Microsoft to comply with FBI requests for BitLocker encryption keys under warrant, highlighting data access r…
Published on: 2026-01-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
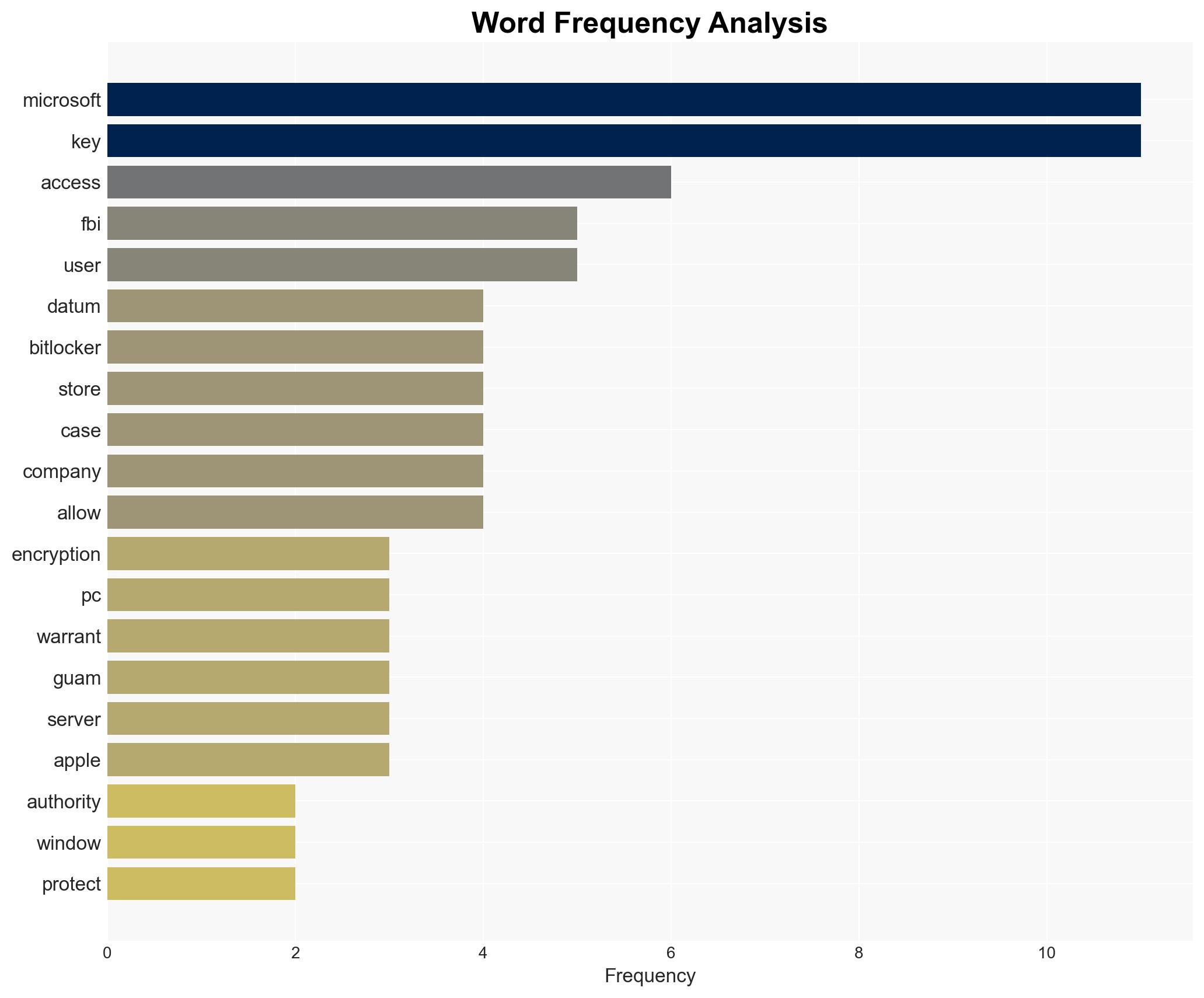
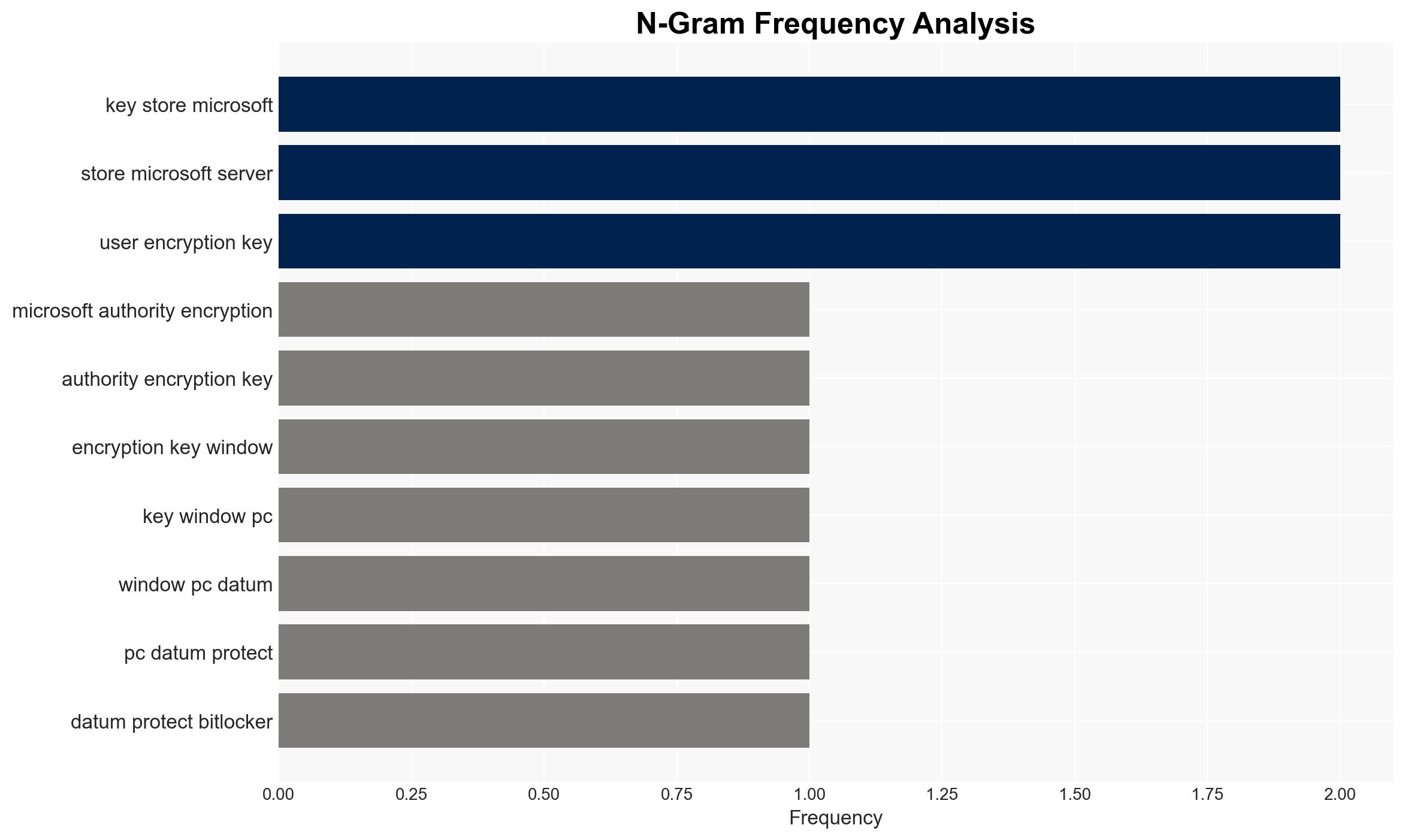
Intelligence Report: Microsoft says sure it’ll hand over your encrypted data to the FBI ‘The lesson here is that if you have access to keys eventually law enforcement is going to come’
1. BLUF (Bottom Line Up Front)
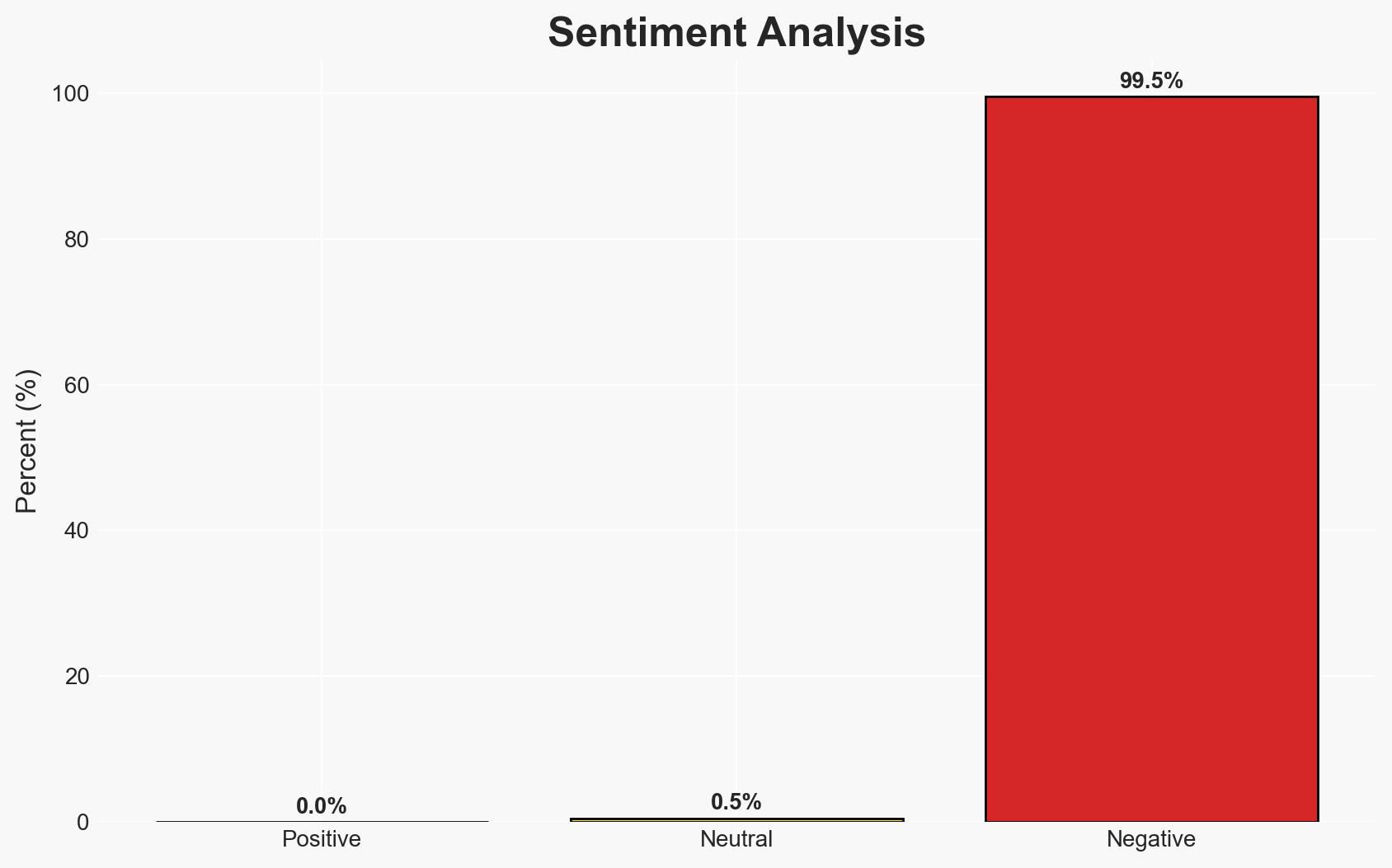
Microsoft’s policy of providing encryption keys to law enforcement upon receiving a warrant poses significant privacy concerns, particularly for users storing keys on Microsoft’s servers. This practice may lead to increased scrutiny and potential regulatory challenges. The most likely hypothesis is that Microsoft will maintain its current policy due to legal obligations and business considerations. Confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Microsoft will continue to comply with law enforcement requests for encryption keys, as it aligns with legal obligations and minimizes potential legal liabilities. Supporting evidence includes Microsoft’s current practice and public statements. Key uncertainties include potential changes in public policy or consumer backlash.
