Ivanti Releases Critical Patch for Actively Exploited Zero-Day Vulnerabilities in Endpoint Management Software
Published on: 2026-02-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ivanti Issues Urgent Fix for Critical Zero-Day Flaws Under Active Attack
1. BLUF (Bottom Line Up Front)
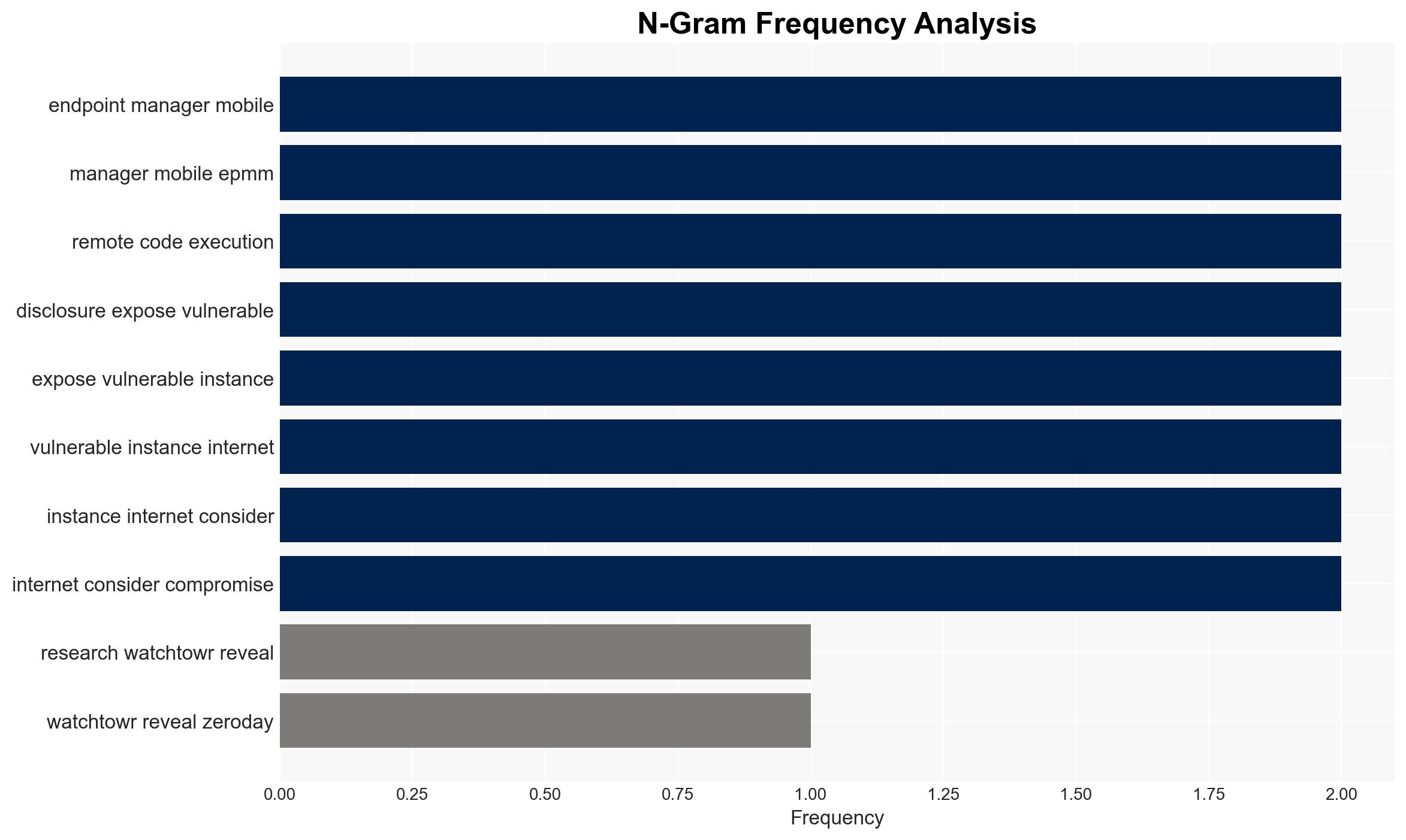
Ivanti’s Endpoint Manager Mobile software is under active exploitation due to critical zero-day vulnerabilities, necessitating immediate patch application. The flaws allow remote code execution, posing significant risks to organizations using the software. The most likely hypothesis is that these vulnerabilities will continue to be exploited until a permanent fix is implemented. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities in Ivanti’s software will be exploited primarily by opportunistic cybercriminals seeking immediate financial gain. This is supported by the history of similar vulnerabilities being exploited for ransomware attacks. However, the lack of specific attribution to financially motivated groups is a key uncertainty.
- Hypothesis B: State-sponsored actors are exploiting these vulnerabilities for espionage purposes. This hypothesis is supported by the strategic value of accessing corporate communications and data. Contradicting evidence includes the absence of direct attribution to any state actor and the immediate release of a patch by Ivanti, which may deter prolonged exploitation.
