Cyberattacks on Poland’s energy sector exploited vulnerable VPN configurations, linked to Russian threat acto…
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Polands energy control systems were breached through exposed VPN access
1. BLUF (Bottom Line Up Front)
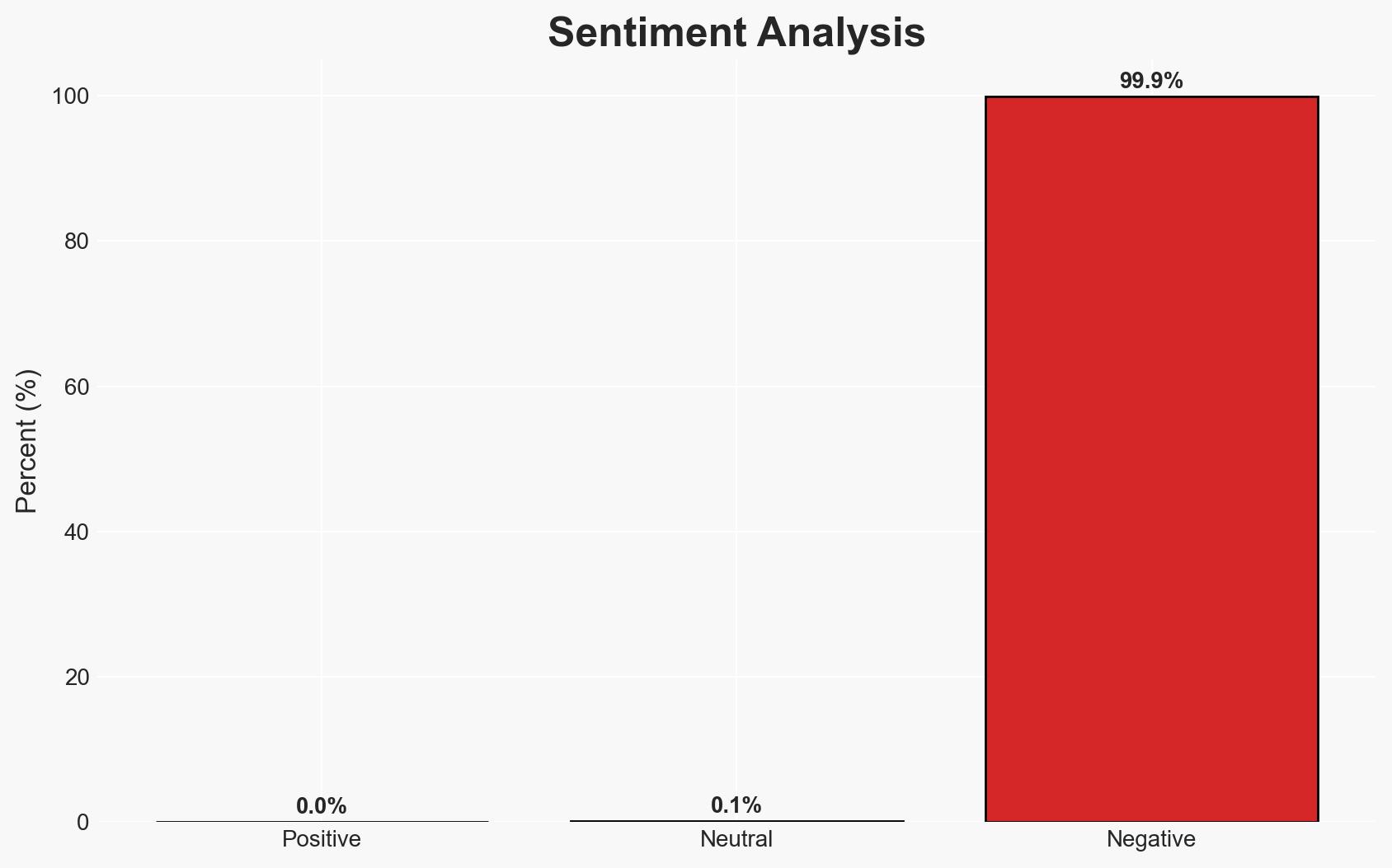
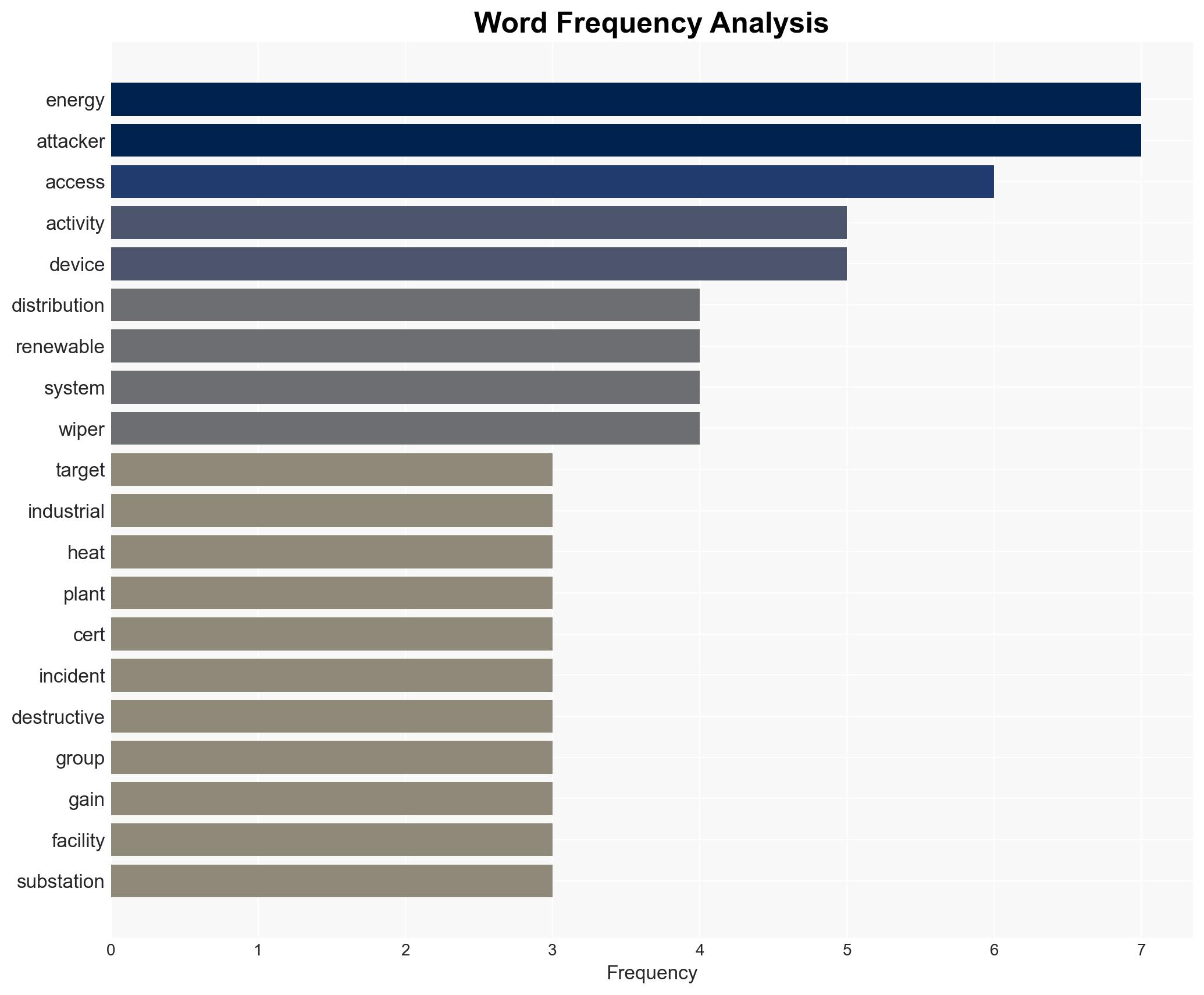
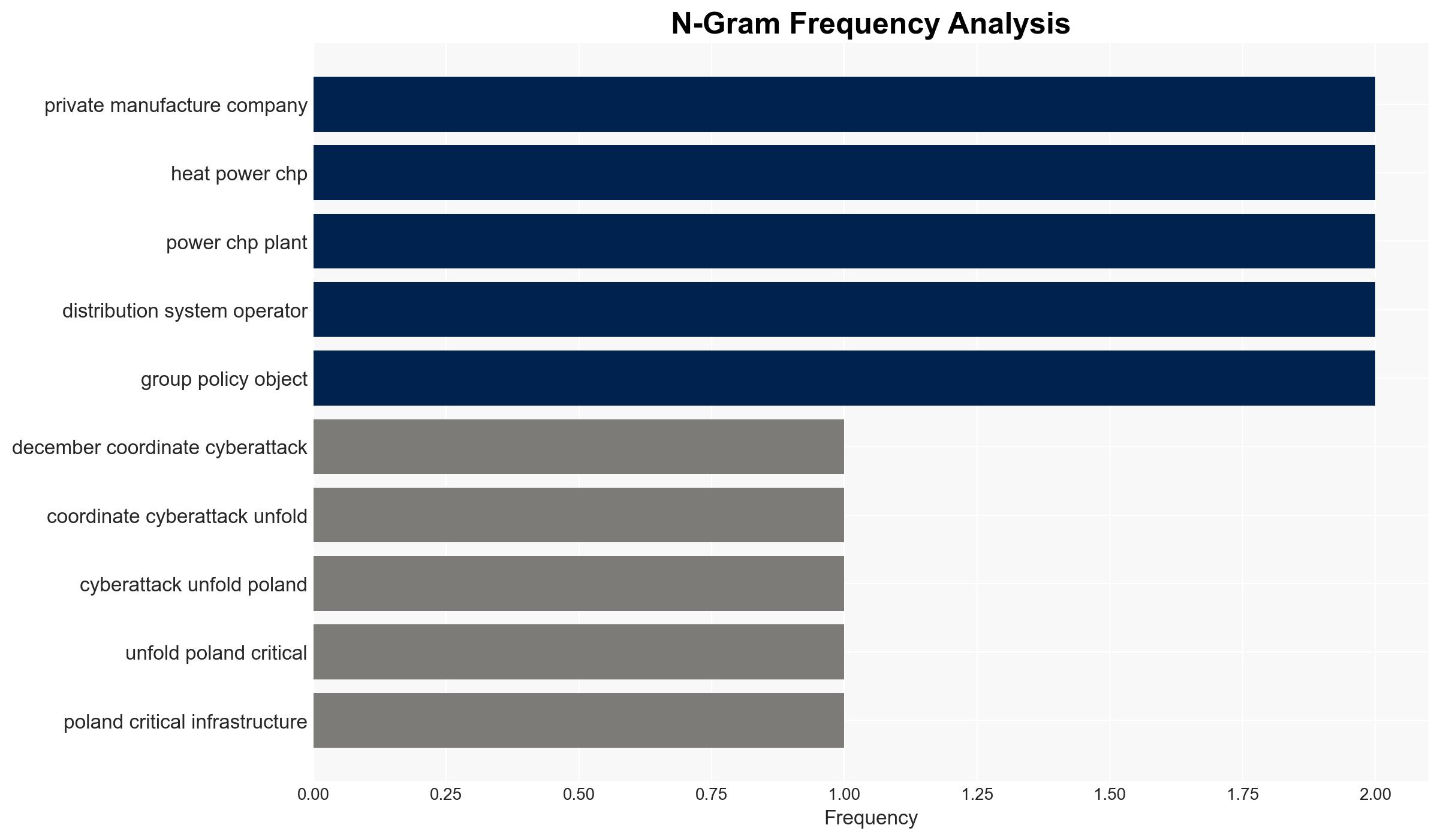
On 29 December 2025, coordinated cyberattacks targeted Poland’s critical energy infrastructure, exploiting exposed VPN access points. The attacks, attributed to a Russia-linked group, were destructive but did not disrupt energy generation. The incidents highlight vulnerabilities in Poland’s energy sector, with moderate confidence in the attribution to Russian actors.
2. Competing Hypotheses
- Hypothesis A: The attacks were conducted by a Russia-linked group aiming to disrupt Polish energy infrastructure as a geopolitical maneuver. This is supported by the alignment with known Russian threat actor tactics and the strategic targeting of critical infrastructure. However, the lack of direct impact on energy generation raises questions about the ultimate intent.
- Hypothesis B: The attacks were conducted by a non-state actor or cybercriminal group seeking to exploit vulnerabilities for financial gain or to test capabilities. The use of destructive tactics and the lack of ransom demands contradict this, but the possibility of misdirection or false flag operations remains.
