eScan and Morphisec Clash Over Mischaracterization of Update Server Incident
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: AV vendor goes to war with security shop over update server scare
1. BLUF (Bottom Line Up Front)
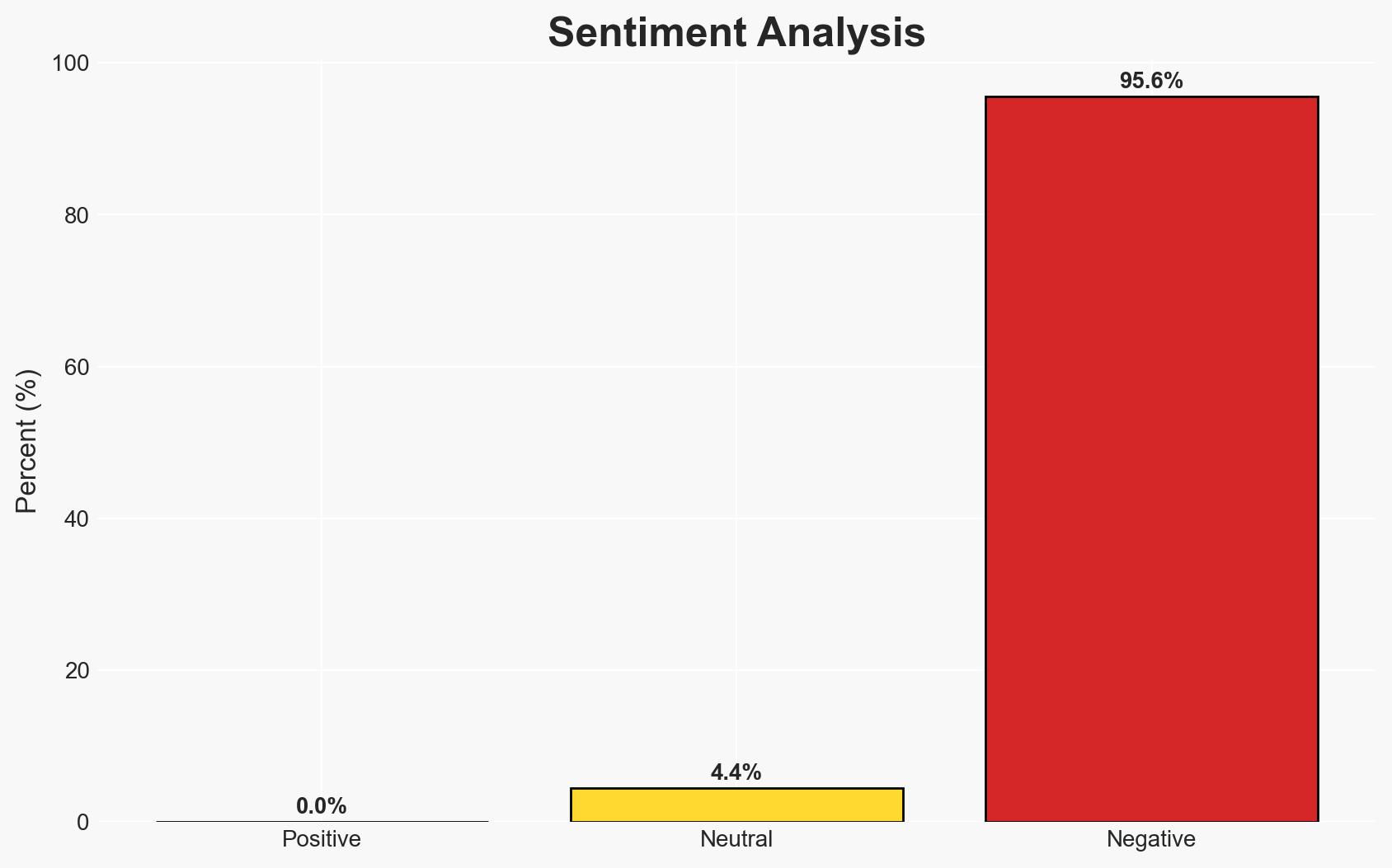
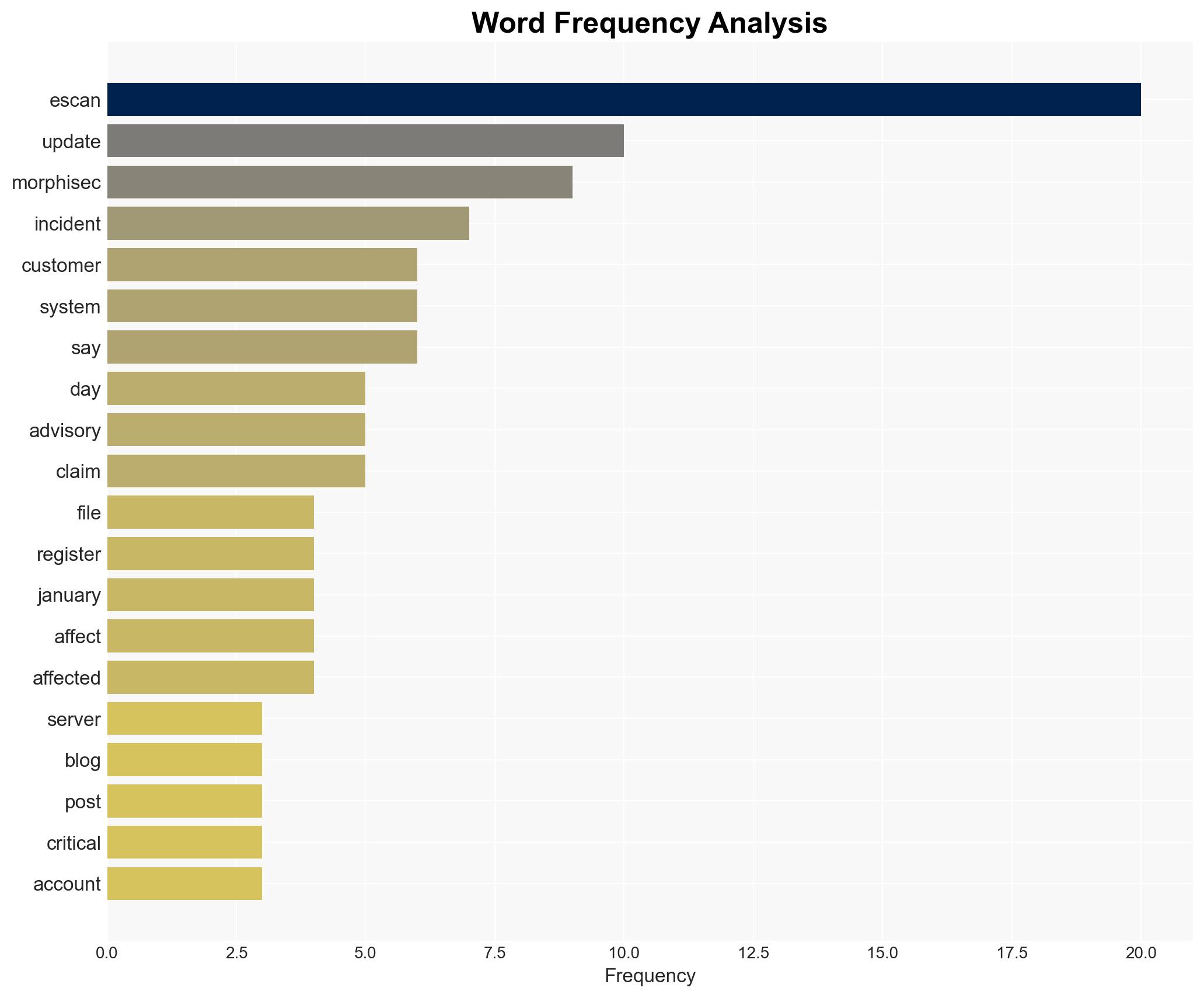
A dispute has arisen between antivirus vendor eScan and threat intelligence firm Morphisec regarding the characterization of an update server incident. eScan claims the incident was minor and contained, while Morphisec describes it as a critical supply-chain compromise. The most likely hypothesis is that the incident was limited in scope, affecting a small number of systems, with moderate confidence due to conflicting accounts and lack of independent verification.
2. Competing Hypotheses
- Hypothesis A: The incident was a minor, localized breach affecting a small number of systems, as claimed by eScan. Supporting evidence includes eScan’s detailed timeline and remediation efforts. Contradicting evidence is Morphisec’s claim of a broader supply-chain compromise. Key uncertainties include the lack of independent verification of either account.
- Hypothesis B: The incident was a significant supply-chain compromise with potentially broader implications, as claimed by Morphisec. Supporting evidence includes Morphisec’s public blog post and characterization of the incident. Contradicting evidence is eScan’s detailed refutation and limited scope of affected systems. Uncertainties include the absence of corroborating reports from other sources.
- Assessment: Hypothesis A is currently better supported due to eScan’s detailed incident response and lack of evidence for a wider impact. Key indicators that could shift this judgment include independent verification of Morphisec’s claims or additional reports of similar incidents.
3. Key Assumptions and Red Flags
- Assumptions: eScan’s internal monitoring is reliable; Morphisec’s characterization is based on credible analysis; the incident did not affect systems outside the reported region.
