Security Researchers Uncover XSS Flaw in StealC Infostealer, Revealing Key Operational Insights
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Researchers Exploit Bug in StealC Infostealer to Collect Evidence
1. BLUF (Bottom Line Up Front)
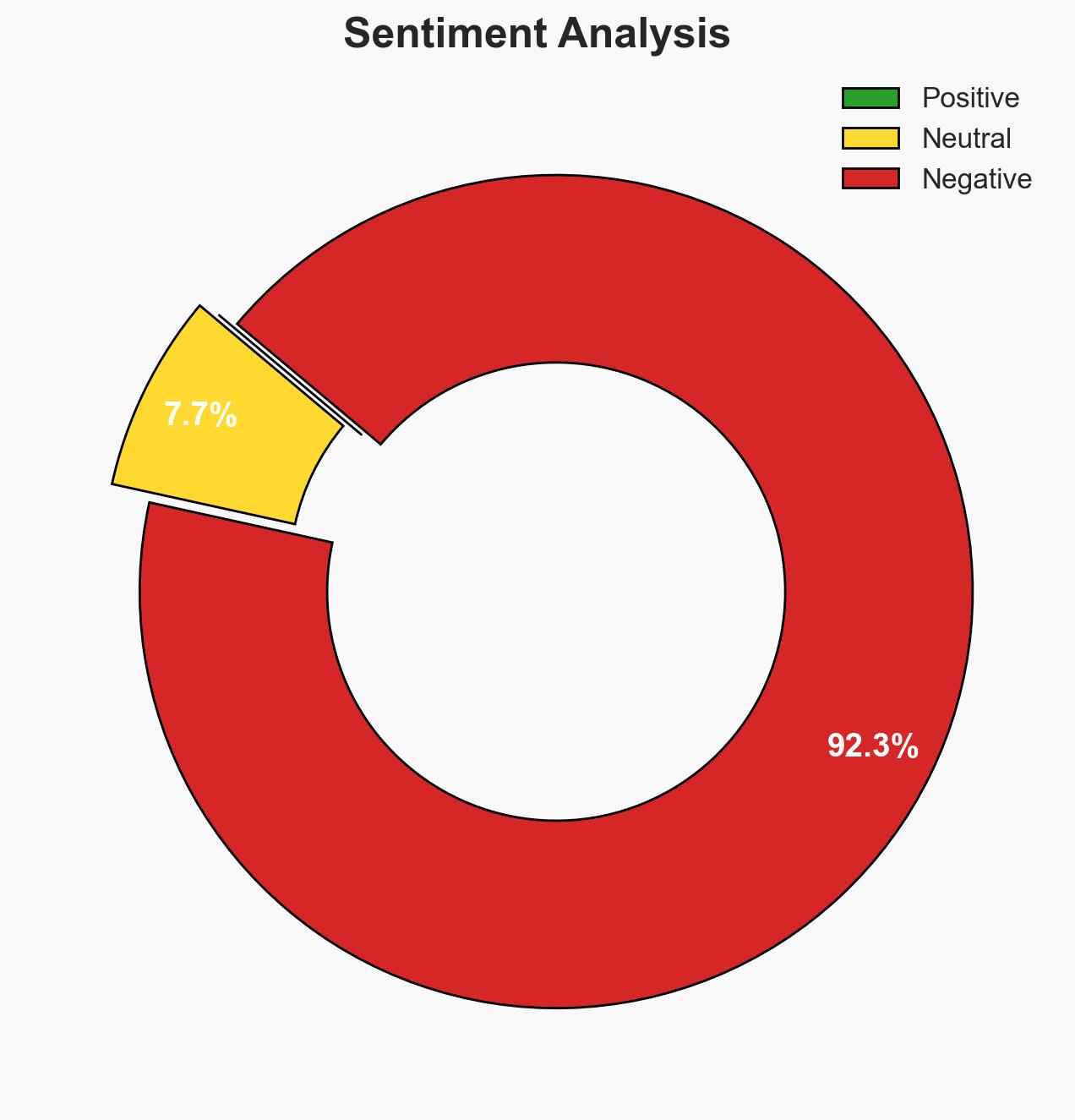
Security researchers have exploited a vulnerability in the StealC infostealer, revealing significant operational details about its users, notably a threat actor named “YouTubeTA.” This development underscores the potential for exploiting malware vulnerabilities to gather intelligence on cybercriminal activities. The most likely hypothesis is that the StealC group has operational weaknesses that can be further exploited. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The StealC group has significant operational weaknesses, as evidenced by the XSS vulnerability, which can be exploited to gather intelligence on its users. Supporting evidence includes the successful exploitation of the vulnerability by researchers, revealing detailed information about “YouTubeTA.” However, the extent of these weaknesses across the entire StealC operation remains uncertain.
- Hypothesis B: The vulnerability exploited by researchers is an isolated incident, and the StealC group generally maintains robust operational security. This hypothesis is contradicted by the successful exploitation and the lack of basic security measures, such as cookie protection, but cannot be entirely ruled out without broader evidence.
- Assessment: Hypothesis A is currently better supported due to the direct evidence of the vulnerability and the intelligence gathered. Indicators that could shift this judgment include further evidence of vulnerabilities in other parts of the StealC operation or improvements in their security practices.
3. Key Assumptions and Red Flags
- Assumptions: The StealC vulnerability is representative of broader operational weaknesses; “YouTubeTA” is a significant actor within the StealC network; the information gathered by researchers is accurate and comprehensive.
- Information Gaps: The full scope of StealC’s operational security measures; potential vulnerabilities in other malware-as-a-service offerings; comprehensive data on the impact of StealC’s operations.
