Osiris Ransomware Emerges with Advanced Techniques Indicating Skilled Cybercriminal Involvement
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New Osiris ransomware reveals sophisticated tactics and experienced attackers
1. BLUF (Bottom Line Up Front)
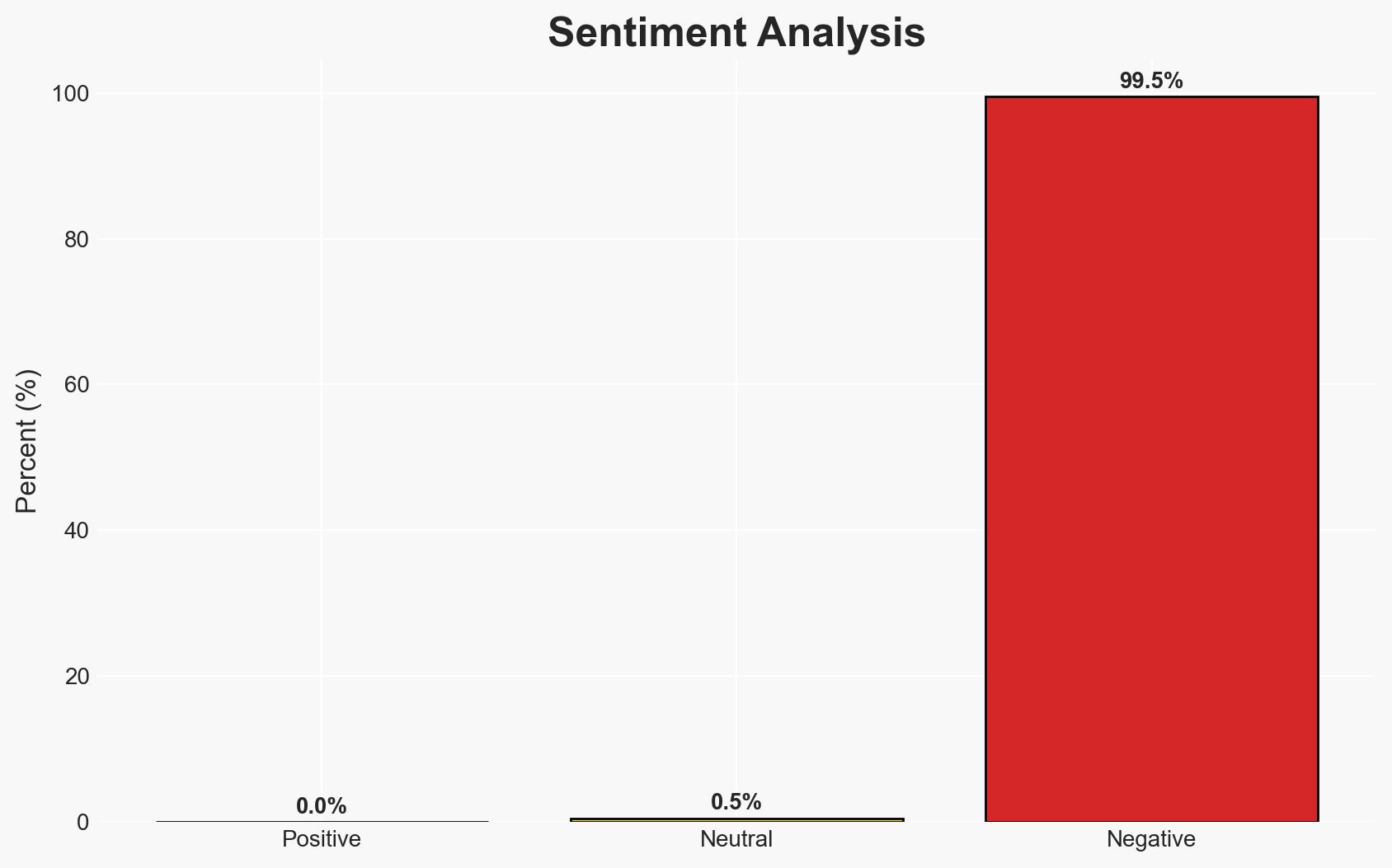
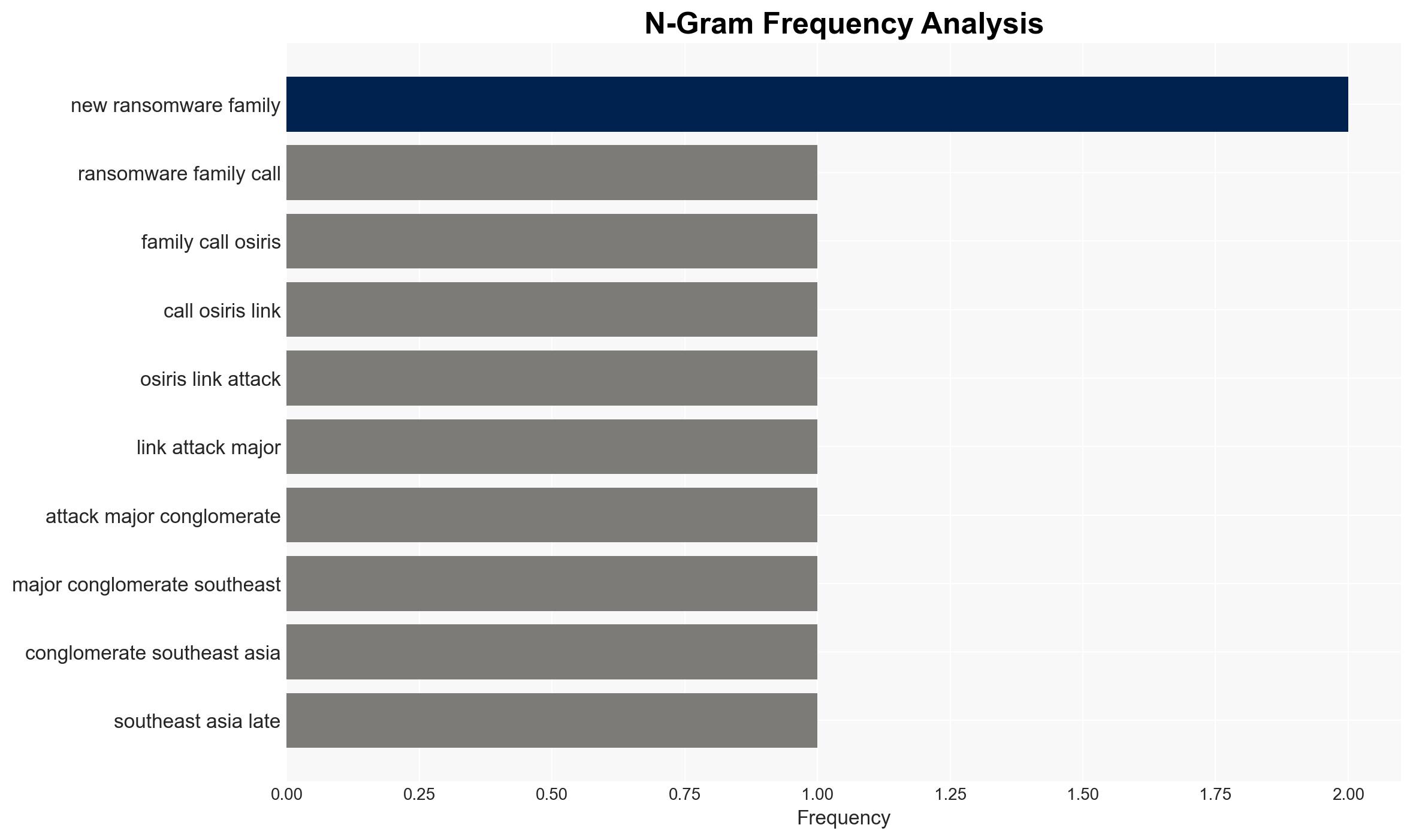
The emergence of the Osiris ransomware, linked to a sophisticated attack on a Southeast Asian conglomerate, suggests the involvement of experienced threat actors, possibly the Inc ransomware group. The ransomware’s advanced features and operational tactics indicate a significant threat to organizations globally. Overall, there is moderate confidence in the assessment that Osiris represents a new and potent threat in the ransomware landscape.
2. Competing Hypotheses
- Hypothesis A: Osiris ransomware is a new creation by the Inc ransomware group, leveraging their previous tactics and tools. Supporting evidence includes the use of a Mimikatz variant and operational overlap with Inc’s past campaigns. However, the developers remain unidentified, which is a key uncertainty.
- Hypothesis B: Osiris is an independent development by a new group of actors who have adopted and adapted known techniques from various ransomware groups, including Inc. The distinct features and lack of direct lineage to existing strains support this, but the operational similarities with Inc suggest otherwise.
- Assessment: Hypothesis A is currently better supported due to the operational and technical overlaps with known Inc group activities. Key indicators that could shift this judgment include the identification of developers or further distinct operational patterns.
3. Key Assumptions and Red Flags
- Assumptions: Osiris is primarily targeting large organizations; the Inc group is still active; the use of Wasabi cloud storage is a deliberate choice by the attackers.
- Information Gaps: The identity of the developers; the full scope of Osiris’s deployment; motivations behind the choice of specific tools and targets.
- Bias & Deception Risks: Potential confirmation bias in linking Osiris to the Inc group; reliance on open-source data that may be incomplete or manipulated by threat actors.
4. Implications and Strategic Risks
The development of Osiris ransomware could signal a new phase in ransomware sophistication, potentially leading to increased targeting of high-value organizations and critical infrastructure.
- Political / Geopolitical: Potential for increased tensions if state actors are involved or if attacks are perceived as state-sponsored.
