Over 149 Million Usernames and Passwords Exposed, Including Major Services Beyond Email Platforms
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: About any type of account imaginable 149 million usernames and passwords exposed and it’s way more than just Outlook OnlyFans and Gmail
1. BLUF (Bottom Line Up Front)
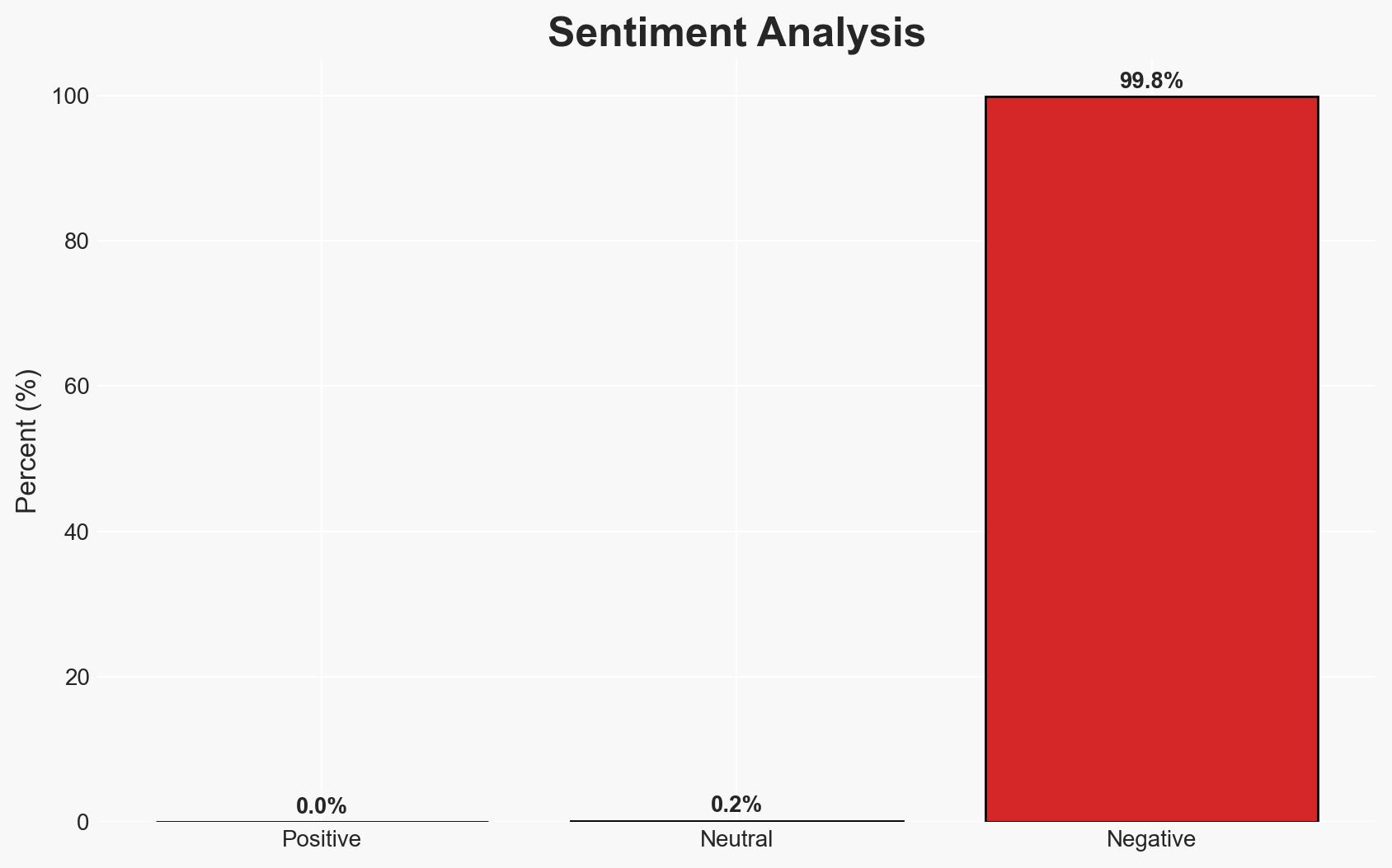
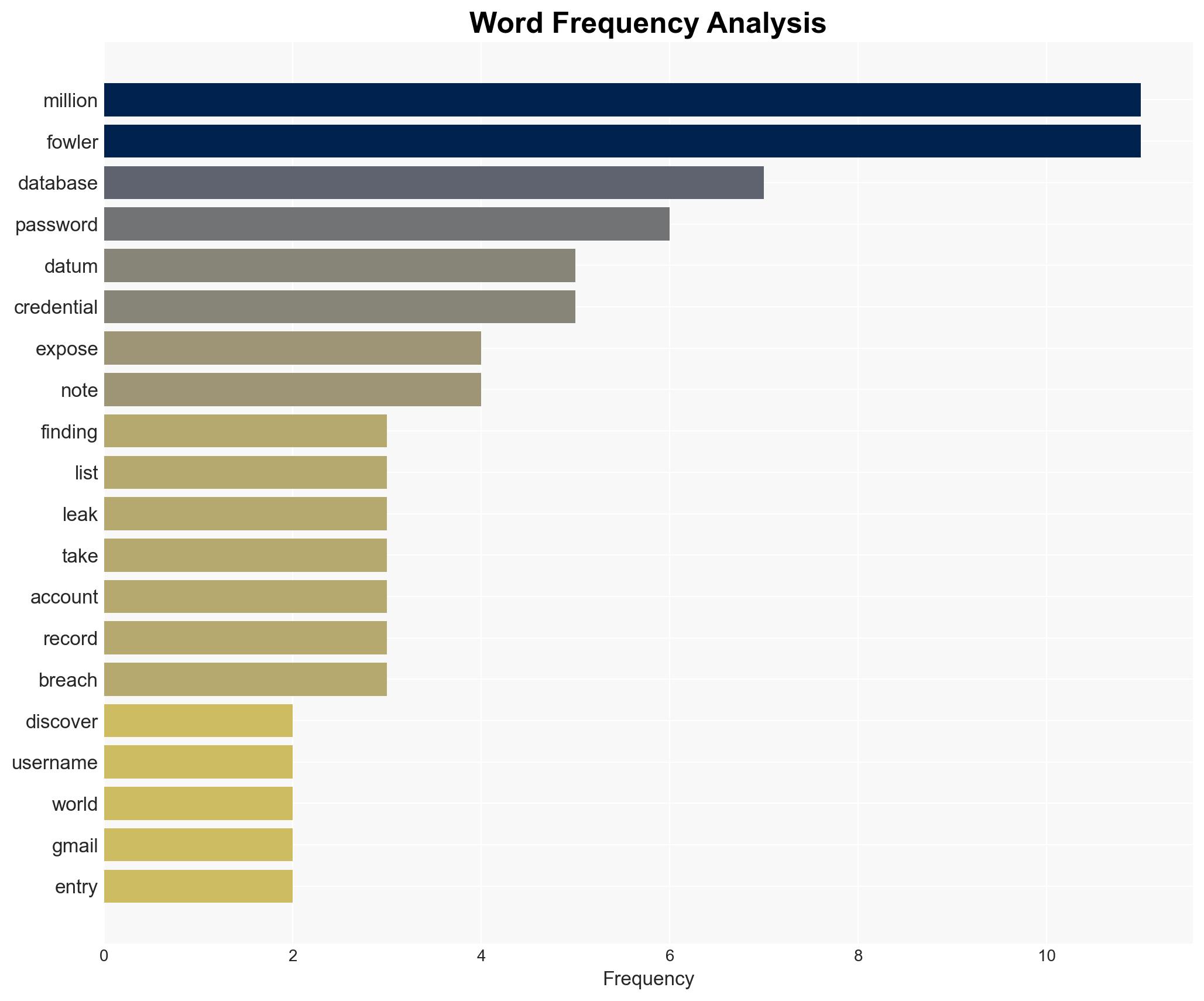
A massive 96GB database containing over 149 million usernames and passwords was exposed, affecting a wide range of online services, including email, social media, and financial accounts. This incident poses significant risks to national security, public safety, and individual privacy. The most likely hypothesis is that the database was compiled over time through malware and subsequently exposed due to a secondary breach. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The database was compiled by a single threat actor using malware over time and was exposed due to a secondary breach. This is supported by the diversity of accounts and the lack of a single breach event. However, uncertainties include the identity of the original threat actor and the timeline of data collection.
- Hypothesis B: Multiple threat actors contributed to the database, which was a collaborative effort in underground markets, and it was exposed accidentally. This is contradicted by the lack of evidence of multiple actors and the consistent methodology suggested by the data collection.
- Assessment: Hypothesis A is currently better supported due to the consistent data collection method and the secondary breach explanation. Indicators that could shift this judgment include evidence of multiple actors or a different breach mechanism.
3. Key Assumptions and Red Flags
- Assumptions: The data was collected via malware; the exposure was unintentional; the database is not linked to a specific nation-state actor; cloud storage was used due to its accessibility.