- Bias & Deception Risks: Potential bias in the researchers’ analysis due to their focus on a single vulnerability; risk of deception by StealC operators to mislead researchers about their capabilities and operations.
4. Implications and Strategic Risks
This development highlights the potential for exploiting cybercriminal vulnerabilities to gather intelligence, which could lead to increased law enforcement actions and policy changes targeting malware-as-a-service operations.
- Political / Geopolitical: Potential for increased international cooperation in cybercrime investigations, particularly involving Eastern European actors.
- Security / Counter-Terrorism: Enhanced ability to disrupt cybercriminal networks by exploiting operational weaknesses.
- Cyber / Information Space: Possible escalation in the arms race between cybercriminals and security researchers, with criminals improving their security measures.
- Economic / Social: Potential economic impact on businesses and individuals targeted by infostealers, leading to increased demand for cybersecurity solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for further vulnerabilities in StealC and similar malware; engage with cybersecurity firms to share intelligence and coordinate actions.
- Medium-Term Posture (1–12 months): Develop partnerships with international law enforcement to address cross-border cybercrime; invest in research to identify and exploit vulnerabilities in malware.
- Scenario Outlook: Best: Significant disruption of StealC operations through continued exploitation of vulnerabilities. Worst: StealC operators enhance their security, reducing intelligence-gathering opportunities. Most-Likely: Continued identification of vulnerabilities with incremental disruptions to StealC operations.
6. Key Individuals and Entities
- Ari Novick, CyberArk
- YouTubeTA, StealC user
- StealC developers, Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
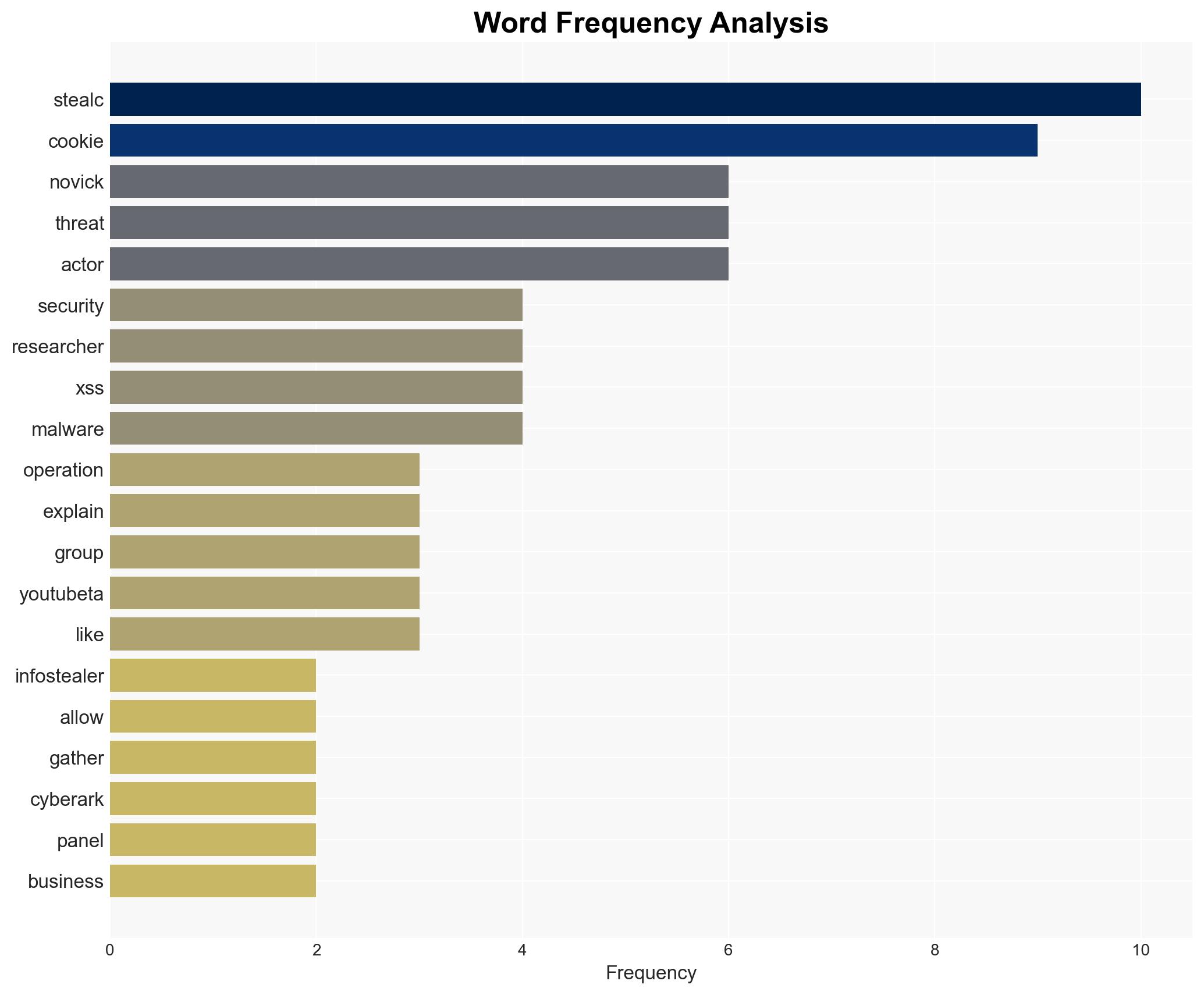
cybersecurity, malware-as-a-service, vulnerability exploitation, cybercrime, operational security, intelligence gathering, Eastern Europe
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us