- Assessment: Hypothesis A is currently better supported due to the immediate financial incentives for cybercriminals and the lack of specific indicators pointing to state-sponsored involvement. Indicators that could shift this judgment include evidence of targeted attacks on high-value political or economic targets.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will apply the temporary patch promptly; the vulnerabilities are primarily exploited for financial gain; Ivanti will release a permanent fix within the projected timeline.
- Information Gaps: Specific attribution of the actors exploiting these vulnerabilities; detailed impact assessment on affected organizations.
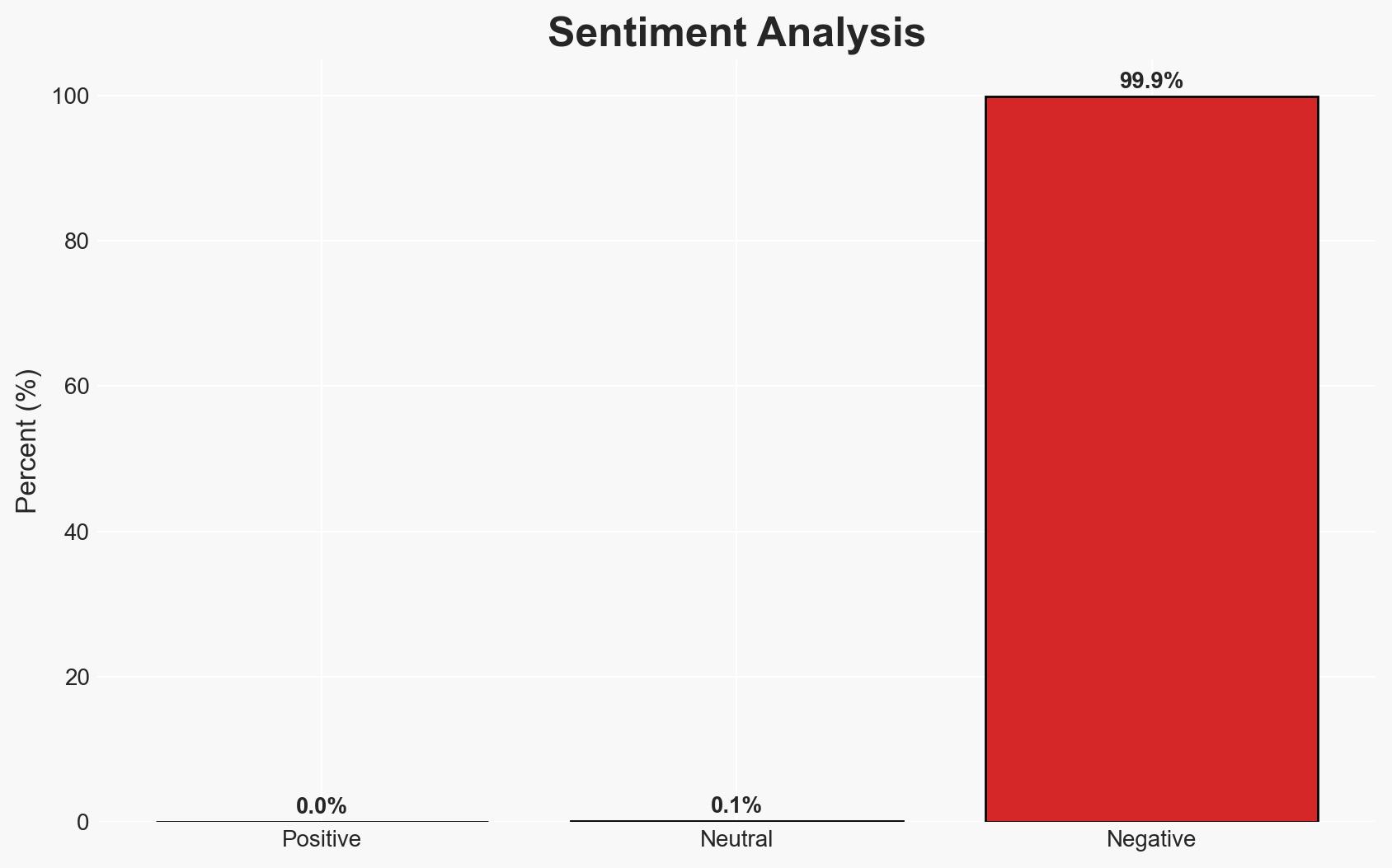
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests; possible underreporting of state-sponsored involvement due to lack of evidence.
4. Implications and Strategic Risks
The exploitation of Ivanti’s vulnerabilities could lead to increased cyber threats and operational disruptions for affected organizations. The situation may evolve with broader implications if state actors are involved.
- Political / Geopolitical: Escalation of tensions if state-sponsored involvement is confirmed, potentially leading to retaliatory cyber measures.
- Security / Counter-Terrorism: Increased risk of data breaches and unauthorized access to sensitive information, affecting organizational security postures.
