Sandworm Group Attempts Cyber Attack on Polish Power Sector Using New DynoWiper Malware
Published on: 2026-01-24
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New DynoWiper Malware Used in Attempted Sandworm Attack on Polish Power Sector
1. BLUF (Bottom Line Up Front)
The Sandworm hacking group, linked to Russian state actors, attempted a significant cyber attack on Poland’s power sector using the new DynoWiper malware. The attack was unsuccessful, but it highlights ongoing threats to critical infrastructure. The most likely hypothesis is that this was a politically motivated operation to destabilize Poland and test its defenses. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was a deliberate attempt by Sandworm, under Russian direction, to disrupt Poland’s energy sector as part of broader geopolitical tensions. This is supported by historical patterns of Sandworm’s activities and the timing coinciding with the anniversary of a previous attack on Ukraine. However, the lack of successful disruption introduces uncertainty.
- Hypothesis B: The attack was an independent operation by Sandworm or a similar group, not directly controlled by the Russian state, aimed at testing new malware capabilities. While this could explain the use of new malware, it is less supported due to the strategic significance of the target and the group’s known affiliations.
- Assessment: Hypothesis A is currently better supported due to the strategic nature of the target and historical context. Indicators such as further cyber activities linked to Russian state interests could reinforce this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Sandworm operates with Russian state support; Poland’s energy sector is a strategic target; DynoWiper is a new tool in Sandworm’s arsenal.
- Information Gaps: Detailed technical analysis of DynoWiper; confirmation of Russian state involvement; full scope of the attack’s objectives.
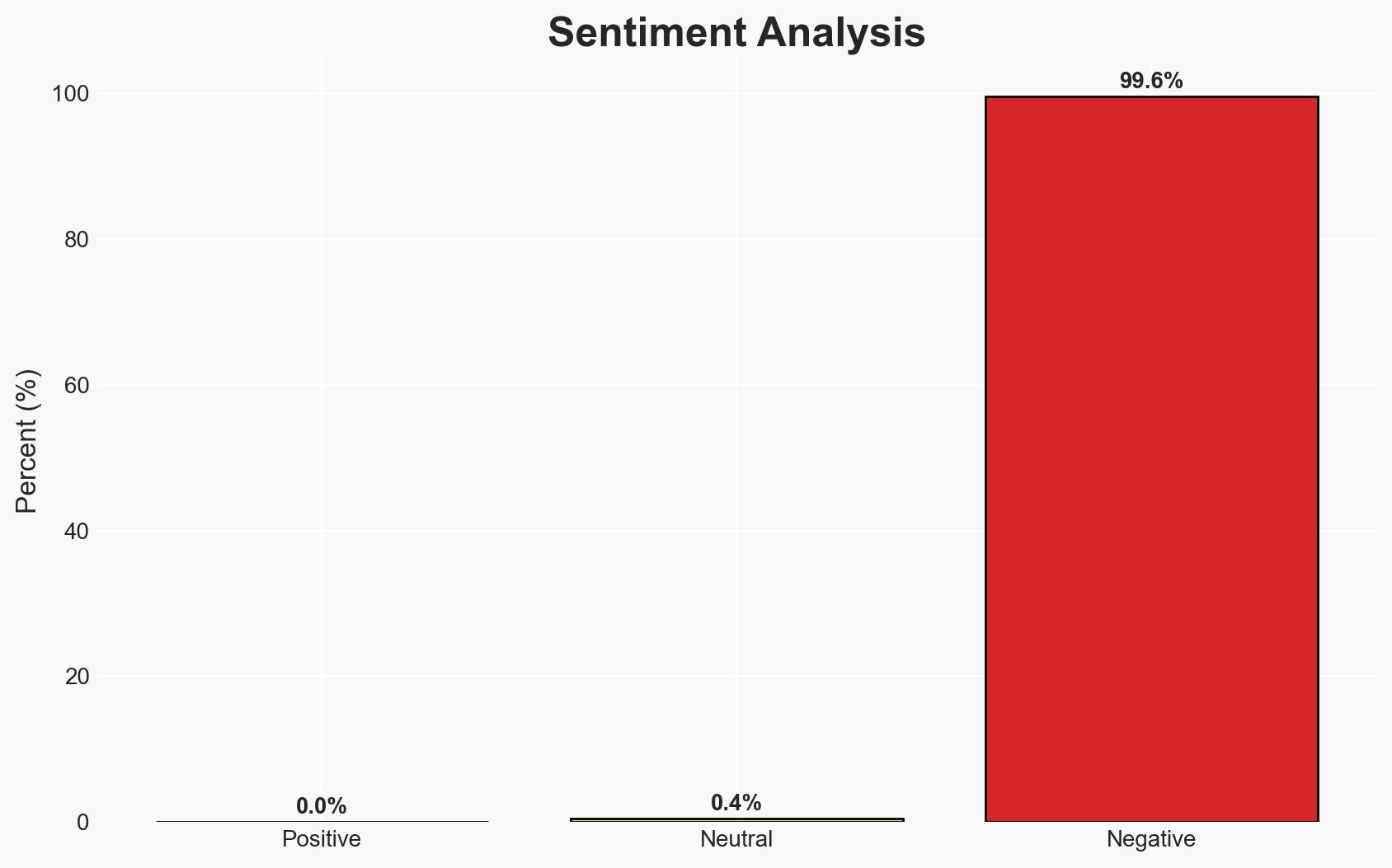
- Bias & Deception Risks: Attribution bias towards Russia; potential misinformation from involved parties; over-reliance on historical patterns.
4. Implications and Strategic Risks
This development could lead to increased tensions between Poland and Russia, with potential for retaliatory cyber measures. It underscores the vulnerability of critical infrastructure to state-sponsored cyber threats.
- Political / Geopolitical: Escalation of cyber conflict between NATO and Russia; potential diplomatic fallout.
- Security / Counter-Terrorism: Heightened alert for similar attacks on other NATO members; increased focus on cybersecurity defenses.
- Cyber / Information Space: Potential for further cyber espionage and sabotage activities; increased investment in cyber defense capabilities.
- Economic / Social: Potential economic impact from disrupted energy supplies; public concern over cybersecurity resilience.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; conduct joint cybersecurity exercises with NATO allies; issue public awareness campaigns on cyber threats.
- Medium-Term Posture (1–12 months): Develop comprehensive cybersecurity legislation; strengthen international cyber cooperation; invest in advanced threat detection technologies.
- Scenario Outlook:
- Best: Improved cyber defenses deter future attacks, leading to reduced tensions.
- Worst: Successful future attacks cause significant disruption and escalate geopolitical tensions.
- Most-Likely: Continued low-level cyber skirmishes with periodic escalations.
6. Key Individuals and Entities
- Milosz Motyka – Poland’s Energy Minister
- Donald Tusk – Prime Minister of Poland
- Sandworm – Russian nation-state hacking group
- ESET – Slovakian cybersecurity company
7. Thematic Tags
cybersecurity, critical infrastructure, Sandworm, Russia-Poland relations, cyber warfare, energy sector, malware
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us