Cyber Threats Loom as Milan Cortina 2026 Olympics Draws Global Attention and Increased Network Vulnerabilities
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: When the Olympics connect everything attackers pay attention
1. BLUF (Bottom Line Up Front)
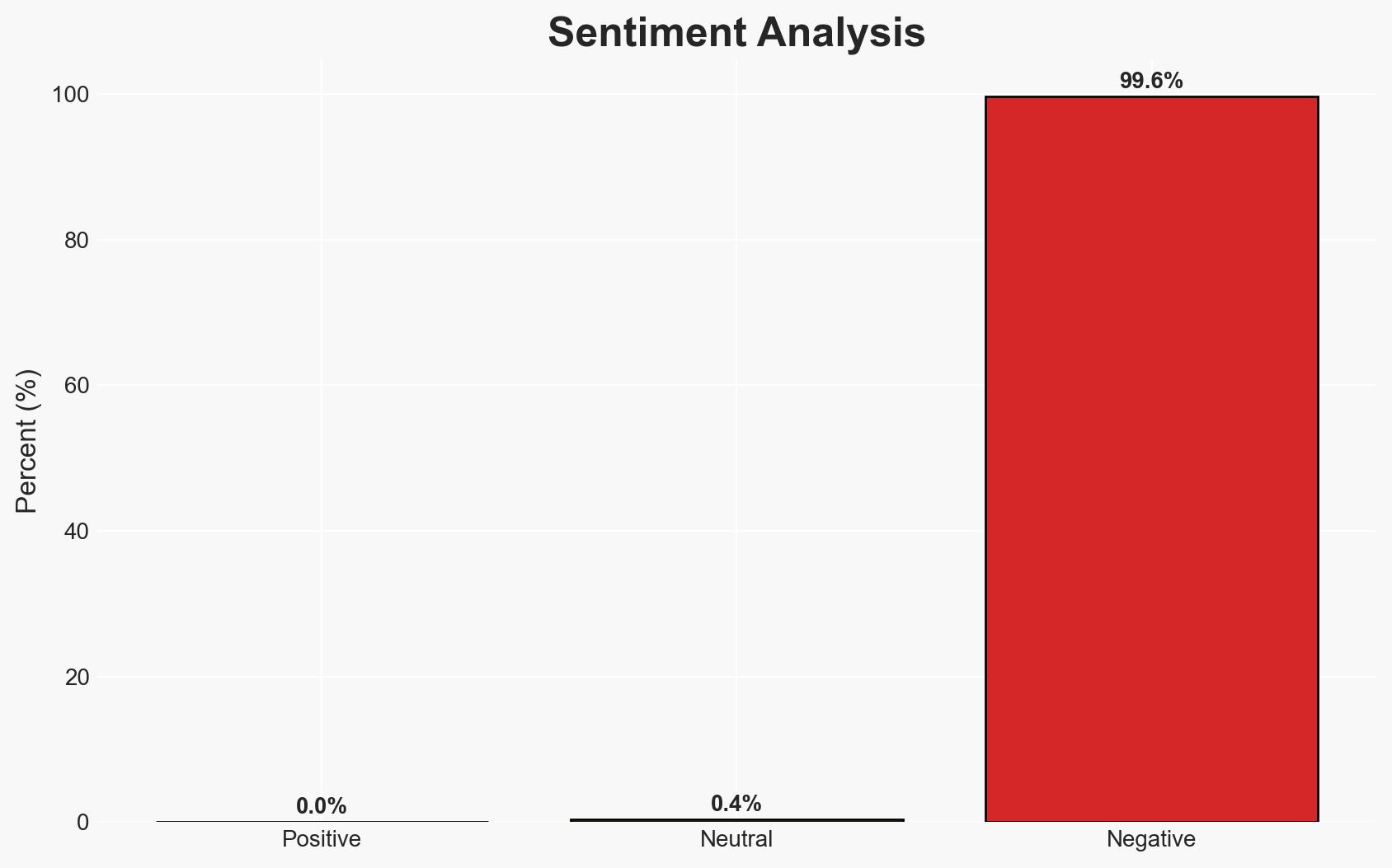
The Milan Cortina 2026 Winter Olympic Games present a significant cyber threat environment due to increased network complexity and high-profile targets. Cyber threat actors are likely to exploit these conditions for financial gain, intelligence collection, and public disruption. The most likely hypothesis is that financially motivated ransomware attacks will pose the greatest immediate threat. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Cyber threat actors will primarily focus on financially motivated attacks, such as ransomware and scams, due to the high volume of transactions and potential for quick financial gain. Supporting evidence includes historical patterns of ransomware targeting event infrastructure and the report’s emphasis on financial incentives. Key uncertainties include the effectiveness of existing cybersecurity measures and the adaptability of threat actors.
- Hypothesis B: Nation-state actors will prioritize intelligence collection and long-term access, leveraging the presence of high-profile individuals and shared infrastructure. This is supported by past espionage activities at similar events and the report’s mention of phishing and custom tooling. However, this hypothesis is less supported by the immediate financial incentives present.
- Assessment: Hypothesis A is currently better supported due to the immediate and tangible financial incentives for ransomware groups, as well as historical precedence. Indicators that could shift this judgment include increased detection of sophisticated espionage tools or a rise in geopolitical tensions involving participating nations.
3. Key Assumptions and Red Flags
- Assumptions: The complexity of the event’s digital infrastructure will remain a vulnerability; existing cybersecurity measures may not be fully effective; threat actors will prioritize targets with the highest financial return; geopolitical tensions will not significantly escalate before the event.
- Information Gaps: Detailed cybersecurity readiness of the event’s infrastructure; specific capabilities and intentions of identified threat groups; effectiveness of international cooperation in cybersecurity for the event.
- Bias & Deception Risks: Potential bias in threat reporting due to commercial interests of cybersecurity firms; risk of underestimating nation-state capabilities due to focus on financially motivated actors; possible deception by threat actors to mask true intentions.
4. Implications and Strategic Risks
The cyber threat landscape surrounding the Milan Cortina 2026 Winter Olympic Games could evolve to impact broader geopolitical and economic dynamics. The event’s digital vulnerabilities may serve as a catalyst for increased international cooperation in cybersecurity or, conversely, exacerbate tensions if attributed attacks occur.
- Political / Geopolitical: Potential for diplomatic fallout if cyber attacks are attributed to specific nation-states, leading to increased geopolitical tensions.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation to protect critical infrastructure and prevent potential physical security breaches.
- Cyber / Information Space: Increased cyber defense measures and information sharing among participating nations; potential for misinformation campaigns targeting public perception of the event’s security.
- Economic / Social: Disruption of event operations could lead to significant economic losses and damage to the host nation’s reputation; potential for public unrest if critical services are impacted.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of event-related digital infrastructure; conduct tabletop exercises simulating ransomware and phishing attacks; increase public awareness campaigns on cyber hygiene for attendees.
- Medium-Term Posture (1–12 months): Develop resilience measures, including backup systems and rapid response teams; strengthen partnerships with international cybersecurity agencies; invest in advanced threat detection capabilities.
- Scenario Outlook:
- Best Case: Effective cybersecurity measures prevent major incidents, enhancing international cooperation (trigger: successful pre-event security assessments).
- Worst Case: Significant cyber attack disrupts the Games, leading to geopolitical tensions (trigger: detection of sophisticated nation-state malware).
- Most-Likely: Isolated ransomware incidents occur, with limited impact due to rapid response (trigger: early detection of ransomware campaigns).
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, espionage, international cooperation, geopolitical tensions, cyber hygiene, critical infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us