Nike Investigates Data Breach as WorldLeaks Claims Theft of 1.4TB of Internal Files
Published on: 2026-01-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Data thieves borrow Nike’s ‘Just Do It’ mantra claim they ran off with 14TB
1. BLUF (Bottom Line Up Front)
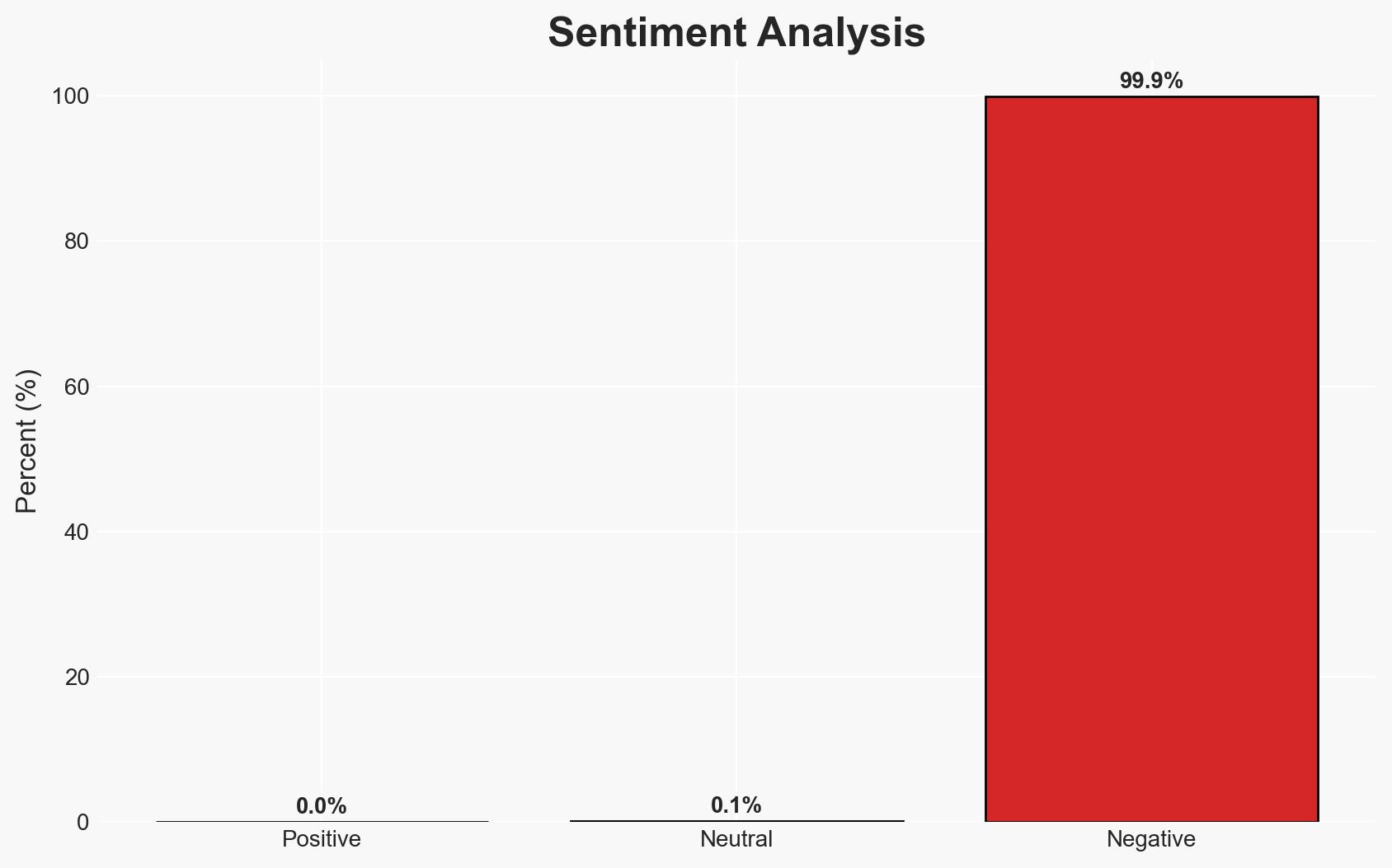
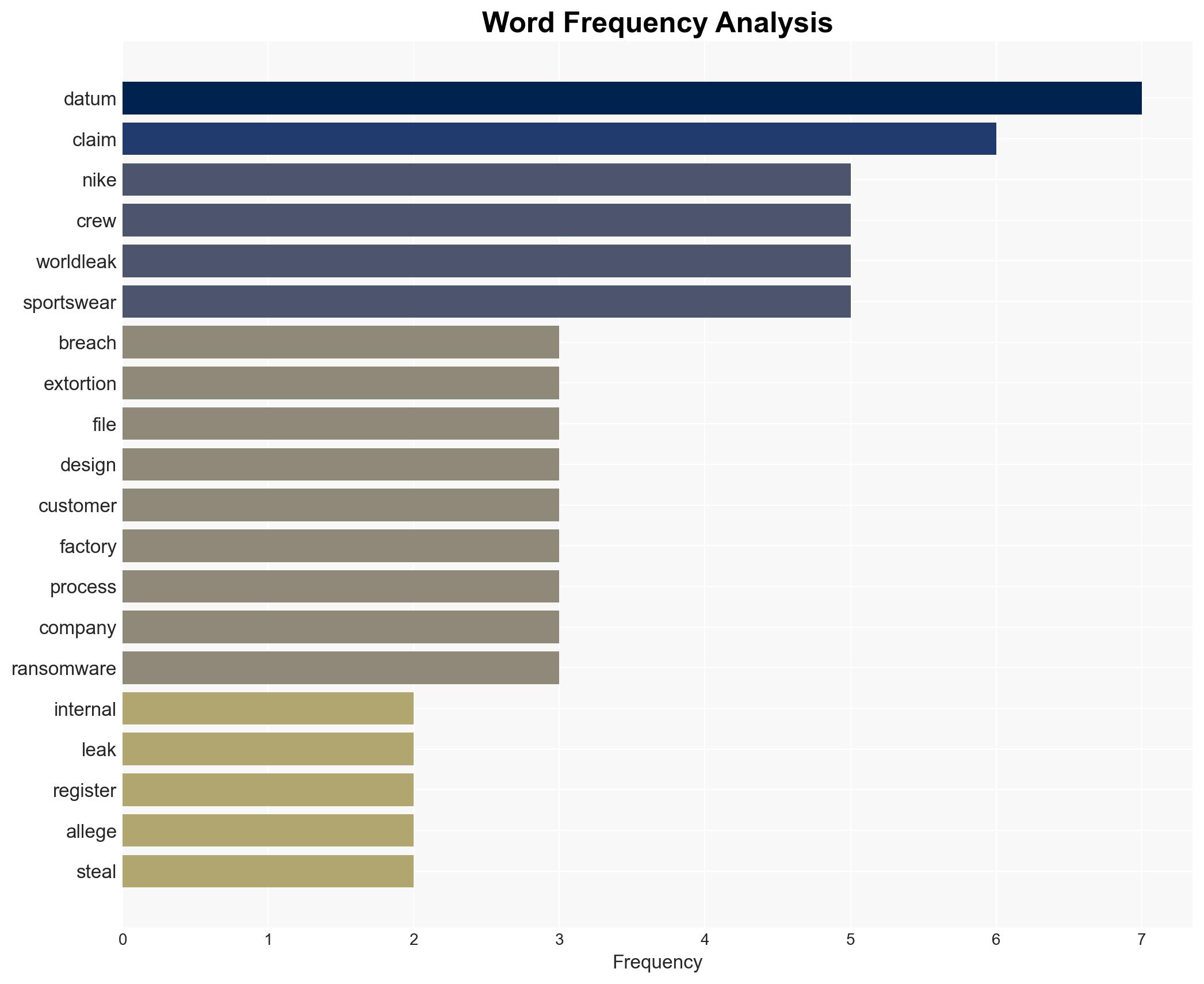
The extortion group WorldLeaks claims to have stolen 1.4TB of internal data from Nike, focusing on design and manufacturing processes. This incident highlights the vulnerability of fashion and sportswear companies to cyber extortion, with moderate confidence in the assessment that WorldLeaks’ claims are credible based on their history and tactics. The breach could lead to significant economic and competitive risks for Nike.
2. Competing Hypotheses
- Hypothesis A: WorldLeaks successfully exfiltrated 1.4TB of sensitive Nike data. Supporting evidence includes the group’s history of similar operations and the publication of sample data. Contradicting evidence includes Nike’s non-confirmation of the breach’s extent and the lack of customer data involvement. Key uncertainties involve the actual volume and sensitivity of the data taken.
- Hypothesis B: WorldLeaks is exaggerating the breach to increase leverage for extortion. Supporting evidence includes the common tactic of inflating claims to pressure victims. Contradicting evidence includes the specific nature of the data described, which aligns with known Nike operations.
- Assessment: Hypothesis A is currently better supported due to WorldLeaks’ established modus operandi and the specificity of the leaked data. Indicators that could shift this judgment include Nike’s confirmation of data specifics or evidence of deceptive practices by WorldLeaks.
3. Key Assumptions and Red Flags
- Assumptions: WorldLeaks has the technical capability to breach Nike’s systems; the data claimed aligns with Nike’s operational processes; Nike’s public statements are accurate reflections of their internal assessments.
- Information Gaps: The exact nature and sensitivity of the stolen data; Nike’s internal cybersecurity posture and response capabilities; potential involvement of third-party vendors.
