Malware Framework DKnife Discovered, Targeting Chinese Routers and Edge Devices by Chinese-Nexus Actors
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Chinese-Made Malware Kit Targets Chinese-Based Routers and Edge Devices
1. BLUF (Bottom Line Up Front)
The DKnife malware framework, attributed to Chinese-nexus threat actors, targets Chinese-based routers and edge devices, posing significant cyber threats to network infrastructure. The framework’s capabilities for deep packet inspection and traffic manipulation suggest a sophisticated tool for persistent access and data exfiltration. This assessment is made with moderate confidence due to the technical evidence provided by Cisco Talos and the potential for shared development with other known frameworks.
2. Competing Hypotheses
- Hypothesis A: DKnife is a state-sponsored tool developed by Chinese threat actors for cyber-espionage and network manipulation. This is supported by the language in the code, infrastructure overlaps, and the use of known Chinese-linked malware like ShadowPad. However, the exact state affiliation remains uncertain.
- Hypothesis B: DKnife is a commercially developed tool by independent Chinese cybercriminals for financial gain. This hypothesis considers the modular and adaptable nature of the framework, which could be marketed to various clients. Contradictory evidence includes the strategic targeting of routers, which aligns more with espionage than financial motives.
- Assessment: Hypothesis A is currently better supported due to the technical indicators and strategic targeting consistent with state-sponsored activities. Future indicators such as attribution from other cybersecurity firms or changes in targeting could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The malware’s targeting of Chinese-speaking users implies a focus on domestic or regional networks; the infrastructure overlaps indicate a shared development lineage; the use of known Chinese malware suggests a nexus with Chinese threat actors.
- Information Gaps: Lack of direct attribution to a specific Chinese state entity; limited visibility into the full scope of DKnife’s deployment and impact.
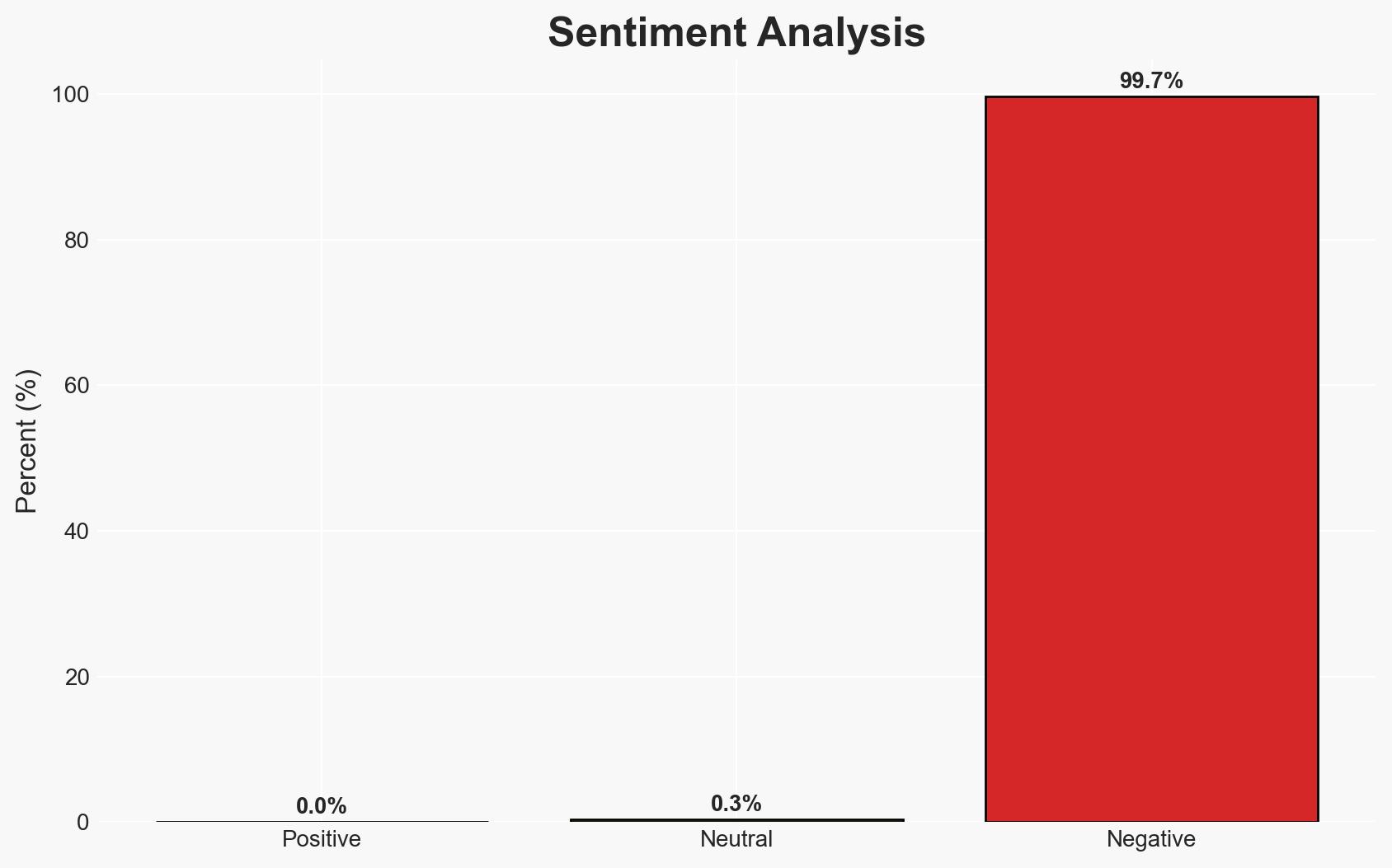
- Bias & Deception Risks: Potential confirmation bias in attributing the malware to Chinese actors based solely on language and infrastructure overlaps; risk of deception through false flag operations by non-Chinese actors.
4. Implications and Strategic Risks
The discovery of DKnife underscores the evolving sophistication of cyber threats targeting critical network infrastructure. This development could lead to increased tensions in cyber diplomacy and necessitate enhanced cybersecurity measures.
- Political / Geopolitical: Potential escalation in cyber tensions between China and other nations, particularly if state sponsorship is confirmed.
- Security / Counter-Terrorism: Increased vulnerability of network infrastructure, requiring heightened vigilance and response capabilities.
- Cyber / Information Space: Enhanced threat landscape with potential for widespread data breaches and network disruptions.
- Economic / Social: Possible economic impacts from disrupted network services and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of network traffic for signs of DKnife activity; collaborate with cybersecurity firms for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures for critical infrastructure; strengthen international partnerships for coordinated cyber defense.
- Scenario Outlook: Best: DKnife is neutralized through coordinated international efforts. Worst: Widespread network disruptions and data breaches occur. Most-Likely: Continued targeted attacks with incremental improvements in detection and response capabilities.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, network security, Chinese threat actors, malware analysis, cyber defense, infrastructure protection, cyber diplomacy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us