WorldLeaks Claims Nike Data Breach, Leaks 1.4TB of Sensitive Files Online
Published on: 2026-01-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Nike Data Breach Claims Surface as WorldLeaks Leaks 14TB of Files Online
1. BLUF (Bottom Line Up Front)
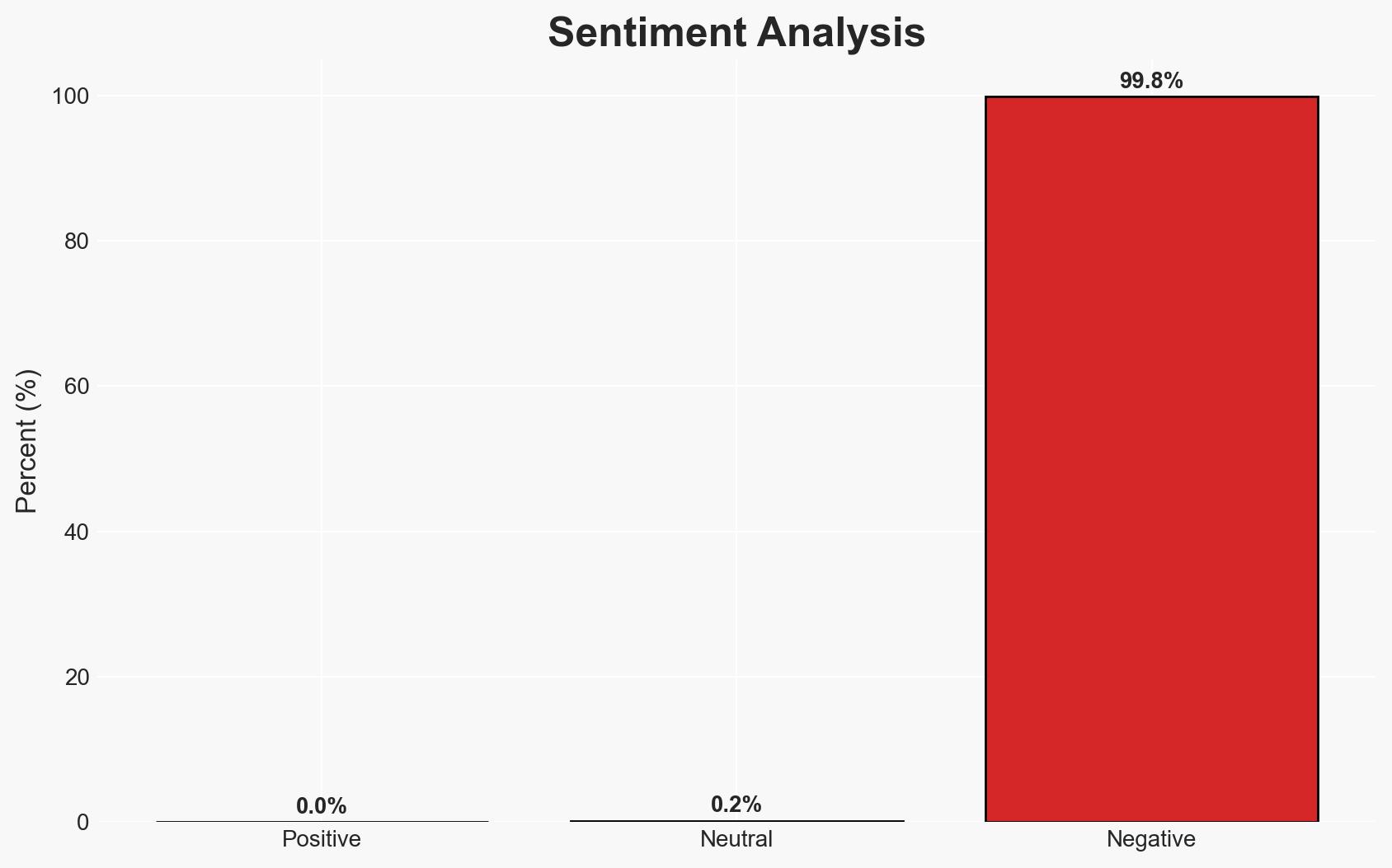
The WorldLeaks group claims to have breached Nike, exfiltrating 1.4TB of sensitive data. The breach primarily involves product development and operational documents, posing significant risks to Nike’s competitive edge and operational security. Current evidence moderately supports the hypothesis that WorldLeaks successfully accessed and leaked the data. The affected parties include Nike, its partners, and potentially the broader athletic apparel market.
2. Competing Hypotheses
- Hypothesis A: WorldLeaks successfully breached Nike’s systems and exfiltrated 1.4TB of data. Supporting evidence includes the group’s history of similar breaches and the detailed nature of the leaked data. However, the authenticity of the data and the full extent of the breach remain unverified, representing key uncertainties.
- Hypothesis B: The breach claims are exaggerated or fabricated by WorldLeaks to enhance their reputation or for other strategic purposes. Contradicting evidence includes the lack of immediate confirmation from Nike and potential motivations for deception. However, the group’s previous successful breaches lend some credibility to their claims.
- Assessment: Hypothesis A is currently better supported due to the detailed nature of the leaked data and WorldLeaks’ track record. Verification of data authenticity and further investigation by Nike could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The data claimed to be leaked is authentic; WorldLeaks has the capability to breach large corporations; Nike’s response is based on preliminary assessments.
- Information Gaps: Verification of the data’s authenticity and the breach’s impact on Nike’s operations; details on how the breach was executed.
- Bias & Deception Risks: Potential bias in reporting from WorldLeaks to exaggerate their capabilities; risk of misinterpretation of the data’s significance without full context.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of corporate cybersecurity practices and potential regulatory responses. The breach may also influence competitive dynamics within the athletic apparel industry.
- Political / Geopolitical: Potential for increased regulatory pressure on data protection and cybersecurity standards.
- Security / Counter-Terrorism: Heightened threat environment for corporations, necessitating enhanced security measures.
- Cyber / Information Space: Possible increase in cyber-espionage activities targeting intellectual property and operational data.
- Economic / Social: Potential financial losses for Nike and its partners; erosion of consumer trust if customer data is perceived at risk.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Nike should conduct a comprehensive forensic investigation, engage with cybersecurity experts, and communicate transparently with stakeholders.
- Medium-Term Posture (1–12 months): Enhance cybersecurity infrastructure, develop partnerships for threat intelligence sharing, and review data protection policies.
- Scenario Outlook:
- Best: Breach claims are disproven, minimal impact on Nike.
- Worst: Data authenticity confirmed, leading to significant operational and financial repercussions.
- Most-Likely: Partial confirmation of breach, resulting in moderate operational adjustments and increased cybersecurity measures.
6. Key Individuals and Entities
- WorldLeaks (formerly Hunters International)
- Nike, Inc.
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, corporate espionage, intellectual property, operational security, ransomware, supply chain risk
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us