Understanding Ransomware: A Growing Threat Impacting Organizations Globally
Published on: 2026-01-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware what it is and why its your problem
1. BLUF (Bottom Line Up Front)
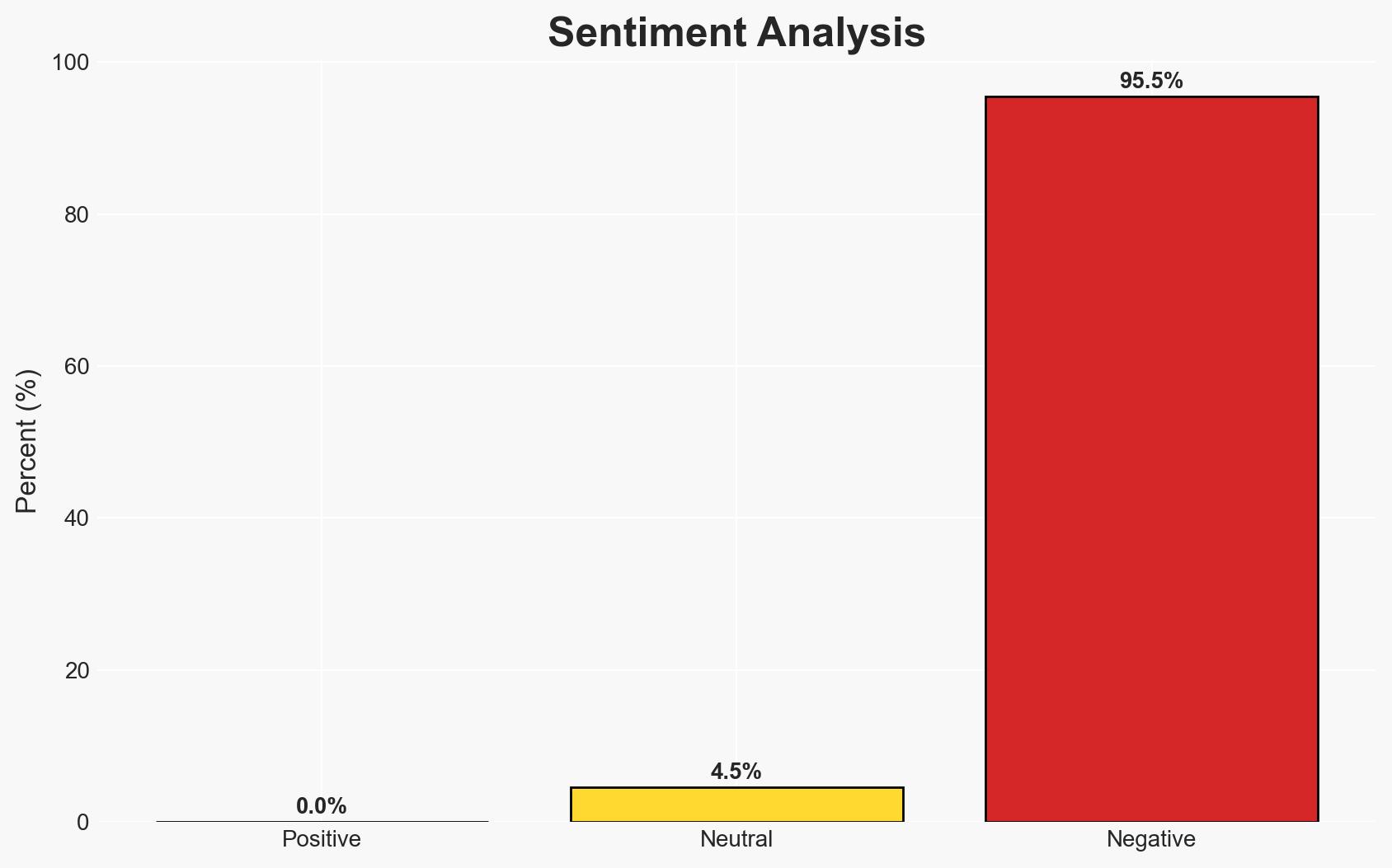
Ransomware remains a significant threat to organizations globally, with Africa emerging as a hotspot due to cybersecurity gaps. The most likely hypothesis is that ransomware attacks will continue to rise in regions with inadequate cybersecurity infrastructure, affecting critical sectors such as healthcare and finance. Overall confidence in this assessment is moderate, given the current data limitations.
2. Competing Hypotheses
- Hypothesis A: Ransomware attacks are primarily driven by financial motives and will continue to target regions with weak cybersecurity defenses. This is supported by the high incidence of attacks in Africa and the willingness of victims to pay ransoms. However, the lack of detailed data on attacker motivations and tactics presents uncertainties.
