DKnife toolkit exploits routers for malware delivery and espionage, active since 2019, linked to Chinese thre…
Published on: 2026-02-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: DKnife toolkit abuses routers to spy and deliver malware since 2019
1. BLUF (Bottom Line Up Front)
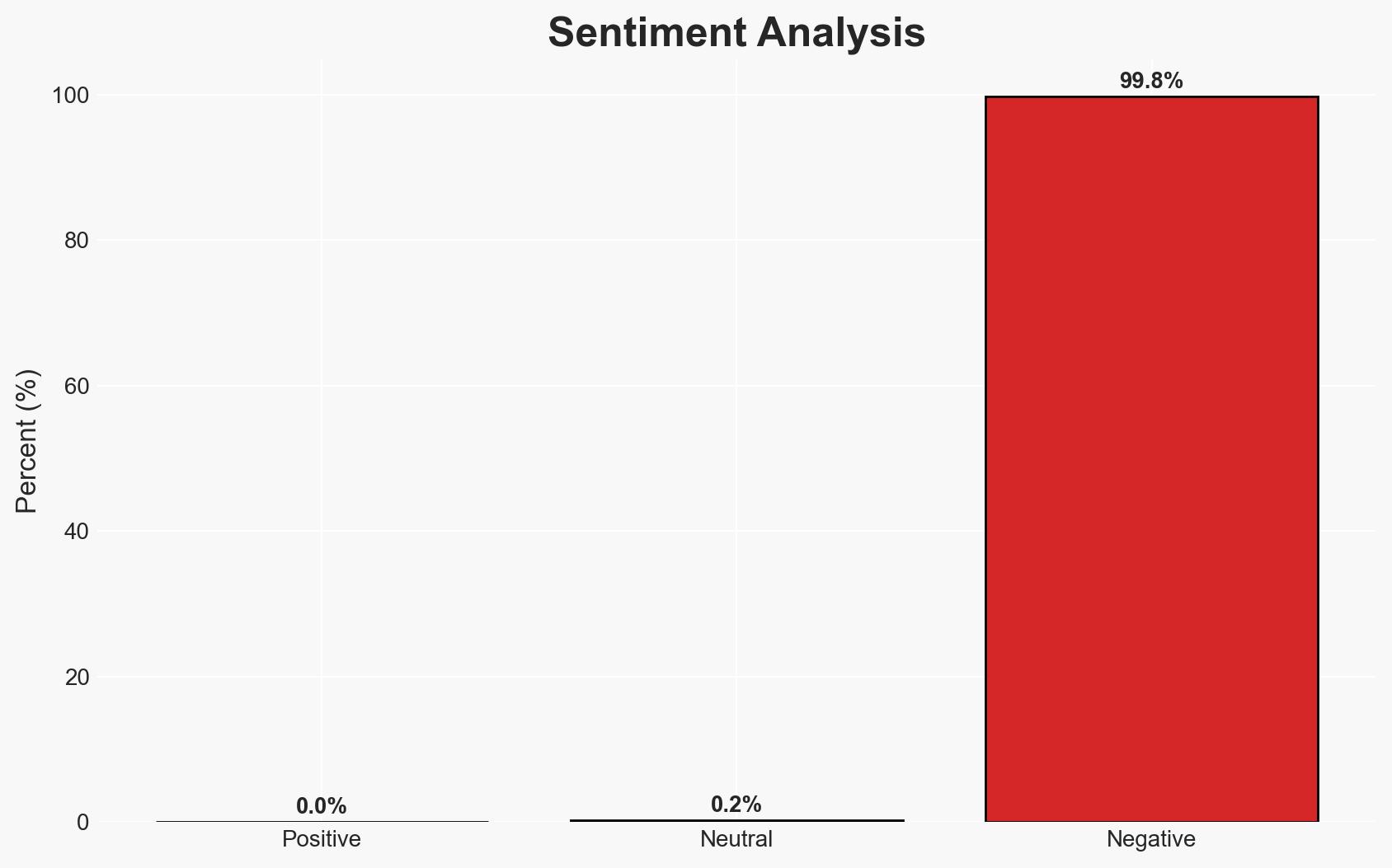
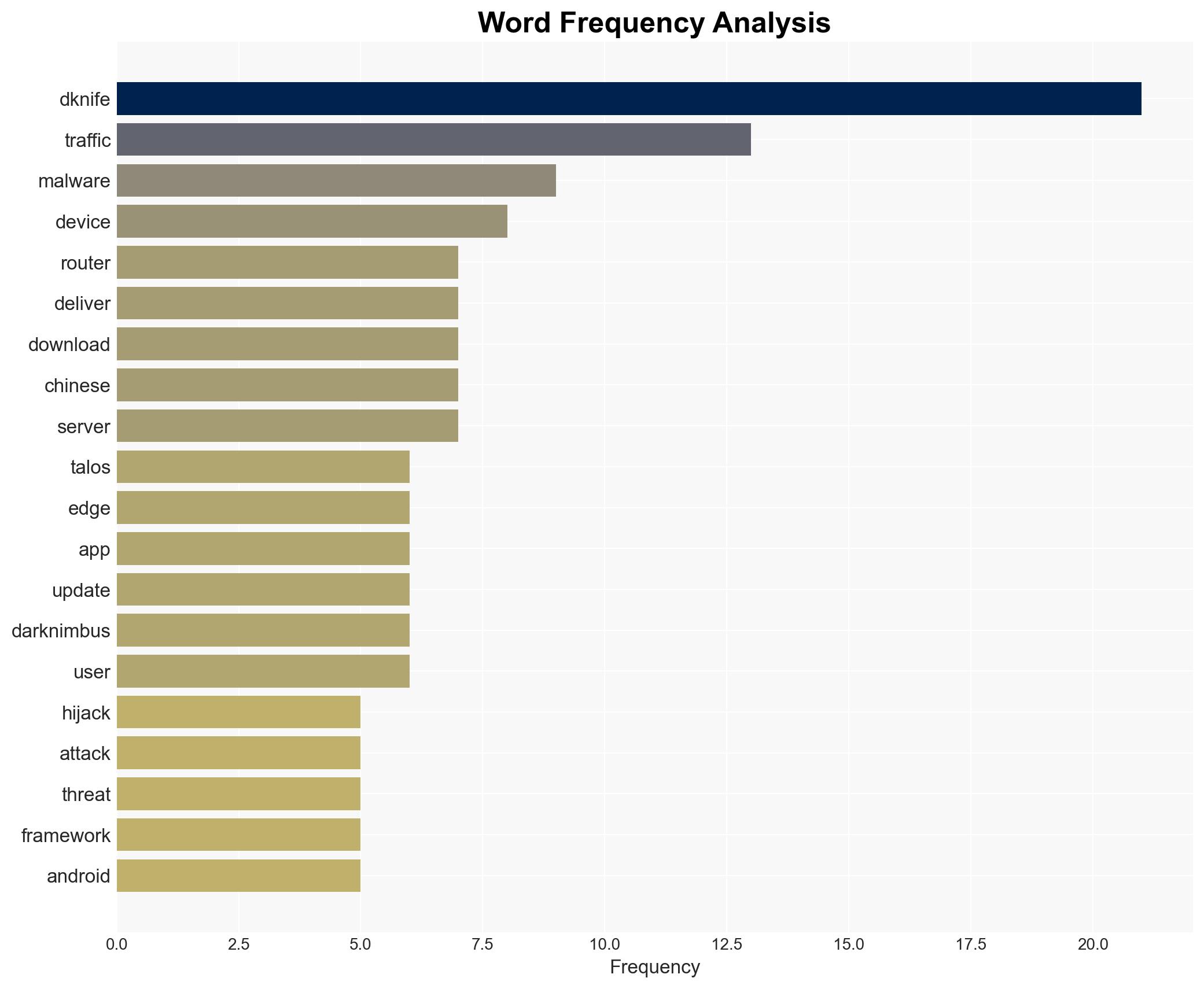
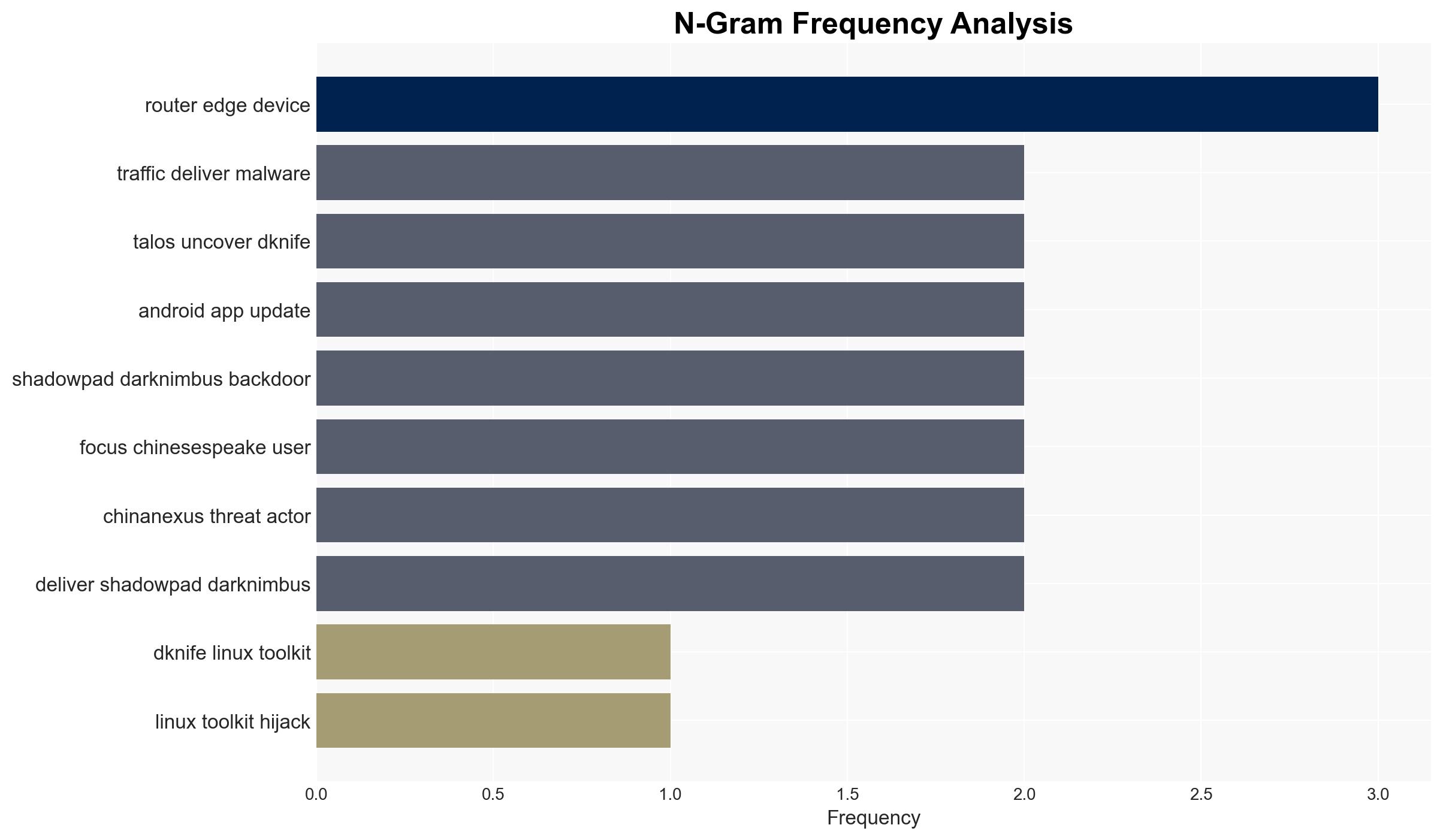
The DKnife toolkit has been used since 2019 to hijack router traffic and deliver malware, primarily targeting Chinese-speaking users. It is linked to China-nexus threat actors and remains active as of January 2026. The toolkit’s focus on Chinese apps and services suggests a strategic interest in regional espionage. Overall, there is moderate confidence in the attribution to Chinese threat actors and the ongoing operational status of DKnife.
2. Competing Hypotheses
- Hypothesis A: DKnife is primarily operated by Chinese state-affiliated actors targeting Chinese-speaking users for espionage purposes. This is supported by the focus on Chinese apps, use of Simplified Chinese in code, and the linkage to known China-nexus threat actors. However, the exact state affiliation remains unconfirmed.
