CISA mandates US federal agencies to upgrade outdated edge devices to enhance cybersecurity measures
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA orders US federal agencies to replace unsupported edge devices
1. BLUF (Bottom Line Up Front)
The US Cybersecurity and Infrastructure Security Agency (CISA) has mandated federal agencies to replace unsupported edge devices to mitigate cyber risks. This directive is likely to enhance network security but may face implementation challenges. The most likely hypothesis is that this will lead to improved cybersecurity posture across federal networks. Overall confidence in this judgment is moderate.
2. Competing Hypotheses
- Hypothesis A: The directive will significantly reduce cyber risks by ensuring all edge devices are supported and secure. This is supported by the structured timeline and CISA’s technical assistance. However, uncertainties include the agencies’ ability to comply within the set deadlines and potential resource constraints.
- Hypothesis B: The directive will have limited impact due to potential non-compliance by agencies and the complexity of replacing numerous devices. This is supported by the lack of financial penalties for non-compliance and the historical challenges in federal IT modernization efforts.
- Assessment: Hypothesis A is currently better supported due to CISA’s proactive measures and the legal weight of the directive. Indicators such as timely compliance reports and reduced cyber incidents could further support this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Agencies have the necessary resources to comply; CISA’s list of end-of-service devices is comprehensive; technical assistance from CISA will be effective; the directive will not face significant legal or political challenges.
- Information Gaps: Specific compliance rates of agencies; detailed resource allocation for implementation; potential resistance from agencies due to operational disruptions.
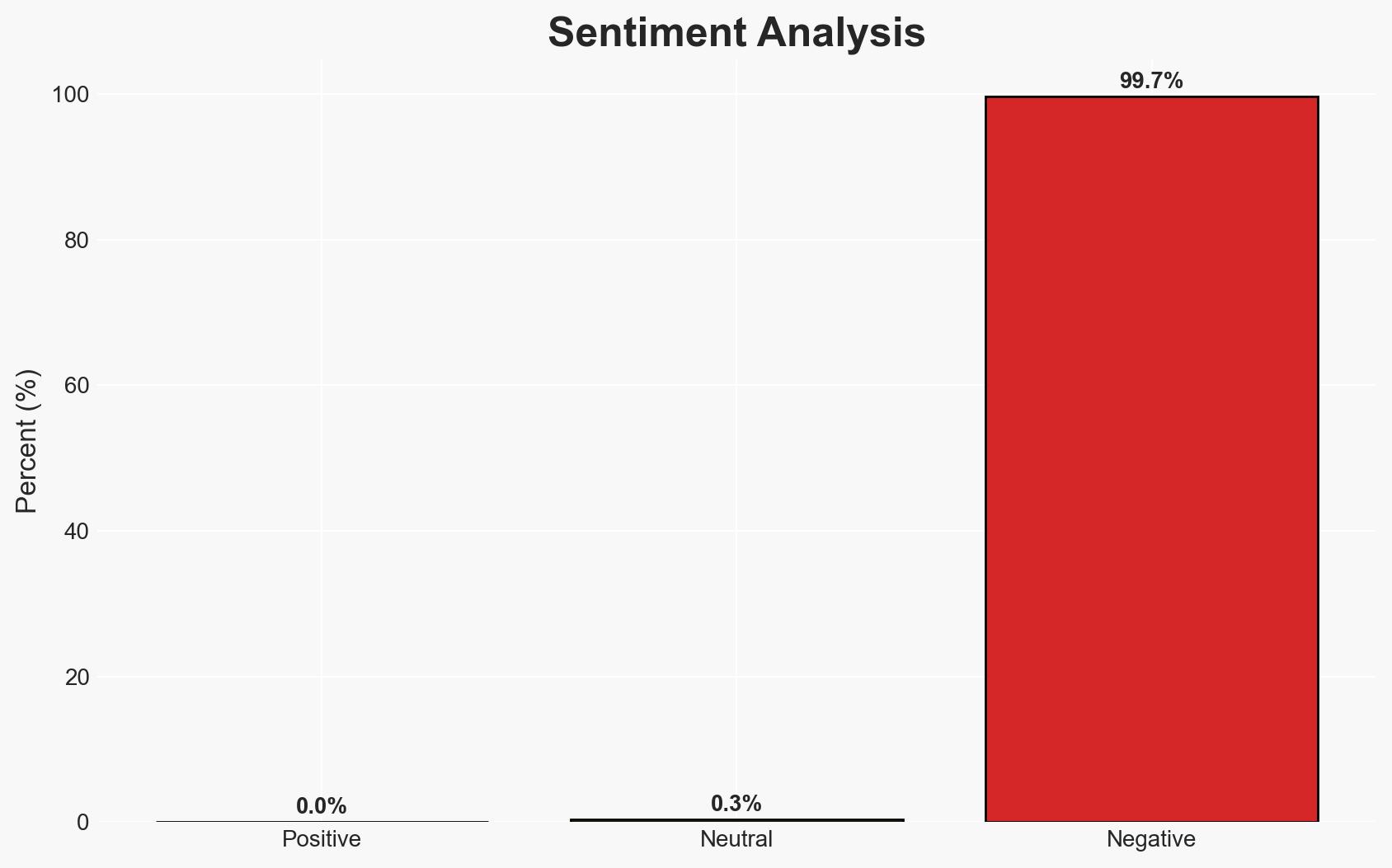
- Bias & Deception Risks: Optimism bias in assessing agency capabilities; potential underreporting of non-compliance; adversarial misinformation campaigns targeting perceived vulnerabilities.
