Foreign spies infiltrate professional online groups posing as experts to extract sensitive information, warns…
Published on: 2026-02-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
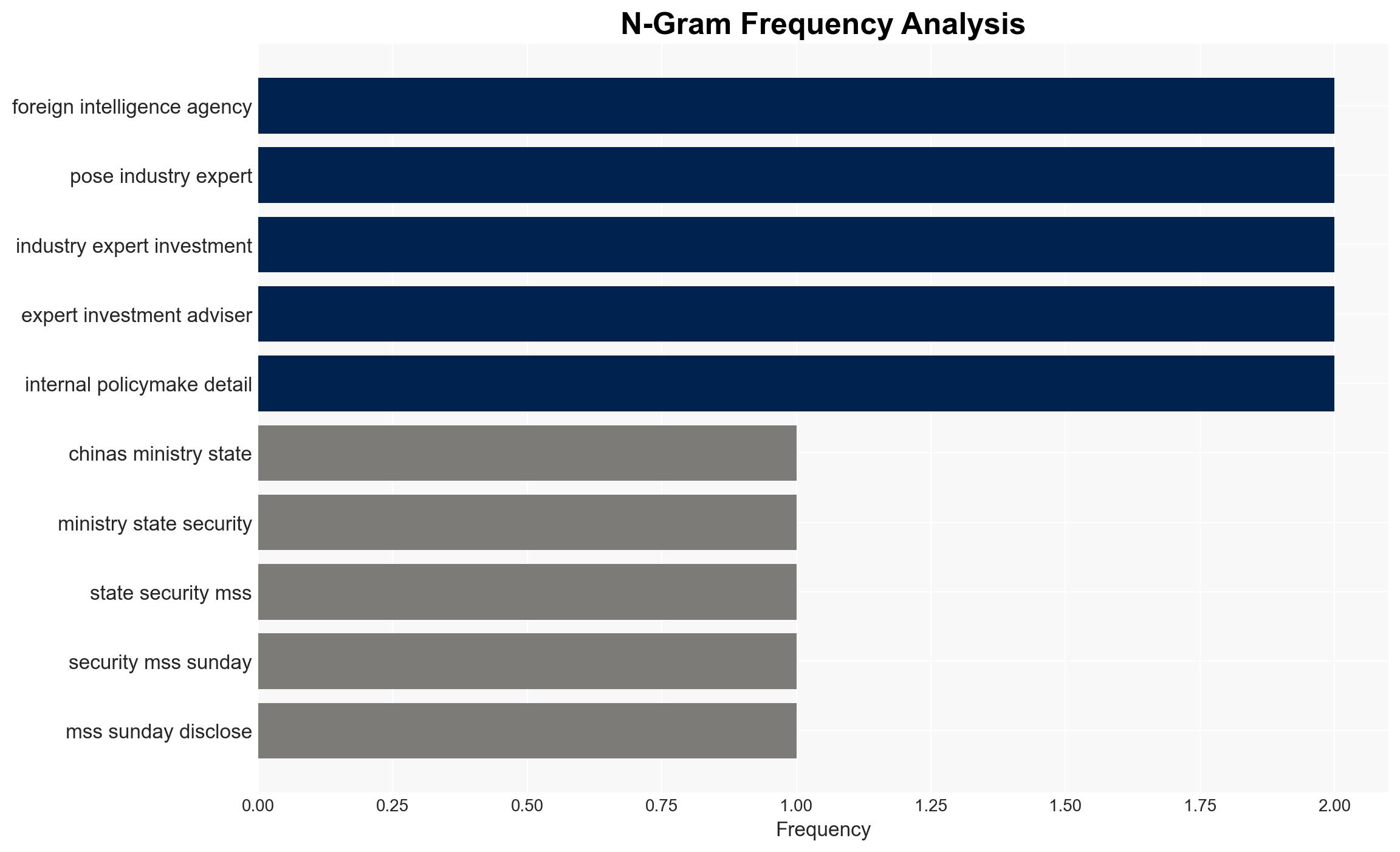
Intelligence Report: Chinese state security authority discloses foreign intelligence operatives posing as experts in online groups to steal sensitive data
1. BLUF (Bottom Line Up Front)
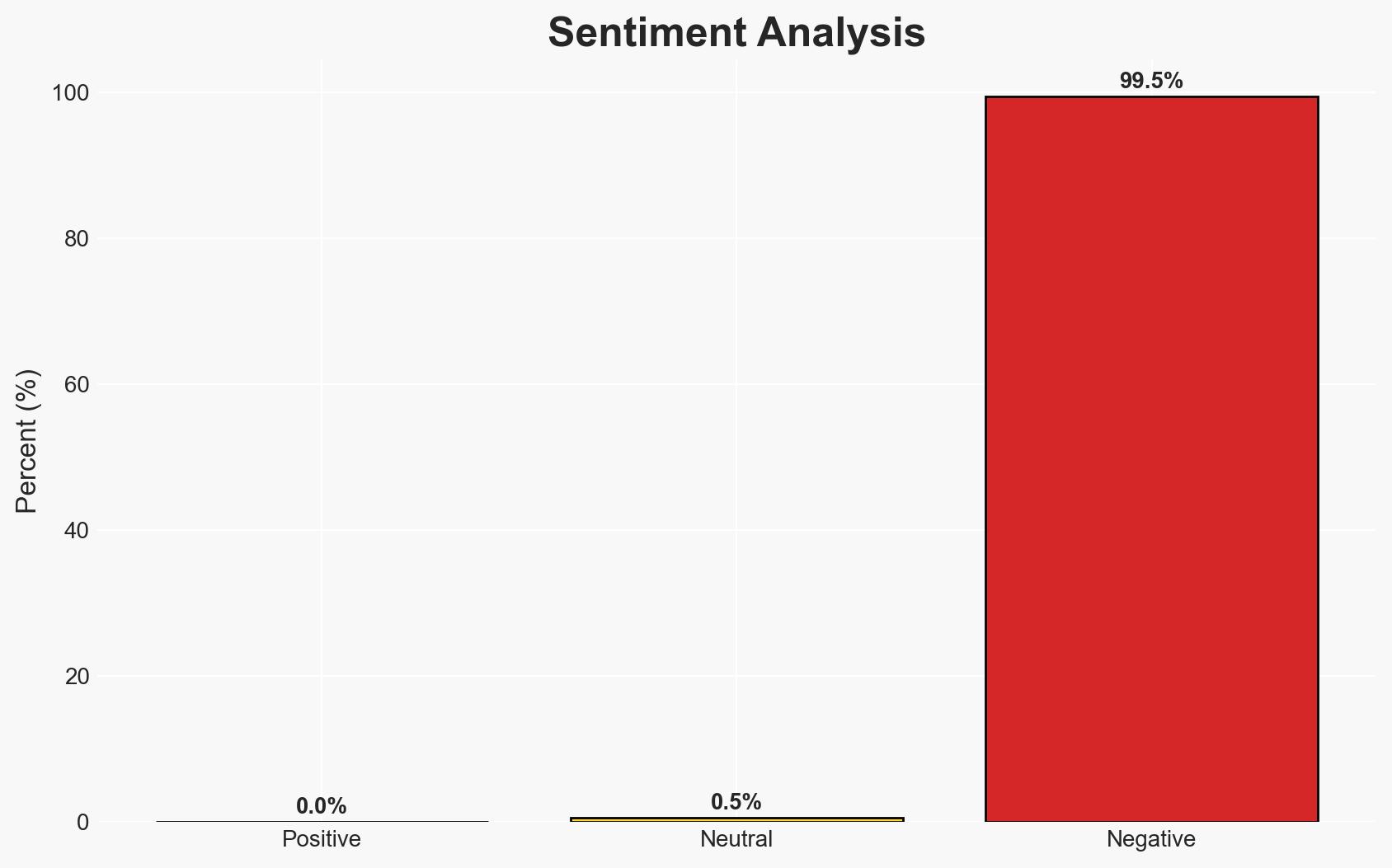
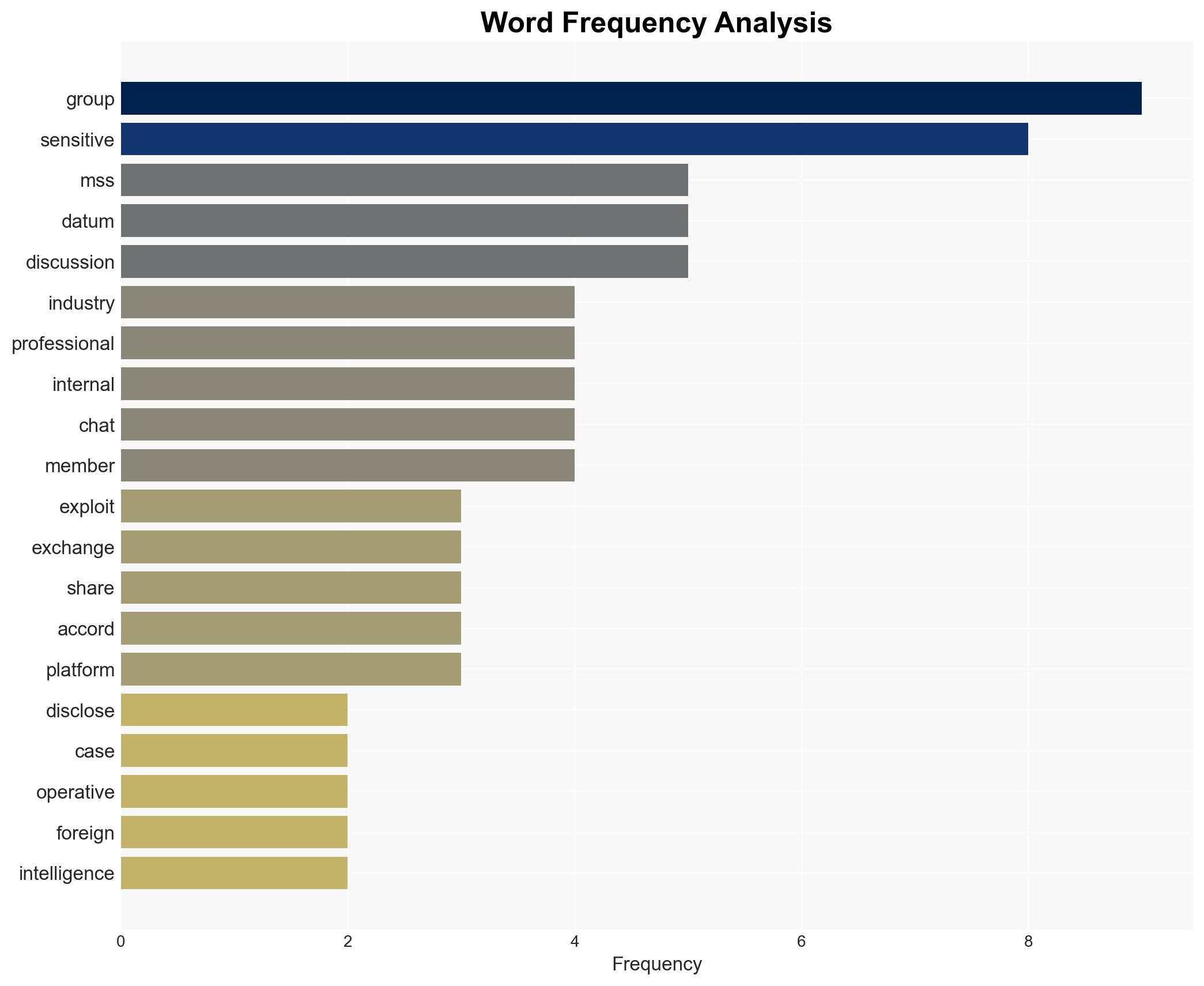
The Chinese Ministry of State Security (MSS) has identified foreign intelligence operatives infiltrating online professional groups to extract sensitive information. This activity poses a significant threat to national security and economic interests by targeting key technical and policy data. The most likely hypothesis is that these operatives are systematically exploiting digital platforms to gather intelligence. Overall confidence in this assessment is moderate due to potential information gaps and source biases.
2. Competing Hypotheses
- Hypothesis A: Foreign intelligence agencies are deliberately infiltrating online professional groups to systematically gather sensitive information. This is supported by MSS reports of operatives posing as experts and using anonymity to exploit trust. Key uncertainties include the scale and specific targets of these operations.