- Cyber / Information Space: Potential for widespread cyber incidents if the vulnerabilities are not promptly patched, impacting the broader cybersecurity landscape.
- Economic / Social: Financial losses for affected companies and potential reputational damage, leading to broader economic implications.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urge organizations to apply the temporary patch immediately and monitor for signs of compromise; enhance network monitoring for unusual activity.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular software updates and incident response plans; foster partnerships for information sharing on emerging threats.
- Scenario Outlook:
- Best: Permanent fix is released promptly, minimizing exploitation risks.
- Worst: Exploitation continues, leading to significant breaches and economic damage.
- Most-Likely: Temporary patch mitigates immediate risks, but vulnerabilities remain a concern until a permanent fix is available.
6. Key Individuals and Entities
- Benjamin Harris, CEO of watchTowr
- Ivanti
- watchTowr
- Hackread.com
7. Thematic Tags
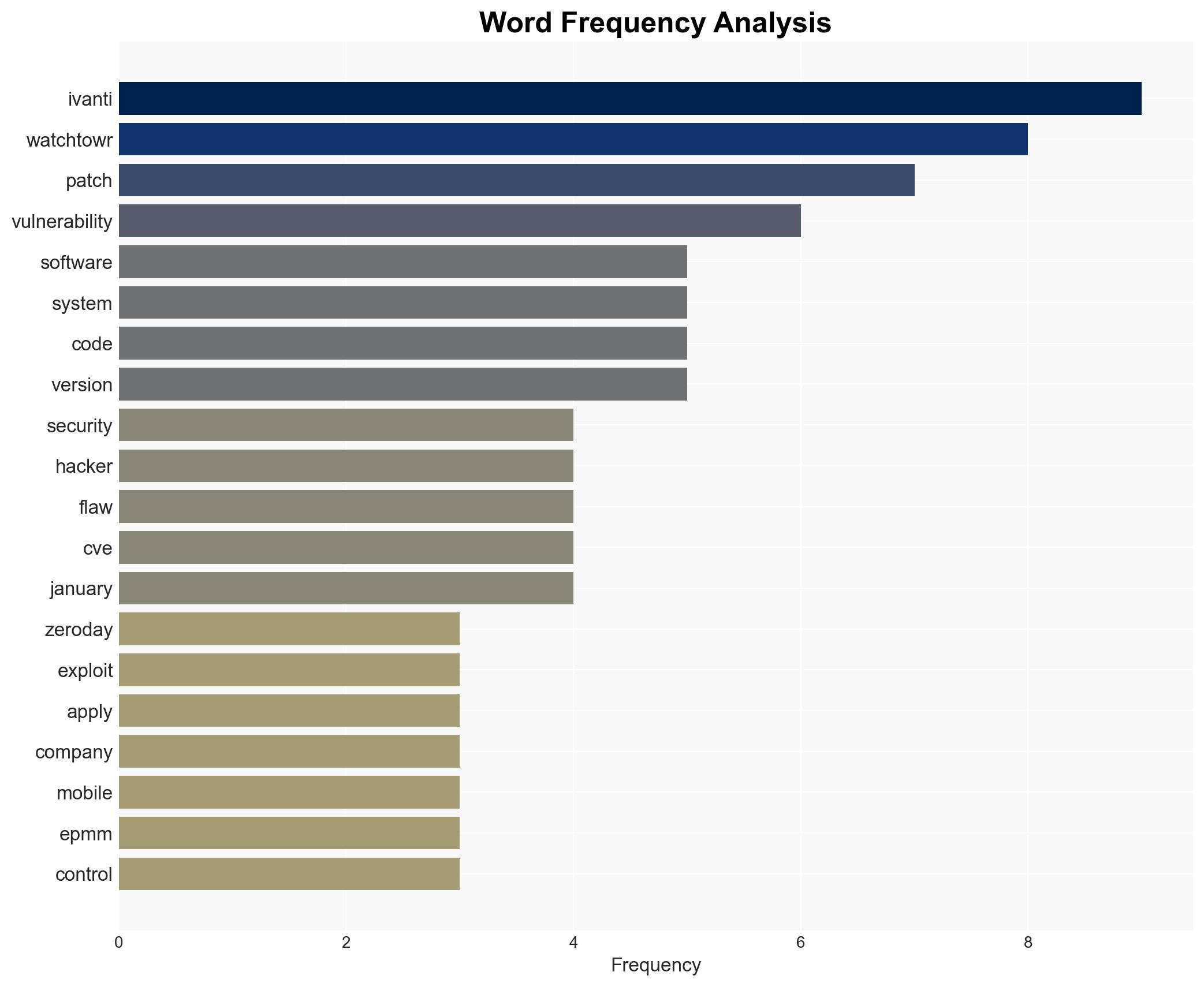
cybersecurity, zero-day vulnerabilities, remote code execution, software patching, cyber threats, information security, corporate IT management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us