Romania’s Conpet Faces Cyberattack Disrupting Business Systems and Website Access
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Romanias national oil pipeline firm Conpet reports cyberattack
1. BLUF (Bottom Line Up Front)
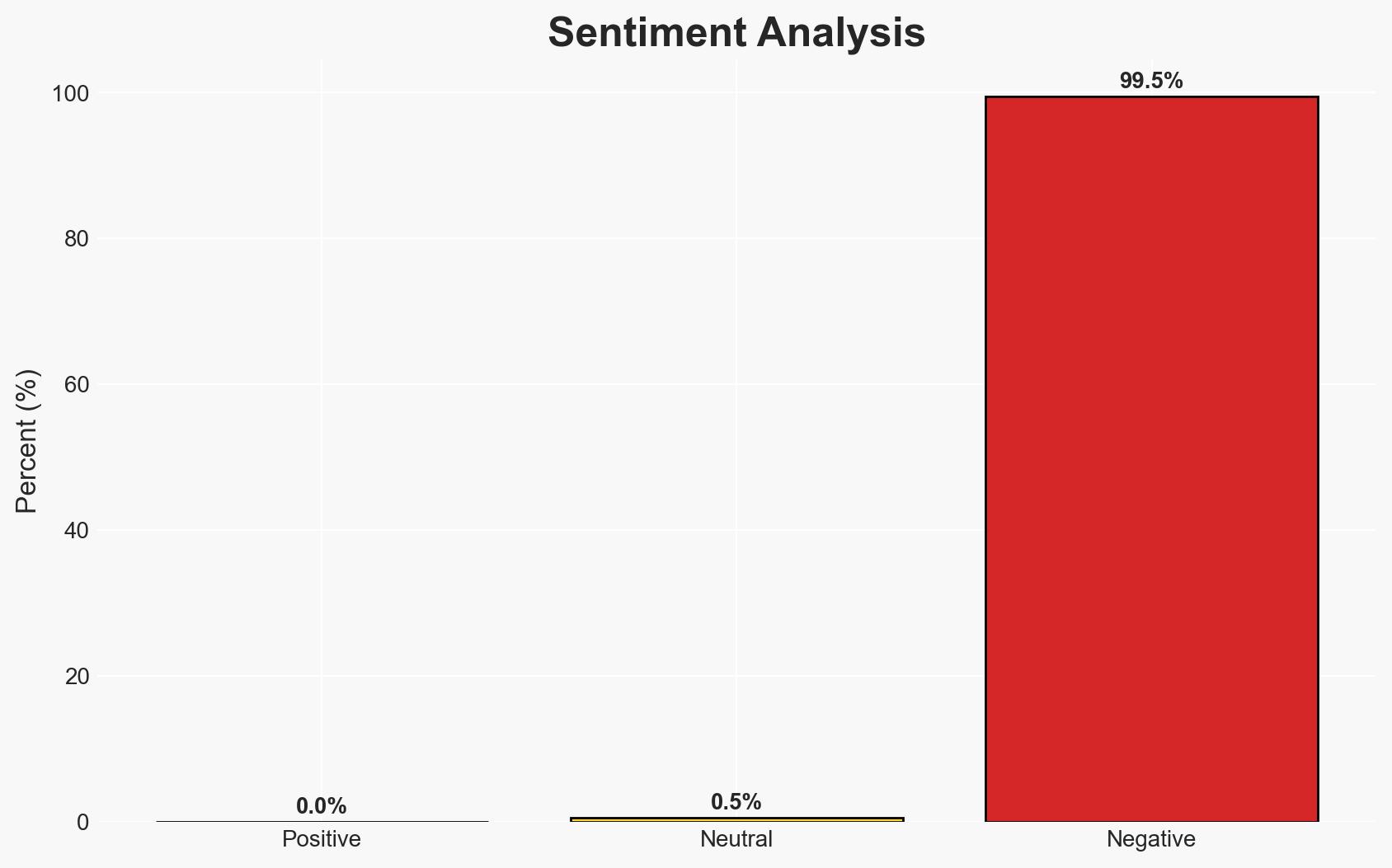
The Romanian national oil pipeline operator Conpet experienced a cyberattack attributed to the Qilin ransomware group, which disrupted its business IT systems but did not impact operational technologies. The attack highlights vulnerabilities in critical infrastructure sectors, with moderate confidence that the incident is part of a broader trend of ransomware targeting. The immediate operational impact appears minimal, but potential data breaches could have longer-term implications.
2. Competing Hypotheses
- Hypothesis A: The cyberattack on Conpet was primarily financially motivated, executed by the Qilin ransomware group to extort money by threatening to leak sensitive data. Supporting evidence includes the addition of Conpet to Qilin’s data leak site and the group’s known modus operandi. However, the absence of a ransom demand in the public domain is a key uncertainty.
- Hypothesis B: The attack may have been a politically motivated operation to destabilize Romanian critical infrastructure, possibly involving state-sponsored actors using Qilin as a proxy. This is less supported due to the lack of direct geopolitical tension indicators and the typical financial focus of Qilin.
- Assessment: Hypothesis A is currently better supported due to the alignment with Qilin’s known financial motivations and tactics. Indicators such as a public ransom demand or geopolitical tensions could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Conpet’s operational technologies remain unaffected; Qilin’s primary motivation is financial; Romanian cybersecurity authorities are effectively collaborating with Conpet.
- Information Gaps: Specific technical details of the cyberattack; whether a ransom demand was made; the extent of data exfiltration.