- Information Gaps: Identity of the original threat actor(s); exact timeline of data collection; potential links to state-sponsored activities.
- Bias & Deception Risks: Source bias from reliance on a single researcher’s findings; potential manipulation of data to obscure true origins or scale.
4. Implications and Strategic Risks
This development could lead to increased cyber threats and exploitation of exposed credentials, affecting both individuals and institutions. The exposure of .gov domain credentials poses a direct risk to national security.
- Political / Geopolitical: Potential for diplomatic tensions if state actors are implicated; increased scrutiny on international cyber norms.
- Security / Counter-Terrorism: Elevated risk of cyber-attacks on government and critical infrastructure; potential use of credentials in terrorist activities.
- Cyber / Information Space: Increased phishing and credential stuffing attacks; potential for misinformation campaigns using compromised accounts.
- Economic / Social: Financial losses from fraud; erosion of trust in digital services; potential social unrest if government systems are compromised.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of affected services; notify users to change passwords; collaborate with cloud providers to secure exposed data.
- Medium-Term Posture (1–12 months): Develop stronger authentication measures; increase public awareness campaigns on cybersecurity; strengthen international cooperation on cybercrime.
- Scenario Outlook: Best: Rapid containment and minimal exploitation; Worst: Widespread use of credentials in cyber-attacks; Most-Likely: Gradual exploitation with increased cyber defenses.
6. Key Individuals and Entities
- Jeremiah Fowler (Cybersecurity Researcher)
- ExpressVPN (Research Publisher)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, national security, malware, credential theft, information security, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us