- Hypothesis B: Ransomware attacks are diversifying beyond financial motives, potentially being used for geopolitical or strategic disruptions. While there is limited evidence in the snippet to support this, the targeting of critical infrastructure could suggest broader objectives.
- Assessment: Hypothesis A is currently better supported due to the evidence of financial gain being a primary driver and the observed patterns of attack in regions with cybersecurity weaknesses. Indicators such as increased targeting of critical infrastructure or evidence of state-sponsored involvement could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations in Africa lack sufficient cybersecurity resources; ransomware attackers are primarily motivated by financial gain; the current trend of increasing attacks will continue.
- Information Gaps: Detailed data on the specific methods and origins of ransomware attacks in Africa; comprehensive statistics on the economic impact of these attacks.
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests; lack of independent verification of reported attack figures.
4. Implications and Strategic Risks
The continued prevalence of ransomware attacks could exacerbate existing vulnerabilities in critical infrastructure, leading to broader systemic risks.
- Political / Geopolitical: Increased pressure on governments to enhance cybersecurity measures and international cooperation.
- Security / Counter-Terrorism: Potential for ransomware to be used as a tool for broader cyber warfare or terrorism-related activities.
- Cyber / Information Space: Escalation in cyber defense measures and potential for increased cyber insurance costs.
- Economic / Social: Disruption to essential services could lead to economic instability and public unrest.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of ransomware threats, increase awareness campaigns, and encourage reporting of incidents.
- Medium-Term Posture (1–12 months): Develop partnerships for cybersecurity capacity building, invest in infrastructure resilience, and establish incident response protocols.
- Scenario Outlook:
- Best: Significant reduction in attacks due to improved defenses and international cooperation.
- Worst: Escalation in attacks leading to widespread disruption of critical services.
- Most-Likely: Continued increase in attacks with gradual improvements in defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
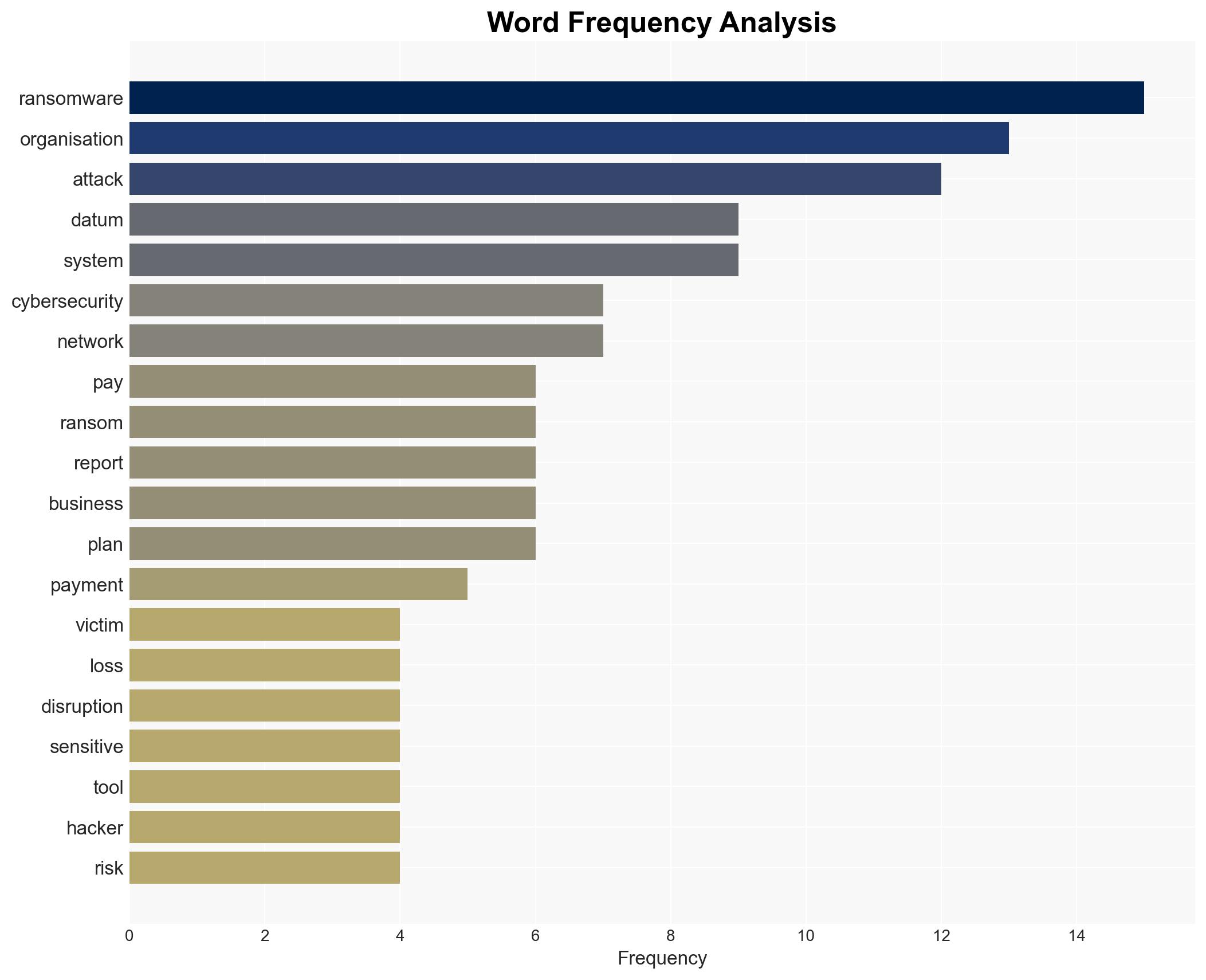
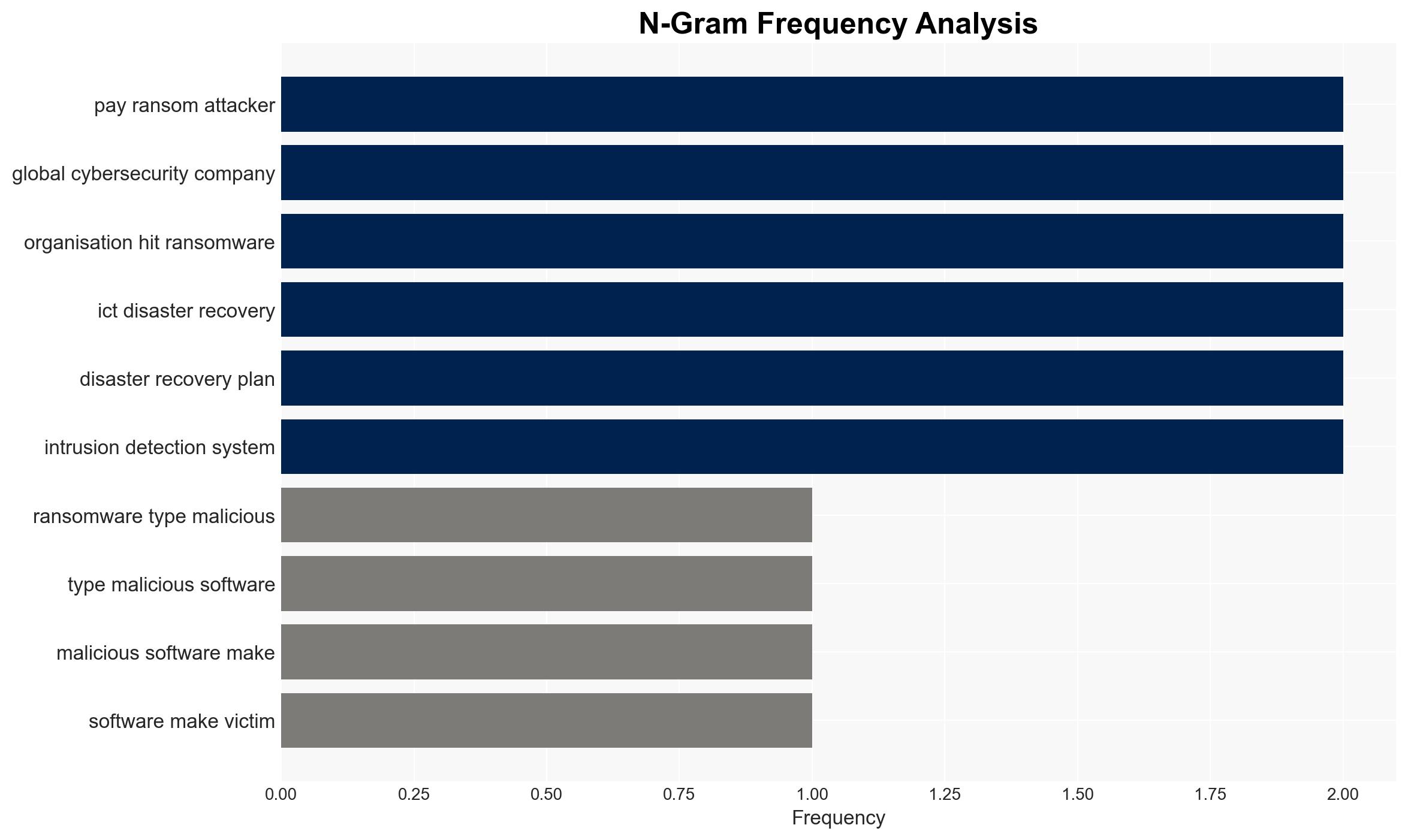
cybersecurity, ransomware, Africa, critical infrastructure, financial crime, cyber defense, information technology
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us