Ingram Micro reveals July ransomware attack compromised data of over 42,500 employees
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ingram Micro admits summer ransomware raid exposed thousands of staff records
1. BLUF (Bottom Line Up Front)
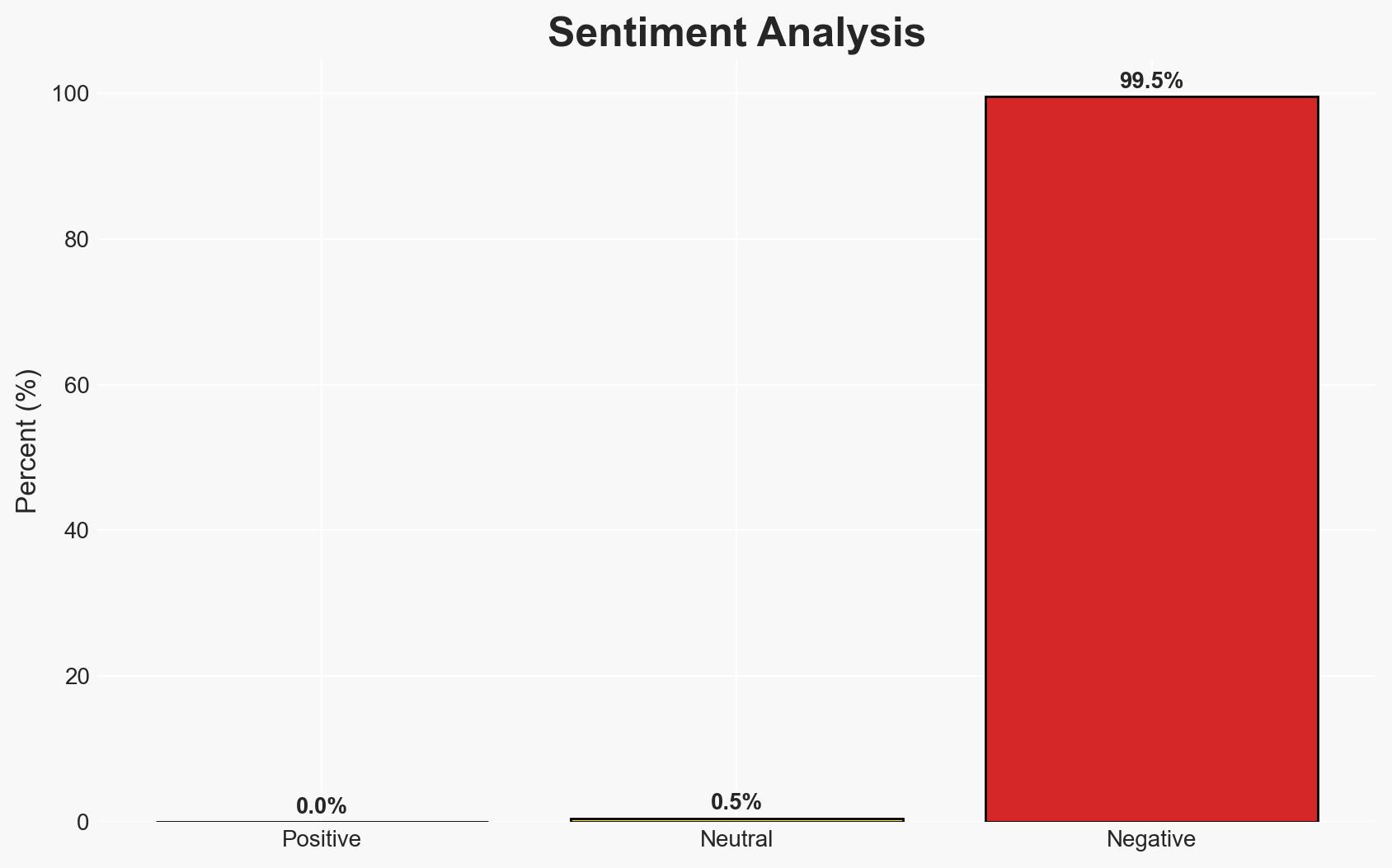
Ingram Micro experienced a significant ransomware attack in July 2025, compromising the personal data of over 42,000 employees. The attack, attributed to the SafePay group, resulted in operational disruptions and potential financial losses. The most likely hypothesis is that the attack was financially motivated. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack was primarily financially motivated, with SafePay seeking ransom payment. This is supported by the ransom demand and the group’s history of similar attacks. However, the non-functional data leak link raises questions about their true intent.
- Hypothesis B: The attack may have been a cover for a more strategic data exfiltration operation, potentially involving espionage. The rapid detection and containment by Ingram Micro could have limited the attackers’ objectives, but the lack of a working data leak link could suggest an incomplete operation.
- Assessment: Hypothesis A is currently better supported due to the explicit ransom demand and SafePay’s known modus operandi. Indicators such as further data leaks or evidence of espionage could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: SafePay is acting independently without state sponsorship; Ingram Micro’s reported data on the breach is accurate; the primary motive is financial gain.
- Information Gaps: Details on the specific vulnerabilities exploited; confirmation of whether any ransom was paid; the full extent of data exfiltration.
- Bias & Deception Risks: Potential bias in relying on Ingram Micro’s disclosures; SafePay’s claims could be exaggerated or deceptive.
4. Implications and Strategic Risks
The ransomware attack on Ingram Micro highlights vulnerabilities in corporate cybersecurity and the ongoing threat posed by ransomware groups. This incident could lead to increased scrutiny and regulatory pressure on companies to enhance data protection measures.
- Political / Geopolitical: Potential for increased regulatory actions and international cooperation against ransomware groups.
- Security / Counter-Terrorism: Heightened awareness and preparedness for similar attacks on critical infrastructure and supply chains.
- Cyber / Information Space: Increased focus on cybersecurity resilience and potential for retaliatory cyber operations.
- Economic / Social: Financial losses for Ingram Micro and potential reputational damage, impacting customer trust and market position.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Ingram Micro’s network for further breaches; engage with cybersecurity experts to assess vulnerabilities; improve communication strategies with stakeholders.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in advanced threat detection technologies; conduct regular security audits.
- Scenario Outlook:
- Best: No further data leaks, improved cybersecurity posture, and restored customer confidence.
- Worst: Additional data breaches and financial losses, leading to regulatory penalties and loss of market share.
- Most-Likely: Gradual recovery with increased cybersecurity measures and ongoing vigilance against future threats.
6. Key Individuals and Entities
- SafePay (ransomware group)
- Ingram Micro (affected entity)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, data breach, financial impact, corporate security, information security, operational disruption
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us