Edelson Lechtzin LLP Investigates Data Breach Affecting Customers of 1st MidAmerica Credit Union
Published on: 2026-02-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: DATA BREACH ALERT Edelson Lechtzin LLP is Investigating Claims on Behalf of 1st MidAmerica Credit Union Customers Whose Data May Have Been Compromised
1. BLUF (Bottom Line Up Front)
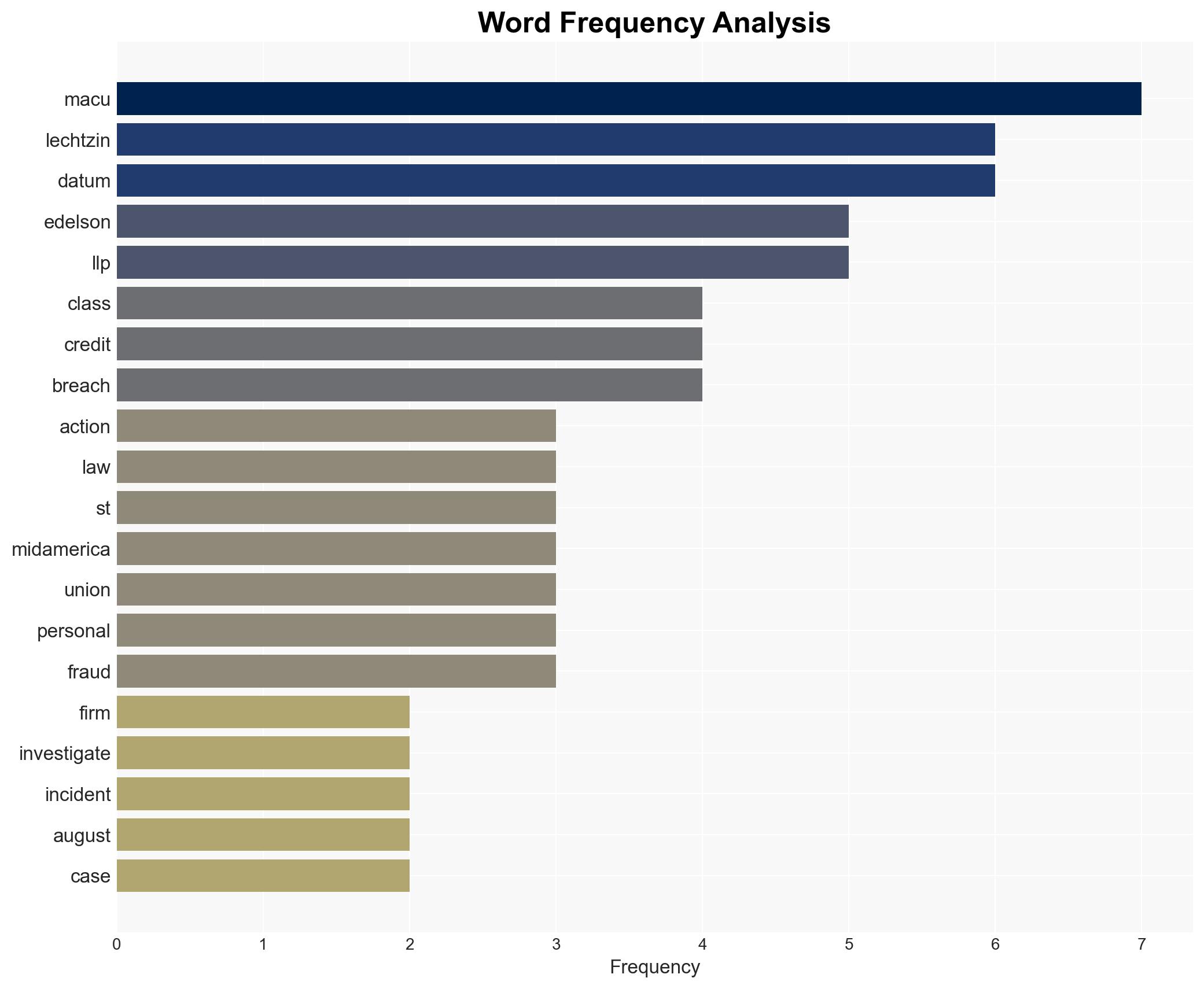
A data breach at 1st MidAmerica Credit Union (MACU) potentially compromised sensitive customer information, including Social Security numbers. The breach was identified by Marquis Software Solutions, a vendor for MACU. Edelson Lechtzin LLP is investigating possible legal claims. The most likely hypothesis is that the breach resulted from a targeted cyber intrusion. Confidence in this assessment is moderate due to limited available information.
2. Competing Hypotheses
- Hypothesis A: The data breach was a result of a targeted cyber intrusion by an external actor. This is supported by the unauthorized access to the network and acquisition of sensitive files. However, the identity and motive of the actor remain unclear.
- Hypothesis B: The breach was due to internal negligence or misconfiguration within Marquis Software Solutions. While possible, there is no direct evidence currently indicating internal fault.
