Indictments reveal organized smuggling network supplying Gaza with goods during wartime, aiding enemy operati…
Published on: 2026-02-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: This is how the smuggling network to Gaza operated
1. BLUF (Bottom Line Up Front)
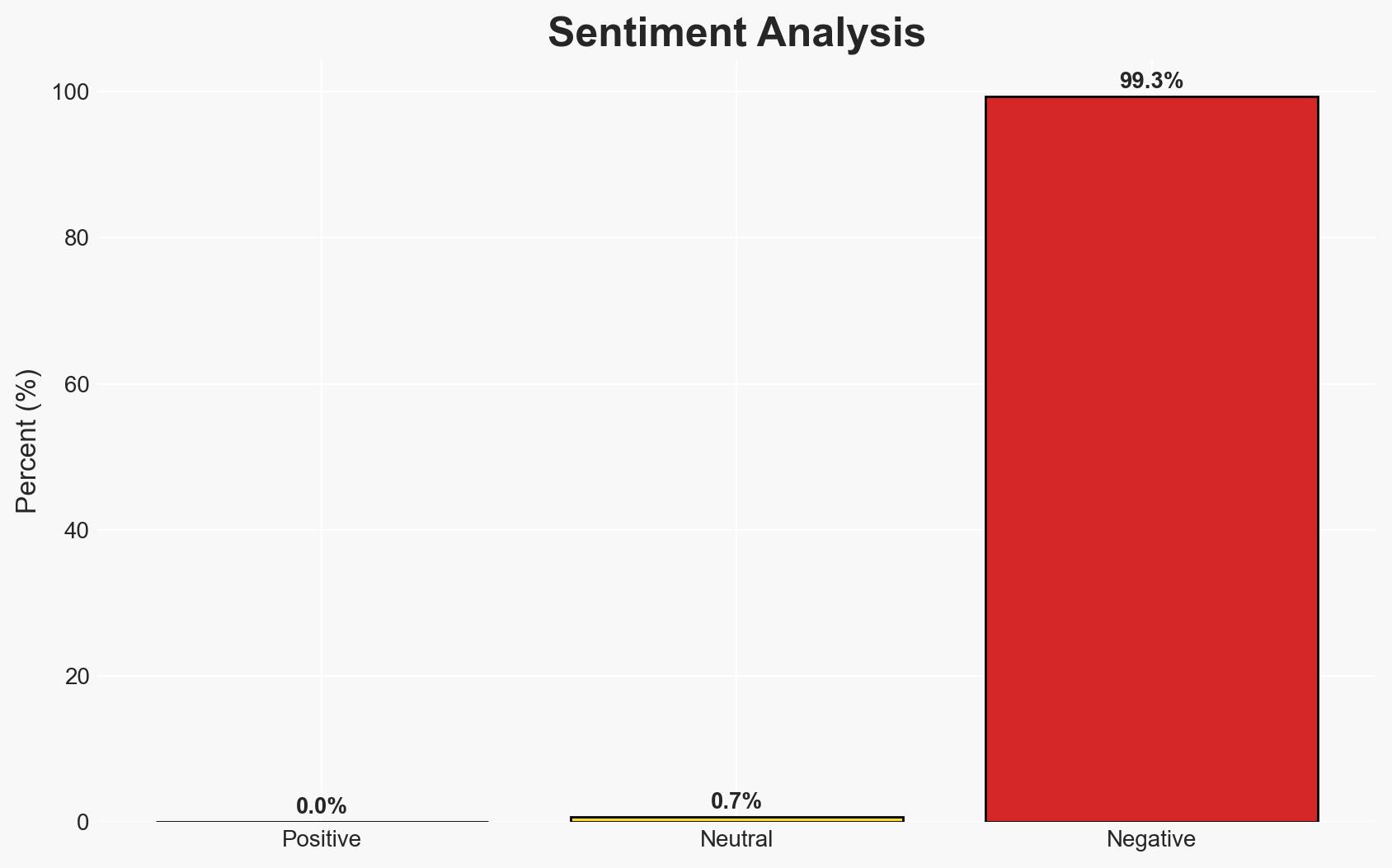
The recent indictments reveal a sophisticated smuggling network into Gaza, potentially aiding Hamas during wartime. The operation involved exploiting military and security vulnerabilities, with significant implications for Israeli national security. The most likely hypothesis is that the network was primarily financially motivated, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: The smuggling network was primarily financially motivated, exploiting vulnerabilities for profit. Evidence includes the diverse range of goods smuggled and the involvement of reservists accepting bribes. Key uncertainties include the extent of ideological alignment with Hamas.
- Hypothesis B: The network was ideologically driven, with financial gain as a secondary motive. This is supported by the awareness of aiding an enemy during wartime. Contradicting evidence includes the commercial nature of the goods and the lack of direct ideological statements.
- Assessment: Hypothesis A is currently better supported due to the commercial nature of the goods and the financial transactions involved. Indicators that could shift this judgment include evidence of ideological communications or directives from Hamas.
3. Key Assumptions and Red Flags
- Assumptions: The defendants acted primarily for financial gain; the smuggling network had limited direct contact with Hamas; the vulnerabilities at crossing points are not widely known.
- Information Gaps: The extent of Hamas’s involvement or awareness; the full scope of the network’s operations; potential other networks exploiting similar vulnerabilities.
- Bias & Deception Risks: Potential bias in focusing on financial motives over ideological ones; risk of deception by defendants to minimize perceived ideological alignment.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and security measures at crossing points, potentially disrupting legitimate trade and humanitarian efforts. It may also prompt retaliatory actions by Hamas if perceived as a crackdown on their supply lines.
- Political / Geopolitical: Potential escalation in Israeli-Palestinian tensions; increased diplomatic pressure on Israel to secure borders.
- Security / Counter-Terrorism: Heightened threat of smuggling networks supporting terrorist activities; need for enhanced counter-smuggling operations.
- Cyber / Information Space: Potential for cyber operations targeting Israeli security systems; misinformation campaigns to exploit the situation.
- Economic / Social: Disruption of trade routes could impact local economies; social unrest if perceived as targeting specific communities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase surveillance and security at crossing points; conduct a thorough review of vulnerabilities; engage with international partners for intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures for border security; strengthen partnerships with regional allies; invest in technology to detect and prevent smuggling.
- Scenario Outlook:
- Best: Successful dismantling of the network with minimal disruption to legitimate activities.
- Worst: Escalation of hostilities and increased smuggling activities.
- Most-Likely: Gradual tightening of security with intermittent disruptions and adjustments.
6. Key Individuals and Entities
- Eliran Algarabli, Avi Algarabli, Imad al-Din Abu Mukh, Ofer Sankar, Yosef Yochananov, Yuri Yakubov, Menachem Abutbul, Nadav Halfon, Meir Levi, Oshri Dahan, Yaron (Beni) Peretz, Atar Even, Anona (company).
7. Thematic Tags
Counter-Terrorism, smuggling, border security, financial crime, Hamas, Israeli-Palestinian conflict, intelligence operations
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us