Massive data breach exposes 149 million stolen credentials, impacting crypto and major social media users
Published on: 2026-01-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Crypto users affected in massive 149M infostealer data dump
1. BLUF (Bottom Line Up Front)
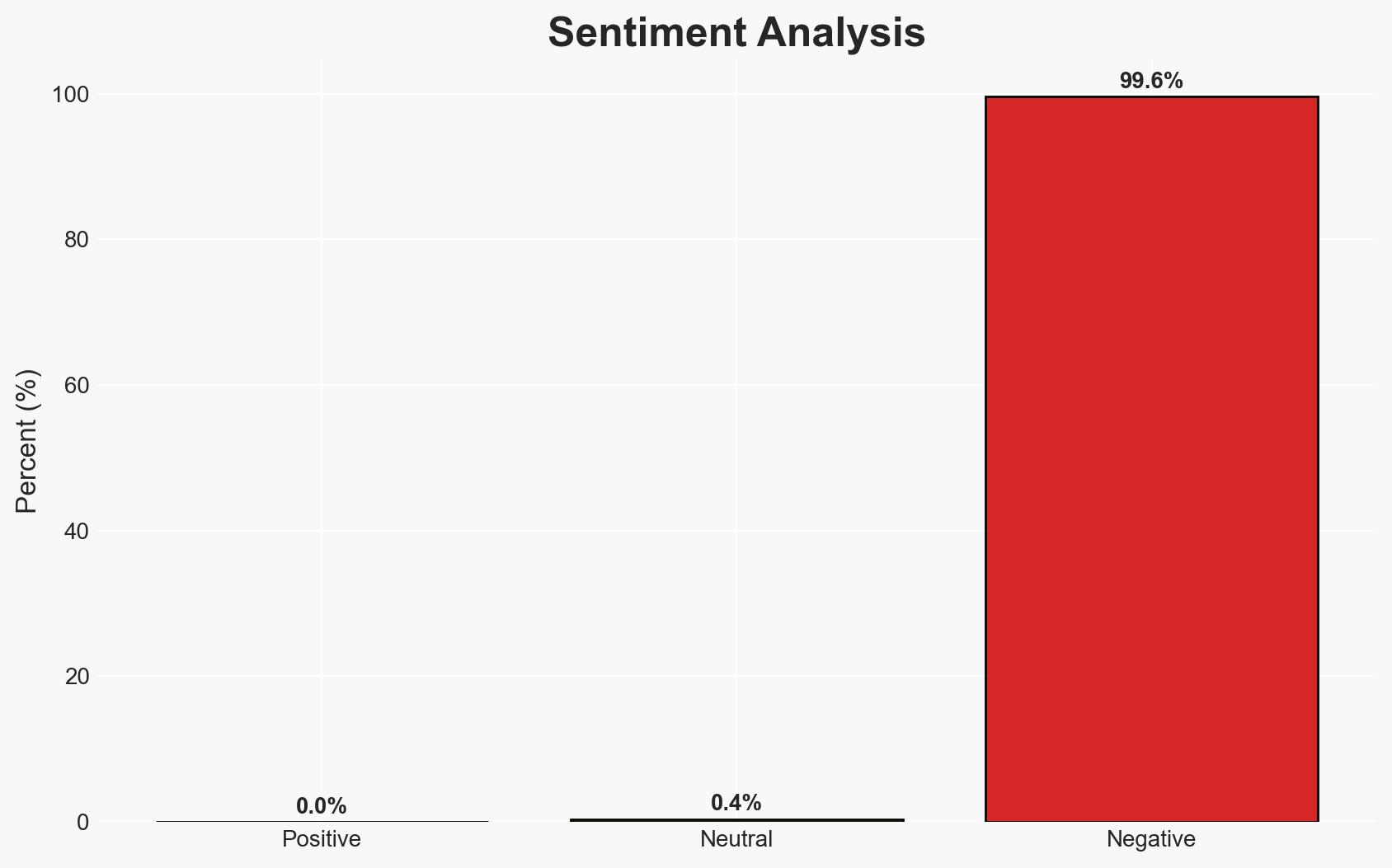
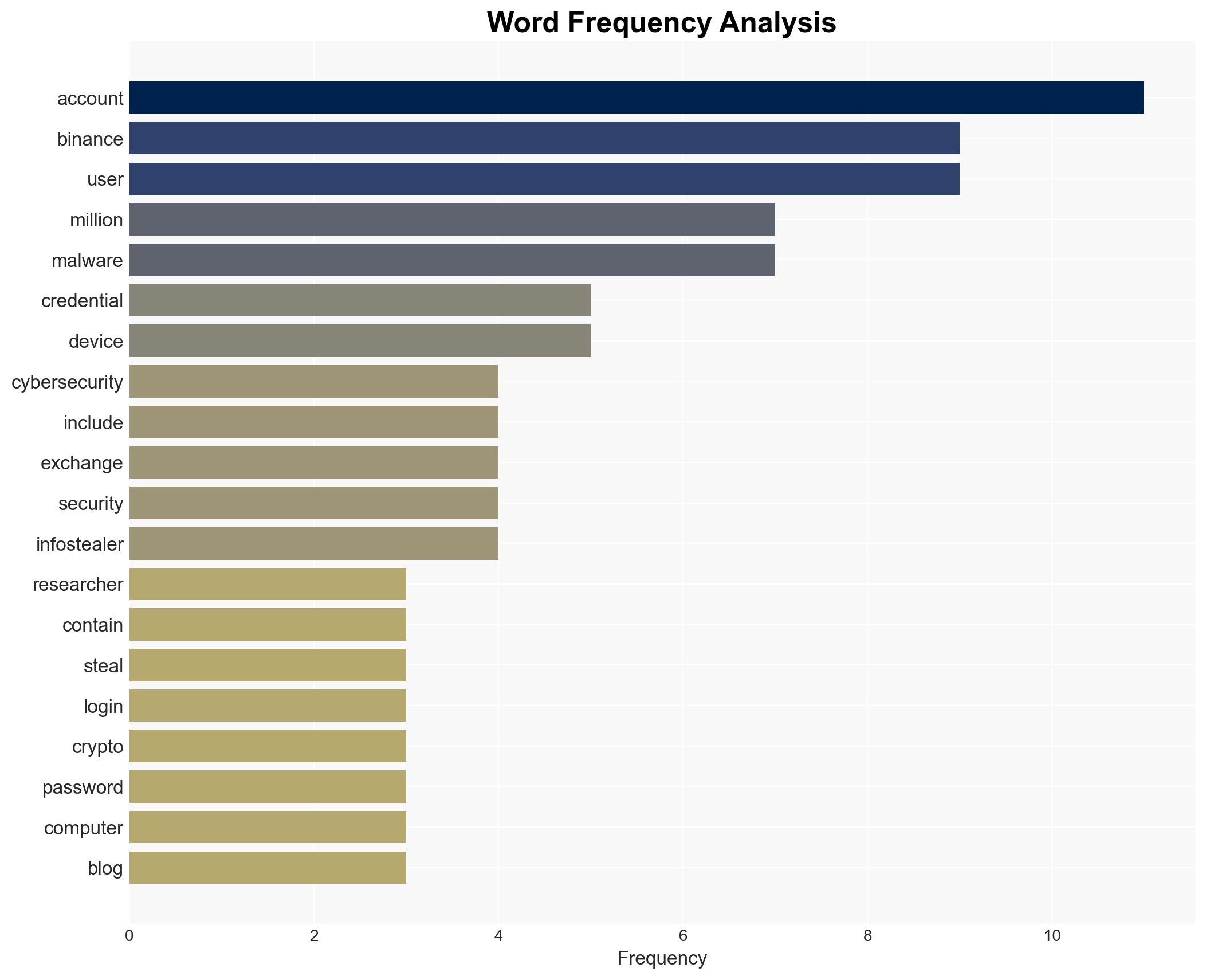
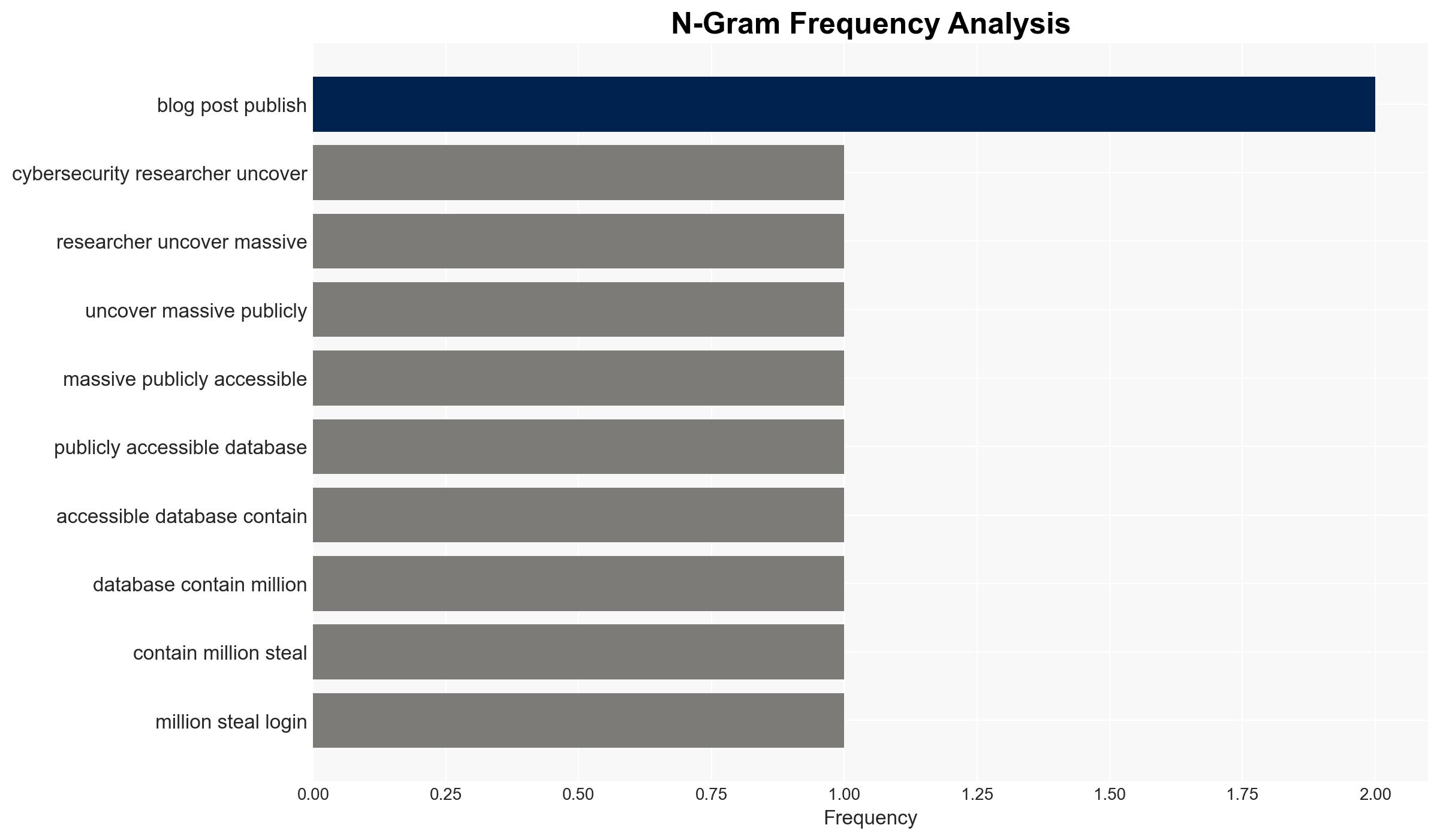
A significant data leak has exposed 149 million login credentials, affecting users of major platforms including Binance, Facebook, and Instagram. The breach stems from infostealer malware on end-user devices rather than a compromise of the platforms themselves. This incident highlights vulnerabilities in user security practices. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The data leak is primarily due to widespread infostealer malware infections on personal devices. This is supported by the nature of the data collection and the lack of evidence for a breach of the platforms’ internal systems. However, the exact scope of the malware’s distribution remains uncertain.
