Android Apps Expose 730TB of User Data and Google Secrets, Raising Concerns Over Security Flaws
Published on: 2026-02-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Shock report claims Android apps have leaked over 730TB of user data and Google secrets – here are some of the worst offenders around
1. BLUF (Bottom Line Up Front)
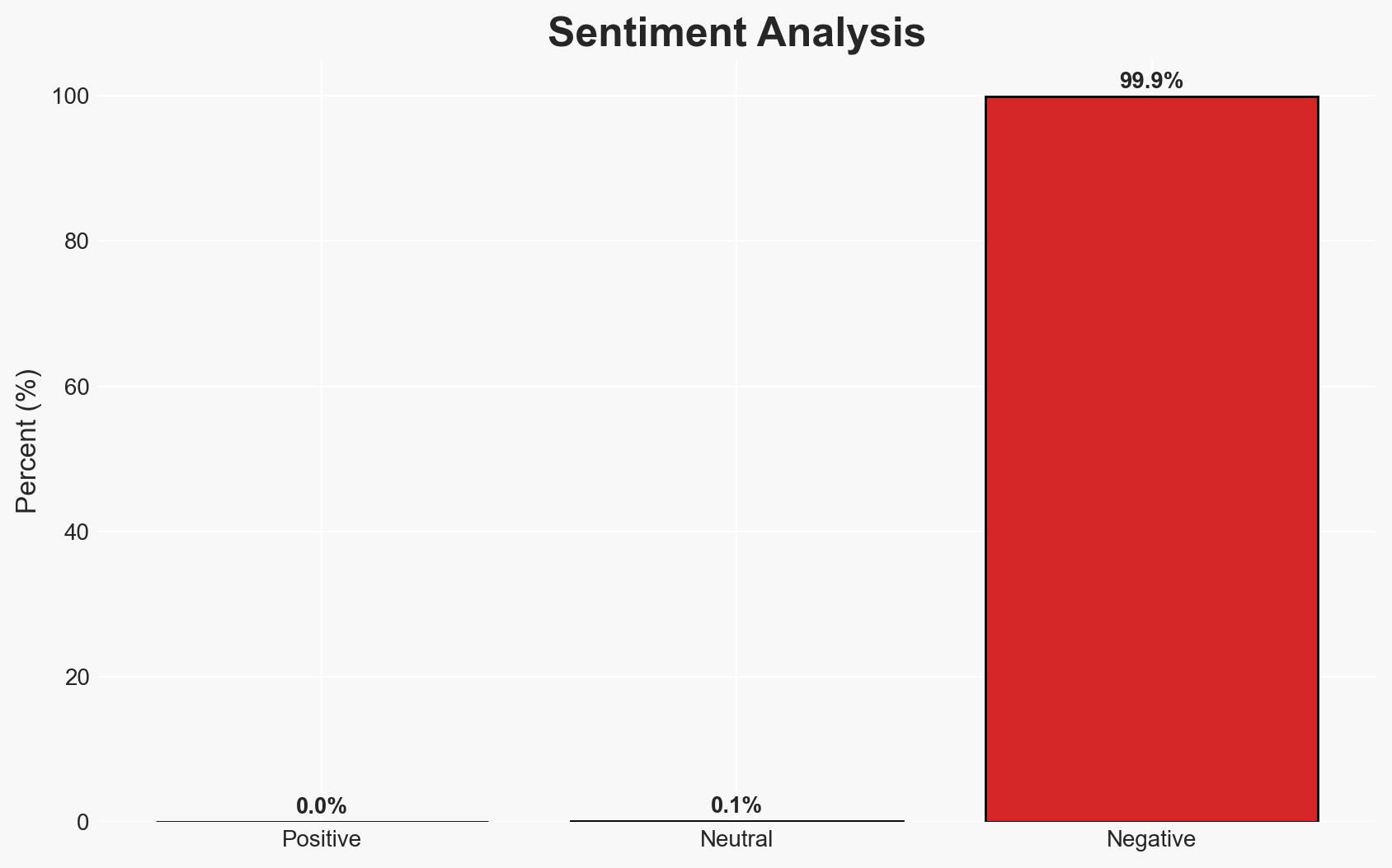
A recent investigation has uncovered significant security vulnerabilities in Android AI apps, leading to the exposure of over 730TB of user data and critical Google secrets. The most likely hypothesis is that these vulnerabilities result from widespread insecure coding practices, affecting app developers and users globally. This assessment is made with moderate confidence, given the scale of the data exposure and the evidence of prior exploitation.
2. Competing Hypotheses
- Hypothesis A: The data leaks are primarily due to systemic insecure coding practices among Android app developers. Supporting evidence includes the widespread presence of hardcoded secrets and misconfigured databases. However, the extent of developer awareness and training remains uncertain.
- Hypothesis B: The leaks are the result of targeted cyber-attacks exploiting known vulnerabilities in Android apps. While some evidence of prior compromise exists, such as attacker-style email addresses, the scale suggests broader systemic issues rather than isolated attacks.
- Assessment: Hypothesis A is currently better supported due to the pervasive nature of the coding flaws and the high percentage of apps affected. Indicators such as improved developer practices or a reduction in exposed secrets could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Developers have limited security training; the exposed data is valuable to malicious actors; the vulnerabilities are not intentionally left by insiders.
