Canada Computers reports data breach impacting 1,284 customers, raising concerns over communication and respo…
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Nearly 1300 customers affected by Canada Computers data breach company says
1. BLUF (Bottom Line Up Front)
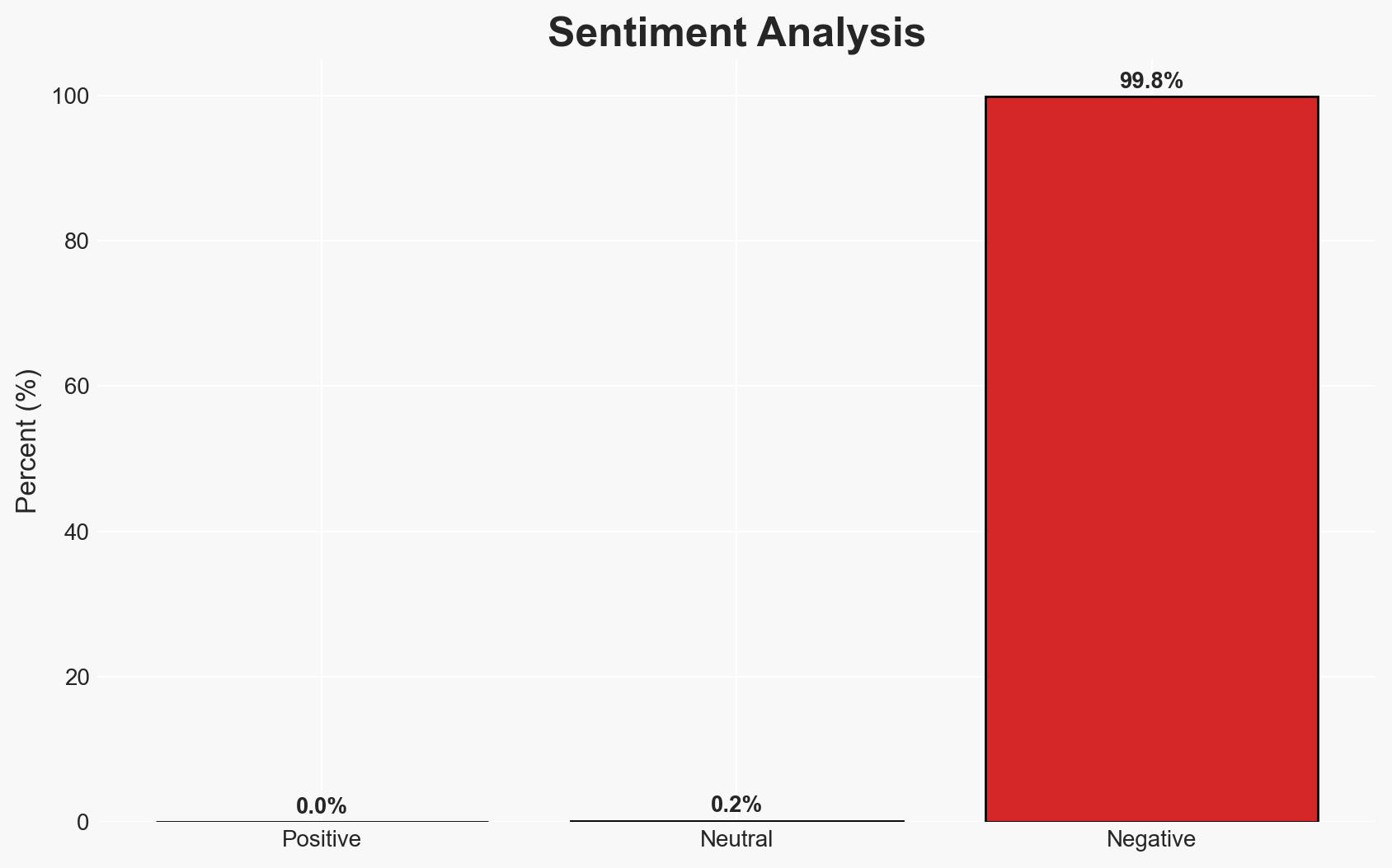
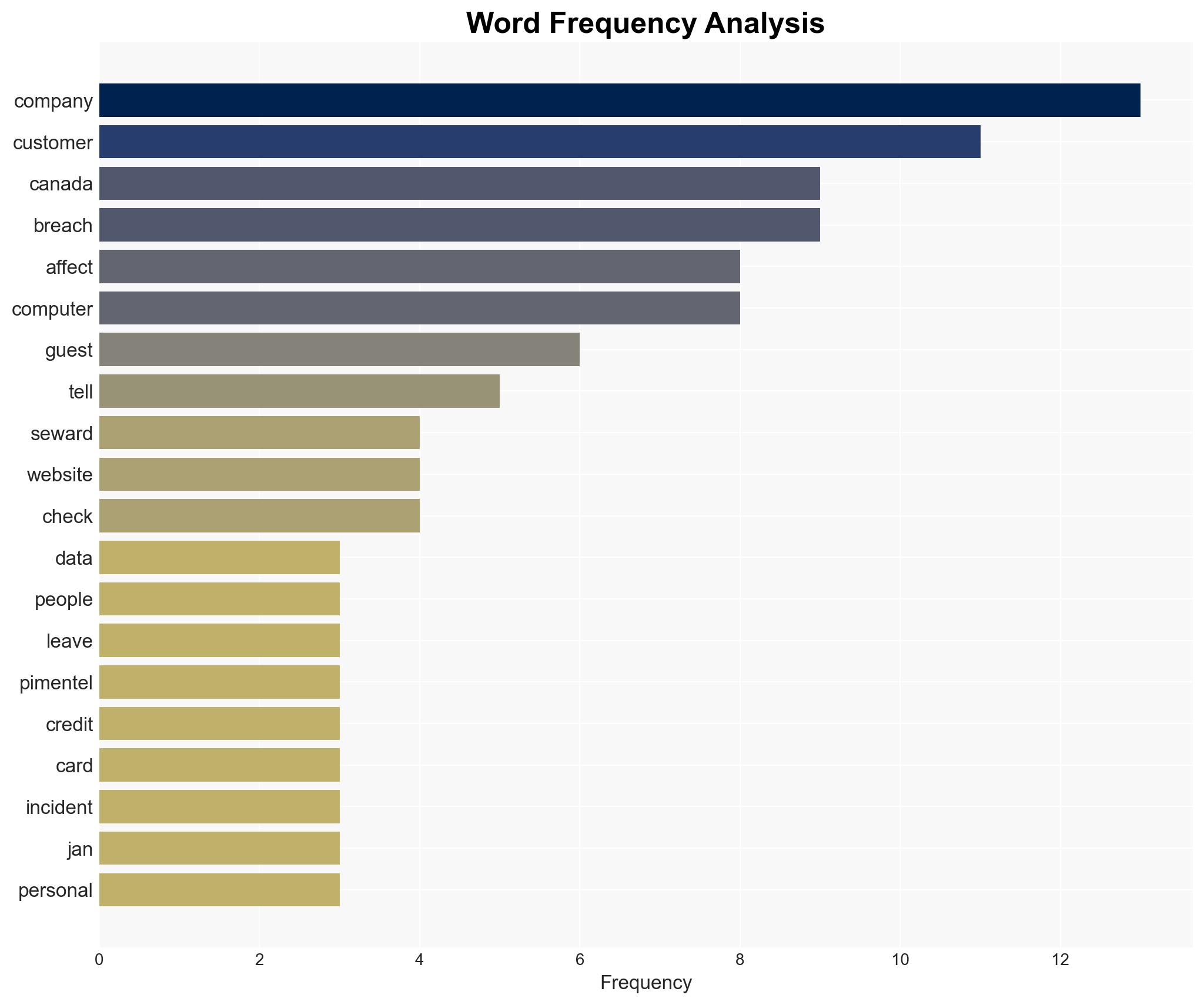
The data breach at Canada Computers has affected 1,284 customers, primarily those who checked out as guests on the company’s website. The incident highlights potential vulnerabilities in their cybersecurity protocols and communication strategies. The company’s response has been criticized for miscommunication, leading to customer dissatisfaction. Overall confidence in this assessment is moderate due to limited information on the breach’s full scope and impact.
2. Competing Hypotheses
- Hypothesis A: The data breach was a result of a targeted cyberattack exploiting vulnerabilities in Canada Computers’ online checkout system. Supporting evidence includes the breach’s focus on online guest checkouts. Contradicting evidence is the lack of detailed technical information about the breach.
- Hypothesis B: The breach was due to internal mismanagement or oversight, leading to accidental exposure of customer data. Supporting evidence includes the company’s admission of miscommunication and the confusion in notifying affected customers. Contradicting evidence is the company’s claim of unauthorized access.
- Assessment: Hypothesis A is currently better supported due to the nature of the breach involving unauthorized access. Key indicators that could shift this judgment include detailed forensic reports or evidence of insider involvement.
3. Key Assumptions and Red Flags
- Assumptions: The breach was limited to the stated 1,284 customers; the company’s cybersecurity measures were insufficient; the breach was detected promptly.
