Fortinet acknowledges incomplete fix for critical FortiCloud authentication bypass exploited in ongoing attac…
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Fortinet confirms critical FortiCloud auth bypass not fully patched
1. BLUF (Bottom Line Up Front)
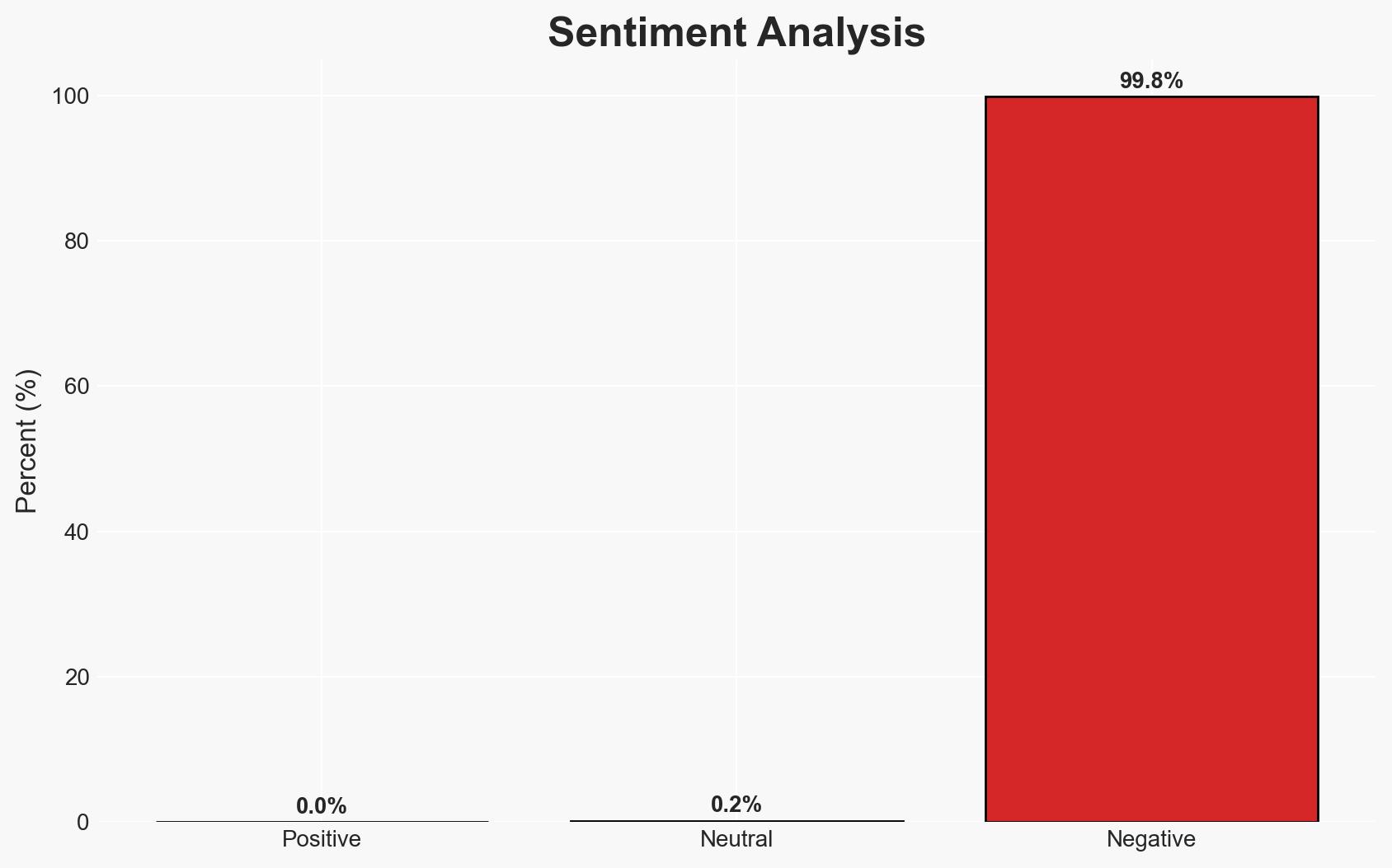
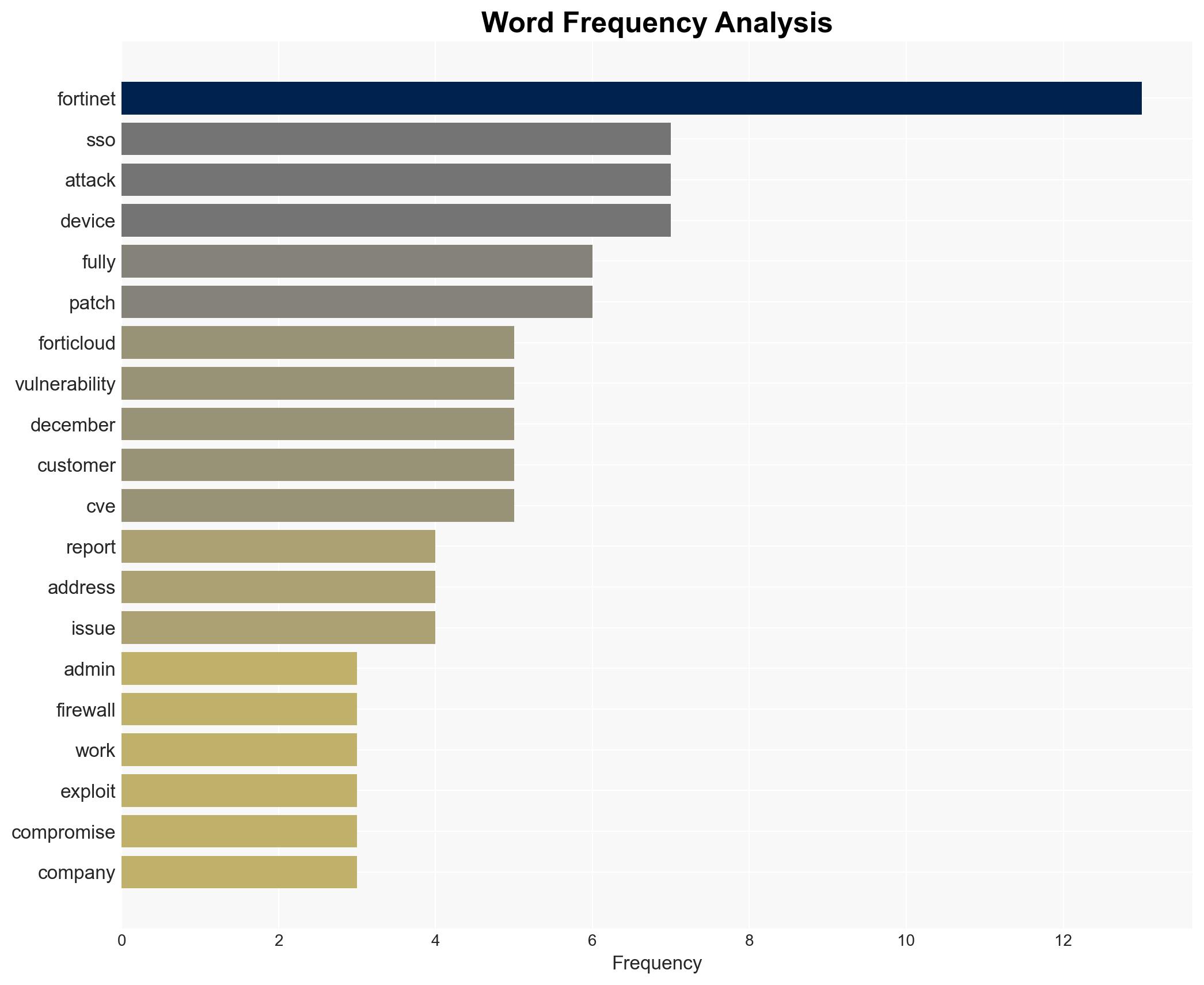
The FortiCloud SSO authentication bypass vulnerability, CVE-2025-59718, remains unpatched, posing a significant risk to Fortinet’s firewall users. Current evidence suggests that threat actors are exploiting this vulnerability to gain unauthorized access to systems. This situation affects organizations using Fortinet products, with moderate confidence in the assessment due to ongoing exploitation reports and Fortinet’s confirmation.
2. Competing Hypotheses
- Hypothesis A: The attacks are exploiting a previously unknown vulnerability or a new attack vector in Fortinet’s systems. Evidence includes reports of fully patched systems being compromised, suggesting a new attack path. However, the lack of detailed technical analysis limits this hypothesis.
- Hypothesis B: The attacks are a continuation of the exploitation of the known CVE-2025-59718 vulnerability, potentially due to incomplete patching. This is supported by Fortinet’s acknowledgment of ongoing exploitation and similarities to past incidents. Contradictory evidence includes reports of fully patched systems being compromised.
- Assessment: Hypothesis B is currently better supported due to Fortinet’s confirmation of ongoing exploitation and the similarity to previous incidents. Key indicators that could shift this judgment include new technical details revealing a different vulnerability or attack vector.
3. Key Assumptions and Red Flags
- Assumptions: Fortinet’s patches are expected to fully address the vulnerability; threat actors are primarily targeting Fortinet users; the vulnerability is limited to Fortinet products.
