National Cybersecurity Strategies Evolve Towards Collaborative, Whole-of-Society Approaches
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cybersecurity planning keeps moving toward whole-of-society models
1. BLUF (Bottom Line Up Front)
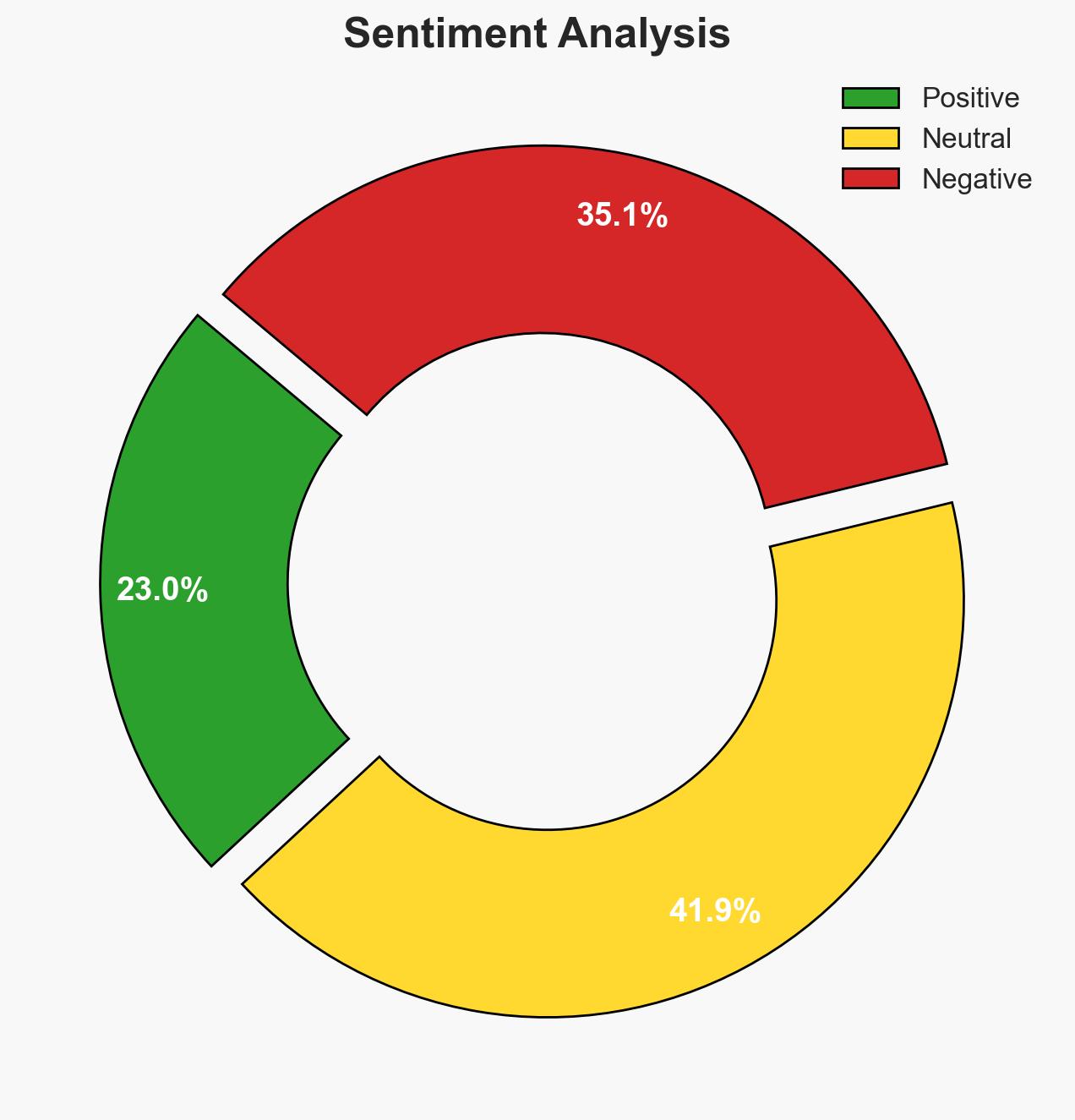
National cybersecurity strategies are increasingly adopting whole-of-society models, integrating government, industry, and civil society to manage cyber risks comprehensively. This approach aims to enhance resilience and trust in digital systems, aligning cybersecurity objectives with broader national priorities. The most likely hypothesis is that these strategies will improve national cybersecurity posture, though challenges remain in coordination and implementation. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The whole-of-society model will significantly enhance national cybersecurity by fostering comprehensive coordination and resource sharing across sectors. Supporting evidence includes the structured frameworks and central coordination bodies that facilitate cross-sector collaboration. Key uncertainties involve the effectiveness of these frameworks in practice and the willingness of private entities to fully engage.
- Hypothesis B: The whole-of-society model may face significant implementation challenges, leading to limited improvements in national cybersecurity. Contradicting evidence includes potential bureaucratic inefficiencies and resistance from private sector stakeholders. The success of this model is contingent on overcoming these barriers.
- Assessment: Hypothesis A is currently better supported due to the structured nature of existing frameworks and the alignment of cybersecurity objectives with national priorities. However, indicators such as private sector engagement levels and incident response effectiveness could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: National strategies will continue to prioritize cybersecurity; private sector cooperation will be forthcoming; central coordination bodies will maintain effectiveness; emerging technologies will be adequately integrated into risk assessments.