- Information Gaps: Detailed technical analysis of the breach, the timeline of detection and response, and the specific vulnerabilities exploited.
- Bias & Deception Risks: Potential bias in company statements aiming to minimize perceived impact; lack of independent verification of breach details.
4. Implications and Strategic Risks
This data breach could have significant implications for Canada Computers’ reputation and customer trust, potentially affecting its market position and financial stability.
- Political / Geopolitical: Minimal direct implications unless linked to broader cyber campaigns.
- Security / Counter-Terrorism: Increased scrutiny on cybersecurity practices in the retail sector.
- Cyber / Information Space: Potential for further cyberattacks exploiting similar vulnerabilities; increased public discourse on data privacy.
- Economic / Social: Possible decline in consumer confidence and sales; increased regulatory scrutiny and potential fines.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive forensic investigation, enhance cybersecurity measures, and improve communication with affected customers.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms, invest in staff training, and implement robust data protection policies.
- Scenario Outlook:
- Best: Breach contained with minimal impact, leading to improved security practices.
- Worst: Further breaches occur, leading to significant financial and reputational damage.
- Most-Likely: Short-term reputational damage with gradual recovery as security measures are enhanced.
6. Key Individuals and Entities
- Eric Pimentel, IT professional
- Brad Seward, customer
- Canada Computers & Electronics
- Terry Cutler, CEO of Cyology Labs
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, customer trust, retail sector, information security, cyber incident response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us