Obsidian Security launches comprehensive solution to enhance SaaS supply chain protection against breaches
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Obsidian Security unveils end-to-end SaaS supply chain security to stop integration-led breaches
1. BLUF (Bottom Line Up Front)
Obsidian Security has introduced a comprehensive SaaS supply chain security solution aimed at mitigating integration-led breaches. This development is particularly relevant for organizations heavily reliant on interconnected SaaS applications, which are increasingly vulnerable to security threats. The solution promises enhanced visibility and proactive threat management, potentially reducing the risk of widespread data breaches. Overall confidence in this assessment is moderate, given the current lack of detailed performance metrics and real-world application examples.
2. Competing Hypotheses
- Hypothesis A: Obsidian’s solution will significantly reduce SaaS supply chain vulnerabilities by providing unprecedented visibility and control over integration risks. This hypothesis is supported by the unique capabilities of the solution to continuously monitor SaaS interactions. However, uncertainties remain regarding its scalability and effectiveness across diverse organizational environments.
- Hypothesis B: The solution may not substantially mitigate SaaS supply chain risks due to potential limitations in integration with existing security frameworks and the evolving nature of SaaS threats. This is supported by the general complexity and dynamic nature of SaaS ecosystems, which may outpace static security solutions.
- Assessment: Hypothesis A is currently better supported due to the innovative approach of continuous monitoring and integration risk visibility, which addresses key gaps in existing security measures. Indicators such as successful deployment in diverse environments and positive feedback from early adopters could further validate this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will prioritize SaaS supply chain security; Obsidian’s solution is compatible with a wide range of existing SaaS applications; SaaS threats will continue to grow in complexity.
- Information Gaps: Lack of specific performance data and case studies demonstrating the solution’s effectiveness; unclear integration process with existing security infrastructures.
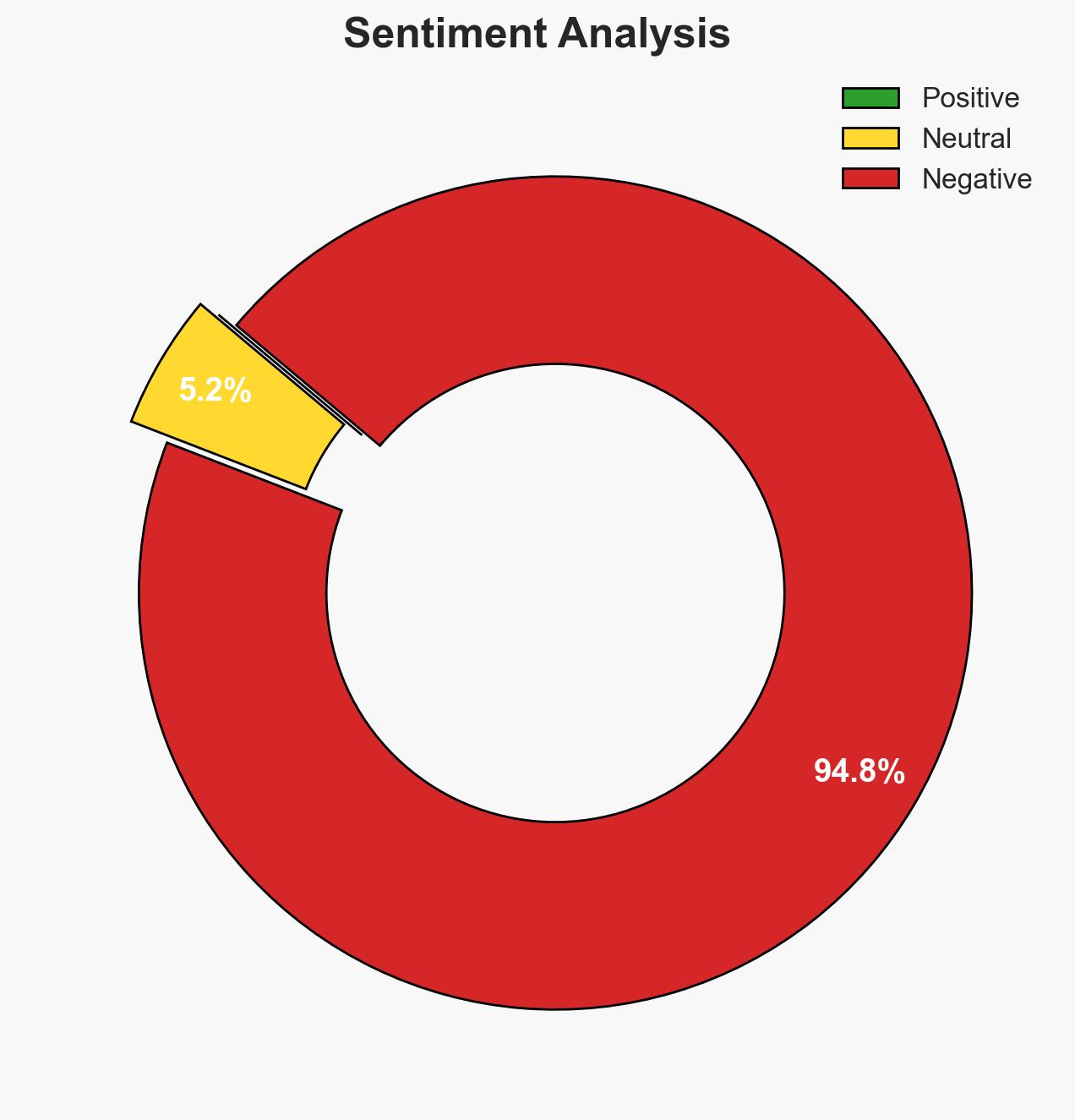
- Bias & Deception Risks: Potential bias from vendor-provided information; risk of over-reliance on a single solution without considering broader security strategies.