- Information Gaps: Detailed data on private sector engagement levels and the effectiveness of current coordination mechanisms are lacking.
- Bias & Deception Risks: Potential bias in overestimating government and private sector cooperation; risk of deception from stakeholders overstating their cybersecurity capabilities.
4. Implications and Strategic Risks
The evolution of whole-of-society cybersecurity models could significantly impact national security and economic stability. Effective implementation may lead to enhanced resilience against cyber threats, while failure could exacerbate vulnerabilities.
- Political / Geopolitical: Enhanced cybersecurity could strengthen national sovereignty and international standing, while failures may expose nations to geopolitical manipulation.
- Security / Counter-Terrorism: Improved coordination could reduce the impact of cyber-terrorism, though gaps could be exploited by adversaries.
- Cyber / Information Space: Increased information sharing may improve threat visibility but also risks data breaches and privacy concerns.
- Economic / Social: Successful strategies could bolster economic growth and public trust, while failures may lead to economic disruptions and social unrest.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of private sector engagement; initiate targeted consultations to address implementation barriers.
- Medium-Term Posture (1–12 months): Develop resilience measures and public-private partnerships; invest in cybersecurity workforce development and emerging technology integration.
- Scenario Outlook: Best: Effective implementation leads to robust national cybersecurity. Worst: Coordination failures result in increased vulnerabilities. Most-Likely: Gradual improvements with ongoing challenges in coordination and engagement.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
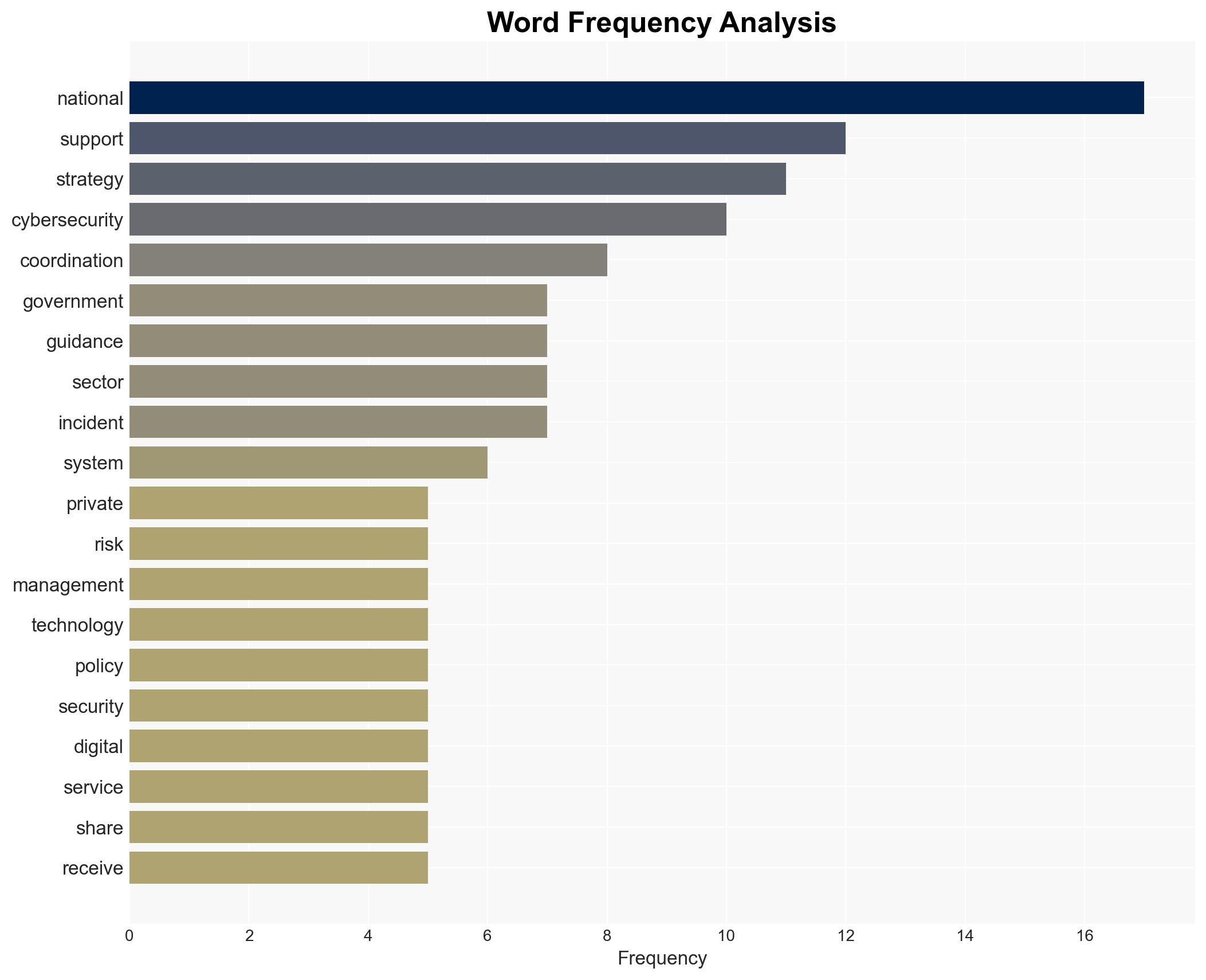
cybersecurity, national security, cybersecurity strategy, public-private partnership, risk management, digital transformation, information sharing, resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us