- Hypothesis B: The leak could be part of a coordinated cyber campaign targeting specific platforms or sectors. While the data includes a wide range of services, the high number of Binance-related credentials could suggest a targeted effort. Contradicting this is the lack of direct evidence linking the leak to a single coordinated attack.
- Assessment: Hypothesis A is currently better supported due to the evidence of infostealer malware activity and the absence of platform breaches. Indicators such as new malware variants or coordinated phishing campaigns could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The malware primarily targets individual users; the platforms’ internal systems remain secure; affected users have not yet been fully notified.
- Information Gaps: The full extent of the malware’s distribution and the specific vulnerabilities exploited remain unclear.
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests; risk of underestimating the coordination level of the attack.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on user security practices and platform responses. The incident may prompt regulatory actions or shifts in user behavior.
- Political / Geopolitical: Potential for increased regulatory pressure on tech companies to enhance user security.
- Security / Counter-Terrorism: Heightened risk of phishing and impersonation attacks, particularly against government-linked accounts.
- Cyber / Information Space: Possible escalation in malware sophistication and distribution methods.
- Economic / Social: Erosion of trust in digital platforms could impact user engagement and economic activity in affected sectors.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web activities, alert affected users, and enforce password resets.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, promote user education on security hygiene, and invest in advanced malware detection technologies.
- Scenario Outlook:
- Best: Rapid containment of malware spread, minimal impact on user trust.
- Worst: Proliferation of similar malware, leading to widespread credential theft and financial losses.
- Most-Likely: Gradual improvement in user security practices, with ongoing malware threats requiring continuous vigilance.
6. Key Individuals and Entities
- Jeremiah Fowler – Cybersecurity Researcher
- Binance – Cryptocurrency Exchange
- Deddy Lavid – CEO, Cyvers
- Kaspersky – Cybersecurity Firm
- ExpressVPN – Blog Post Source
7. Thematic Tags
cybersecurity, data breach, cryptocurrency, malware, user security, phishing, regulatory impact
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us