4. Implications and Strategic Risks
This directive could lead to a more secure federal network environment, but its success depends on effective implementation and compliance monitoring. The evolution of this initiative will interact with broader cybersecurity and policy dynamics.
- Political / Geopolitical: Strengthened cybersecurity could enhance national security posture and international confidence in US cyber defenses.
- Security / Counter-Terrorism: Reduced risk of cyber intrusions could lower the threat level from state and non-state actors exploiting outdated devices.
- Cyber / Information Space: Improved network security may deter cyber espionage and reduce the attack surface for adversaries.
- Economic / Social: Potential short-term financial strain on agencies due to replacement costs; long-term economic benefits from reduced cyber incidents.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Agencies should conduct an immediate inventory of edge devices and prioritize patching; CISA should establish a robust compliance monitoring mechanism.
- Medium-Term Posture (1–12 months): Develop inter-agency partnerships for resource sharing; enhance training programs for IT staff on lifecycle management.
- Scenario Outlook:
- Best: Full compliance leads to a significant reduction in cyber incidents.
- Worst: Widespread non-compliance results in continued vulnerabilities.
- Most-Likely: Partial compliance with gradual improvement in cybersecurity posture.
6. Key Individuals and Entities
- US Cybersecurity and Infrastructure Security Agency (CISA)
- Office of Management and Budget
- US Federal Civilian Agencies
- Advanced Threat Actors (implied adversaries)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
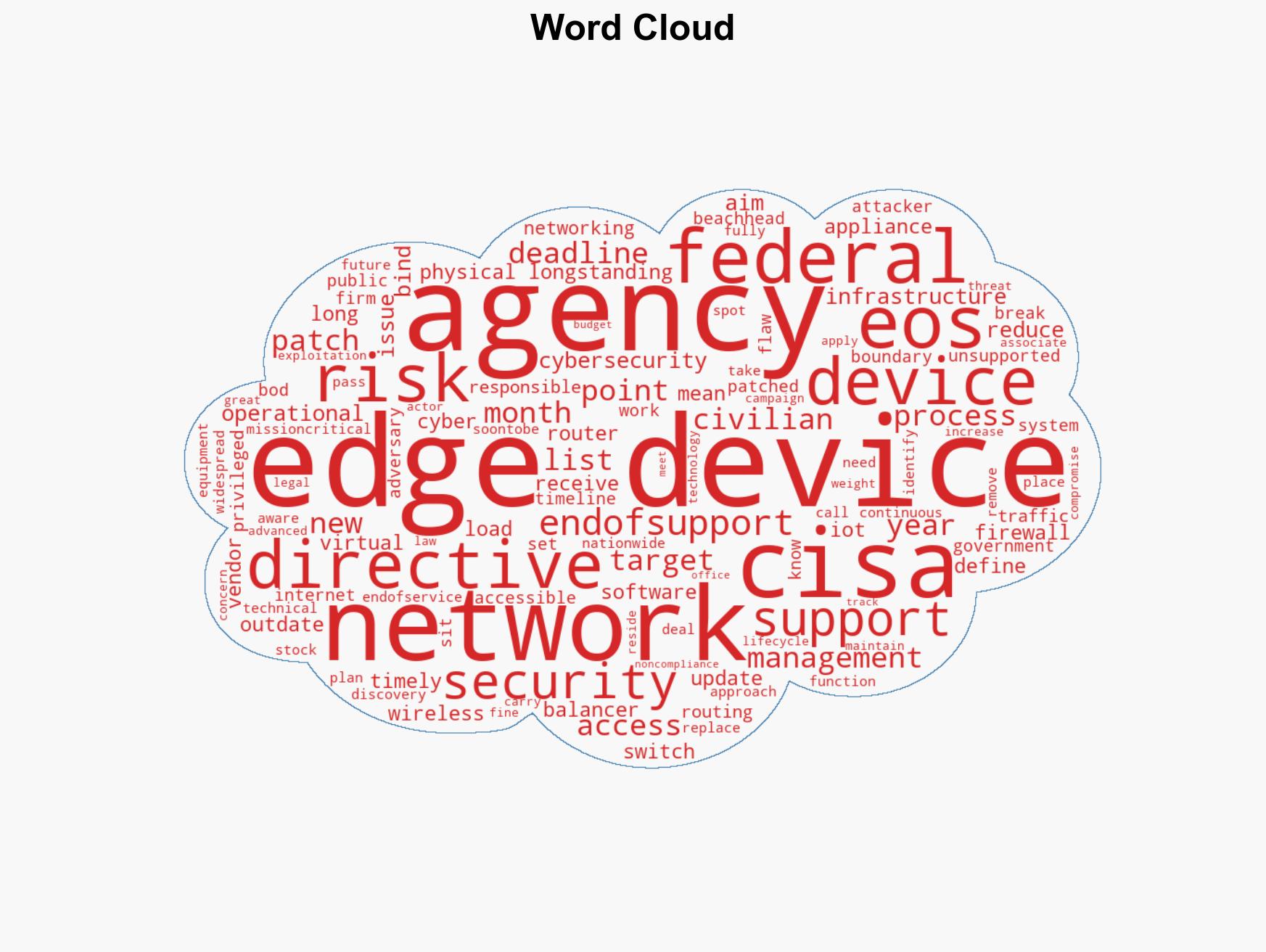
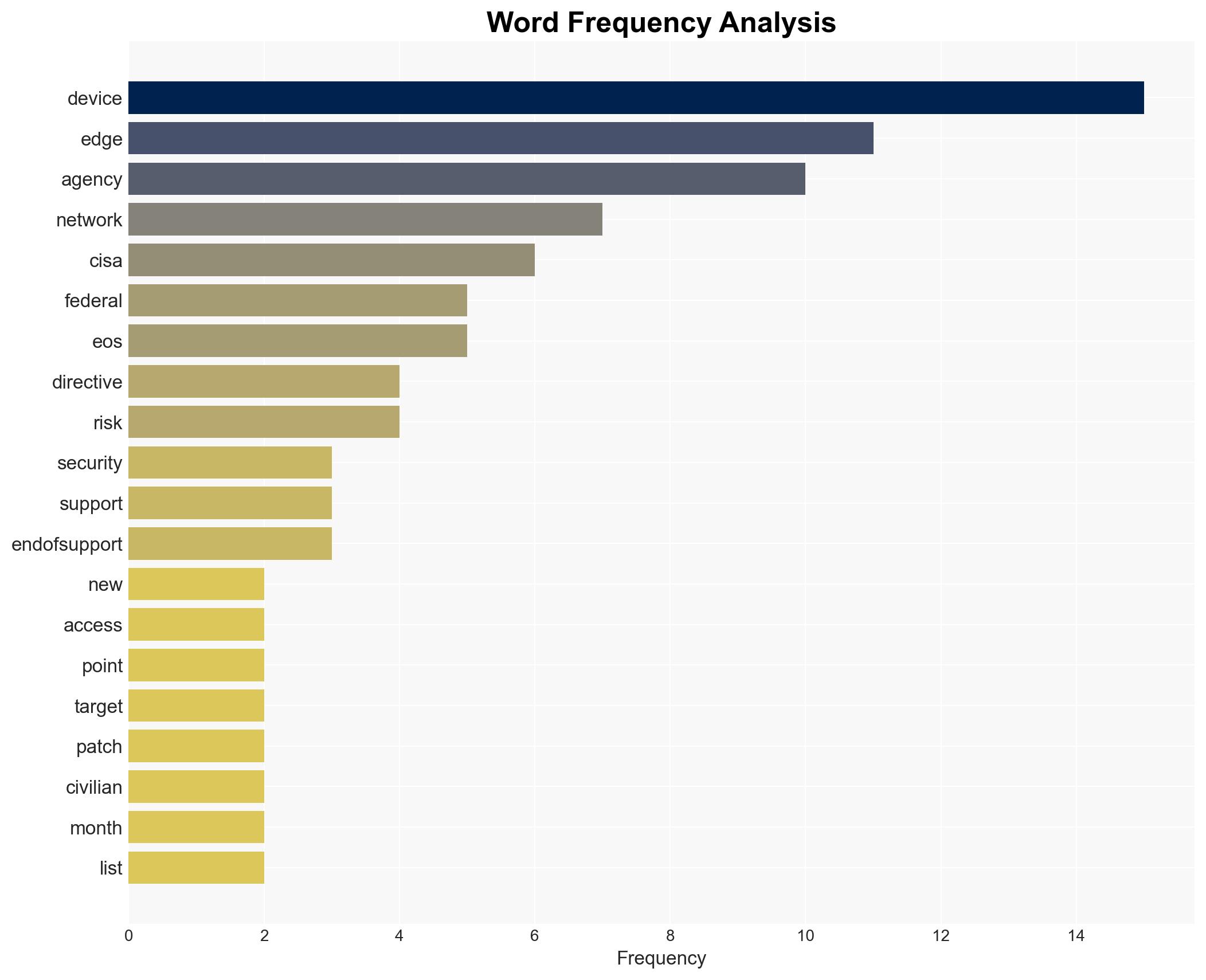
cybersecurity, federal networks, CISA directive, edge devices, compliance, cyber risk management, IT modernization
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us