Winter Cyberattack on Poland’s Power Grid Poses Deadly Risks, Experts Warn
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cyberattack on Poland’s power grid could have turned deadly in winter cold
1. BLUF (Bottom Line Up Front)
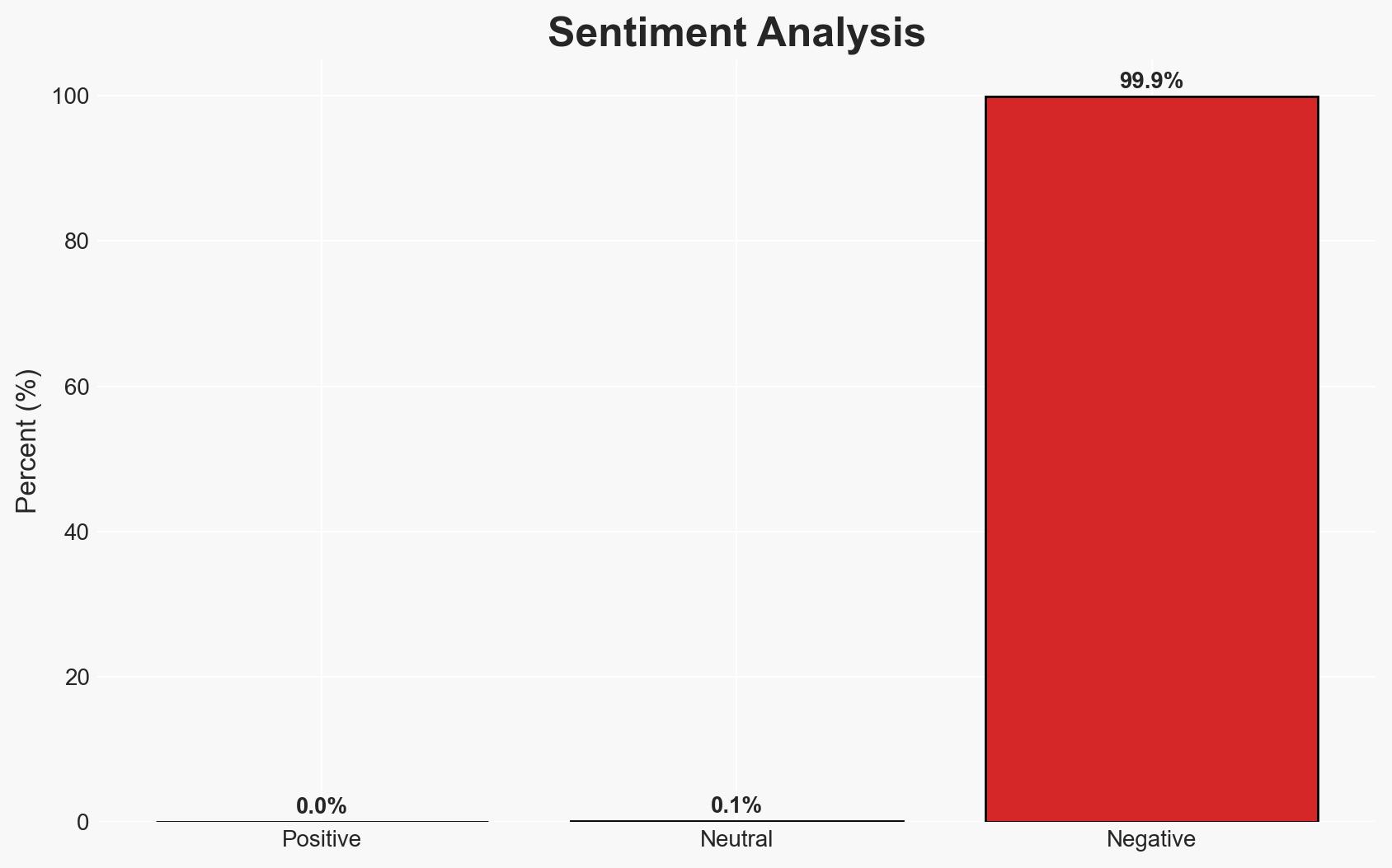
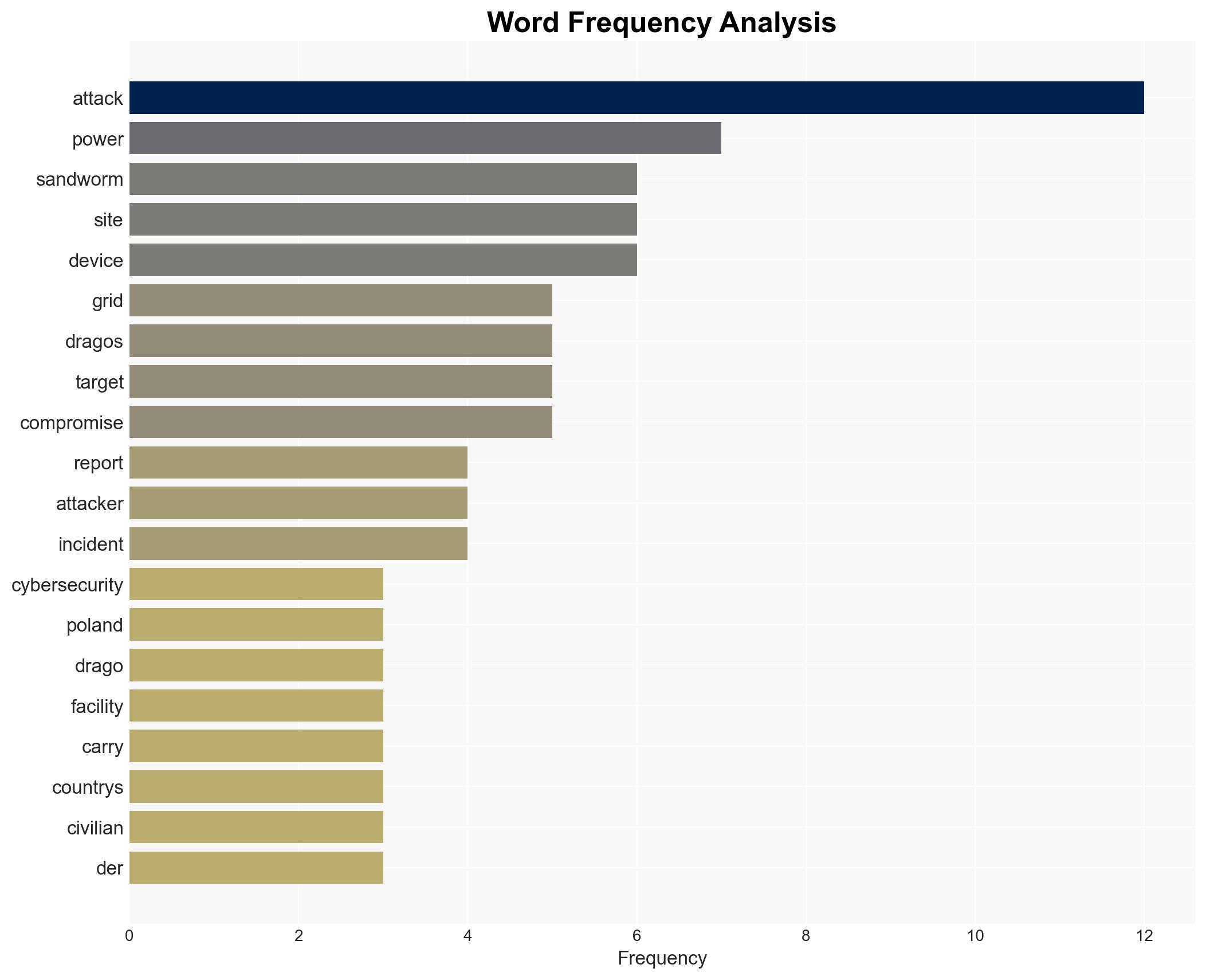
The cyberattack on Poland’s power grid, attributed to Russian intelligence, posed a significant threat to civilian safety, particularly during winter. The attack targeted distributed energy resources (DERs) and demonstrated advanced capabilities, although it did not result in outages. The most likely hypothesis is that the attack was a deliberate attempt to test and exploit vulnerabilities in Poland’s energy infrastructure. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was a deliberate effort by Russian intelligence to disrupt Poland’s power grid, leveraging advanced cyber capabilities to target DERs. This is supported by the attribution to Sandworm and the use of sophisticated techniques. However, the lack of actual outages introduces uncertainty.
- Hypothesis B: The attack was an opportunistic attempt by non-state actors or independent hackers to exploit vulnerabilities for financial gain or to test capabilities, rather than a state-sponsored operation. The coordinated nature and advanced methods contradict this hypothesis.
- Assessment: Hypothesis A is better supported due to the attribution to Sandworm, a known Russian state-affiliated group, and the sophisticated nature of the attack. Indicators such as further similar attacks or intelligence confirming state sponsorship could reinforce this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attribution to Sandworm is accurate; the attack was state-sponsored; DERs are increasingly targeted due to lower cybersecurity investment; winter conditions increased potential lethality.
- Information Gaps: Specific details of the attack methods and full extent of damage; confirmation of state sponsorship beyond attribution; motivations behind the timing and target selection.