- Assessment: Hypothesis A is currently better supported due to the nature of the unauthorized access and the typical profile of such breaches. Indicators that could shift this judgment include evidence of internal vulnerabilities or insider involvement.
3. Key Assumptions and Red Flags
- Assumptions: The breach involved external actors; the compromised data includes sensitive personal information; legal actions will proceed based on the breach’s impact.
- Information Gaps: Specific details about the breach’s origin, the full scope of compromised data, and the identity of the perpetrators.
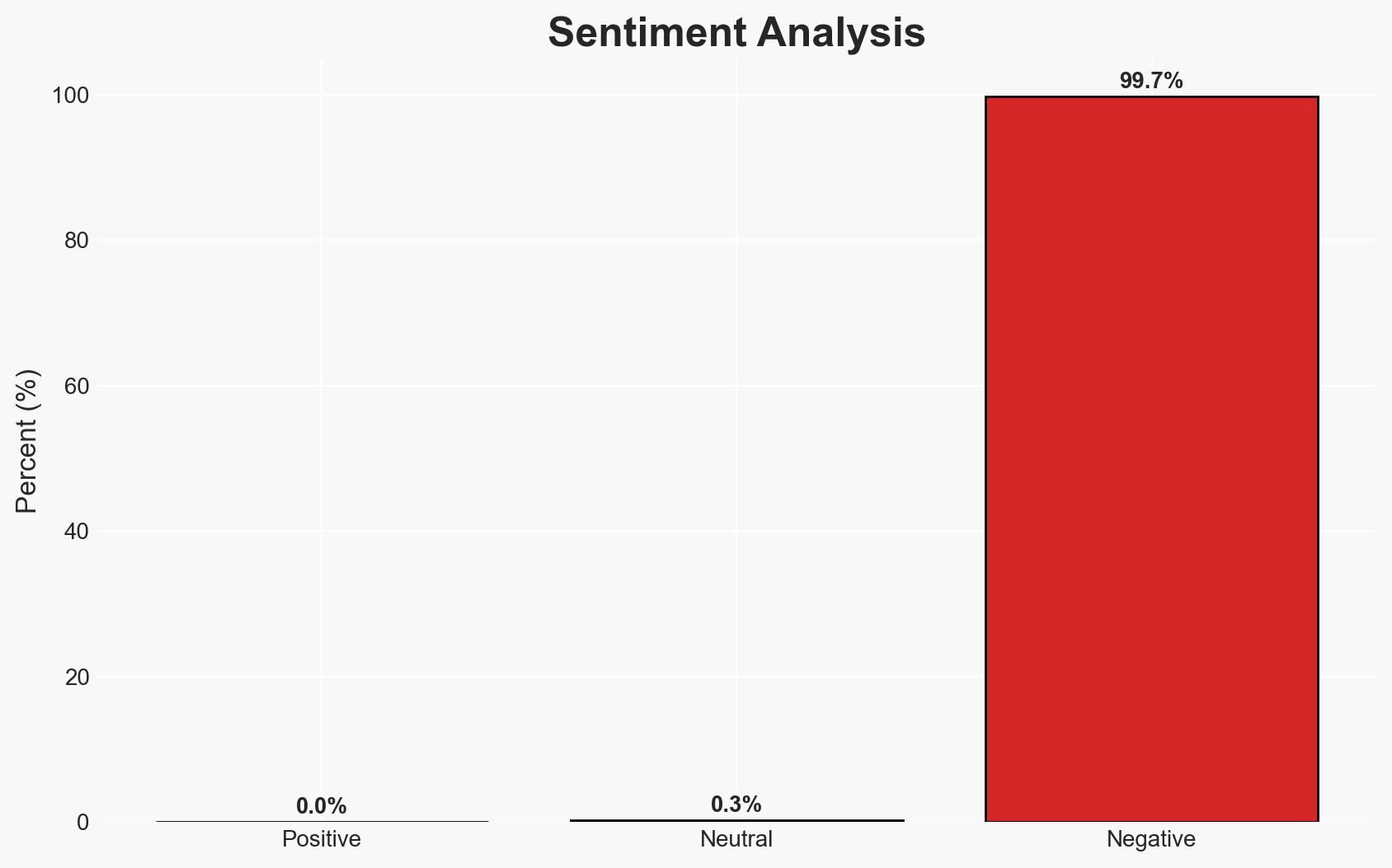
- Bias & Deception Risks: Potential bias from the investigating law firm due to vested interests in pursuing a class action lawsuit; possible underreporting or misdirection by involved parties to minimize reputational damage.
4. Implications and Strategic Risks
This data breach could lead to increased scrutiny of vendor security practices and regulatory pressures on financial institutions to enhance cybersecurity measures.
- Political / Geopolitical: Limited direct implications, but potential for increased regulatory action.
- Security / Counter-Terrorism: No immediate counter-terrorism implications, but highlights vulnerabilities in financial sector cybersecurity.
