19-year-old arrested after driving 1,500 miles to abduct two minors he met online, police report
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
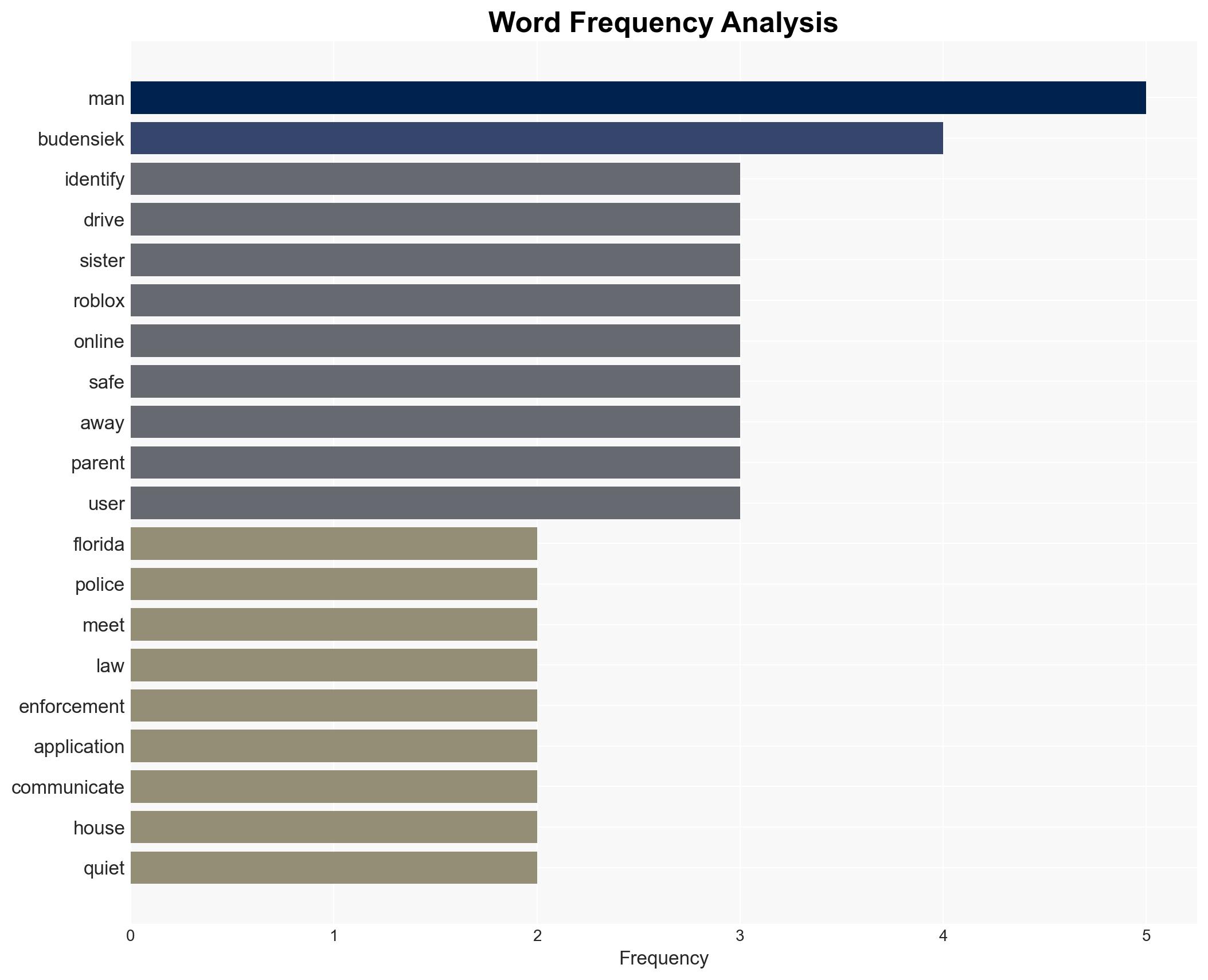
Intelligence Report: 19-year-old drove for 22 hours straight to kidnap 2 underage girls he met on Roblox game police say
1. BLUF (Bottom Line Up Front)
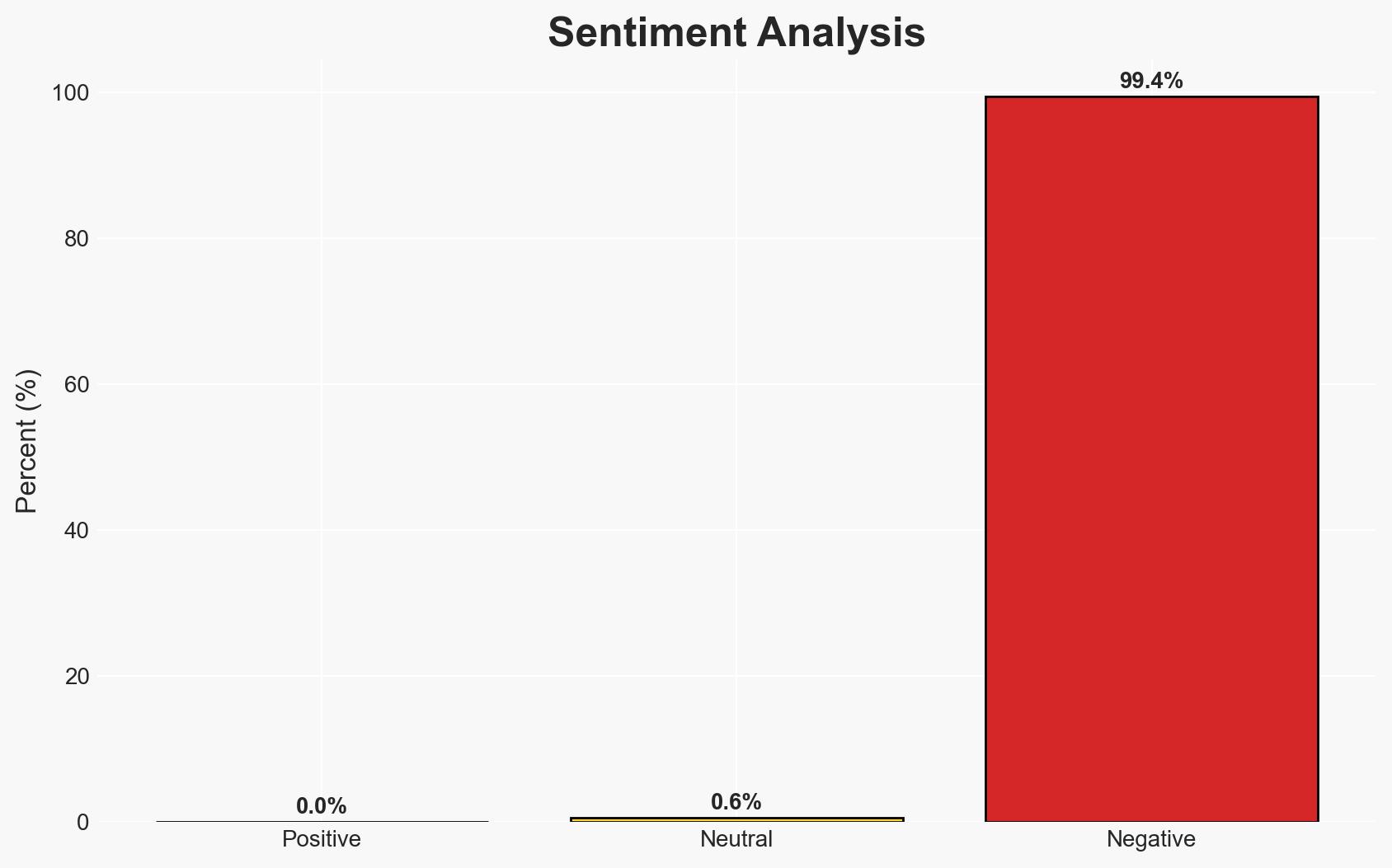
A 19-year-old male drove 1,500 miles to allegedly kidnap two underage girls he met online, highlighting vulnerabilities in digital platforms used by minors. The incident underscores the need for enhanced parental vigilance and platform security measures. Moderate confidence in the assessment that online safety for minors remains a critical issue.
2. Competing Hypotheses
- Hypothesis A: The suspect intended to harm or exploit the girls, evidenced by the long-distance travel and the clandestine nature of the communication. However, the exact intentions remain unclear due to lack of direct evidence of planned harm.
- Hypothesis B: The suspect may have been motivated by a misguided belief in a consensual relationship, supported by the use of social media for communication. Contradicted by the age difference and legal definitions of consent.
- Assessment: Hypothesis A is currently better supported due to the suspect’s covert actions and the legal charges of kidnapping, though further investigation could shift this judgment if evidence of alternative motives emerges.
3. Key Assumptions and Red Flags
- Assumptions: The suspect acted alone; the girls were unaware of the full implications of their actions; digital platforms have inherent vulnerabilities.
- Information Gaps: Detailed intentions of the suspect, communication content between the suspect and the victims, and potential prior incidents involving the suspect.