- Hypothesis B: DKnife could be operated by non-state actors or a third-party group mimicking Chinese tactics to obfuscate true origins. While the evidence strongly points to Chinese involvement, the possibility of false flag operations cannot be entirely ruled out.
- Assessment: Hypothesis A is currently better supported due to the consistent pattern of targeting Chinese services and the linguistic and operational indicators pointing to Chinese actors. Confirmation of state affiliation or further evidence of alternative origins could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: DKnife’s primary operators are Chinese-speaking; the toolkit is used for espionage; the infrastructure is controlled by a single group.
- Information Gaps: Lack of direct evidence linking DKnife to specific Chinese state entities; limited visibility into the full scope of targeted regions beyond Chinese-speaking users.
- Bias & Deception Risks: Potential confirmation bias in attributing to Chinese actors due to linguistic evidence; risk of deception through false flag operations by other actors.
4. Implications and Strategic Risks
The continued use of DKnife could exacerbate regional tensions and influence cyber policy responses. The toolkit’s capabilities suggest a sophisticated threat that could evolve to target broader regions.
- Political / Geopolitical: Increased cyber tensions between China and affected nations; potential diplomatic fallout if state affiliation is confirmed.
- Security / Counter-Terrorism: Enhanced threat landscape for Chinese-speaking regions; potential for similar tactics to be adopted by other actors.
- Cyber / Information Space: Risks of widespread malware distribution and data breaches; potential for misinformation campaigns leveraging compromised data.
- Economic / Social: Disruption to businesses reliant on targeted apps; potential erosion of trust in digital services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of network traffic for signs of DKnife activity; collaborate with Chinese-speaking regions to share threat intelligence.
- Medium-Term Posture (1–12 months): Develop resilience measures for router and edge device security; strengthen partnerships with cybersecurity firms for threat intelligence sharing.
- Scenario Outlook:
- Best: Effective international cooperation leads to dismantling of DKnife infrastructure.
- Worst: DKnife operations expand, targeting additional regions and sectors.
- Most-Likely: Continued focused operations on Chinese-speaking users with periodic expansion attempts.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, China-nexus, malware, router security, cyber operations, regional targeting, false flag operations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us