- Cyber / Information Space: Potential for further cyber intrusions if vulnerabilities are not addressed; increased risk of identity theft and fraud.
- Economic / Social: Possible financial losses for affected individuals; erosion of trust in financial institutions’ ability to safeguard data.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of affected systems, notify impacted customers, and offer identity theft protection services.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity protocols, conduct regular audits of vendor security practices, and foster partnerships for information sharing on threats.
- Scenario Outlook:
- Best Case: Breach contained with minimal impact, leading to improved security measures.
- Worst Case: Additional breaches occur, resulting in significant financial and reputational damage.
- Most Likely: Legal proceedings highlight vulnerabilities, prompting regulatory and institutional changes.
6. Key Individuals and Entities
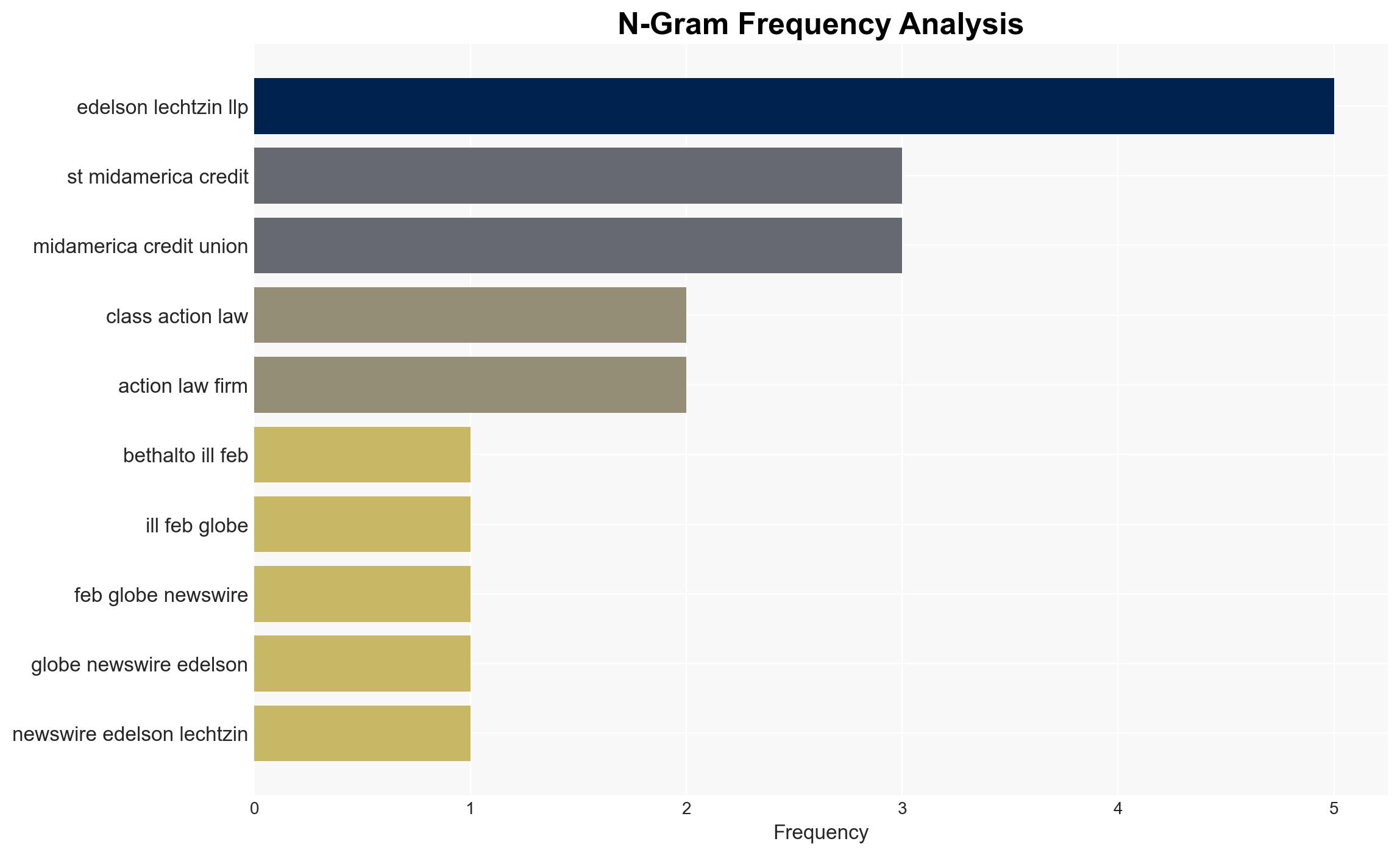
- 1st MidAmerica Credit Union
- Marquis Software Solutions
- Edelson Lechtzin LLP
- Eric Lechtzin, Esq.
7. Thematic Tags
cybersecurity, data breach, financial sector, legal investigation, identity theft, regulatory compliance, vendor management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us