Multi-Stage Phishing Campaign Targets Russian Users with Amnesia RAT and Ransomware via Fake Business Documen…
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
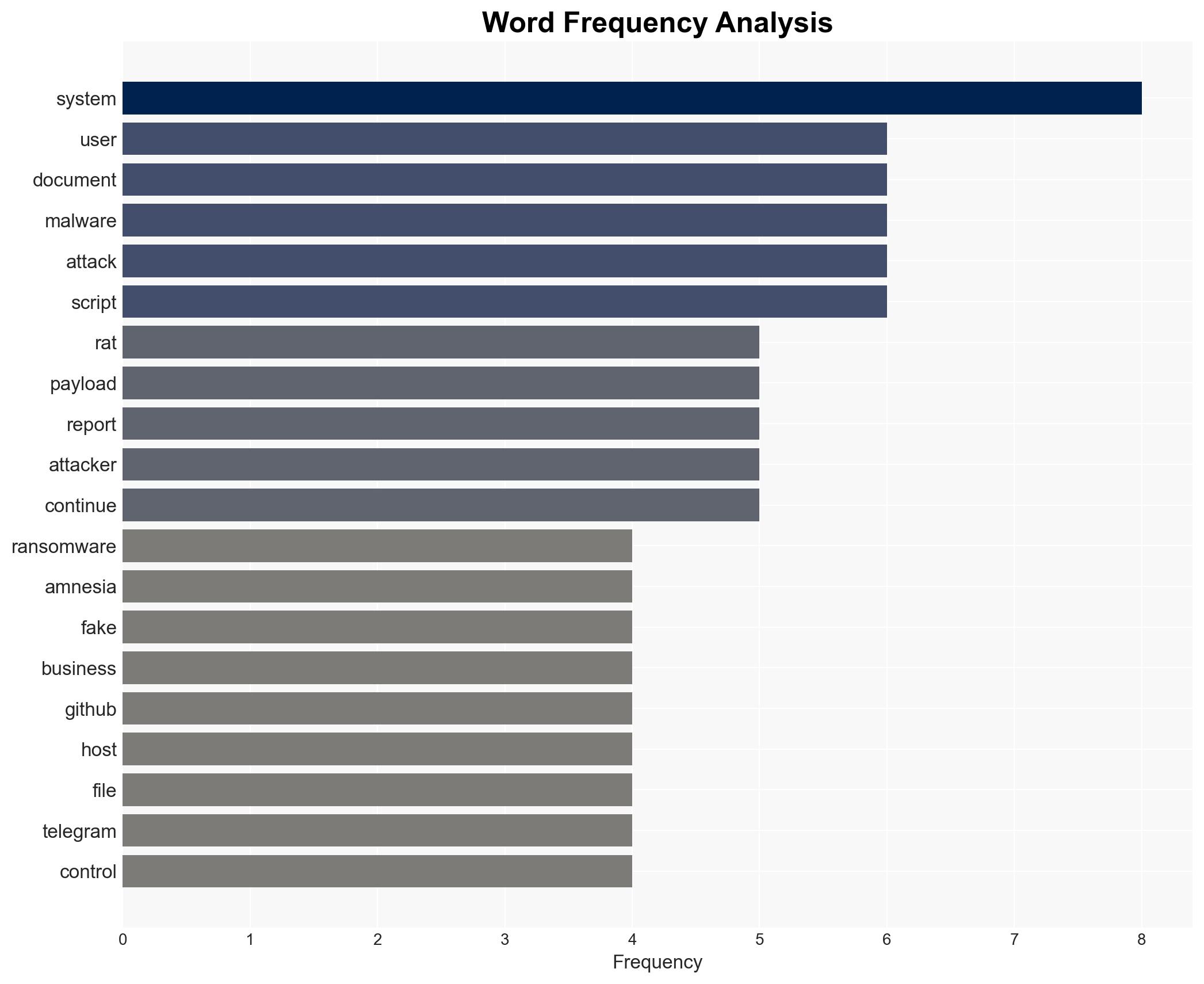
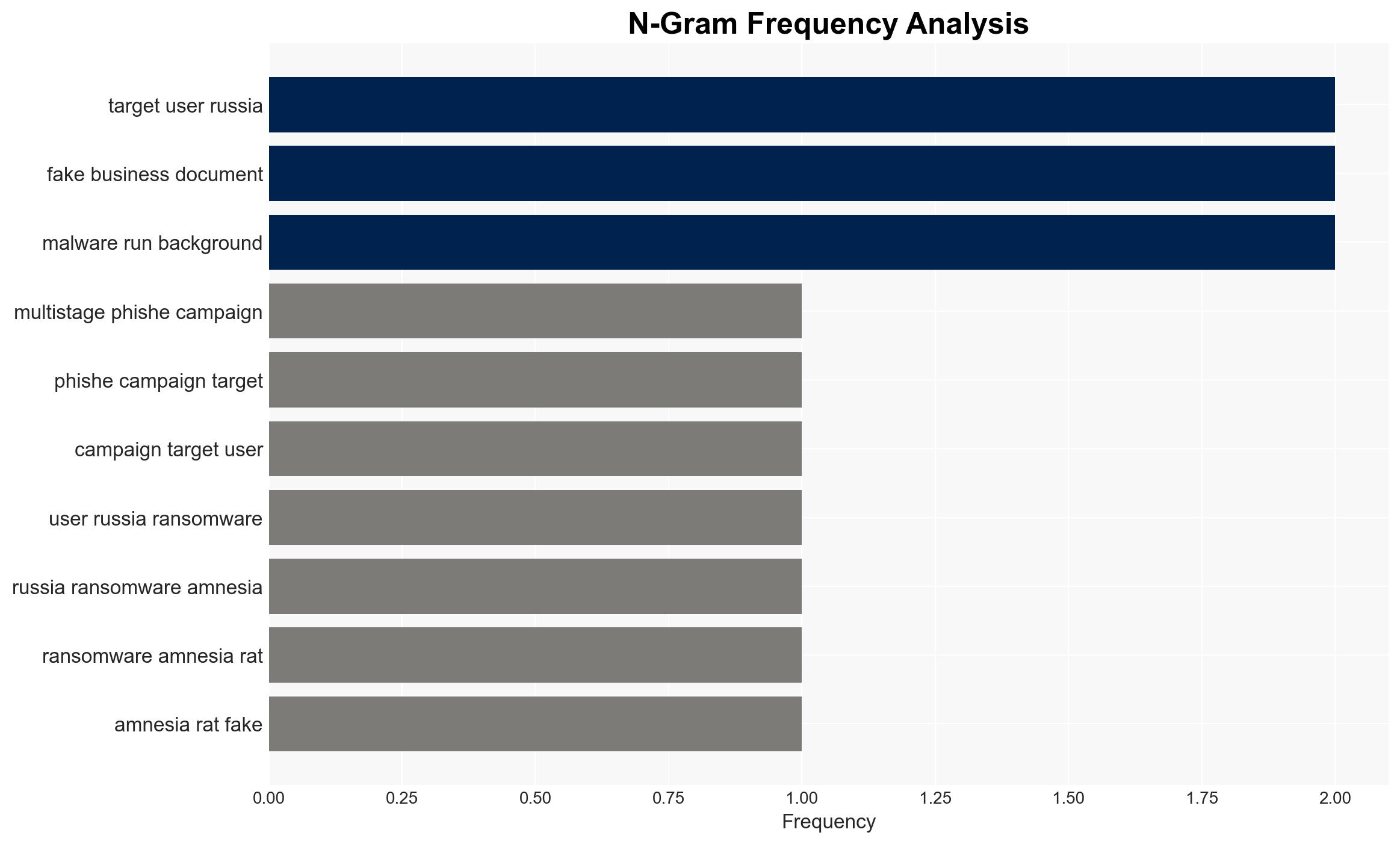
Intelligence Report: Amnesia RAT deployed in multi-stage phishing attacks against Russian users
1. BLUF (Bottom Line Up Front)
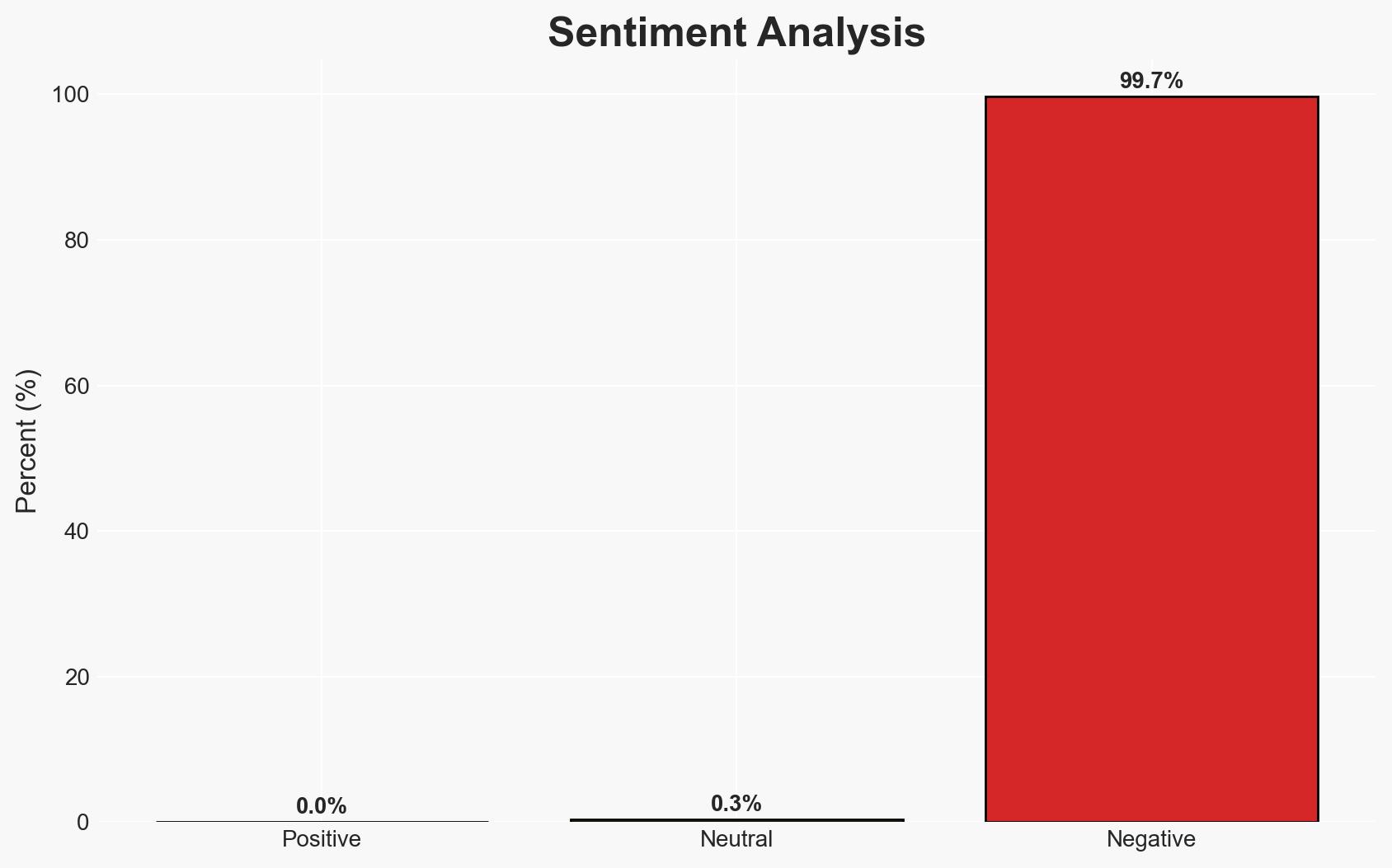
The Amnesia RAT has been deployed in a sophisticated multi-stage phishing campaign targeting Russian users, leveraging fake business documents to execute malware. This campaign poses a significant threat to corporate environments due to its reliance on social engineering and cloud-based payload hosting. The most likely hypothesis is that the campaign is orchestrated by a financially motivated cybercriminal group. Overall confidence in this assessment is moderate due to existing information gaps and potential deception indicators.
2. Competing Hypotheses
- Hypothesis A: The campaign is conducted by a financially motivated cybercriminal group targeting Russian corporate users to extract ransom payments. This is supported by the use of ransomware and the targeting of business environments. However, the specific group identity remains unclear, and the absence of direct attribution limits certainty.
