1Password Enhances Security with New Anti-Phishing Feature to Combat Rising Credential Theft Risks
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: 1Password’s new anti-phishing feature adds a crucial layer of protection – how it works
1. BLUF (Bottom Line Up Front)
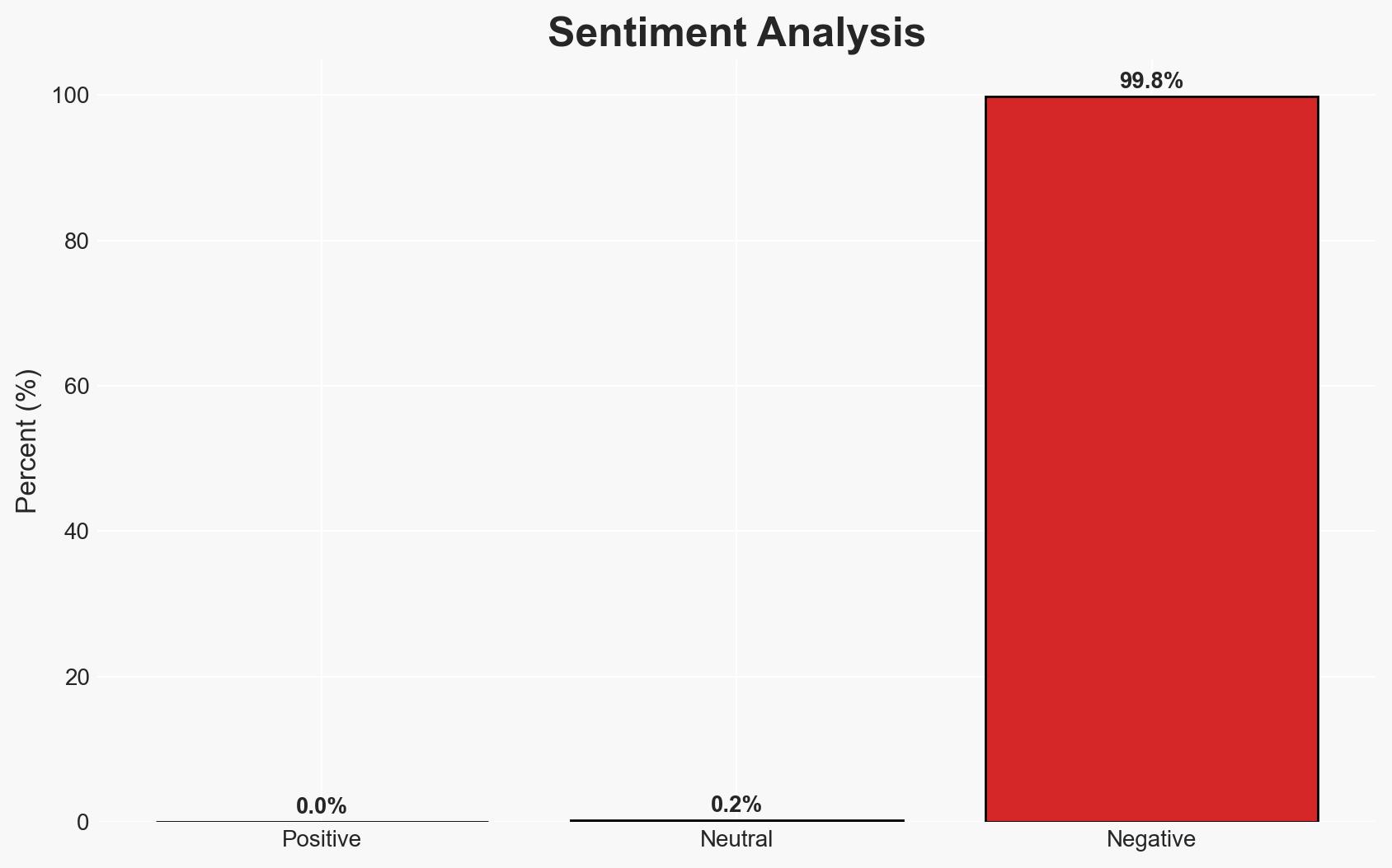
The introduction of 1Password’s new anti-phishing feature represents a significant advancement in cybersecurity defenses against phishing attacks, which are increasingly sophisticated and prevalent. This development primarily affects businesses and individual users who are frequent targets of phishing scams. The feature is likely to reduce successful phishing attempts, although its effectiveness depends on user awareness and adoption. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: 1Password’s new feature will significantly reduce phishing success rates by providing an additional layer of verification during the login process. This is supported by the feature’s design to prevent credential entry on fraudulent sites, but its success is contingent on user engagement and understanding.
- Hypothesis B: The new feature will have limited impact on phishing success rates due to potential user complacency or misunderstanding of the feature’s function. This is contradicted by the feature’s proactive design but is supported by historical challenges in user adherence to cybersecurity protocols.
