Investigation launched into potential terrorist act involving explosive device at Indigenous rights protest i…
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
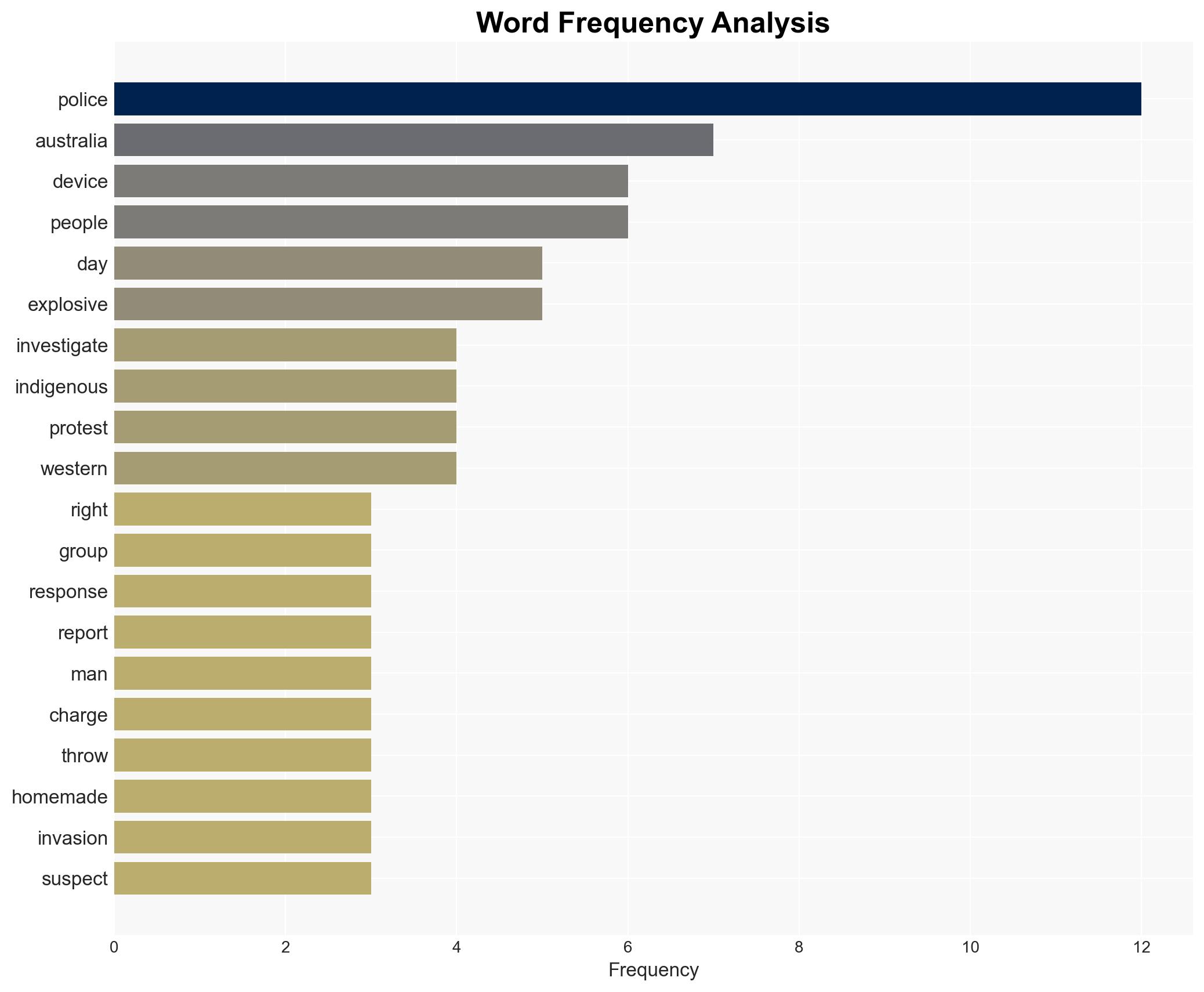
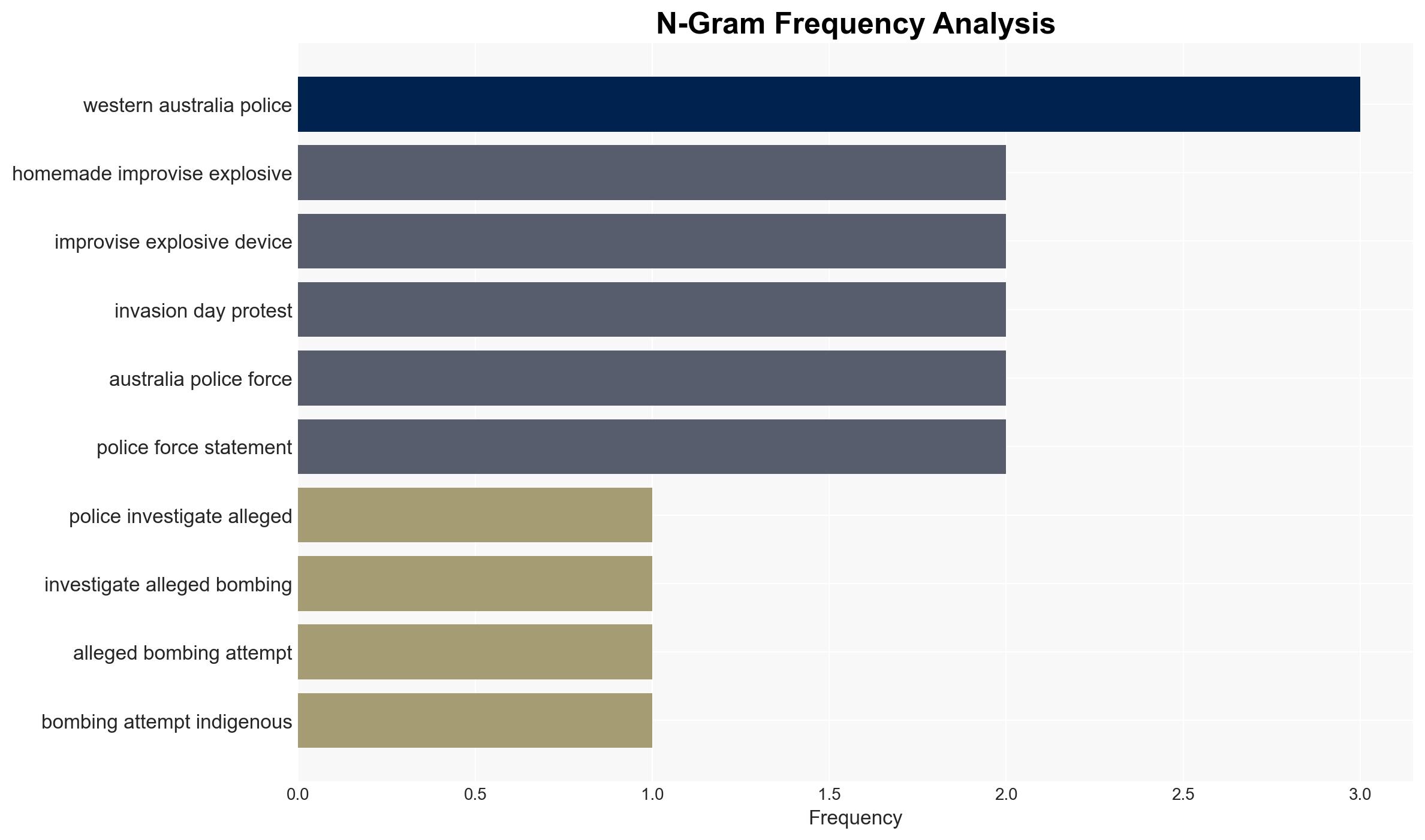
Intelligence Report: Police probe explosive device thrown at Indigenous protest in Australia
1. BLUF (Bottom Line Up Front)
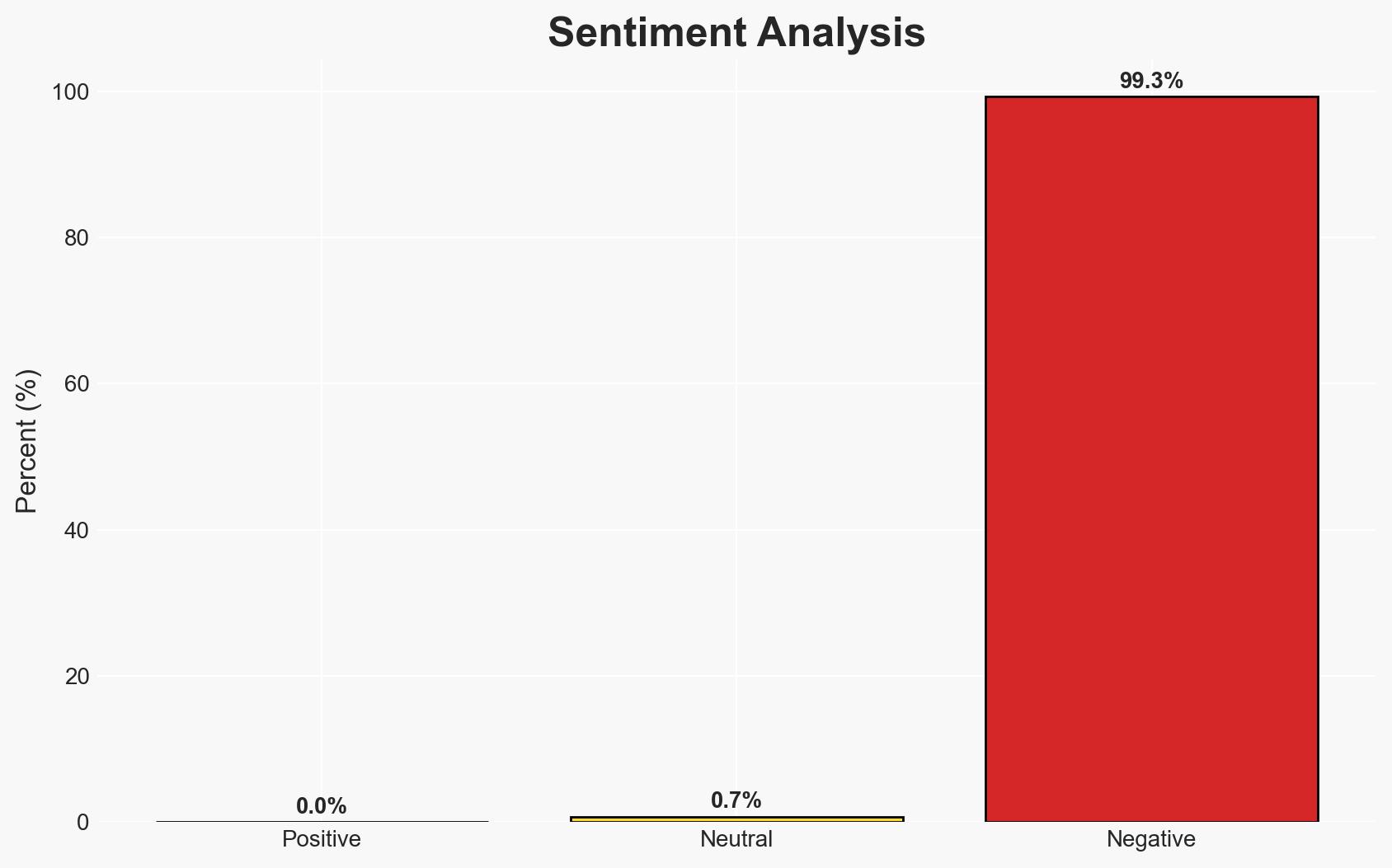
The investigation into an explosive device thrown at an Indigenous protest in Perth is being considered as a potential terrorist act, reflecting heightened tensions around Indigenous rights in Australia. The incident underscores the need for robust law enforcement responses to threats at public gatherings. Moderate confidence in the assessment that the act was intended to intimidate or harm the protestors.
2. Competing Hypotheses
- Hypothesis A: The act was a targeted attempt to intimidate or harm Indigenous protestors, motivated by racial or political animus. Supporting evidence includes the timing during a significant cultural protest and the nature of the device. Key uncertainties include the suspect’s specific motivations and affiliations.
