Ireland seeks to enhance police powers to intercept and decrypt digital communications through new legislation
Published on: 2026-01-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ireland wants to give its cops spyware ability to crack encrypted messages
1. BLUF (Bottom Line Up Front)
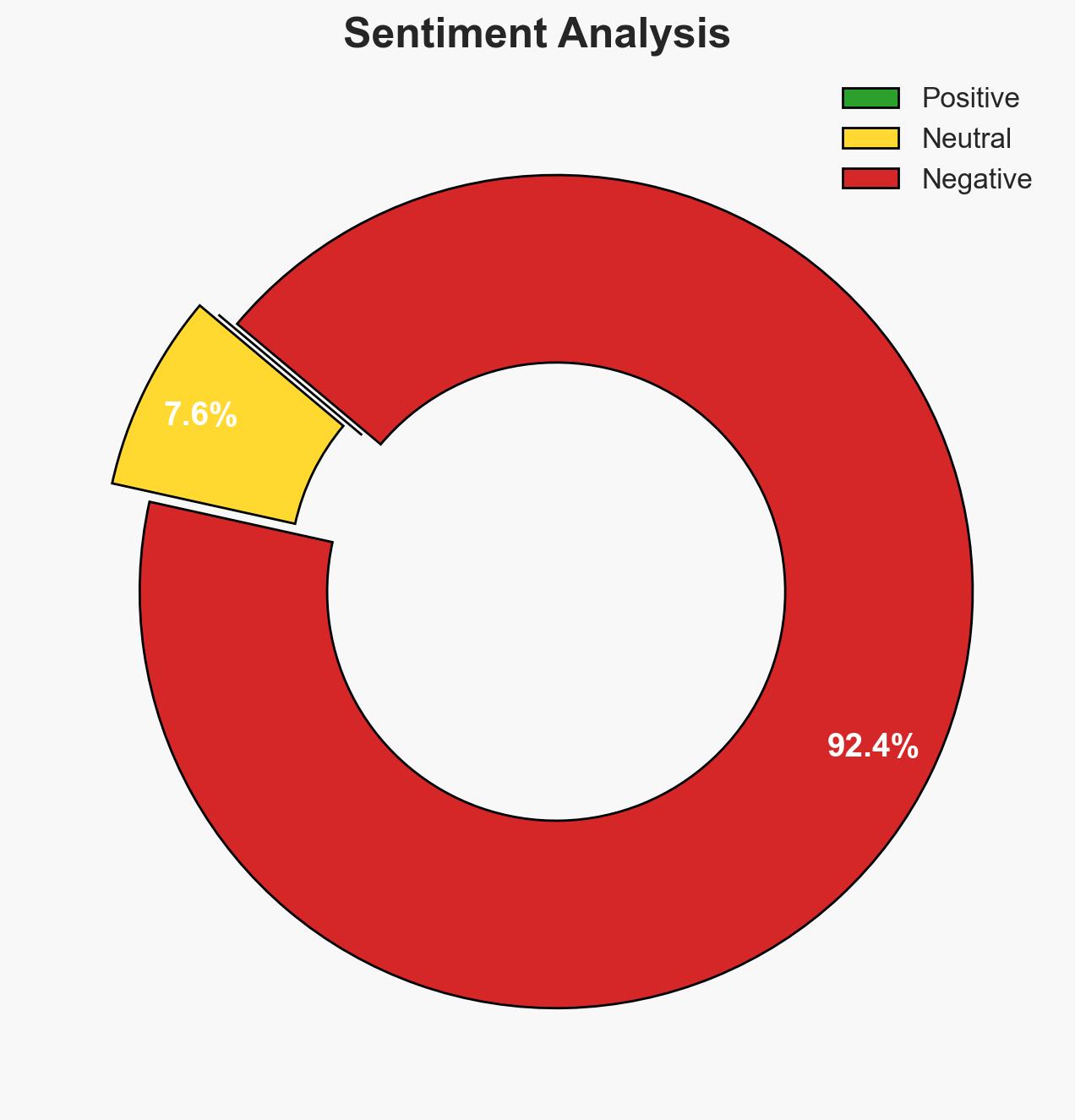
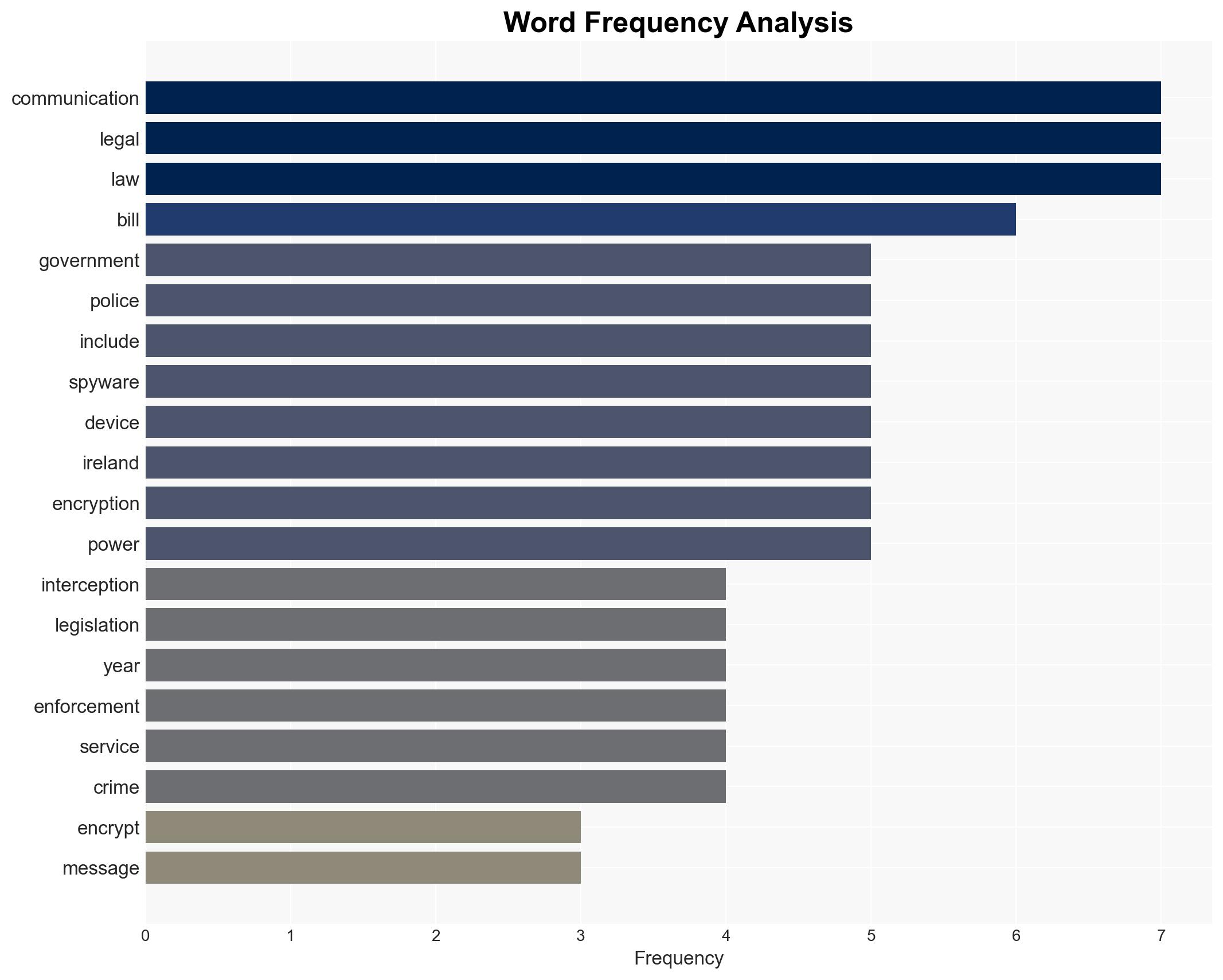
The Irish government’s proposal to enhance police capabilities to intercept encrypted communications via the Communications (Interception and Lawful Access) Bill could significantly impact privacy and law enforcement dynamics. The initiative aims to modernize outdated legislation and align with EU directives, but faces strong opposition from privacy advocates. Overall, there is moderate confidence in the assessment that this proposal will face substantial legal and technical challenges before implementation.
2. Competing Hypotheses
- Hypothesis A: The Irish government will successfully implement the proposed legislation, enabling law enforcement to intercept encrypted communications. Supporting evidence includes the government’s commitment to updating legal frameworks and aligning with EU guidelines. Contradicting evidence includes technical challenges and potential resistance from privacy advocates and technology companies.
- Hypothesis B: The proposed legislation will face insurmountable opposition and technical barriers, preventing its full implementation. Supporting evidence includes strong opposition from privacy advocates and the technical infeasibility of breaking end-to-end encryption without significant security trade-offs. Contradicting evidence includes the government’s determination to pursue this legislative update.
- Assessment: Hypothesis B is currently better supported due to the technical challenges and strong opposition from privacy advocates and technology companies. Key indicators that could shift this judgment include changes in EU regulations or technological breakthroughs in encryption interception.
3. Key Assumptions and Red Flags
