Marquis attributes ransomware attack to breach of SonicWall cloud backup, impacting U.S. financial institutio…
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Marquis blames ransomware breach on SonicWall cloud backup hack
1. BLUF (Bottom Line Up Front)
Marquis Software Solutions attributes a ransomware attack affecting its systems and numerous U.S. financial institutions to a SonicWall cloud backup breach. The attack leveraged stolen firewall configuration data, suggesting a sophisticated threat actor. This assessment is made with moderate confidence due to ongoing investigations and incomplete data.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack on Marquis was facilitated by a breach of SonicWall’s cloud backup service, allowing attackers to extract firewall configuration data. This is supported by Marquis’ statements and SonicWall’s admission of a breach affecting its cloud backup service.
- Hypothesis B: The ransomware attack was independent of the SonicWall breach, potentially involving other vulnerabilities or insider threats. Contradictory evidence includes SonicWall’s initial claim of limited impact and the lack of direct evidence linking the breach to the ransomware attack.
- Assessment: Hypothesis A is currently better supported due to the alignment of Marquis’ and SonicWall’s statements regarding the breach. However, further investigation could reveal alternative vectors or actors, shifting this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The breach of SonicWall’s cloud backup service directly enabled the ransomware attack; Marquis’ systems were otherwise secure; the threat actor is sophisticated and potentially state-sponsored.
- Information Gaps: Details on the specific methods used by attackers to exploit the stolen data; full scope of affected entities and systems; identity and motivations of the threat actor.
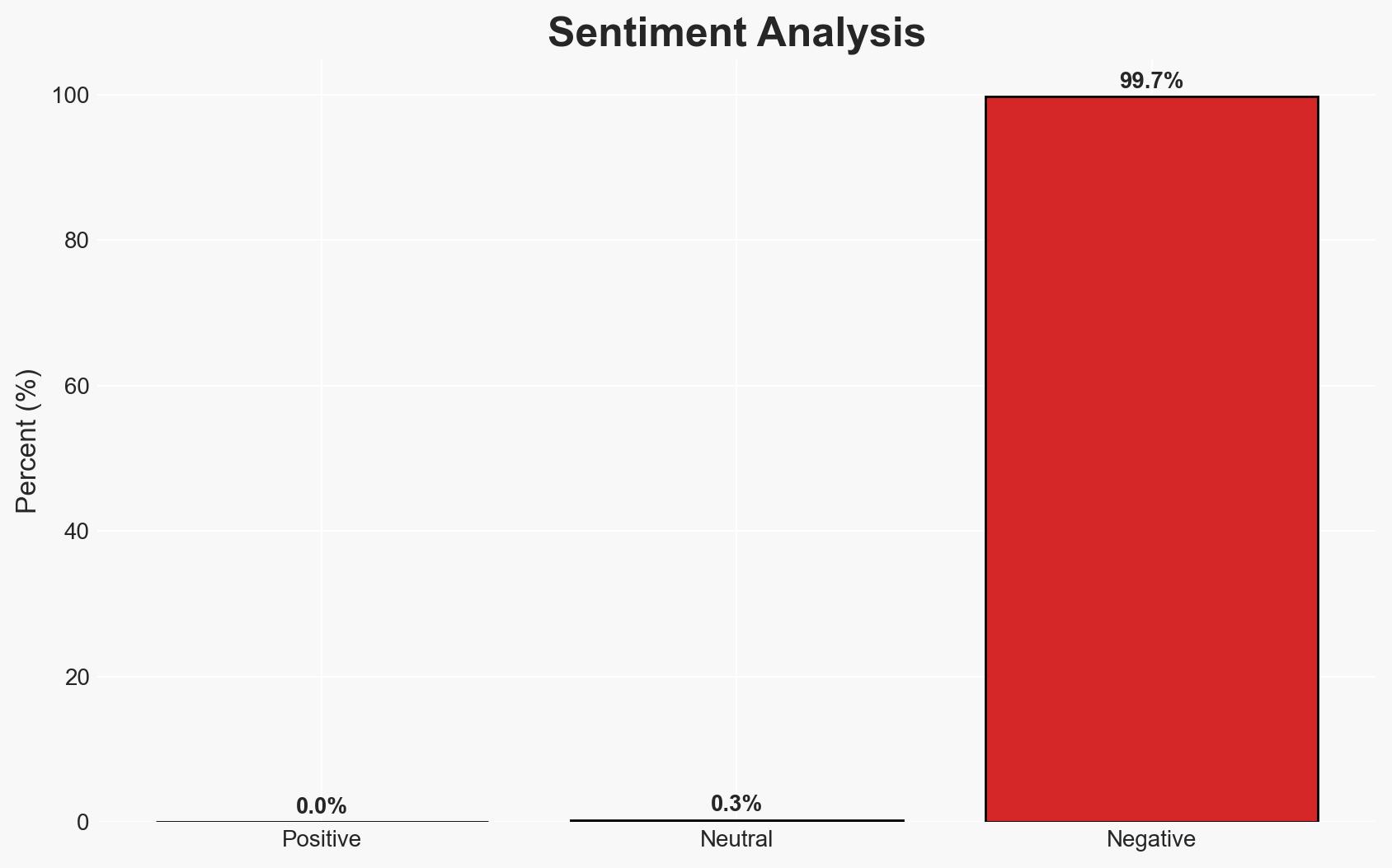
- Bias & Deception Risks: Potential bias in Marquis’ statements to deflect responsibility; SonicWall’s initial underreporting of breach impact; possibility of deliberate misinformation by threat actors.
4. Implications and Strategic Risks
This development could signal increased vulnerability in cloud-based security solutions, prompting broader scrutiny and regulatory responses. It may also embolden threat actors to exploit similar vulnerabilities.
- Political / Geopolitical: Potential for increased tensions if state-sponsored involvement is confirmed, impacting U.S. relations with implicated nations.
- Security / Counter-Terrorism: Heightened threat environment for financial institutions, necessitating enhanced cybersecurity measures.
- Cyber / Information Space: Increased focus on cloud security vulnerabilities and potential for copycat attacks exploiting similar methods.
- Economic / Social: Financial losses for affected institutions and potential erosion of trust in digital banking services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough audits of firewall configurations; enhance monitoring for anomalous activities; engage with SonicWall for detailed breach analysis.
- Medium-Term Posture (1–12 months): Develop resilience measures, including diversified security solutions; strengthen partnerships with cybersecurity firms; invest in employee training on cyber hygiene.
- Scenario Outlook:
- Best: Rapid containment and patching of vulnerabilities, minimizing further impact.
- Worst: Widespread exploitation of similar vulnerabilities, leading to systemic financial sector disruptions.
- Most-Likely: Incremental improvements in security posture with periodic breaches as vulnerabilities are addressed.
6. Key Individuals and Entities
- Marquis Software Solutions
- SonicWall
- BleepingComputer
- Huntress
- Mandiant
7. Thematic Tags
cybersecurity, ransomware, cloud security, financial sector, state-sponsored threats, data breach, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us