Fancy Bear Exploits Microsoft Office Vulnerability CVE-2026-21509 in Phishing Campaign Targeting Users
Published on: 2026-02-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Russian hackers are exploiting recently patched Microsoft Office vulnerability CVE-2026-21509
1. BLUF (Bottom Line Up Front)
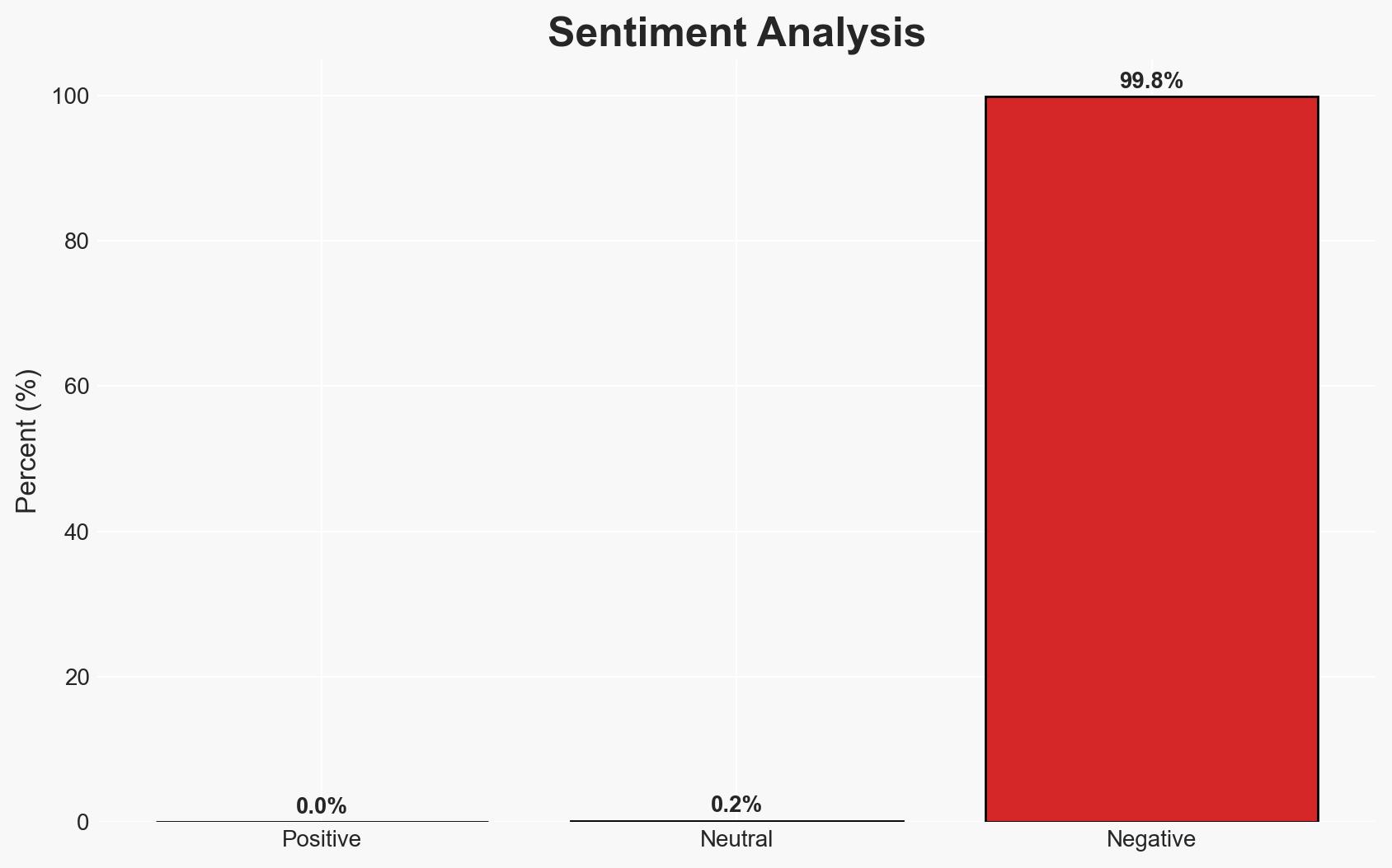
Russian state-sponsored group APT28 is exploiting a recently patched Microsoft Office vulnerability (CVE-2026-21509) to conduct cyber operations targeting entities in Central and Eastern Europe, including Ukraine. This campaign uses phishing emails to deliver malware, potentially compromising sensitive communications. The assessment is made with moderate confidence due to the attribution to APT28 and the observed attack patterns.
2. Competing Hypotheses
- Hypothesis A: APT28 is exploiting CVE-2026-21509 to conduct espionage operations against European entities. Supporting evidence includes the use of known APT28 tactics and targeting patterns. However, there is uncertainty regarding the full scope of the campaign and potential other actors involved.
- Hypothesis B: Another threat actor is mimicking APT28’s tactics to conduct similar operations, potentially to mislead attribution. This hypothesis is less supported due to the consistency of the tactics with APT28’s historical operations and the specific targeting of Ukrainian and European entities.
- Assessment: Hypothesis A is currently better supported due to the alignment of tactics and targets with APT28’s known activities. Indicators that could shift this judgment include evidence of different command and control infrastructure or divergent operational goals.
3. Key Assumptions and Red Flags
- Assumptions: APT28 has the capability and intent to exploit newly discovered vulnerabilities; the targeted entities have not fully patched the vulnerability; the attribution to APT28 is accurate based on current evidence.
- Information Gaps: Lack of detailed technical analysis of the malware components; limited visibility into the full list of targeted entities and the impact of the operations.
