Sandworm Group’s DynoWiper Malware Linked to Foiled Cyber Attack on Polish Energy Infrastructure
Published on: 2026-01-24
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New DynoWiper Malware Used in Attempted Sandworm Attack on Polish Power Sector
1. BLUF (Bottom Line Up Front)
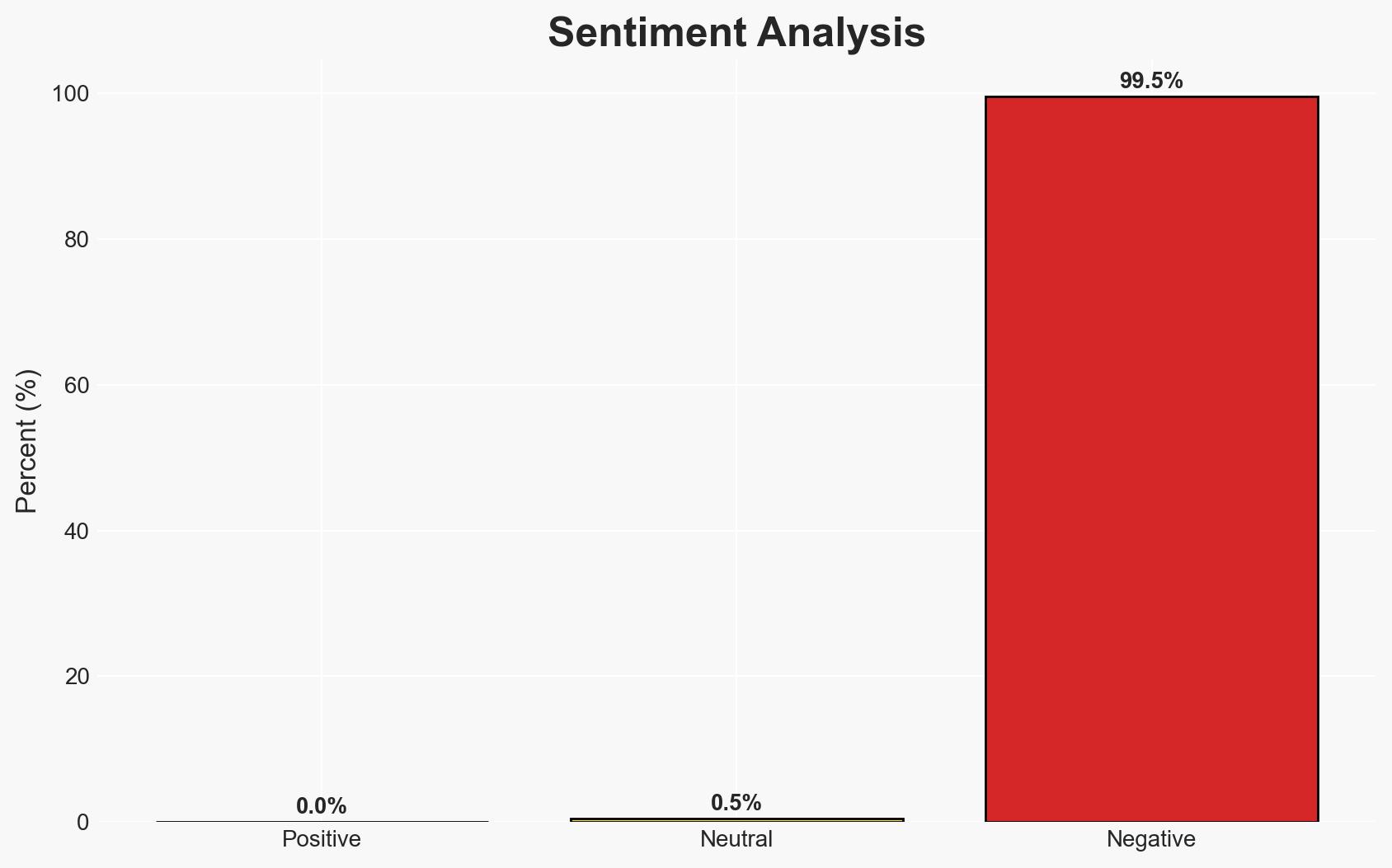
The Russian hacking group Sandworm attempted a significant cyber attack on Poland’s power sector using the DynoWiper malware, but the attack was unsuccessful. The incident underscores ongoing threats to critical infrastructure from state-sponsored actors. The most likely hypothesis is that Sandworm, linked to Russian state interests, conducted the attack to destabilize Poland’s energy sector. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Sandworm, a Russian state-sponsored group, conducted the attack to disrupt Poland’s energy infrastructure. This is supported by the use of DynoWiper, similar tactics in past attacks, and geopolitical tensions. However, the lack of successful disruption introduces uncertainty.
- Hypothesis B: Another actor, possibly imitating Sandworm, conducted the attack to create confusion or misattribute responsibility. While the attack’s timing and method align with Sandworm’s history, the absence of definitive proof of Russian state involvement remains a gap.
- Assessment: Hypothesis A is currently better supported due to historical patterns of Sandworm’s behavior and the geopolitical context. Key indicators that could shift this judgment include new intelligence on the attack’s origins or evidence of alternative actors.
3. Key Assumptions and Red Flags
- Assumptions: Sandworm operates under Russian state directives; DynoWiper is a tool developed or acquired by Sandworm; Poland’s energy sector is a strategic target for Russia.
- Information Gaps: Detailed technical analysis of DynoWiper’s origin; direct evidence linking the attack to Russian state apparatus; motivations behind the specific timing of the attack.
- Bias & Deception Risks: Attribution bias due to historical precedent; potential for false flag operations; reliance on open-source cybersecurity reports which may have inherent biases.
4. Implications and Strategic Risks
This development highlights the persistent threat of cyber attacks on critical infrastructure, potentially leading to increased geopolitical tensions and necessitating enhanced cybersecurity measures.
- Political / Geopolitical: Escalation of tensions between Poland and Russia, potential for broader NATO involvement.
- Security / Counter-Terrorism: Increased vigilance and defensive postures in critical infrastructure sectors; potential for retaliatory cyber operations.
- Cyber / Information Space: Heightened focus on cybersecurity frameworks; potential for misinformation campaigns exploiting the attack.
- Economic / Social: Potential economic impacts from disrupted energy supply; public concern over national security vulnerabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; conduct a thorough forensic analysis of the attack; engage in diplomatic channels to address potential state-sponsored cyber aggression.
- Medium-Term Posture (1–12 months): Strengthen international cybersecurity partnerships; invest in resilience measures for critical infrastructure; update national cybersecurity legislation and frameworks.
- Scenario Outlook:
- Best Case: Strengthened defenses deter future attacks, leading to improved regional stability.
- Worst Case: Successful future attacks cause significant disruptions, escalating geopolitical tensions.
- Most Likely: Continued attempts at cyber intrusions with varying degrees of success, necessitating ongoing vigilance and adaptation.
6. Key Individuals and Entities
- Milosz Motyka – Poland’s Energy Minister
- Donald Tusk – Prime Minister of Poland
- Sandworm – Russian nation-state hacking group
- ESET – Slovakian cybersecurity company
- Cisco Talos – Cybersecurity entity
7. Thematic Tags
cybersecurity, critical infrastructure, state-sponsored cyber attacks, energy sector, Russia-Poland relations, Sandworm, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us