- Assumptions: The Irish government has the technical capability to implement the proposed measures; EU regulations will support such legislative changes; privacy concerns can be sufficiently mitigated.
- Information Gaps: Specific technical methods for intercepting encrypted communications; detailed privacy safeguards proposed by the government.
- Bias & Deception Risks: Potential bias in government communications emphasizing security over privacy; risk of underestimating technical challenges due to political motivations.
4. Implications and Strategic Risks
This development could significantly alter the balance between privacy and security in Ireland, with potential ripple effects across the EU and globally.
- Political / Geopolitical: May strain relationships with privacy-focused EU member states and technology companies.
- Security / Counter-Terrorism: Could enhance law enforcement capabilities but also drive criminal communications to more secure platforms.
- Cyber / Information Space: Risk of increased cyber vulnerabilities if encryption standards are weakened.
- Economic / Social: Potential negative impact on Ireland’s tech sector if companies withdraw services over privacy concerns.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor legislative developments and stakeholder reactions; engage with EU partners to assess alignment and potential conflicts.
- Medium-Term Posture (1–12 months): Develop strategies to address privacy concerns and engage with technology companies to explore feasible technical solutions.
- Scenario Outlook:
- Best: Legislation is implemented with strong privacy safeguards, enhancing security without major backlash.
- Worst: Legislation fails due to technical and legal challenges, damaging government credibility.
- Most-Likely: Partial implementation with ongoing legal and technical disputes.
6. Key Individuals and Entities
- Irish Department of Justice, Home Affairs, and Migration
- EU Commission
- Technology companies (e.g., Signal, Tuta Mail)
- Privacy advocacy groups
7. Thematic Tags
cybersecurity, encryption, privacy, law enforcement, EU regulations, legislative process, technology policy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us