Bloody Wolf Aims at Uzbekistan and Russia with NetSupport RAT in Targeted Phishing Attacks
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Bloody Wolf Targets Uzbekistan Russia Using NetSupport RAT in Spear-Phishing Campaign
1. BLUF (Bottom Line Up Front)
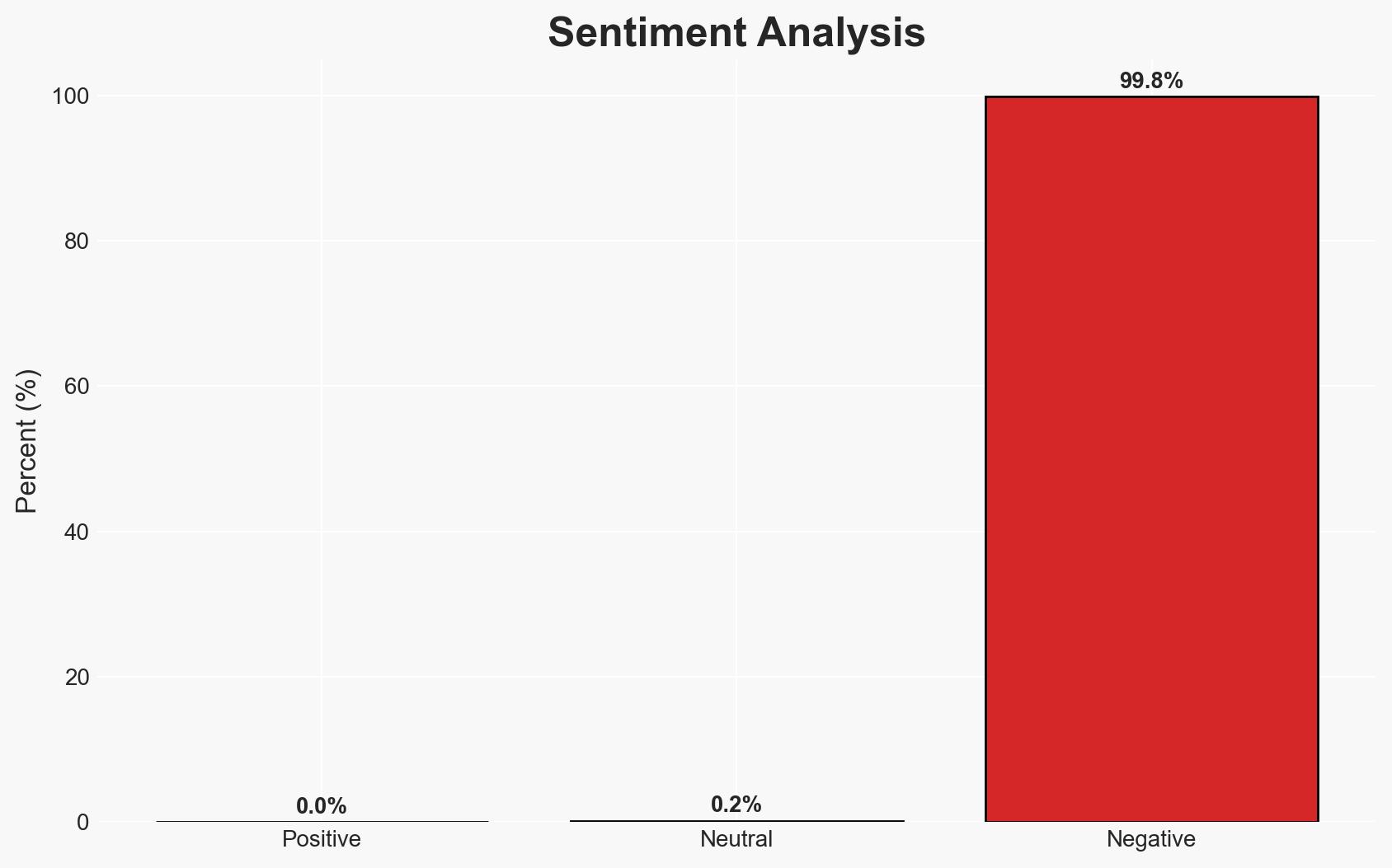
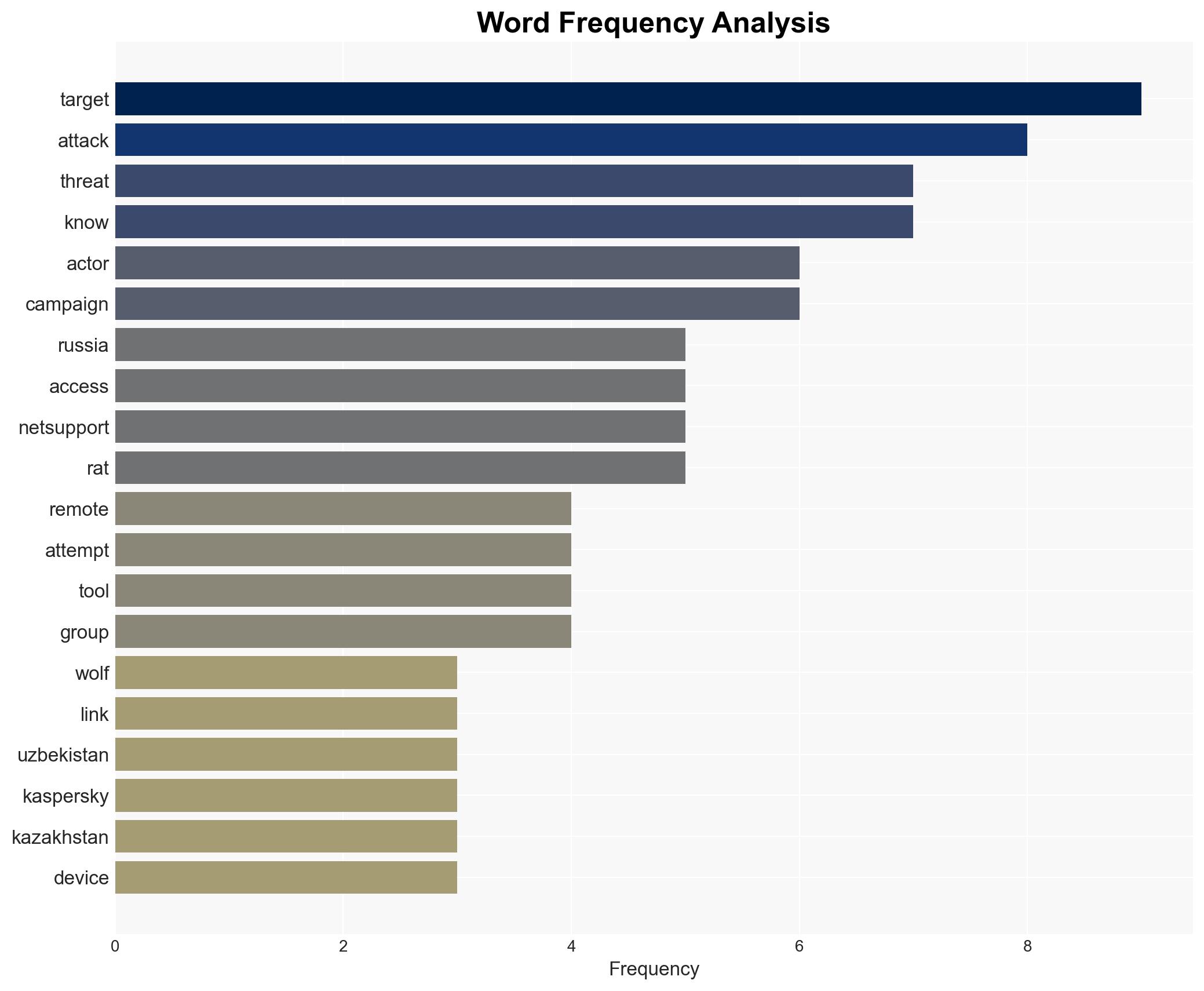
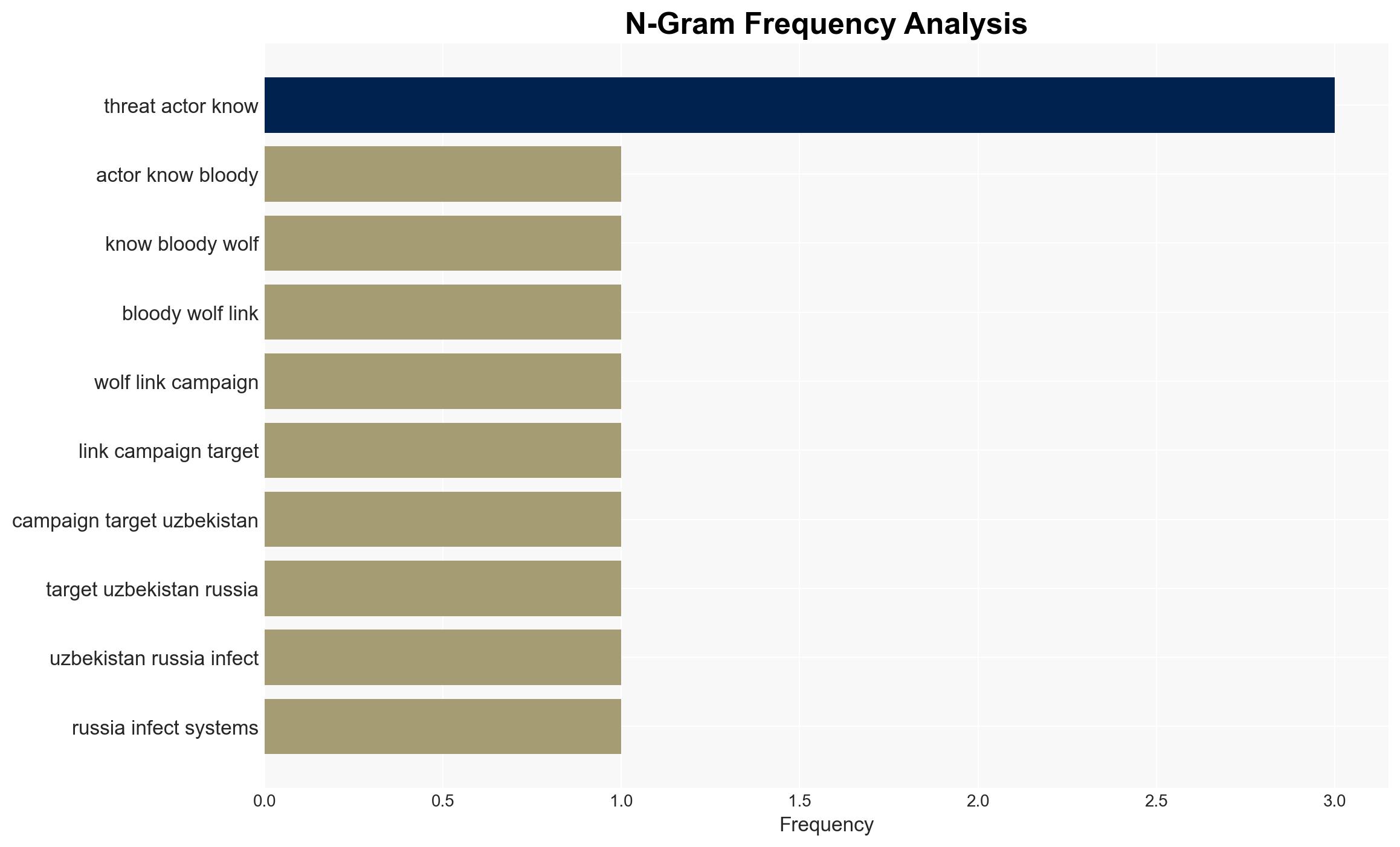
The cyber threat actor known as Bloody Wolf is conducting a spear-phishing campaign targeting Uzbekistan and Russia, employing the NetSupport RAT to compromise systems. The campaign appears financially motivated but may also involve espionage activities. The operation has impacted multiple sectors, including government and finance, with a moderate confidence level in the assessment of its dual-purpose nature.
2. Competing Hypotheses
- Hypothesis A: Bloody Wolf’s campaign is primarily financially motivated, targeting financial institutions and leveraging RATs for monetary gain. This is supported by the targeting of financial sectors and the use of spear-phishing, a common tactic for financial cybercrime. However, the use of RATs could also serve espionage purposes.
- Hypothesis B: The campaign is primarily aimed at cyber espionage, with financial gain as a secondary objective. The use of RATs and targeting of government and educational institutions suggest an interest in intelligence collection. Contradicting this is the emphasis on financial institutions, which typically indicates financial motives.
