Leading Open Source and Commercial Threat Intelligence Feeds for Enhanced Cybersecurity Defense
Published on: 2026-02-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Top open source and commercial threat intelligence feeds
1. BLUF (Bottom Line Up Front)
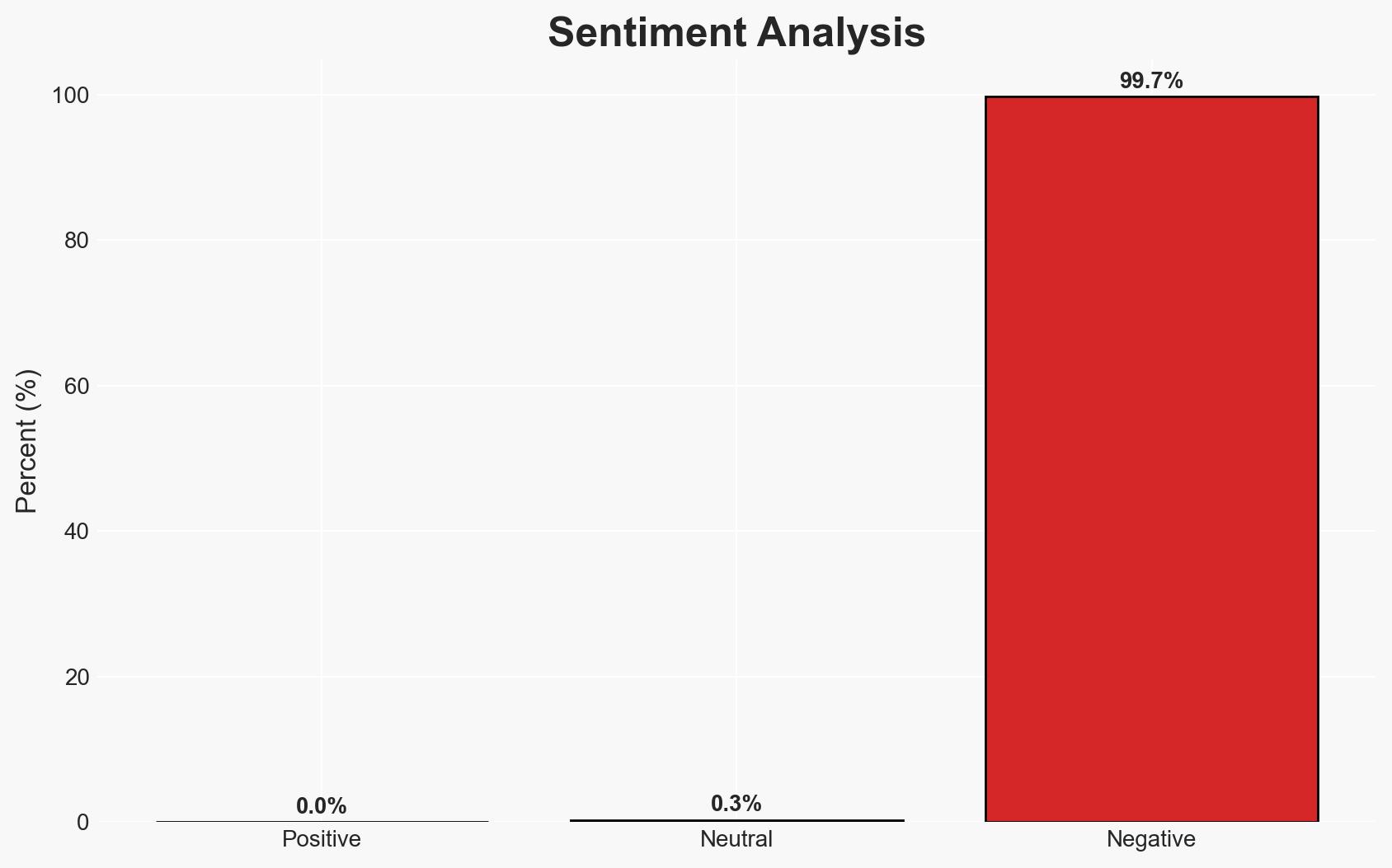
The integration of both open source and commercial threat intelligence feeds is crucial for enhancing cybersecurity defenses. Organizations that leverage these feeds can improve their detection and response capabilities, although the effectiveness varies based on the feed’s quality and relevance. The current assessment supports the hypothesis that a hybrid approach is optimal, with moderate confidence due to variability in feed quality and organizational needs.
2. Competing Hypotheses
- Hypothesis A: Organizations using both open source and commercial threat intelligence feeds achieve superior cybersecurity outcomes. This is supported by the complementary nature of the feeds, where commercial feeds provide resources and open source feeds offer diverse, community-driven insights. However, the quality of feeds varies, and not all organizations may benefit equally.
- Hypothesis B: Relying solely on commercial threat intelligence feeds is more effective due to their structured resources and verification processes. This hypothesis is contradicted by the potential lack of diversity and adaptability found in open source feeds, which can provide unique insights into emerging threats.
