Phishing Kits Enhance Vishing Attacks Targeting Okta Users and Corporate Credentials
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Okta users under attack Modern phishing kits are turbocharging vishing attacks
1. BLUF (Bottom Line Up Front)
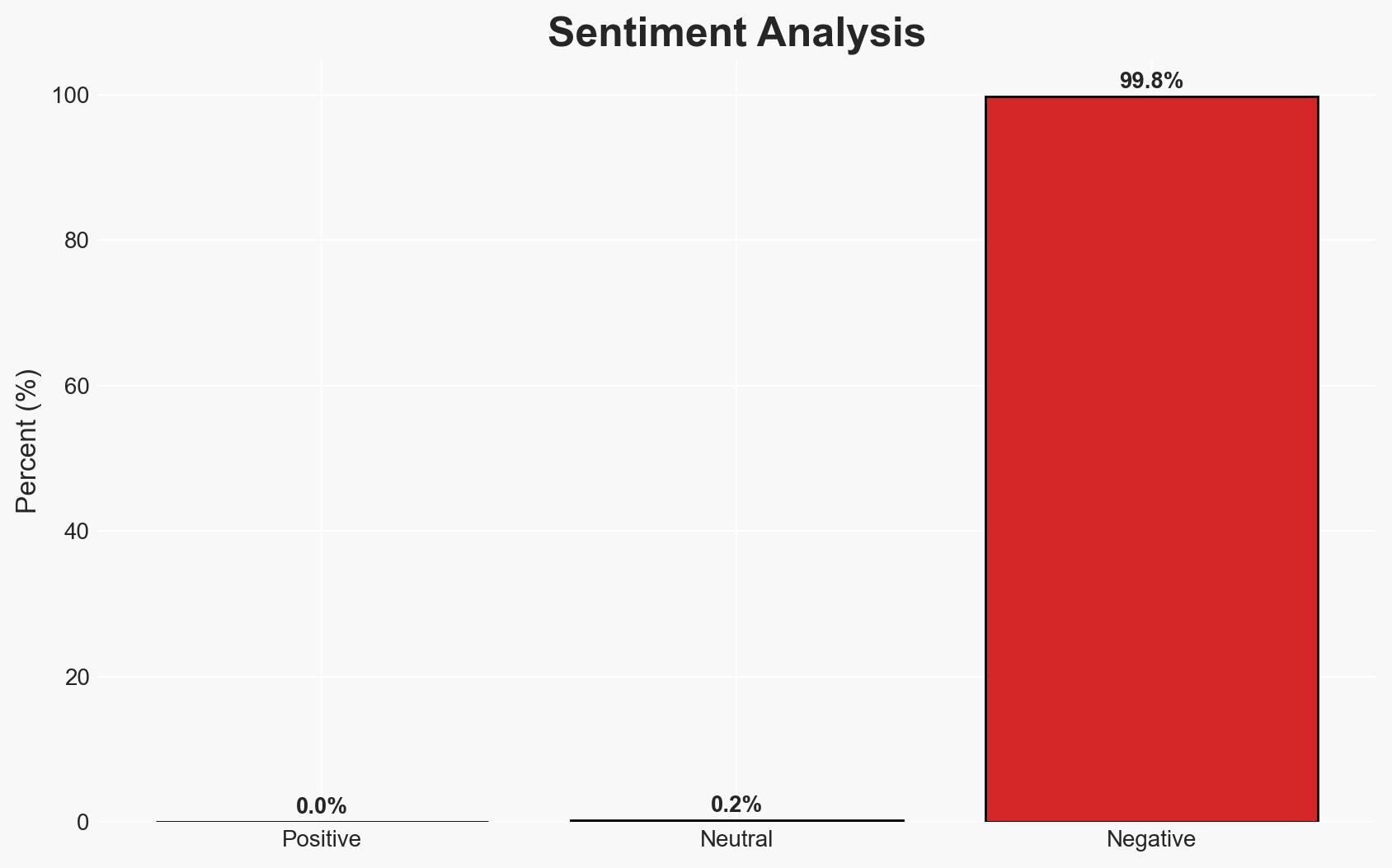
Threat actors are leveraging advanced phishing kits to conduct sophisticated vishing attacks targeting Okta users and other corporate systems. These kits enable real-time control of authentication flows, significantly increasing the threat to corporate security infrastructures. The most likely hypothesis is that these kits will become standard tools for cybercriminals, posing a growing risk to organizations reliant on multi-factor authentication. Overall confidence in this assessment is moderate due to the evolving nature of the threat and incomplete data on the full scope of affected entities.
2. Competing Hypotheses
- Hypothesis A: The primary goal of these phishing kits is to compromise corporate systems by targeting authentication processes. This is supported by the evidence of kits being used to intercept login credentials and manipulate authentication flows. However, the extent of their deployment and the full range of targeted entities remain uncertain.
- Hypothesis B: Alternatively, these phishing kits are primarily a tool for financial gain, targeting cryptocurrency providers and other financially lucrative sectors. While there is evidence of targeting such entities, the broader application to corporate systems suggests a more extensive operational scope.
- Assessment: Hypothesis A is currently better supported due to the strategic targeting of authentication processes across multiple high-value sectors, indicating a broader intent to compromise corporate systems. Indicators such as increased incidents of vishing attacks and the rapid adaptation of these kits could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The threat actors have the technical capability to adapt phishing kits quickly; multi-factor authentication remains a primary target; corporate systems are inadequately prepared for this type of attack.