- Bias & Deception Risks: Potential bias in Conpet’s reporting to minimize perceived impact; possible deception by Qilin regarding the extent of data stolen.
4. Implications and Strategic Risks
This cyberattack could signal increasing threats to critical infrastructure, potentially encouraging similar attacks. The incident may prompt policy reviews and increased cybersecurity investments.
- Political / Geopolitical: Potential for increased scrutiny on Romania’s cybersecurity posture and international cooperation on cyber defense.
- Security / Counter-Terrorism: Heightened alert for critical infrastructure operators; potential for copycat attacks.
- Cyber / Information Space: Increased activity from ransomware groups targeting critical sectors; potential data leaks could affect public trust.
- Economic / Social: Minimal immediate economic impact, but potential reputational damage and increased costs for cybersecurity enhancements.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure cyber threats; conduct a thorough forensic investigation; engage with international cyber defense partners.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular cybersecurity audits and employee training; strengthen public-private partnerships in cybersecurity.
- Scenario Outlook:
- Best: No further incidents; enhanced cybersecurity measures prevent future attacks.
- Worst: Data breach leads to significant operational disruptions or geopolitical tensions.
- Most-Likely: Continued targeting of critical infrastructure by ransomware groups, with periodic disruptions.
6. Key Individuals and Entities
- Conpet S.A.
- Qilin Ransomware Group
- Romania’s National Cybersecurity Authorities
- Directorate for Investigating Organized Crime and Terrorism (DIICOT)
7. Thematic Tags
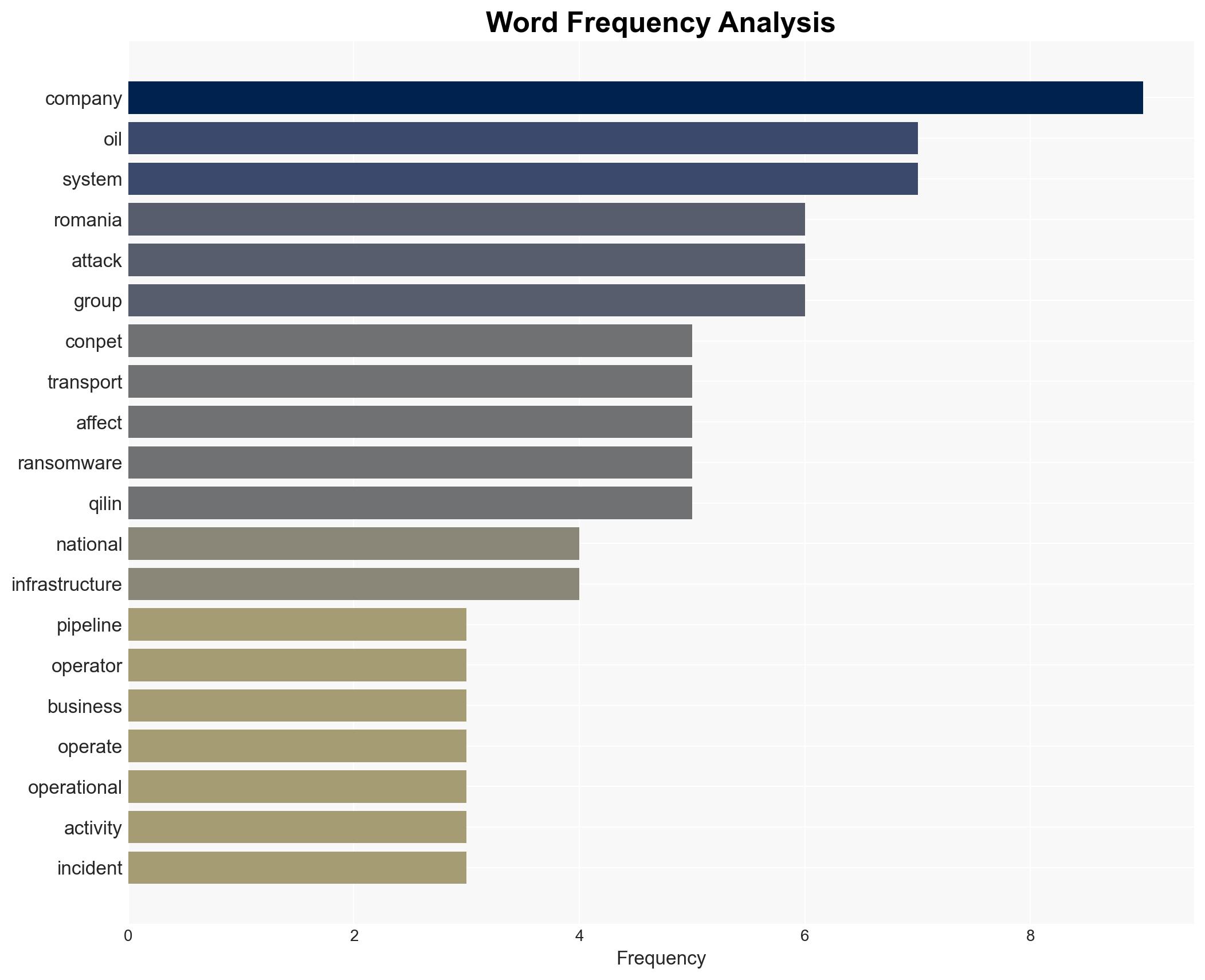
cybersecurity, ransomware, critical infrastructure, Romania, Qilin group, cyber defense, data breach
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us