New Windows Malware Employs Pulsar RAT for Data Theft and Live Interaction with Victims
Published on: 2026-01-31
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
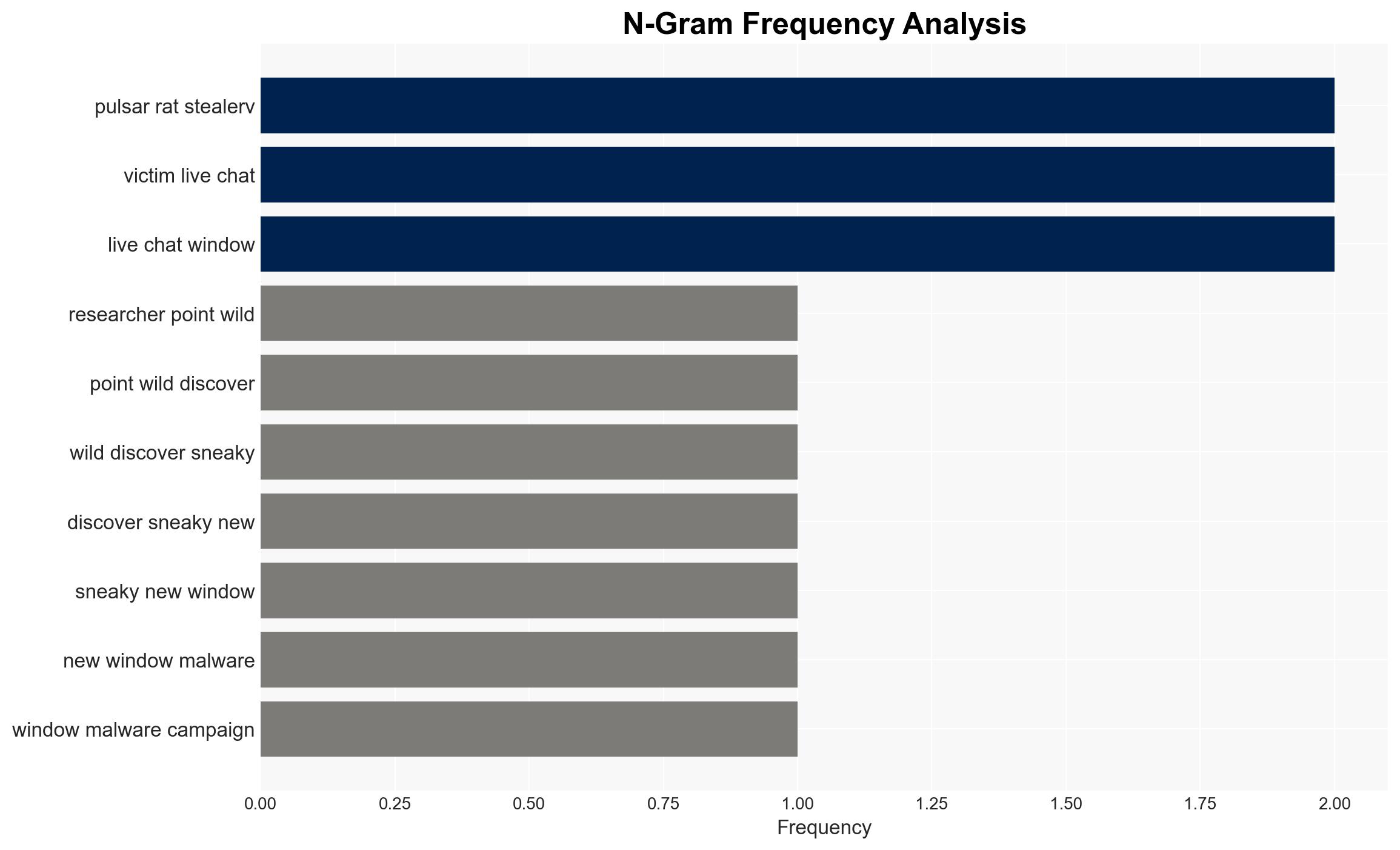
Intelligence Report: Windows Malware Uses Pulsar RAT for Live Chats While Stealing Data
1. BLUF (Bottom Line Up Front)
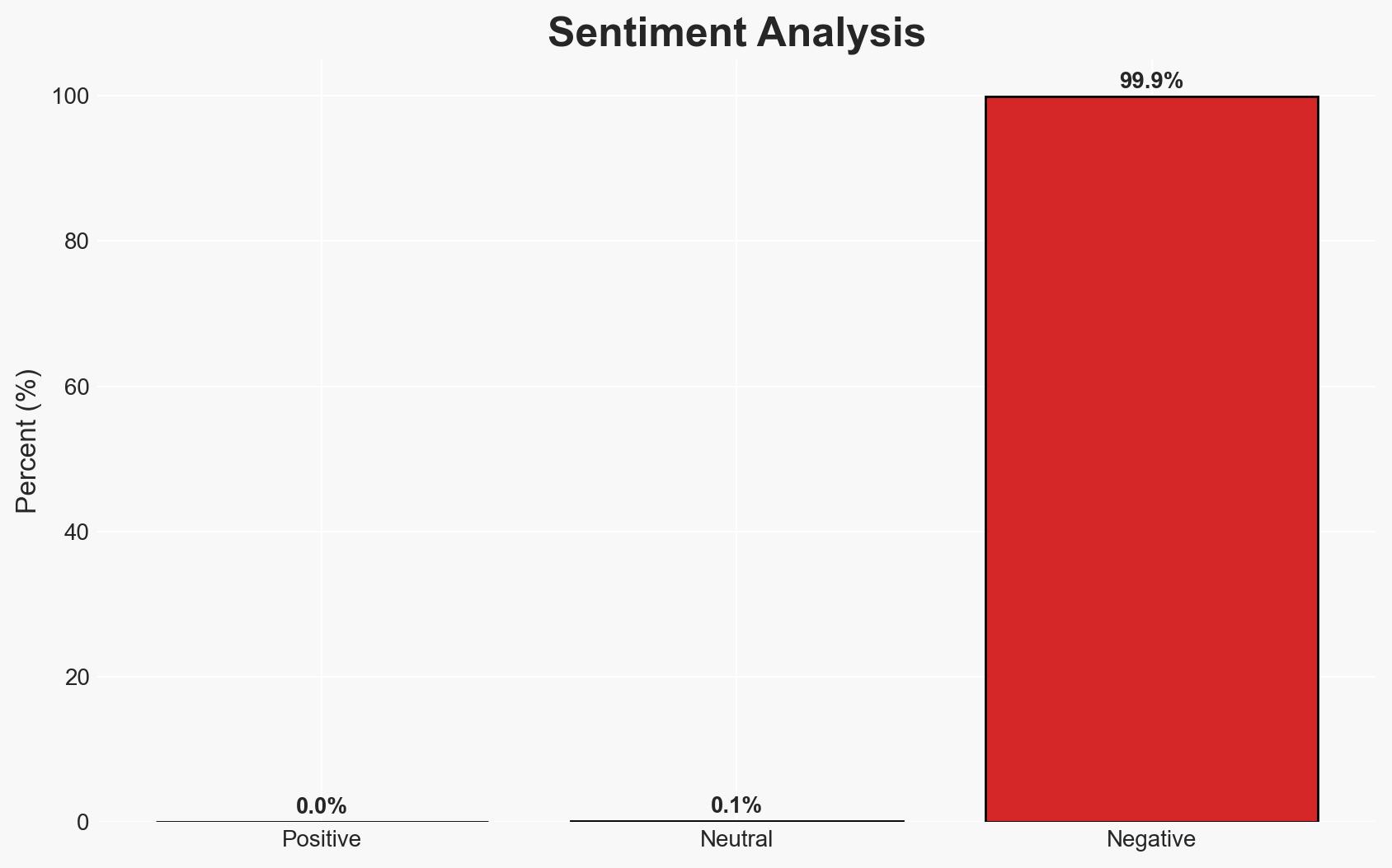
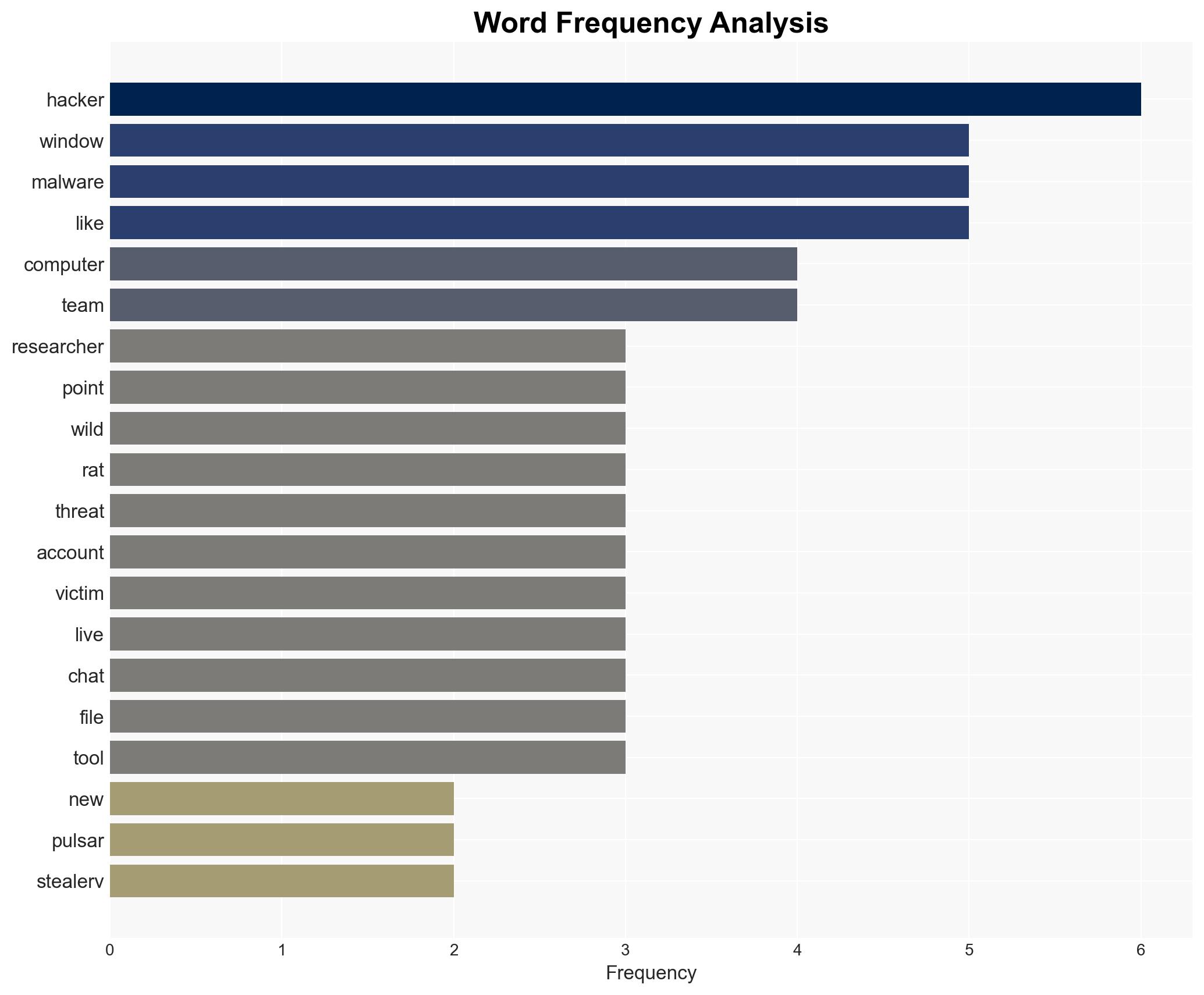
The discovery of a sophisticated Windows malware campaign using Pulsar RAT and Stealerv37 represents a significant cyber threat, targeting personal data and financial assets through innovative techniques such as live chat interaction with victims. This development primarily affects individual users and potentially organizations with inadequate cybersecurity measures. Overall, there is moderate confidence in the assessment due to the detailed technical analysis provided by cybersecurity researchers.
2. Competing Hypotheses
- Hypothesis A: The malware campaign is primarily financially motivated, aiming to steal personal data and financial assets. This is supported by the malware’s focus on crypto wallets, passwords, and gaming accounts. However, the live chat feature introduces uncertainty about whether there are additional motives, such as psychological manipulation.
- Hypothesis B: The malware campaign is a precursor to larger-scale cyber operations, potentially testing new methods for broader cyber-espionage or state-sponsored activities. The use of advanced techniques like living-off-the-land and memory-only execution supports this, but there is limited evidence of state-level involvement.