- Information Gaps: Specific details on the number of organizations affected and the geographic distribution of these attacks are lacking.
- Bias & Deception Risks: Potential bias in source reporting from cybersecurity firms with vested interests; possible deception by threat actors to obscure true targets and methods.
4. Implications and Strategic Risks
This development could lead to a significant increase in successful cyber intrusions, undermining trust in corporate security measures and potentially leading to regulatory scrutiny.
- Political / Geopolitical: Increased tensions between nations over cyber espionage and attribution challenges.
- Security / Counter-Terrorism: Enhanced threat landscape requiring updated security protocols and potential for increased state-sponsored activity.
- Cyber / Information Space: Evolution of phishing tactics may drive innovation in cybersecurity defenses and response strategies.
- Economic / Social: Potential financial losses for targeted companies and erosion of consumer trust in digital services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of authentication processes, conduct phishing resilience training, and update incident response plans.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for intelligence sharing, invest in advanced threat detection technologies, and strengthen multi-factor authentication protocols.
- Scenario Outlook: Best: Rapid adaptation of defenses mitigates threat; Worst: Widespread breaches lead to significant economic damage; Most-Likely: Incremental improvements in security posture reduce but do not eliminate risk.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
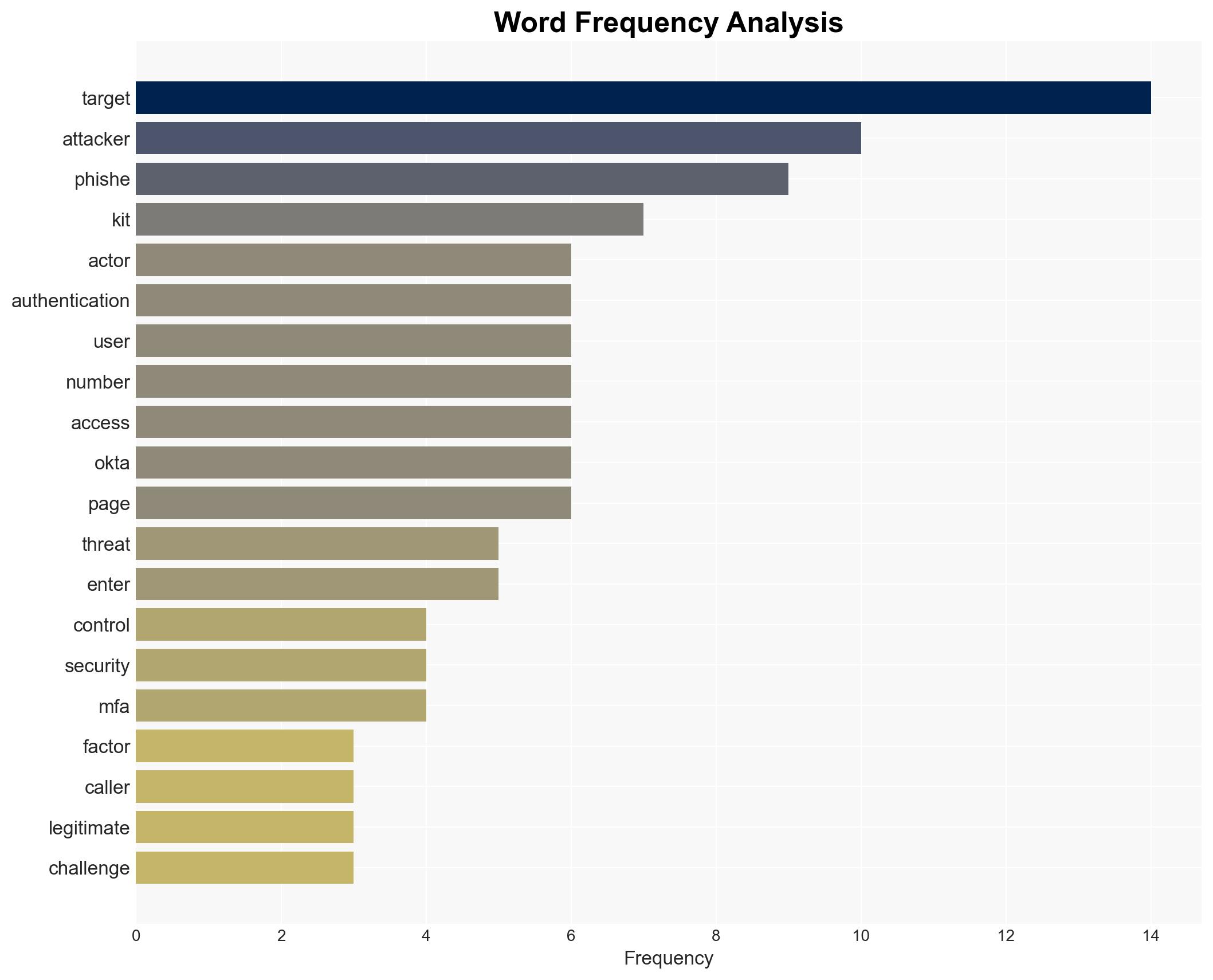
cybersecurity, vishing, phishing kits, multi-factor authentication, corporate security, cybercrime, threat actors
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us