- Hypothesis B: Microsoft will revise its policy to enhance user privacy, potentially by adopting more robust encryption practices similar to Apple or Google. This is contradicted by the lack of current movement towards such a policy change and the ongoing compliance with law enforcement requests.
- Assessment: Hypothesis A is currently best supported due to consistent historical behavior and legal compliance requirements. Indicators that could shift this judgment include significant regulatory changes or a major public relations crisis.
3. Key Assumptions and Red Flags
- Assumptions: Microsoft will prioritize legal compliance over user privacy; law enforcement will continue to seek access to encrypted data; consumer behavior will not significantly shift towards privacy-centric alternatives.
- Information Gaps: Specific details on the frequency and scope of law enforcement requests; potential internal discussions within Microsoft about policy changes.
- Bias & Deception Risks: Potential bias in public statements by Microsoft aiming to mitigate backlash; risk of underestimating consumer privacy concerns.
4. Implications and Strategic Risks
This development could lead to increased tension between tech companies and privacy advocates, influencing regulatory landscapes and consumer trust.
- Political / Geopolitical: Potential for increased regulatory scrutiny and legislative action on data privacy.
- Security / Counter-Terrorism: Enhanced law enforcement capabilities in accessing encrypted data, potentially improving counter-terrorism efforts.
- Cyber / Information Space: Risk of increased cyber threats targeting Microsoft’s cloud services to access stored encryption keys.
- Economic / Social: Possible consumer shift towards companies with stronger privacy protections, impacting market dynamics.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor regulatory developments and public reactions; assess potential impacts on consumer trust and market position.
- Medium-Term Posture (1–12 months): Develop strategies to enhance transparency and user control over encryption keys; engage with policymakers to shape privacy regulations.
- Scenario Outlook: Best: Microsoft enhances privacy measures, gaining consumer trust. Worst: Regulatory penalties and consumer backlash lead to market share loss. Most-Likely: Continued compliance with law enforcement, with gradual policy adjustments in response to regulatory pressures.
6. Key Individuals and Entities
- Microsoft
- FBI
- Apple
- Meta
- Senator Ron Wyden
- Matt Green, Johns Hopkins University
7. Thematic Tags
cybersecurity, data privacy, encryption, law enforcement, cyber security, regulatory compliance, consumer trust, tech policy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us