- Bias & Deception Risks: Potential bias in law enforcement narratives emphasizing parental responsibility; risk of underestimating the suspect’s sophistication or network.
4. Implications and Strategic Risks
This incident could prompt increased scrutiny of online platforms and parental controls, influencing regulatory and security measures in the tech industry.
- Political / Geopolitical: Potential for legislative action on digital safety standards and cross-state law enforcement collaboration.
- Security / Counter-Terrorism: Highlights the need for improved monitoring of online interactions to prevent exploitation and abduction.
- Cyber / Information Space: Raises concerns about the effectiveness of current digital safety protocols and the need for robust age verification systems.
- Economic / Social: Could lead to public pressure on tech companies to enhance safety features, impacting their operational costs and user trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of online platforms for suspicious activities; increase public awareness campaigns on digital safety for minors.
- Medium-Term Posture (1–12 months): Develop partnerships between tech companies and law enforcement to improve response times; invest in advanced AI tools for detecting predatory behavior online.
- Scenario Outlook:
- Best: Successful implementation of enhanced safety measures reduces similar incidents.
- Worst: Failure to address vulnerabilities leads to increased exploitation cases.
- Most-Likely: Incremental improvements in digital safety with ongoing challenges in enforcement and compliance.
6. Key Individuals and Entities
- Hser Mu Lah Say (suspect)
- Martin County Sheriff John Budensiek
- Roblox Corporation
- Georgia Highway Patrol
7. Thematic Tags
national security threats, online safety, child exploitation, digital platforms, law enforcement, cybersecurity, parental vigilance, cross-state collaboration
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us