- Assessment: Hypothesis A is currently better supported due to the alignment with known Russian cyber tactics and strategic interests in destabilizing regional adversaries. Indicators such as further geopolitical tensions or retaliatory actions could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attribution to a Russia-linked group is accurate; the primary intent was geopolitical disruption; Poland’s energy infrastructure remains a high-value target.
- Information Gaps: Detailed forensic evidence linking the attacks conclusively to a specific group; insights into the attackers’ long-term objectives; potential insider assistance.
- Bias & Deception Risks: Attribution bias towards Russia due to historical precedence; potential for false flag operations by other state or non-state actors.
4. Implications and Strategic Risks
The cyberattacks on Poland’s energy infrastructure could signal a broader campaign of cyber aggression in Eastern Europe, potentially escalating geopolitical tensions. The incidents underscore vulnerabilities in critical infrastructure that adversaries may exploit.
- Political / Geopolitical: Potential for increased tensions between Poland and Russia, with possible calls for NATO involvement or support.
- Security / Counter-Terrorism: Heightened alertness in Poland’s cybersecurity posture and potential for retaliatory cyber operations.
- Cyber / Information Space: Increased scrutiny on VPN configurations and cybersecurity protocols across critical sectors.
- Economic / Social: Potential investor concerns about the security of Poland’s energy infrastructure, impacting economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; conduct thorough forensic analysis; engage international partners for intelligence sharing.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity measures, including multi-factor authentication; develop resilience strategies; foster regional cybersecurity partnerships.
- Scenario Outlook:
- Best: Strengthened cybersecurity deters future attacks, leading to improved regional stability.
- Worst: Escalation into broader cyber conflict, impacting multiple sectors and international relations.
- Most-Likely: Continued low-level cyber skirmishes with periodic disruptions, prompting ongoing cybersecurity enhancements.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, critical infrastructure, Russia, energy sector, VPN vulnerabilities, geopolitical tensions, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us