- Assessment: Hypothesis A is currently better supported as it aligns with the need for diverse threat data and the limitations of relying on a single source. Indicators such as feed accuracy, update frequency, and relevance to specific sectors could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have the capability to integrate and utilize multiple threat intelligence feeds; the quality of threat intelligence feeds is consistent over time; organizations can accurately assess the relevance of feeds to their specific needs.
- Information Gaps: Detailed metrics on the accuracy and timeliness of specific threat intelligence feeds; comprehensive data on the integration success rates across different organizations.
- Bias & Deception Risks: Potential bias in feed selection based on vendor relationships; risk of deception through manipulated or false data in open source feeds.
4. Implications and Strategic Risks
The evolution of threat intelligence feeds will likely influence cybersecurity strategies and resource allocation. Organizations may face increased pressure to adopt hybrid models to stay competitive in threat detection and response.
- Political / Geopolitical: Increased collaboration or tension among nations over cybersecurity standards and threat intelligence sharing.
- Security / Counter-Terrorism: Enhanced threat detection capabilities could disrupt planned cyber-attacks, but also lead to adversaries developing more sophisticated methods.
- Cyber / Information Space: Greater reliance on threat intelligence could lead to improved cybersecurity postures but also increase the risk of information overload and false positives.
- Economic / Social: Investment in threat intelligence feeds could drive economic growth in cybersecurity sectors, but also strain budgets if not managed effectively.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct an audit of current threat intelligence feeds; establish criteria for evaluating feed effectiveness and relevance.
- Medium-Term Posture (1–12 months): Develop partnerships with feed providers to ensure access to high-quality data; invest in training for security teams to better leverage threat intelligence.
- Scenario Outlook: Best: Organizations achieve high threat detection accuracy with minimal false positives. Worst: Over-reliance on poor-quality feeds leads to security breaches. Most-Likely: Incremental improvements in security posture as organizations refine feed integration strategies.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
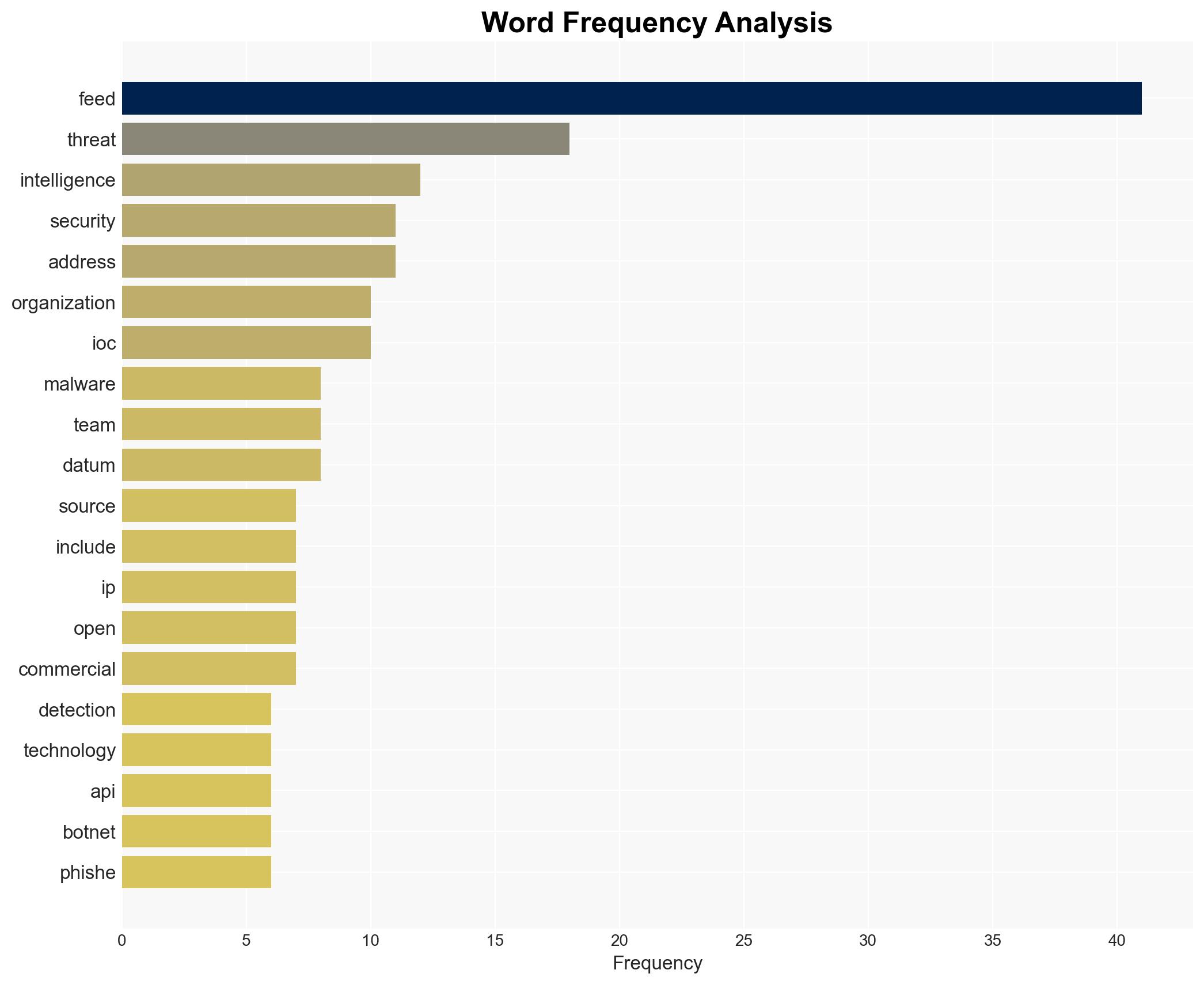
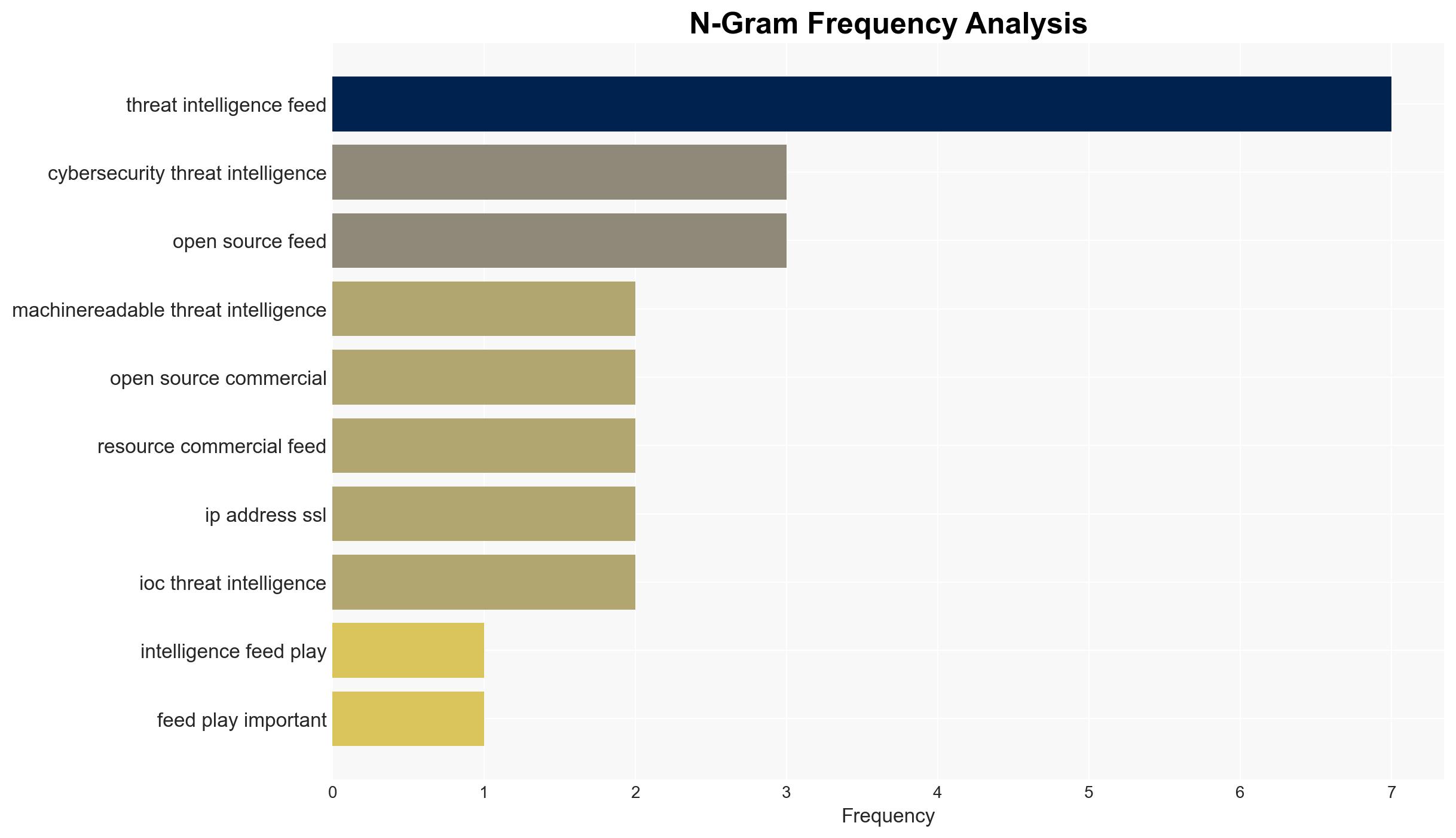
cybersecurity, threat intelligence, open source intelligence, commercial intelligence, cyber defense, information security, risk management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us