- Hypothesis B: The campaign is a state-sponsored operation aimed at disrupting Russian economic activities or gathering intelligence. This is contradicted by the lack of sophisticated exploits and the focus on financial gain rather than strategic intelligence collection.
- Assessment: Hypothesis A is currently better supported due to the financial nature of the attack and the use of ransomware. Indicators such as ransom demands or further targeting of financial sectors could reinforce this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attackers are financially motivated; the use of GitHub and Dropbox is primarily for evasion and resilience; Russian users are the primary targets.
- Information Gaps: The identity of the threat actors; specific ransom demands or communications; detailed impact assessment on targeted organizations.
- Bias & Deception Risks: Potential bias in assuming financial motivation without direct evidence; risk of misattribution due to the use of common cloud services; possibility of false flag operations.
4. Implications and Strategic Risks
This development could lead to increased cyber threat levels in Russia and potentially inspire similar tactics globally. The use of cloud services for payload distribution complicates detection and mitigation efforts.
- Political / Geopolitical: Potential for increased tension if attributed to state actors; could influence cyber policy and international cyber norms.
- Security / Counter-Terrorism: Heightened alert for corporate cybersecurity teams; potential for copycat attacks.
- Cyber / Information Space: Demonstrates evolving tactics in cybercrime; highlights vulnerabilities in cloud service security.
- Economic / Social: Potential economic disruption for affected businesses; increased demand for cybersecurity solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cloud service traffic; disseminate phishing awareness training; collaborate with cloud service providers for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures against social engineering; strengthen partnerships with cybersecurity firms; invest in advanced threat detection capabilities.
- Scenario Outlook:
- Best: Effective mitigation and attribution lead to a decline in similar attacks.
- Worst: Escalation to broader regional cyber conflicts or significant economic damage.
- Most-Likely: Continued sporadic attacks with gradual improvements in corporate defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, phishing, cloud services, social engineering, Russian targets, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us