- Hypothesis B: The act was an isolated incident by an individual with no broader political or racial motivations, possibly driven by personal grievances or mental instability. Contradicting evidence includes the premeditated nature of the device and its deployment at a large public event.
- Assessment: Hypothesis A is currently better supported due to the context of the protest and the nature of the device. Indicators that could shift this judgment include evidence of the suspect’s affiliations or communications suggesting broader intent.
3. Key Assumptions and Red Flags
- Assumptions: The suspect acted alone; the device was intended to cause harm; the protest was the primary target.
- Information Gaps: Details on the suspect’s background, motivations, and any affiliations with extremist groups.
- Bias & Deception Risks: Potential bias in interpreting the act as terrorism without clear evidence of political motives; media or public pressure influencing the investigation’s framing.
4. Implications and Strategic Risks
This incident could exacerbate tensions between Indigenous communities and authorities, potentially leading to increased polarization and unrest. It also highlights vulnerabilities in public event security.
- Political / Geopolitical: Potential escalation in Indigenous rights advocacy and government responses.
- Security / Counter-Terrorism: Increased scrutiny on public event security and potential for copycat incidents.
- Cyber / Information Space: Possible exploitation of the incident in online narratives to fuel division.
- Economic / Social: Strain on community relations and potential impacts on tourism or public event participation.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance security measures at public events, conduct thorough investigation into suspect’s background, and engage with Indigenous leaders to address community concerns.
- Medium-Term Posture (1–12 months): Develop community outreach programs to build trust, and enhance intelligence-sharing mechanisms to prevent future incidents.
- Scenario Outlook: Best: Improved relations and security measures prevent future incidents. Worst: Increased tensions lead to further violence. Most-Likely: Continued scrutiny and gradual improvements in security and community relations.
6. Key Individuals and Entities
- Western Australia Police Force
- Hannah McGlade, Indigenous Noongar community member
- Human Rights Law Centre
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, counter-terrorism, Indigenous rights, public safety, hate crime, protest security, racial tensions, law enforcement
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us