Microsoft Provided BitLocker Encryption Keys to FBI in Landmark Case Linked to Fraud Investigation
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Reportedly Turned Over BitLocker Encryption Keys to the FBI
1. BLUF (Bottom Line Up Front)
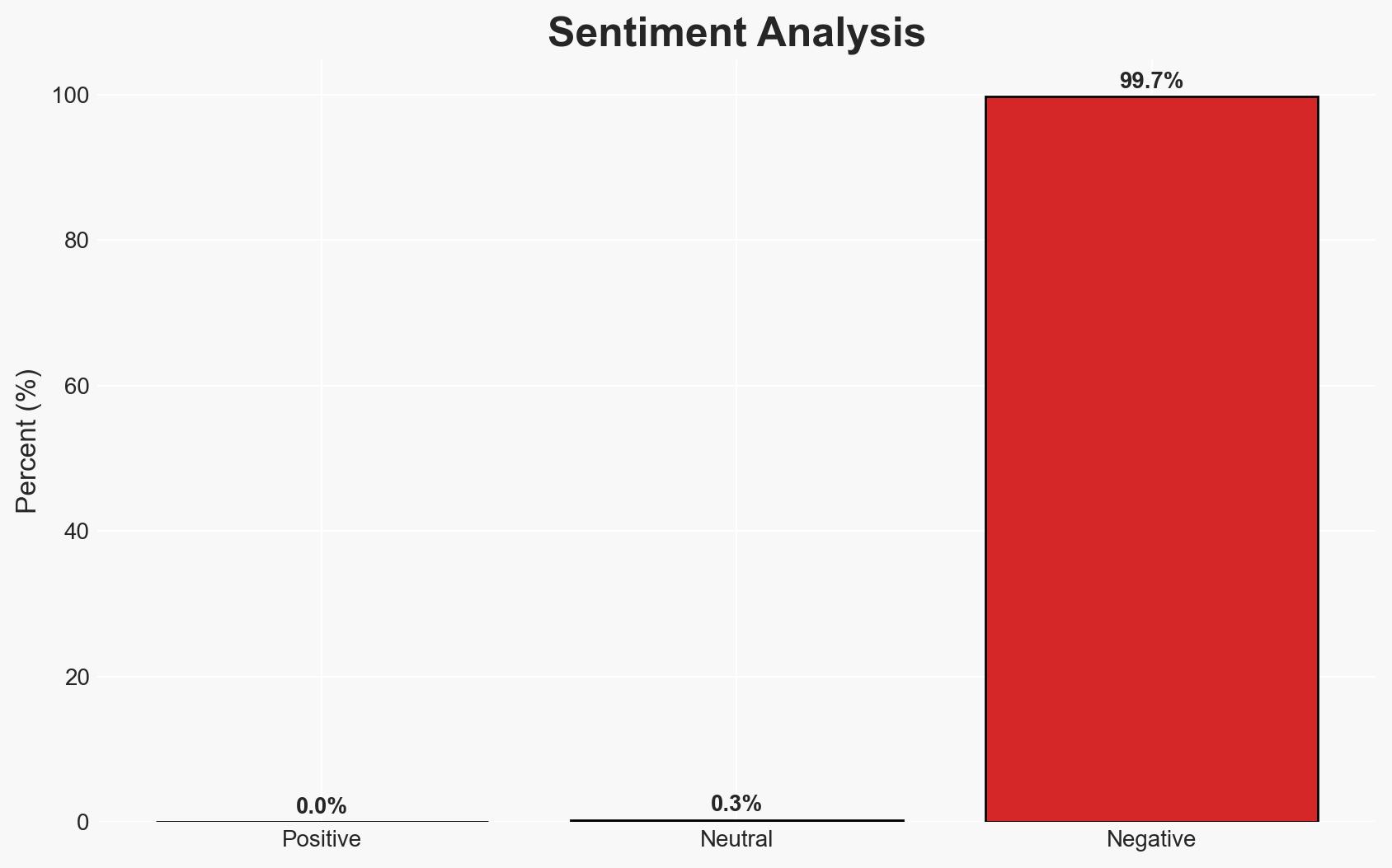
Microsoft’s compliance with an FBI request for BitLocker encryption keys highlights potential vulnerabilities in cloud-stored recovery keys, raising concerns about data security and privacy. This development primarily affects users relying on BitLocker for data protection and could have broader implications for trust in cloud services. Overall confidence in this assessment is moderate, given the limited information on the specifics of the FBI’s request and Microsoft’s compliance process.
2. Competing Hypotheses
- Hypothesis A: Microsoft provided BitLocker keys solely in compliance with a legal search warrant, reflecting standard legal obligations. Supporting evidence includes the existence of a search warrant and Microsoft’s statement on compliance. Contradicting evidence includes concerns about ease of access to keys.