- Bias & Deception Risks: Potential bias in attribution due to historical precedents; risk of overestimating the threat based on incomplete data; possibility of false flag operations.
4. Implications and Strategic Risks
The attack on Poland’s power grid highlights vulnerabilities in critical infrastructure and the evolving threat landscape. It may prompt increased investment in cybersecurity for DERs and influence geopolitical tensions.
- Political / Geopolitical: Potential escalation in cyber hostilities between Russia and NATO countries; increased diplomatic tensions.
- Security / Counter-Terrorism: Heightened alert for similar attacks on critical infrastructure in other regions; potential for copycat attacks.
- Cyber / Information Space: Increased focus on securing DERs; potential for misinformation campaigns exploiting the incident.
- Economic / Social: Potential economic impact from increased cybersecurity spending; public concern over energy security and reliability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of DERs; conduct vulnerability assessments; engage in diplomatic channels to address state-sponsored cyber threats.
- Medium-Term Posture (1–12 months): Develop resilience measures for critical infrastructure; strengthen international partnerships for cyber defense; invest in cybersecurity for DERs.
- Scenario Outlook: Best: Improved cybersecurity and deterrence reduce attack frequency. Worst: Escalation leads to significant outages and geopolitical conflict. Most-Likely: Continued low-level cyber skirmishes with incremental improvements in defense.
6. Key Individuals and Entities
- Sandworm (Russian GRU-affiliated group)
- Dragos (Cybersecurity firm)
- Electrum (Alternative name for Sandworm)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, critical infrastructure, state-sponsored cyberattacks, energy security, geopolitical tensions, Sandworm, distributed energy resources
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us