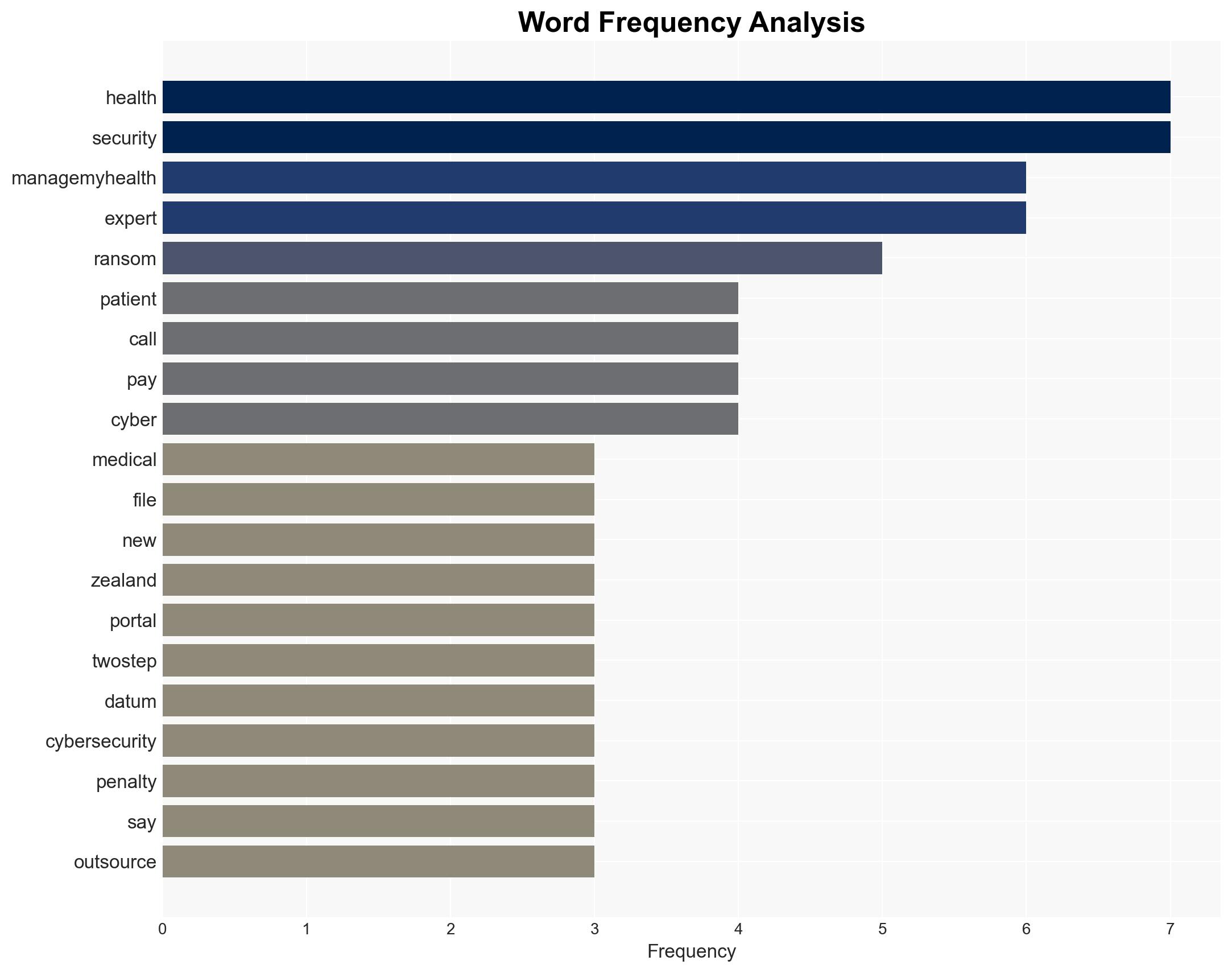
cybersecurity, healthcare data breach, ransomware, regulatory compliance, data protection, public trust, digital health
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us