- Assessment: Hypothesis A is currently better supported due to the explicit targeting of financial institutions and the historical use of similar tactics for financial gain. Indicators such as the expansion to IoT devices and the presence of Mirai botnet payloads could shift this judgment towards espionage.
3. Key Assumptions and Red Flags
- Assumptions: Bloody Wolf is capable of sustaining operations across multiple countries; the use of NetSupport RAT is a strategic choice for its dual-use capabilities; financial gain is a primary motivator.
- Information Gaps: Detailed attribution of Bloody Wolf’s leadership and sponsorship; comprehensive victim impact assessment; confirmation of espionage activities.
- Bias & Deception Risks: Potential bias in source reporting from cybersecurity vendors; possibility of false flag operations to mislead attribution; reliance on open-source data may omit classified insights.
4. Implications and Strategic Risks
This campaign could evolve into a broader regional threat, affecting geopolitical stability and increasing cyber tensions. The dual-use nature of the tools employed suggests a potential for escalation into state-sponsored cyber activities.
- Political / Geopolitical: Increased cyber tensions between targeted states and potential retaliatory measures.
- Security / Counter-Terrorism: Enhanced threat landscape for targeted sectors, necessitating improved cybersecurity defenses.
- Cyber / Information Space: Potential for increased cyber espionage activities and information warfare tactics.
- Economic / Social: Disruption to financial sectors could have broader economic impacts, affecting investor confidence and market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of phishing activities; deploy advanced threat detection tools; increase awareness and training for potential targets.
- Medium-Term Posture (1–12 months): Develop partnerships for intelligence sharing; invest in cybersecurity infrastructure; conduct joint exercises to simulate and prepare for similar threats.
- Scenario Outlook:
- Best: Successful mitigation and attribution lead to reduced threat activity.
- Worst: Escalation into state-sponsored cyber conflict with significant geopolitical ramifications.
- Most-Likely: Continued targeted attacks with gradual improvements in defensive measures and intelligence capabilities.
6. Key Individuals and Entities
- Bloody Wolf (Threat Actor)
- Kaspersky (Cybersecurity Vendor)
- Group-IB (Cybersecurity Firm)
- ExCobalt (Other Threat Actor)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, financial crime, spear-phishing, remote access trojan, geopolitical tensions, information warfare
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us