State-sponsored and criminal groups exploit critical WinRAR vulnerability for initial access and malware depl…
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Nation-state and criminal actors leverage WinRAR flaw in attacks
1. BLUF (Bottom Line Up Front)
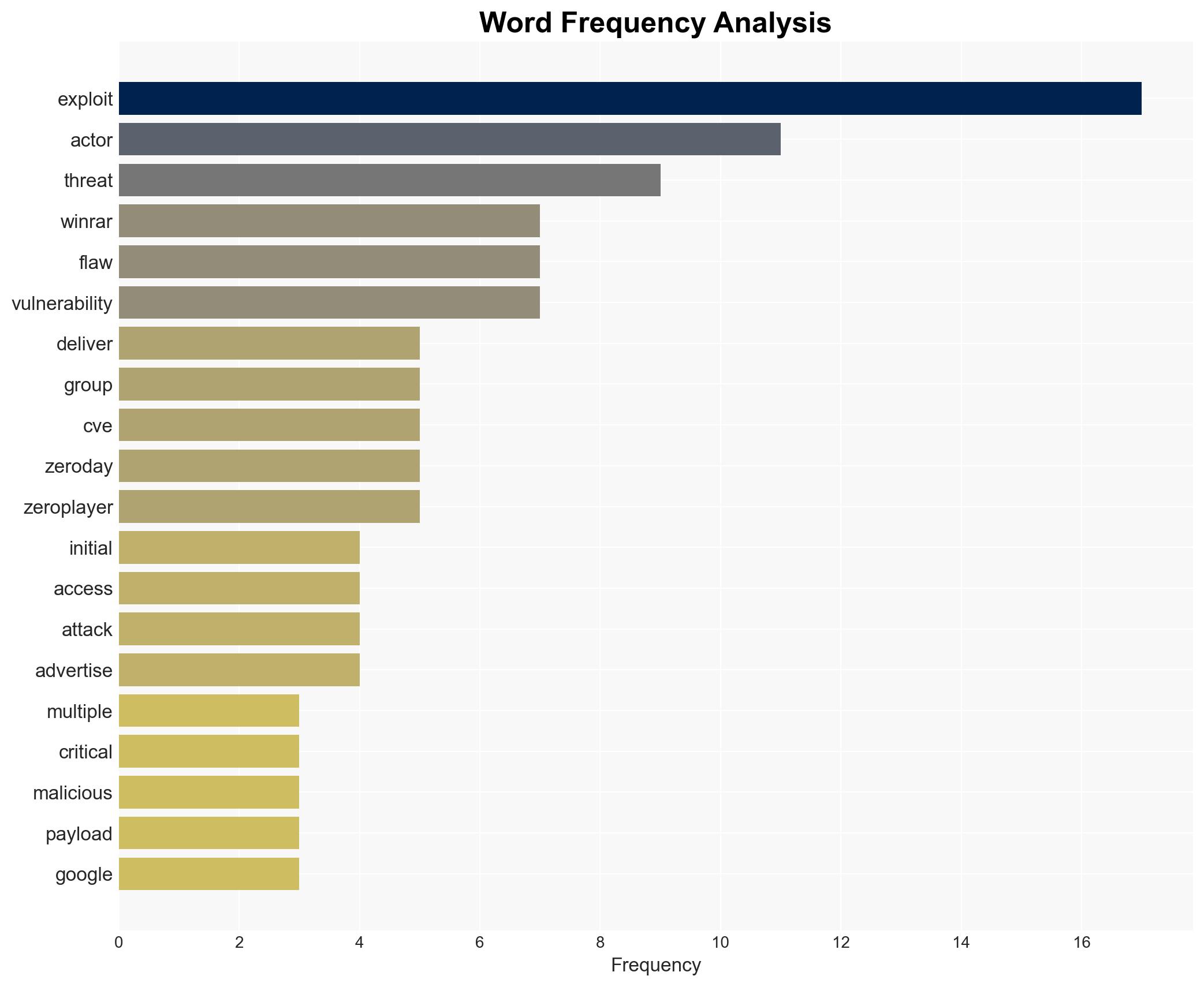
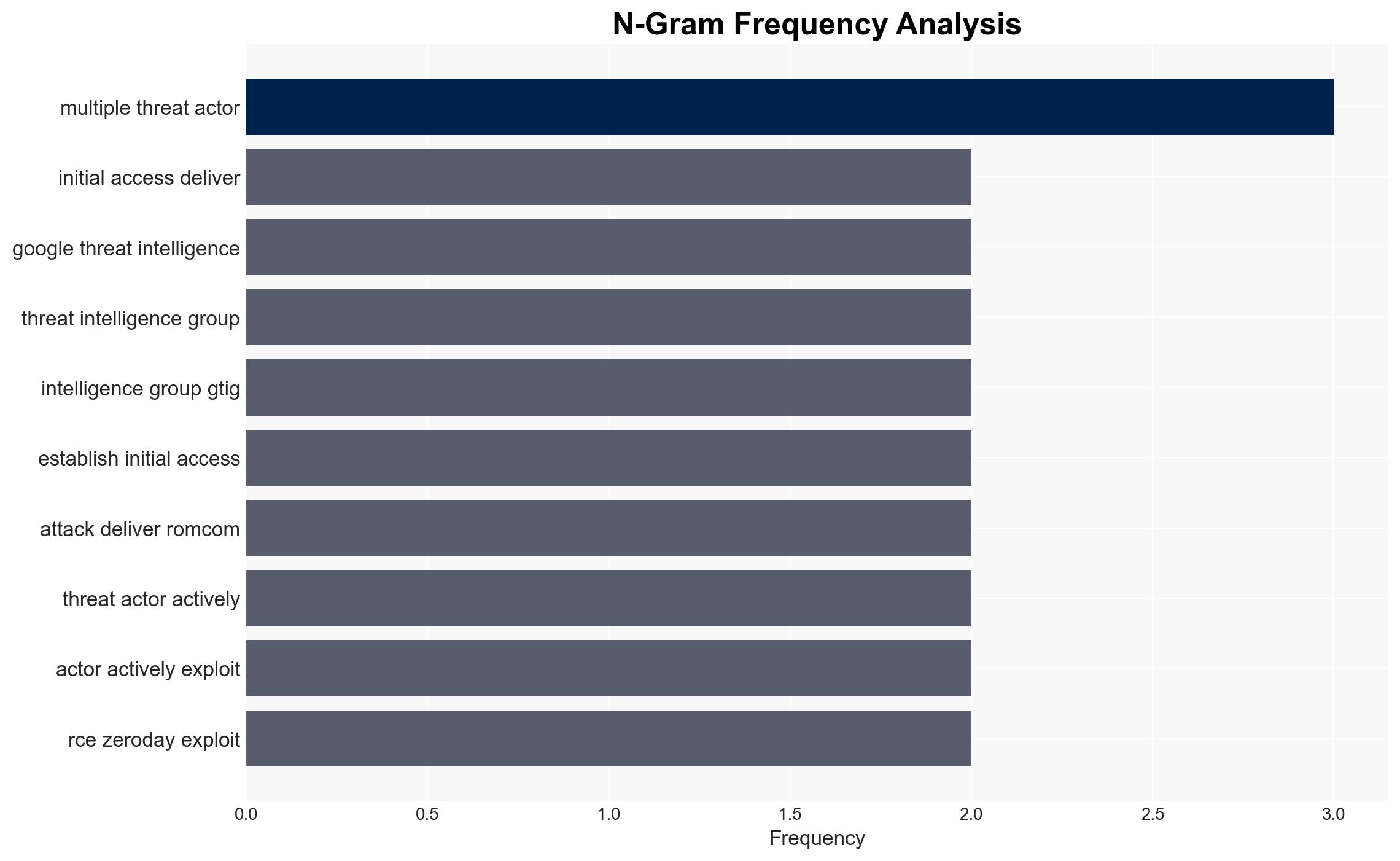
Multiple threat actors, including nation-state and financially motivated groups, are exploiting the CVE-2025-8088 vulnerability in WinRAR to gain unauthorized access and deploy malware. The flaw, despite being patched, remains a significant threat due to its widespread adoption by both state and non-state actors. The most likely hypothesis is that this exploitation will continue to evolve, targeting critical sectors like military and government. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The exploitation of the WinRAR flaw is primarily driven by nation-state actors targeting geopolitical adversaries. Supporting evidence includes targeted attacks on military and government sectors, particularly by Russian and Chinese actors. Contradicting evidence is the involvement of financially motivated groups, suggesting broader motivations.
- Hypothesis B: The exploitation is opportunistic, with both nation-state and criminal actors leveraging the flaw due to its availability and effectiveness. Supporting evidence includes rapid adoption by cybercriminals and the sale of exploits in underground markets. Contradicting evidence is the sophisticated targeting of specific sectors, which may imply strategic objectives beyond financial gain.
- Assessment: Hypothesis B is currently better supported due to the diverse range of actors and motivations involved. Key indicators that could shift this judgment include evidence of coordinated campaigns by specific nation-states or a significant increase in attacks on non-strategic sectors.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability will continue to be exploited despite the availability of a patch; nation-state actors have strategic motivations beyond immediate financial gain; cybercriminals will prioritize easily exploitable vulnerabilities.
- Information Gaps: Detailed attribution of specific attacks to particular actors; the extent of patch adoption among vulnerable systems; motivations behind specific targeting choices.