4. Implications and Strategic Risks
The introduction of Obsidian’s solution could reshape organizational approaches to SaaS security, emphasizing proactive and continuous monitoring. However, its success will depend on widespread adoption and integration with existing systems.
- Political / Geopolitical: Limited direct implications, though increased security could enhance national resilience against cyber threats.
- Security / Counter-Terrorism: Improved SaaS security could reduce the risk of data breaches that might be exploited by malicious actors, including terrorist organizations.
- Cyber / Information Space: Enhanced visibility into SaaS ecosystems could deter cyber-espionage and data theft activities.
- Economic / Social: Successful implementation could protect businesses from financial losses due to breaches, thereby supporting economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Evaluate the compatibility of Obsidian’s solution with existing systems; conduct pilot tests to assess effectiveness.
- Medium-Term Posture (1–12 months): Develop partnerships with SaaS providers to ensure seamless integration; invest in training for security teams on the new platform.
- Scenario Outlook:
- Best: Widespread adoption leads to a significant reduction in SaaS-related breaches.
- Worst: Incompatibility issues limit deployment, and threats evolve faster than security measures.
- Most-Likely: Gradual adoption with mixed results, requiring ongoing adjustments and enhancements.
6. Key Individuals and Entities
- Joseph Gothelf, VP, Cybersecurity, Wyndham Hotels and Resorts
- Grace Liu, SVP and CIO, Seagate Technology
- Obsidian Security
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
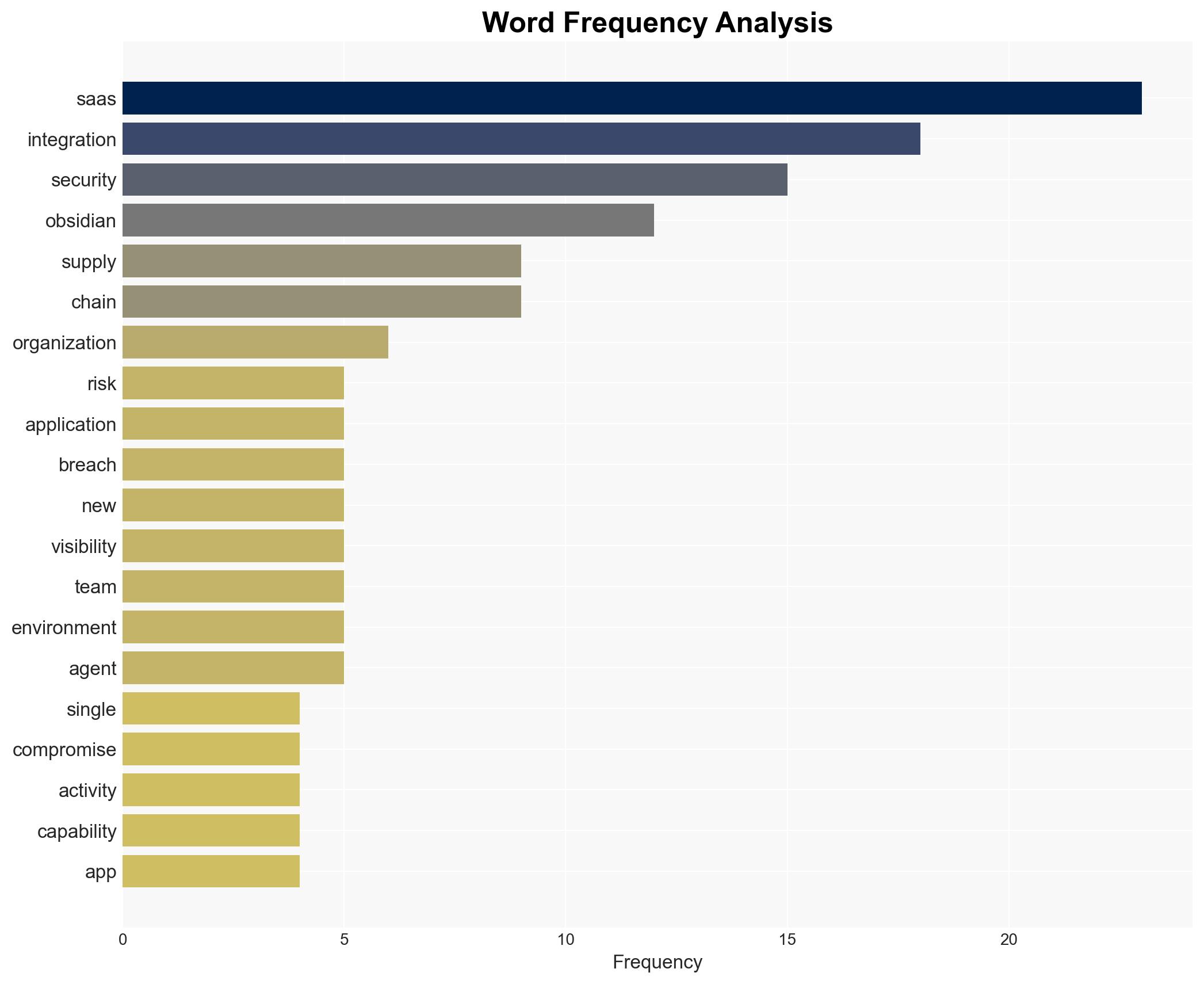
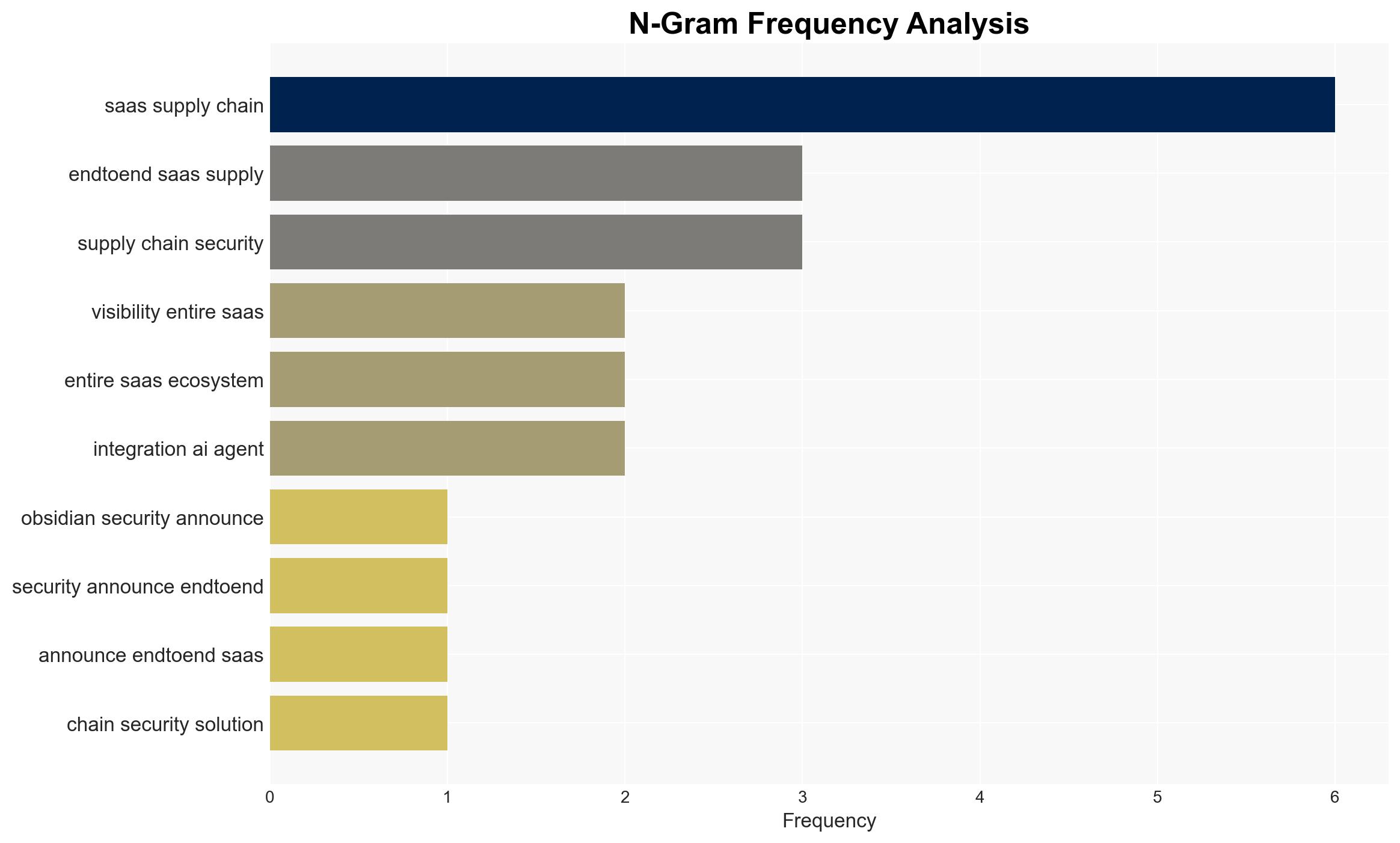
cybersecurity, SaaS security, cyber threats, integration risk, data breaches, cybersecurity solutions, supply chain security, digital resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us