- Information Gaps: Detailed information on the specific apps affected and the full extent of data compromised.
- Bias & Deception Risks: Potential bias in the selection of apps analyzed; possibility of exaggeration of the threat by the reporting entity to gain attention.
4. Implications and Strategic Risks
The exposure of vast amounts of data could lead to increased cybercrime, loss of consumer trust, and regulatory scrutiny. The situation may evolve with potential geopolitical ramifications if state actors exploit these vulnerabilities.
- Political / Geopolitical: Potential for diplomatic tensions if state-sponsored actors are implicated.
- Security / Counter-Terrorism: Increased risk of cyber-attacks leveraging exposed data.
- Cyber / Information Space: Heightened vulnerability to cyber espionage and misinformation campaigns.
- Economic / Social: Possible economic impact on affected companies and erosion of user trust in digital platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of Android apps for security vulnerabilities; engage with developers for immediate remediation.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to enhance security training; implement stricter app store vetting processes.
- Scenario Outlook: Best: Rapid mitigation and improved security practices; Worst: Continued data breaches and exploitation; Most-Likely: Gradual improvements with intermittent breaches.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
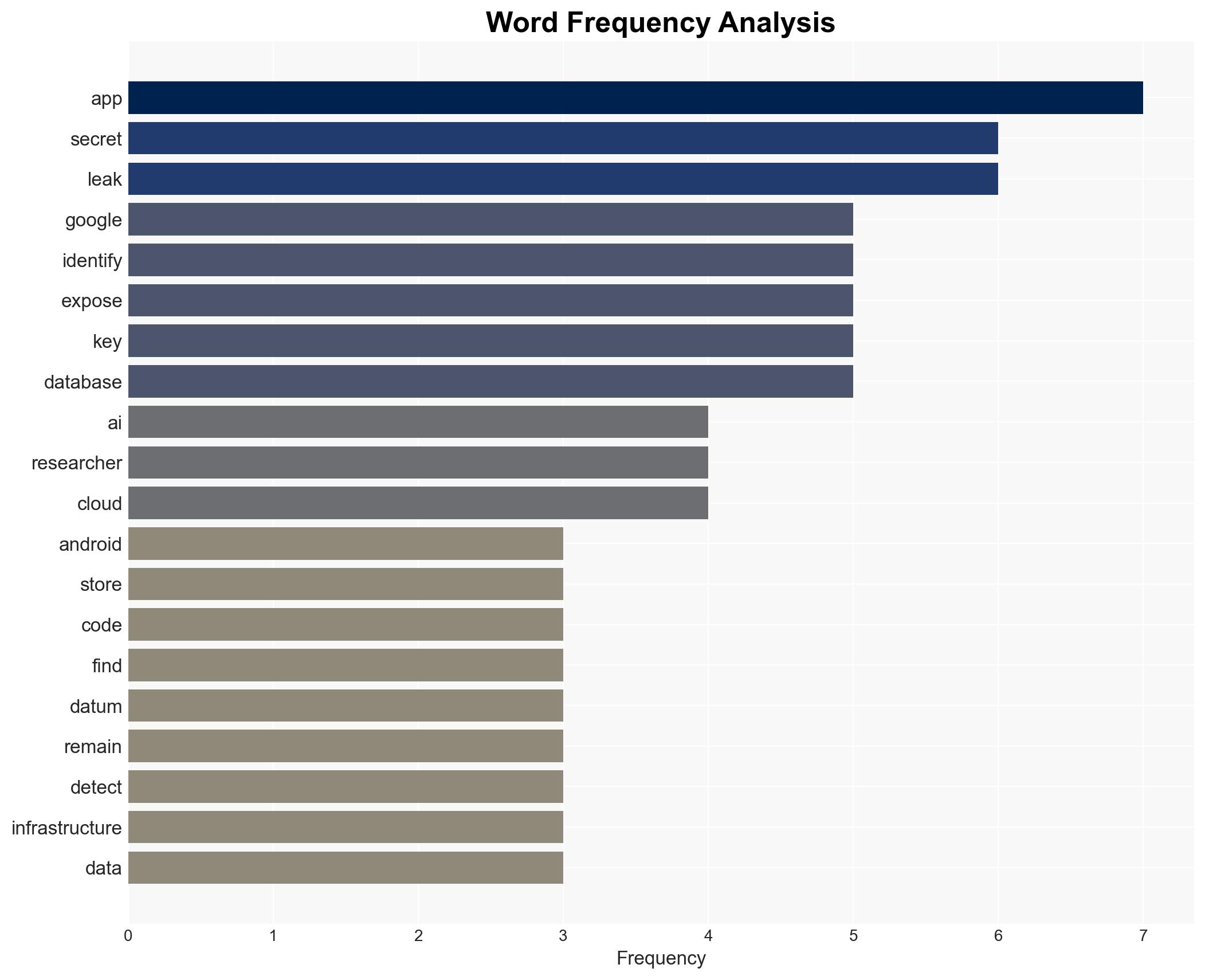
cybersecurity, data breach, Android apps, Google Cloud, AI vulnerabilities, information security, app development
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us