- Hypothesis B: Microsoft’s compliance indicates a broader vulnerability in cloud-stored encryption keys, potentially exposing user data to unauthorized access. Supporting evidence includes expert concerns about the ease of access and potential for misuse. Contradicting evidence includes the lack of reported unauthorized access incidents.
- Assessment: Hypothesis A is currently better supported due to the legal framework governing search warrants and Microsoft’s stated compliance policy. However, indicators such as unauthorized access incidents or policy changes by Microsoft could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Microsoft acted within legal boundaries; cloud-stored keys are generally secure; FBI requests are legitimate and lawful.
- Information Gaps: Details on the FBI’s request process and any internal Microsoft policies on key disclosure.
- Bias & Deception Risks: Potential bias in reporting due to reliance on a single source; risk of deception if FBI requests are not thoroughly vetted.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of cloud-based encryption services and affect user trust in data security measures provided by major tech companies.
- Political / Geopolitical: Potential for international scrutiny on U.S.-based tech companies’ compliance with law enforcement requests.
- Security / Counter-Terrorism: May impact operational security for individuals relying on BitLocker for sensitive data protection.
- Cyber / Information Space: Increased risk of cyber threats targeting cloud-stored encryption keys.
- Economic / Social: Possible decline in consumer trust in cloud services, affecting market dynamics and tech industry reputation.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for any unauthorized access incidents; engage with Microsoft for clarity on compliance policies.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to enhance transparency in data protection practices; strengthen legal frameworks for data access requests.
- Scenario Outlook: Best: Strengthened data protection policies enhance trust. Worst: Increased incidents of unauthorized access lead to regulatory backlash. Most-Likely: Continued scrutiny and gradual policy adjustments by tech companies.
6. Key Individuals and Entities
- Microsoft
- FBI
- Josh Tenorio (Lieutenant Governor of Guam)
- Charissa Tenorio
- Matthew Green (Cryptography Expert)
7. Thematic Tags
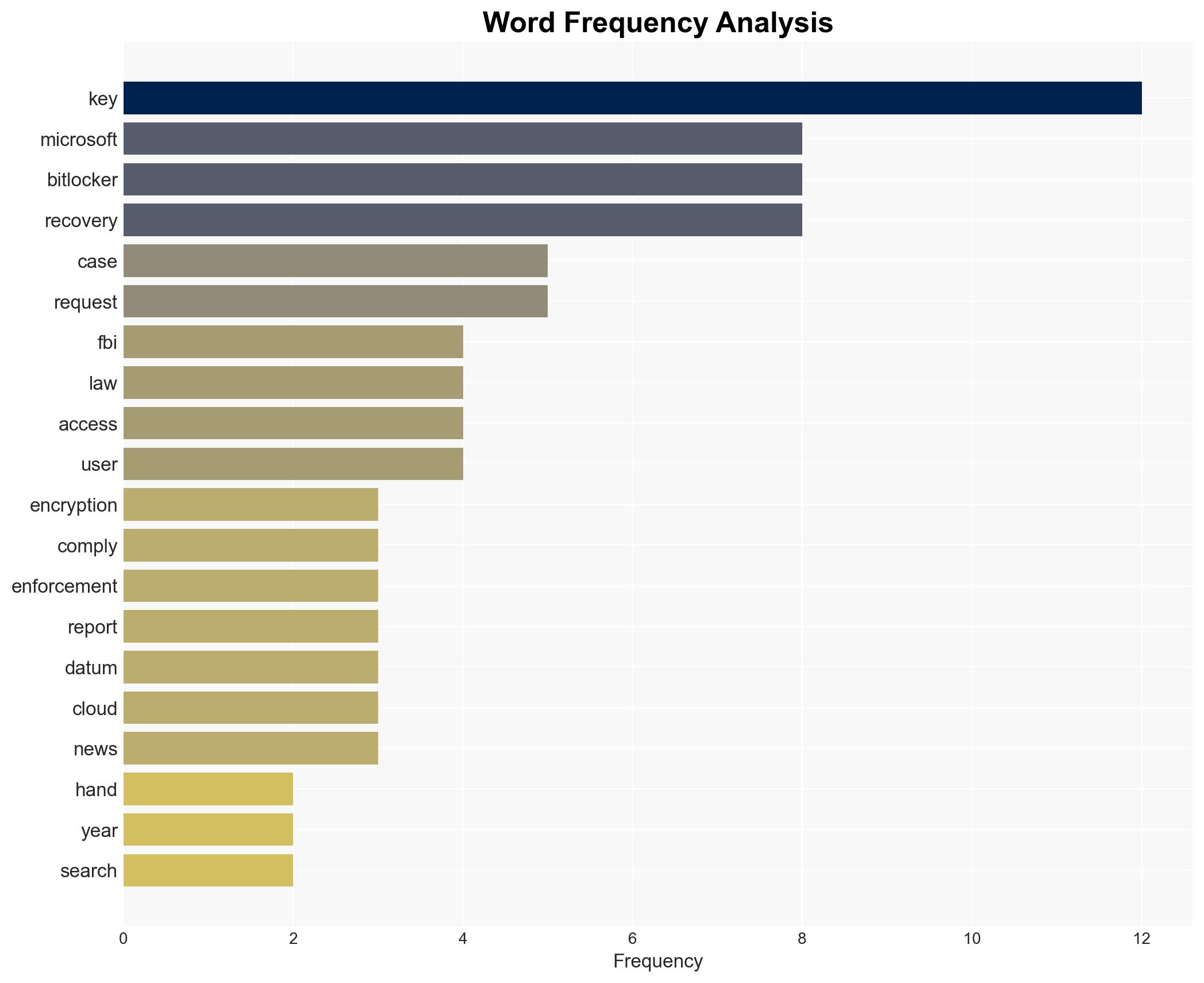
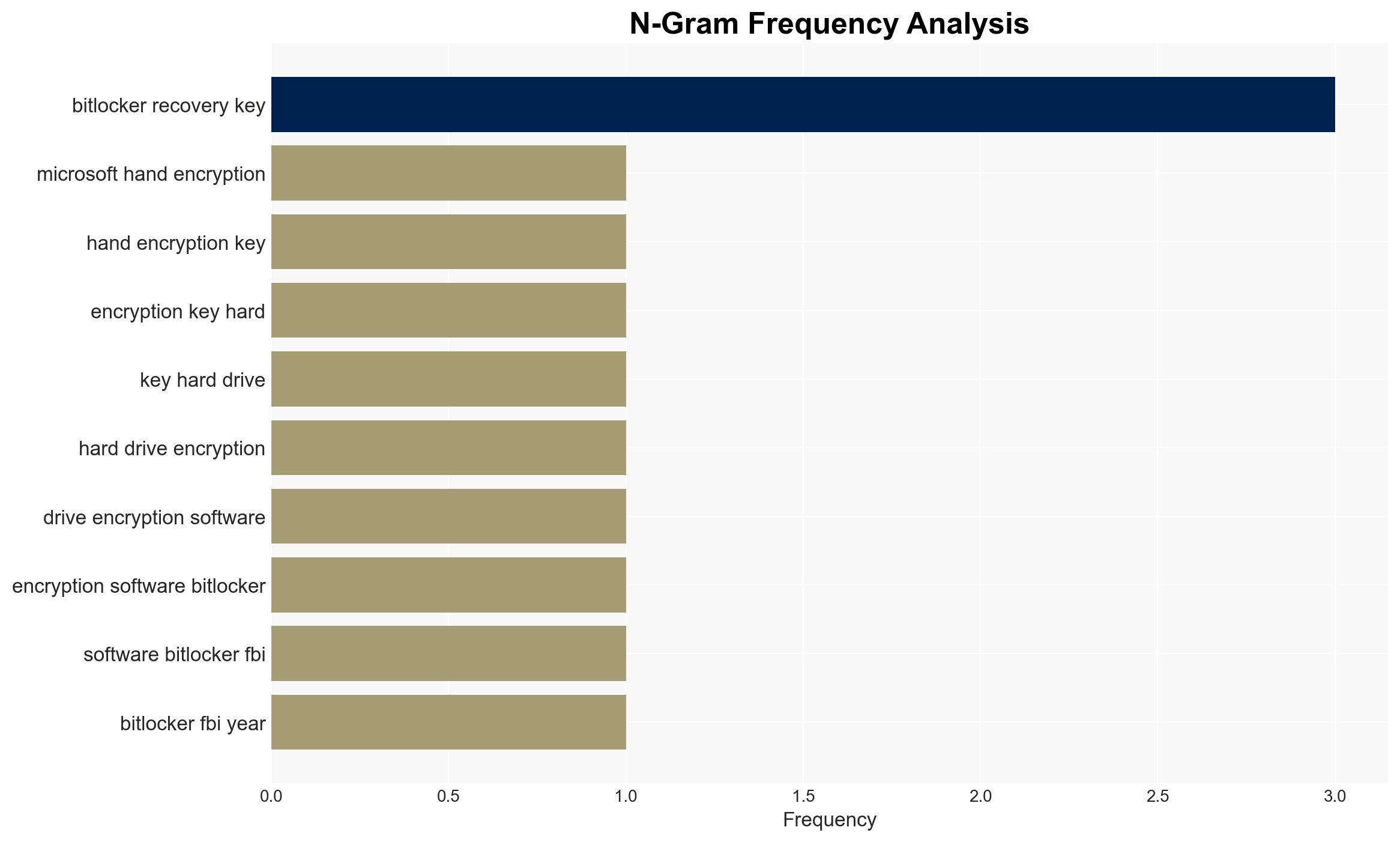
cybersecurity, encryption, data privacy, law enforcement, cloud security, cyber vulnerabilities, tech compliance, user trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us