- Bias & Deception Risks: Potential bias in WorldLeaks’ claims to inflate their success; Nike’s possible underreporting to minimize reputational damage; confirmation bias in assessing WorldLeaks’ credibility based on past activities.
4. Implications and Strategic Risks
This development could lead to increased targeting of fashion and sportswear companies by cybercriminals, exploiting vulnerabilities in global supply chains. The breach may also encourage copycat operations or grey-market production using stolen designs.
- Political / Geopolitical: Limited direct implications, but potential for increased regulatory scrutiny on data protection practices in multinational corporations.
- Security / Counter-Terrorism: No direct counter-terrorism implications, but highlights the evolving threat landscape in cyber extortion.
- Cyber / Information Space: Reinforces the trend of data theft over ransomware, shifting focus to data exfiltration and extortion.
- Economic / Social: Potential economic impact on Nike through competitive disadvantage and reputational damage; possible increase in counterfeit goods.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Nike should conduct a thorough forensic investigation, enhance monitoring of dark web activities for data leaks, and engage with law enforcement and cybersecurity experts.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity measures, particularly around supply chain data; develop partnerships with other industry players for threat intelligence sharing.
- Scenario Outlook:
- Best: Nike contains the breach with minimal data exposure, leading to improved security practices.
- Worst: Significant data exposure leads to competitive losses and regulatory penalties.
- Most-Likely: Moderate data exposure results in temporary reputational damage and increased cybersecurity investment.
6. Key Individuals and Entities
- WorldLeaks (extortion group)
- Nike (victim organization)
- Hunters International (potential predecessor group)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, corporate espionage, supply chain security, cyber extortion, intellectual property theft
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us