- Security / Counter-Terrorism: Heightened threat environment requiring enhanced defensive measures and inter-agency cooperation.
- Cyber / Information Space: Possible escalation in cyber warfare tactics and increased demand for cybersecurity solutions.
- Economic / Social: Potential economic disruptions and increased costs for cybersecurity insurance and mitigation efforts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of ransomware activities, enhance network defenses, and share intelligence with allies and partners.
- Medium-Term Posture (1–12 months): Develop resilience measures, invest in cybersecurity training, and establish public-private partnerships for threat intelligence sharing.
- Scenario Outlook:
- Best Case: Osiris is contained with minimal impact due to rapid response and improved defenses.
- Worst Case: Widespread disruption across multiple sectors, leading to significant economic and social impacts.
- Most Likely: Continued sporadic attacks with increasing sophistication, necessitating ongoing vigilance and adaptation.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
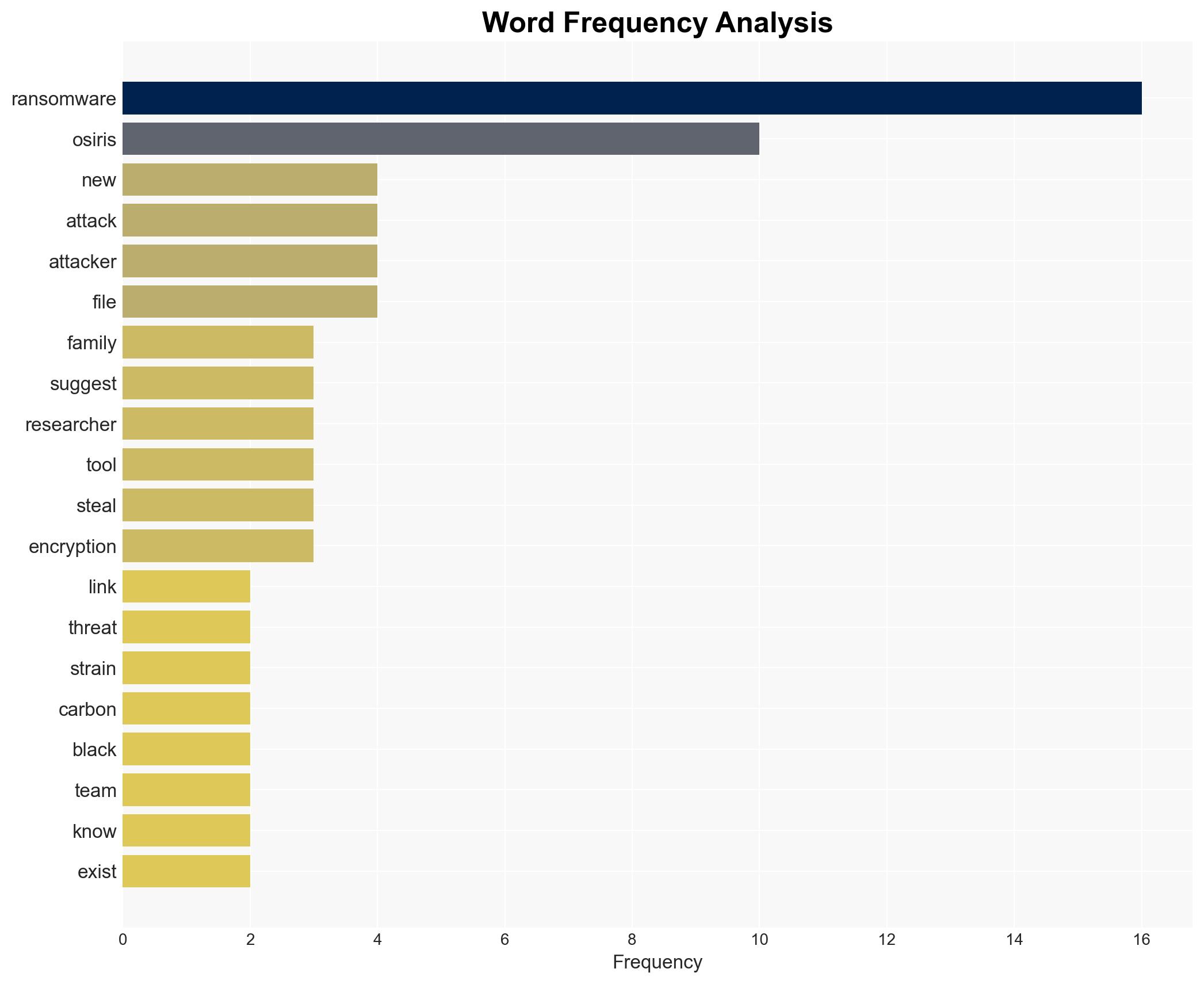
cybersecurity, ransomware, threat actors, Southeast Asia, Inc group, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us