- Assessment: Hypothesis A is currently better supported due to the innovative nature of the feature and its alignment with known effective cybersecurity practices. Indicators that could shift this judgment include user adoption rates and reports of continued phishing success despite the feature.
3. Key Assumptions and Red Flags
- Assumptions: Users will understand and properly utilize the new feature; phishing tactics will not rapidly evolve to circumvent this feature; 1Password’s market penetration will ensure widespread adoption.
- Information Gaps: Detailed user feedback on the feature’s usability and effectiveness; data on phishing attack rates post-feature implementation.
- Bias & Deception Risks: Potential bias from 1Password’s self-reported data; phishing campaigns may employ deception to undermine the feature’s effectiveness.
4. Implications and Strategic Risks
This development could lead to a decrease in successful phishing attacks if widely adopted, potentially prompting cybercriminals to innovate new tactics. The feature’s success could influence other cybersecurity firms to adopt similar measures, enhancing overall digital security.
- Political / Geopolitical: Minimal direct impact, but improved cybersecurity could enhance national resilience against state-sponsored cyber operations.
- Security / Counter-Terrorism: Reduced risk of data breaches and ransomware attacks, which could indirectly support counter-terrorism efforts by limiting funding sources.
- Cyber / Information Space: Potential shift in phishing tactics, requiring ongoing adaptation in cybersecurity strategies.
- Economic / Social: Increased trust in digital transactions and communications, potentially boosting economic activity and social stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor user feedback and phishing attack rates; conduct awareness campaigns to educate users on the new feature.
- Medium-Term Posture (1–12 months): Develop partnerships with other cybersecurity firms to standardize similar protective measures; invest in user education and support.
- Scenario Outlook: Best: Significant reduction in phishing success rates; Worst: Phishing tactics evolve to bypass protections; Most-Likely: Moderate reduction in phishing success with ongoing adaptation required.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
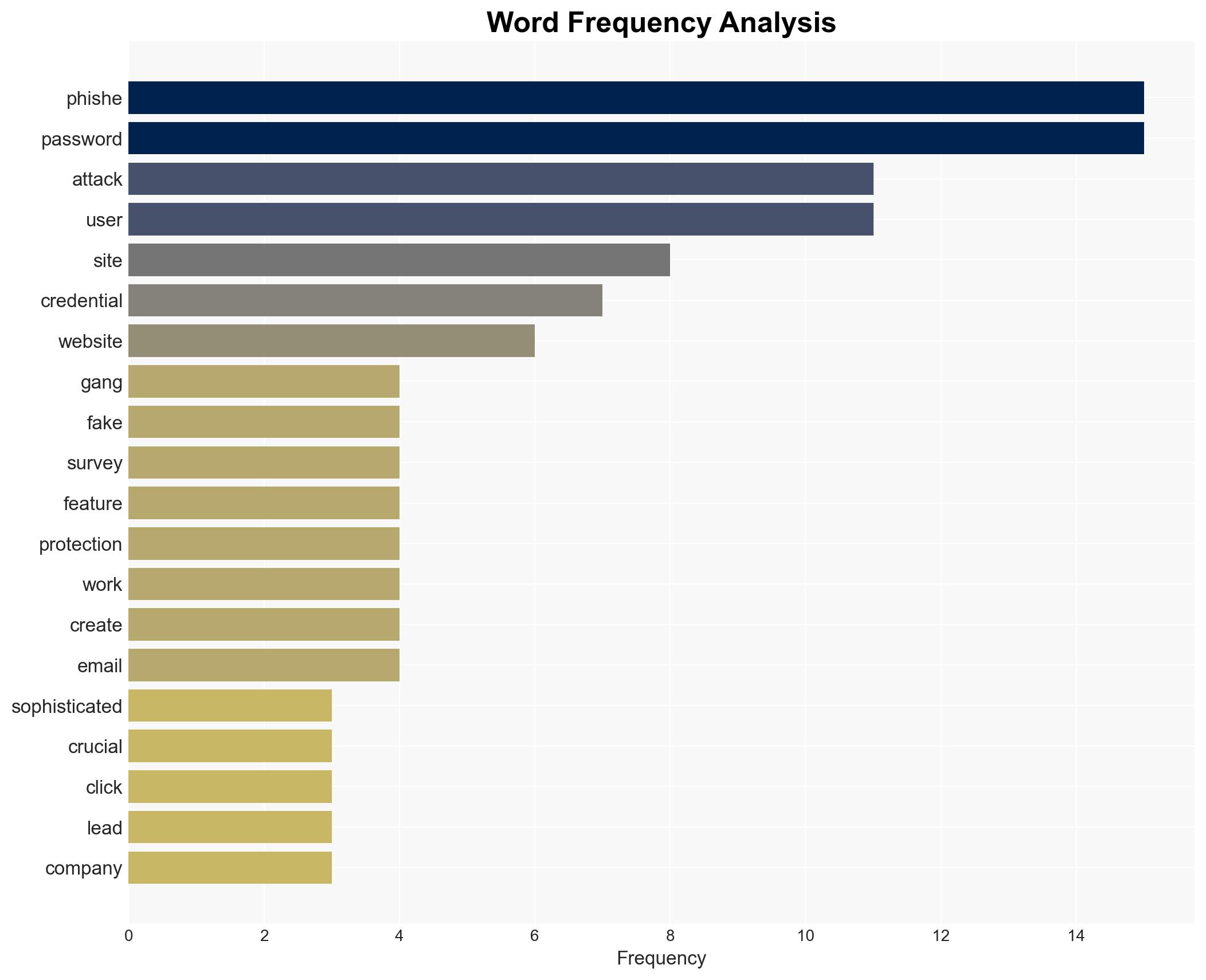
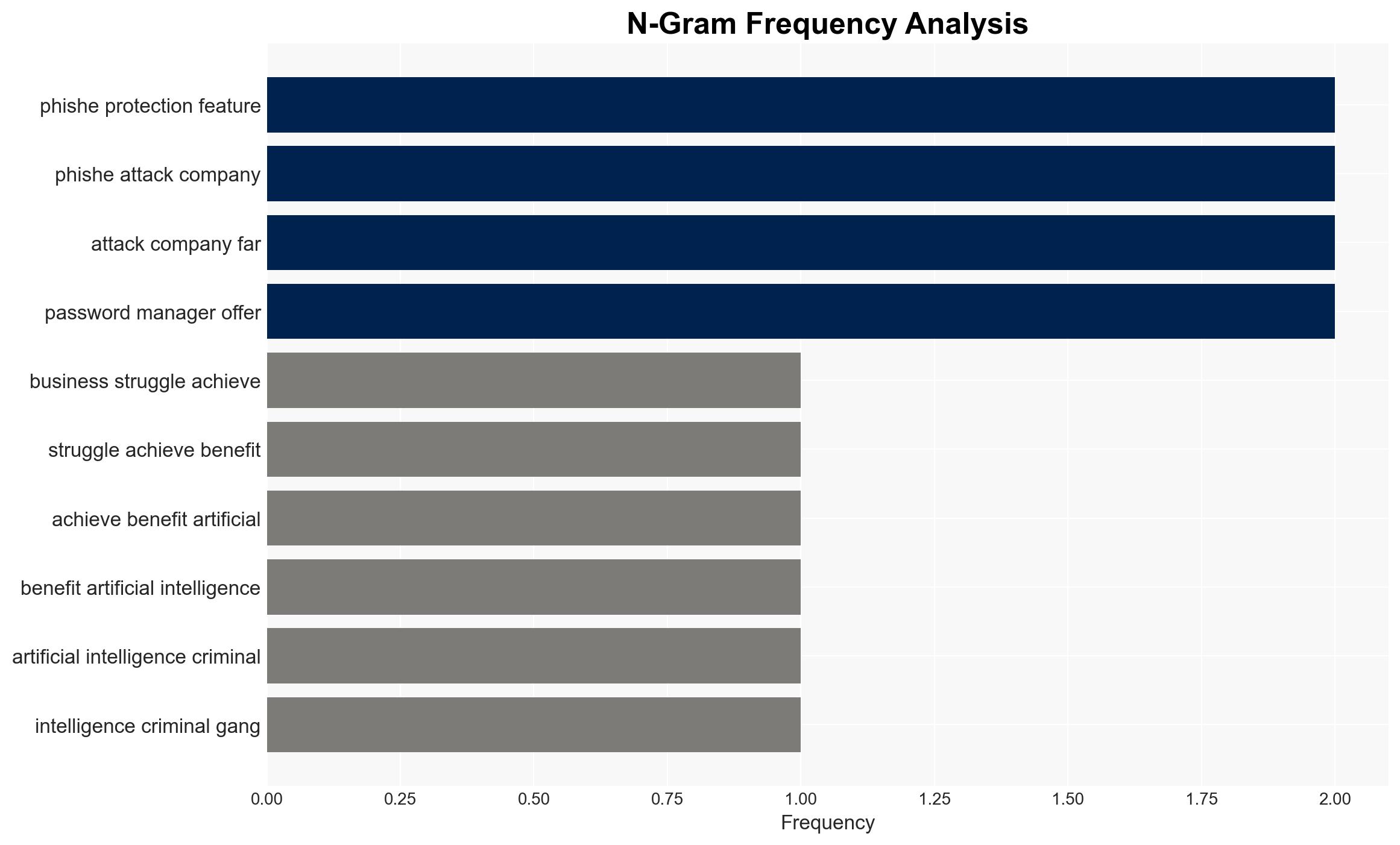
cybersecurity, phishing, digital protection, user awareness, cybercrime, password management, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us