- Information Gaps: Independent assessments of the incident; detailed technical analysis of the rogue file; confirmation of the affected region.
- Bias & Deception Risks: Potential bias in eScan’s and Morphisec’s accounts due to reputational stakes; risk of exaggeration or downplaying of the incident’s scope.
4. Implications and Strategic Risks
This development could influence vendor trust and customer confidence in cybersecurity solutions, potentially affecting market dynamics and vendor reputations.
- Political / Geopolitical: Limited direct implications, but could affect international perceptions of cybersecurity standards.
- Security / Counter-Terrorism: Highlights vulnerabilities in software supply chains, potentially encouraging similar attacks.
- Cyber / Information Space: May lead to increased scrutiny of update mechanisms and supply-chain security practices.
- Economic / Social: Potential impact on eScan’s market position and customer trust, influencing competitive dynamics in the cybersecurity industry.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct independent technical analysis to verify claims; monitor for similar incidents; engage with both parties for clarity.
- Medium-Term Posture (1–12 months): Strengthen supply-chain security practices; develop partnerships for threat intelligence sharing; enhance incident response capabilities.
- Scenario Outlook:
- Best: Incident is confirmed minor, leading to improved security practices.
- Worst: Broader compromise is confirmed, leading to significant reputational damage and financial loss for eScan.
- Most-Likely: Incident remains contained with minor reputational impact, prompting industry-wide security reviews.
6. Key Individuals and Entities
- eScan (MicroWorld Technologies)
- Morphisec
- The Register (media outlet)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, supply-chain security, antivirus, incident response, threat intelligence, vendor dispute, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us