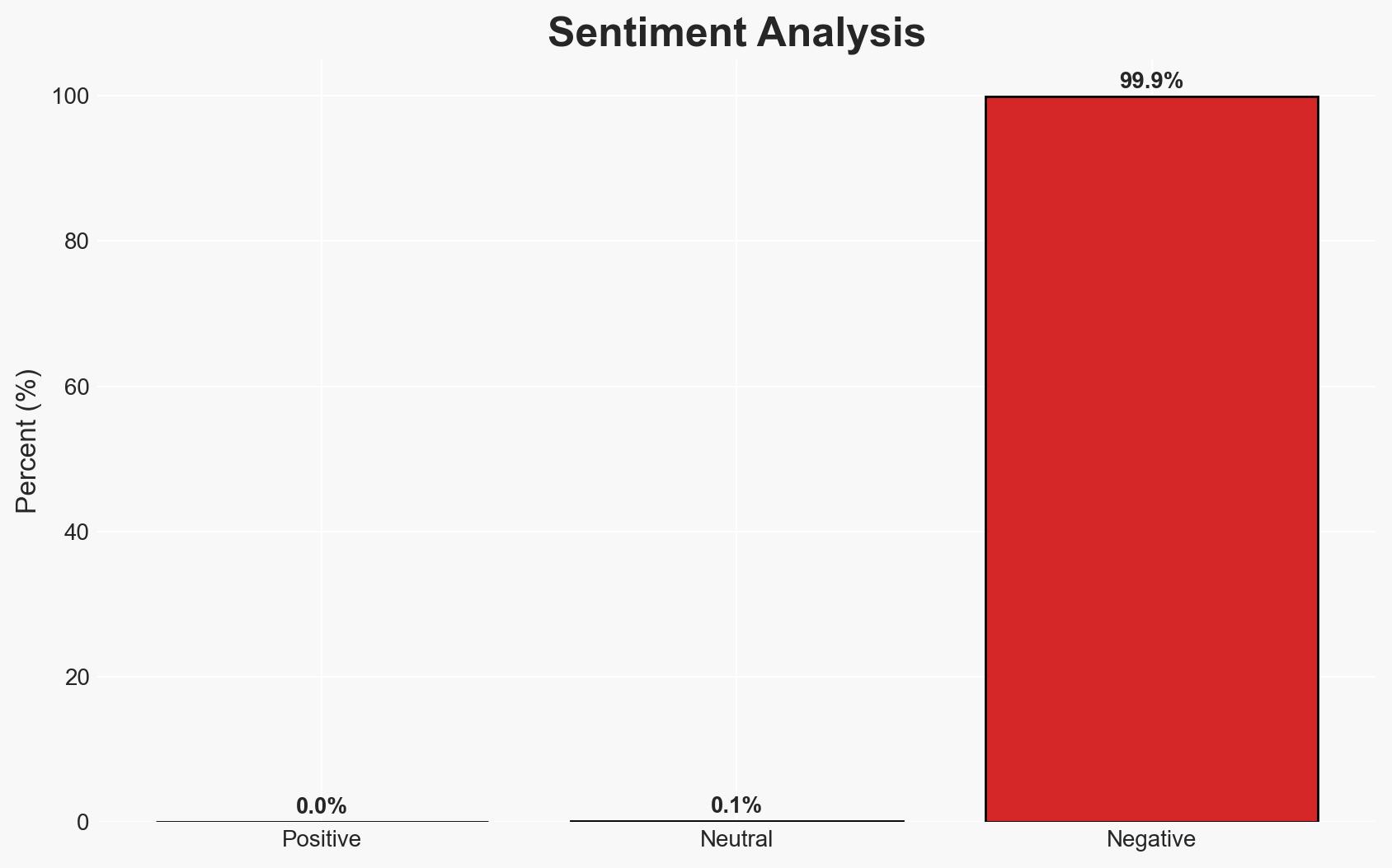
- Bias & Deception Risks: Potential bias in attributing attacks to nation-states without conclusive evidence; risk of overestimating the impact of the vulnerability due to media amplification.
4. Implications and Strategic Risks
The continued exploitation of the WinRAR flaw could exacerbate existing geopolitical tensions and lead to increased cyber conflict. The involvement of both state and non-state actors indicates a complex threat landscape that may evolve with technological and strategic shifts.
- Political / Geopolitical: Potential escalation in cyber operations between adversarial nations, particularly involving Russia and China.
- Security / Counter-Terrorism: Increased risk to critical infrastructure and sensitive government operations, necessitating enhanced cybersecurity measures.
- Cyber / Information Space: Proliferation of similar vulnerabilities could lead to a surge in cyber-espionage and data breaches.
- Economic / Social: Potential economic disruptions from targeted attacks on financial institutions and businesses, leading to broader social instability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage rapid patch deployment across vulnerable systems; enhance monitoring for indicators of compromise related to the WinRAR flaw.
- Medium-Term Posture (1–12 months): Develop partnerships for intelligence sharing on emerging vulnerabilities; invest in resilience measures for critical sectors.
- Scenario Outlook:
- Best: Rapid patch adoption mitigates the threat, reducing exploitation incidents.
- Worst: Widespread exploitation leads to significant geopolitical and economic disruptions.
- Most-Likely: Continued exploitation with gradual decline as patch adoption increases, but with sporadic high-impact incidents.
6. Key Individuals and Entities
- Google Threat Intelligence Group (GTIG)
- ESET researchers: Anton Cherepanov, Peter Košinár, Peter Strýček
- Threat actor “zeroplayer”
- Nation-state actors linked to Russia and China
7. Thematic Tags
cybersecurity, nation-state actors, vulnerability exploitation, cybercrime, geopolitical tensions, malware deployment, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us