- Assessment: Hypothesis A is currently better supported due to the explicit targeting of financial and personal data, which aligns with typical financially motivated cybercrime. Indicators that could shift this judgment include evidence of state sponsorship or geopolitical targets.
3. Key Assumptions and Red Flags
- Assumptions: The malware’s primary goal is financial theft; the live chat feature is not indicative of broader psychological operations; the campaign is not state-sponsored.
- Information Gaps: Lack of information on the identity or location of the attackers; unclear if the campaign targets specific regions or demographics.
- Bias & Deception Risks: Potential bias in the source’s interpretation of the malware’s capabilities; risk of deception if attackers have planted false indicators to mislead attribution efforts.
4. Implications and Strategic Risks
This malware campaign could evolve into a more widespread threat, leveraging its advanced techniques to bypass traditional defenses and potentially inspire copycat operations.
- Political / Geopolitical: Minimal direct implications unless linked to state actors; potential for increased tension if attribution suggests state involvement.
- Security / Counter-Terrorism: Highlights vulnerabilities in current cybersecurity practices, necessitating enhanced defensive measures.
- Cyber / Information Space: Demonstrates the evolving nature of cyber threats, emphasizing the need for continuous adaptation in cybersecurity strategies.
- Economic / Social: Potential economic impact through financial theft; social implications if personal data is exploited for identity theft or fraud.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of systems for signs of infection; update antivirus and security protocols to detect memory-resident malware; educate users on recognizing phishing attempts and suspicious activity.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced detection technologies; enhance user authentication methods, including multi-factor authentication.
- Scenario Outlook:
- Best: Rapid containment and neutralization of the malware with minimal financial loss.
- Worst: Expansion of the campaign leading to significant financial and data losses, with potential geopolitical ramifications if state involvement is confirmed.
- Most-Likely: Continued targeting of individual users and small organizations, with gradual improvements in detection and response capabilities.
6. Key Individuals and Entities
- Point Wild (Cybersecurity Research Firm)
- Lat61 Threat Intelligence Team (Cybersecurity Research Team)
- Dr. Zulfikar Ramzan (Head of Lat61 Team)
- Hackread.com (Media Outlet)
7. Thematic Tags
cybersecurity, financial theft, malware, Pulsar RAT, cybercrime, information security, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us