- Bias & Deception Risks: Attribution bias towards APT28 due to historical patterns; potential for adversarial deception in mimicking known threat actor tactics.
4. Implications and Strategic Risks
This exploitation could lead to increased geopolitical tensions and further cyber operations against European entities. The vulnerability’s exploitation may prompt broader cyber defense measures and policy responses.
- Political / Geopolitical: Potential escalation in cyber operations against European nations, impacting diplomatic relations.
- Security / Counter-Terrorism: Heightened threat environment for targeted regions, necessitating increased vigilance and response measures.
- Cyber / Information Space: Increased focus on patch management and vulnerability exploitation; potential for misinformation campaigns leveraging compromised data.
- Economic / Social: Limited immediate economic impact, but potential long-term effects on trust in digital infrastructure and services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urge rapid patching of CVE-2026-21509 across vulnerable systems; enhance monitoring for phishing campaigns and related indicators of compromise.
- Medium-Term Posture (1–12 months): Develop resilience measures including improved threat intelligence sharing and cybersecurity partnerships with affected regions.
- Scenario Outlook: Best: Rapid patching and defensive measures mitigate impact. Worst: Widespread exploitation leads to significant data breaches. Most-Likely: Continued targeted attacks with moderate impact, prompting increased cybersecurity measures.
6. Key Individuals and Entities
- APT28 (Fancy Bear) – Russian state-sponsored hacking group
- Zscaler – Cybersecurity firm identifying the campaign
- Ukrainian CERT – National cybersecurity authority in Ukraine
- Microsoft – Software company responsible for patching the vulnerability
7. Thematic Tags
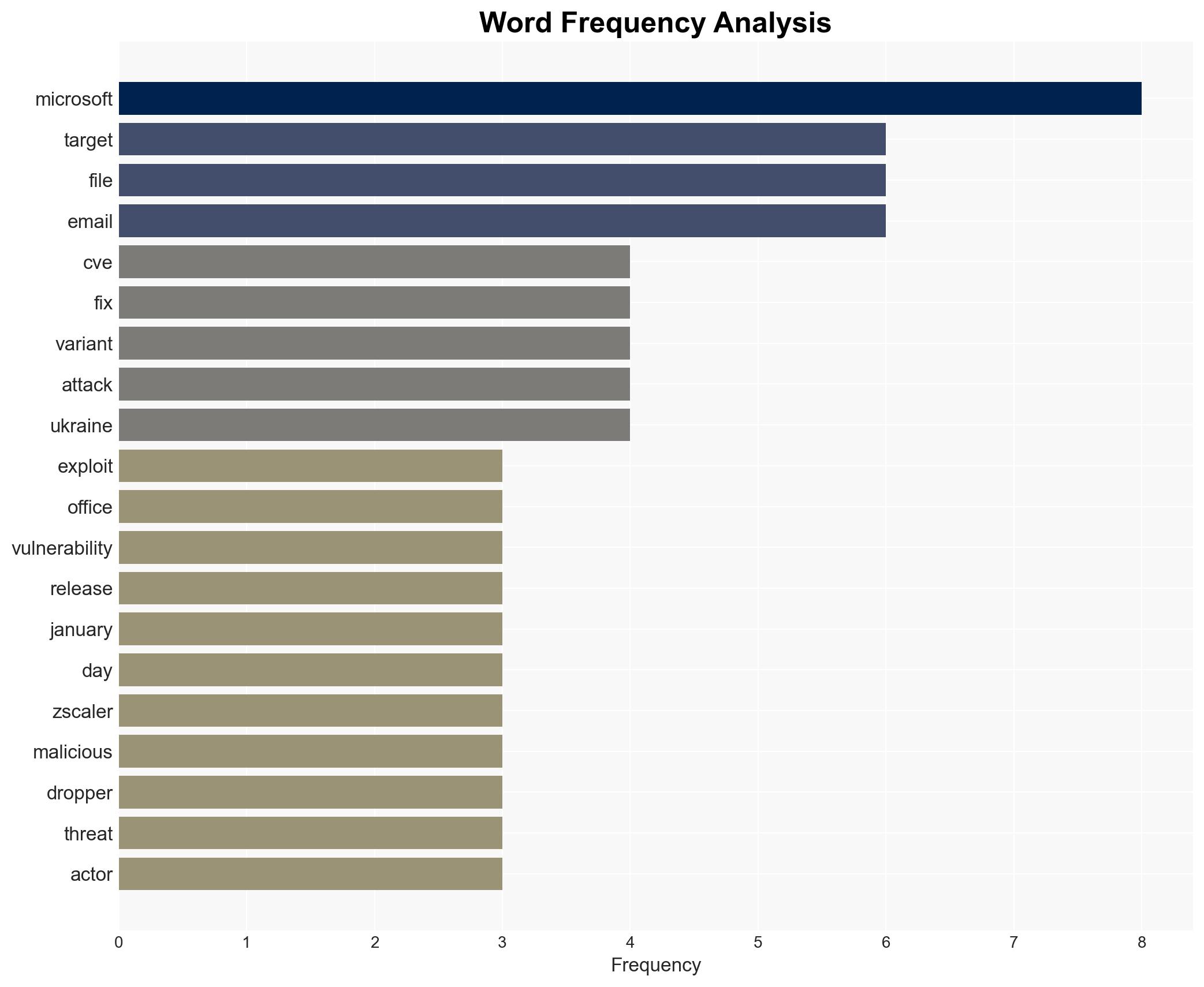
cybersecurity, cyber-espionage, vulnerability exploitation, APT28, phishing campaigns, Eastern Europe security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us