- Information Gaps: Detailed technical analysis of the attack vector; confirmation of whether a new vulnerability exists; comprehensive data on the scope of affected systems.
- Bias & Deception Risks: Potential bias in relying on Fortinet’s public statements; risk of underestimating the threat actor’s capabilities or intentions; possible manipulation of incident reports by affected parties.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of Fortinet’s security practices and impact customer trust. If unresolved, it may encourage further exploitation by threat actors.
- Political / Geopolitical: Potential for increased regulatory pressure on cybersecurity standards and practices.
- Security / Counter-Terrorism: Elevated risk of cyber-attacks on critical infrastructure using Fortinet products.
- Cyber / Information Space: Possible increase in cyber espionage activities exploiting this vulnerability.
- Economic / Social: Financial losses for affected organizations and potential reputational damage to Fortinet.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement Fortinet’s recommended security measures, monitor for indicators of compromise, and prepare incident response plans.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, enhance cybersecurity training, and invest in alternative security solutions.
- Scenario Outlook:
- Best: Fortinet releases a comprehensive patch, and exploitation ceases.
- Worst: New vulnerabilities are discovered, leading to widespread exploitation.
- Most-Likely: Continued exploitation until a full patch is deployed, with gradual mitigation as organizations implement interim security measures.
6. Key Individuals and Entities
- Fortinet
- Arctic Wolf
- Fortinet Chief Information Security Officer (CISO) Carl Windsor
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, vulnerability management, Fortinet, cyber-espionage, network security, threat intelligence, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us