- Hypothesis B: The activities reported may be isolated incidents of opportunistic data gathering rather than a coordinated effort by foreign intelligence. Contradicting evidence includes the structured nature of the infiltrations and the strategic use of professional networks, suggesting a higher level of organization.
- Assessment: Hypothesis A is currently better supported due to the detailed methods described by the MSS, indicating a systematic approach. Indicators that could shift this judgment include evidence of broader coordination or confirmation of specific state actors involved.
3. Key Assumptions and Red Flags
- Assumptions: The MSS’s report is accurate and not exaggerated for political purposes; foreign operatives have the capability to exploit online platforms effectively; the targeted data is of significant value to foreign entities.
- Information Gaps: Specific identities of the foreign operatives and their affiliations; the full extent of data compromised; the response measures being implemented by affected organizations.
- Bias & Deception Risks: Potential MSS bias in framing foreign threats to justify domestic security measures; risk of deception by foreign entities to mislead Chinese authorities about the true nature of their activities.
4. Implications and Strategic Risks
This development could lead to increased tensions between China and foreign states accused of espionage, impacting diplomatic relations and international cooperation. The exploitation of online platforms for intelligence gathering may prompt tighter regulations and surveillance measures, affecting global digital communication norms.
- Political / Geopolitical: Potential diplomatic fallout and retaliatory measures by China against suspected foreign states.
- Security / Counter-Terrorism: Heightened security protocols and counter-intelligence operations within China.
- Cyber / Information Space: Increased scrutiny and regulation of online platforms, possibly affecting global internet governance.
- Economic / Social: Potential disruption in international business collaborations and trust in digital communication tools.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of online professional groups, implement stricter access controls, and conduct awareness campaigns on information security.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to improve platform security, invest in counter-intelligence capabilities, and foster international dialogue on cyber norms.
- Scenario Outlook:
- Best: Effective countermeasures reduce infiltration incidents, leading to improved security and international cooperation.
- Worst: Escalation of cyber-espionage activities results in significant data breaches and diplomatic crises.
- Most-Likely: Continued low-level infiltration with periodic successes, prompting ongoing security enhancements and cautious international engagement.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, national security, intelligence operations, digital platforms, information security, geopolitical tensions, counter-intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us